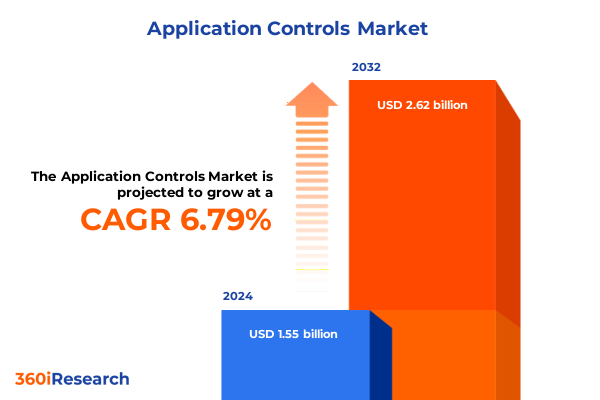
The Application Controls Market size was estimated at USD 1.65 billion in 2025 and expected to reach USD 1.77 billion in 2026, at a CAGR of 6.80% to reach USD 2.62 billion by 2032.
Understanding the Crucial Role of Application Controls in Safeguarding Organizational Data Integrity and Ensuring Regulatory Compliance Amid Rapid Technological Evolution
In a landscape defined by escalating cyber threats, evolving regulatory mandates, and the relentless pace of technological innovation, application controls have become indispensable pillars of enterprise risk management. These controls encompass the preventive, detective, and corrective mechanisms embedded within software applications to ensure data accuracy, integrity, and security. As organizations broaden their digital footprints across cloud environments, mobile platforms, and interconnected ecosystems, the significance of robust application controls cannot be overstated.
Effective application controls not only safeguard sensitive information against unauthorized access and manipulation but also enhance the reliability of financial reporting, operational processes, and decision-making systems. By integrating these controls seamlessly into software development lifecycles and IT operations, businesses can mitigate risks associated with human error, system failures, and emerging threat vectors. As a result, stakeholders gain increased confidence in the consistency and compliance of mission-critical applications, ultimately reinforcing organizational resilience.
Navigating the Confluence of Cloud, AI, and Regulatory Dynamics to Drive Next-Generation Intelligence-Based Application Control Environments
Over the past few years, the application controls landscape has been fundamentally reshaped by a wave of transformative shifts that challenge legacy assumptions and demand new strategic imperatives. The widespread adoption of cloud-native architectures and hybrid deployment models has blurred the boundaries between traditional on-premises systems and externally hosted environments. This shift requires organizations to reengineer control frameworks to operate seamlessly across diverse infrastructures, ensuring consistent policy enforcement and real-time visibility.
Artificial intelligence and machine learning have emerged as powerful enablers of adaptive control mechanisms, capable of analyzing vast data streams to identify anomalies and preempt potential threats. Simultaneously, the democratization of low-code and no-code platforms empowers business units to develop bespoke applications at unprecedented speed, heightening the need for automated guardrails that maintain governance without stifling innovation. Moreover, the global rise of stringent data protection regulations has compelled enterprises to adopt proactive control strategies that embed privacy-by-design principles into every stage of application development.
Collectively, these dynamics have catalyzed a shift from manual, perimeter-focused approaches toward continuous, intelligence-driven control environments. Organizations that embrace these transformative shifts are better positioned to anticipate vulnerabilities, streamline compliance processes, and harness operational efficiencies, thereby turning application controls into strategic levers for sustained competitive advantage.
Assessing the Ripple Effects of 2025 United States Tariffs on Application Control Strategies, Vendor Ecosystems, and Supply Chain Resilience
The imposition of new United States tariffs in 2025 on select software components and related hardware has created a cascade of challenges and opportunities impacting application control adoption. Heightened import duties on server appliances, memory modules, and specialized security processors have increased total cost of ownership for on-premises solutions. As procurement teams grapple with elevated capital expenditures, many have reevaluated their application control strategies, accelerating migrations toward cloud-based alternatives where tariff impacts are diffused across global infrastructure providers.
These tariff-driven cost pressures have also underscored the strategic importance of vendor diversification and supply chain resilience. Organizations have begun to prioritize software platforms that support a broad range of hardware configurations, including import-neutral commodity servers and localized manufacturing partnerships. Consequently, application control vendors have responded by expanding interoperability standards and forging alliances with domestic hardware producers to mitigate tariff exposure.
In parallel, the regulatory scrutiny accompanying tariff policy shifts has prompted enterprises to reinforce compliance pipelines for import documentation, audit trails, and software asset management. Application controls have thus evolved to encompass modules that track end-to-end procurement and deployment lifecycles, ensuring transparent lineage from purchase order to operational runtime. This expanded scope has not only bolstered adherence to trade regulations but also facilitated more agile responses to future policy adjustments, positioning organizations to adapt more rapidly in an increasingly protectionist trade environment.
Elucidating Market Trajectories Across Industry Verticals, Deployment Paradigms, Organizational Scale, and Layered Control Mechanisms
The multifaceted nature of the application controls market becomes apparent when viewed through the lens of industry verticals, deployment modes, organization sizes, and control typologies. Financial institutions, defense bodies, healthcare providers, IT and telecom firms, and retail and e-commerce enterprises each present distinct operational risks and compliance mandates that shape the selection and prioritization of control mechanisms. Within banking, capital markets, and insurance, for example, granular transaction validation and anti-money laundering safeguards take precedence, while hospitals and pharmaceutical entities concentrate on patient data confidentiality and regulatory audit trails.
Deployment choices further differentiate market demand. Cloud-based models-spanning public, private, and hybrid environments-offer rapid scalability and built-in redundancy, appealing to organizations seeking to alleviate tariff-induced hardware costs and accelerate time to value. In contrast, on-premises implementations, leveraging either bare metal infrastructure or virtualized machines, continue to hold sway where data sovereignty or bespoke customization drives preferences. These deployment decisions often correlate with organizational size: large enterprises typically command the resources to maintain complex, heterogeneous environments, whereas small and medium enterprises gravitate toward managed, turnkey solutions that minimize operational overhead.
Diving deeper into control typologies, preventive measures such as automated authentication, role-based access, and integrity checks serve as the first line of defense, complemented by detective controls like continuous monitoring, event log review, and anomaly detection. When breaches occur or discrepancies arise, corrective controls activate processes for incident response, root cause analysis, and remediation workflows. Together, these control categories form an integrated, multi-layered shield that adapts dynamically to the evolving risk landscape, ensuring that application governance remains both robust and flexible.
This comprehensive research report categorizes the Application Controls market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Control Type
- Industry Vertical
- Deployment Mode
- Organization Size
Uncovering Regional Adoption Patterns Driven by Divergent Regulatory Landscapes, Technological Maturity, and Cross-Border Security Imperatives
Geographic nuances play a pivotal role in shaping application control adoption, reflecting regional regulatory frameworks, technology infrastructure maturity, and localized threat vectors. In the Americas, a strong emphasis on data privacy legislation and digital transformation roadmaps has promoted extensive deployment of cloud-native control platforms, often leveraging North American hyperscalers and regional service integrators. Organizations here tend to prioritize solutions that harmonize with multijurisdictional compliance requirements, particularly for cross-border data flows and international audit standards.
The Europe, Middle East & Africa corridor presents a tapestry of regulatory complexity, where the General Data Protection Regulation coexists with emerging national cybersecurity directives. Enterprises across this region invest in modular control suites that can be tailored to diverse legal environments, combining encryption, pseudonymization, and localized data residency features. Moreover, heightened geopolitical tensions have elevated the role of defensive controls capable of mitigating sophisticated threat campaigns targeting critical infrastructure and defense contractors.
In Asia-Pacific, a dual narrative unfolds: advanced economies such as Japan and Australia pursue AI-enhanced continuous monitoring and predictive analytics, while rapidly developing markets in Southeast Asia and India focus on leapfrogging legacy systems through cloud-first strategies. Government initiatives promoting digital governance and cybersecurity frameworks have stimulated adoption, driving demand for interoperable controls that integrate with both domestic platforms and global technology ecosystems. Across all regions, intercontinental partnerships and consortiums are catalyzing knowledge exchange, further accelerating the harmonization of application control best practices.
This comprehensive research report examines key regions that drive the evolution of the Application Controls market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Charting the Competitive Dynamics Shaping Application Control Innovations Through Strategic Alliances, Acquisitions, and Agile Specialization
The competitive landscape for application controls is marked by a dynamic interplay between established global technology firms and emerging specialist vendors. Leading software providers have augmented their core platforms with advanced security modules, leveraging machine learning models to automate anomaly detection and policy enforcement. These incumbents frequently pursue vertical-specific enhancements through targeted acquisitions, integrating niche capabilities such as real-time encryption key management and fraud prevention intelligence.
Concurrently, mid-tier and boutique vendors differentiate themselves through rapid innovation cycles and deep domain expertise. By focusing on agile development methodologies and modular architecture, they can deliver purpose-built solutions that address unique pain points within healthcare diagnostics, financial trading floors, or retail supply chains. Partnerships between these specialists and larger systems integrators have become commonplace, enabling seamless orchestration of comprehensive control frameworks that combine best-of-breed components.
Furthermore, strategic alliances with cloud service providers and cybersecurity consultancies have broadened the go-to-market reach for several emerging players, allowing them to embed application controls within broader digital transformation and managed security service offerings. This collaborative ecosystem not only fosters continuous feature enrichment but also responds to evolving customer requirements for unified, end-to-end risk management solutions.
This comprehensive research report delivers an in-depth overview of the principal market players in the Application Controls market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Check Point Software Technologies Ltd.
- Diligent Corporation
- International Business Machines Corporation
- MetricStream, Inc.
- Microsoft Corporation
- Oracle Corporation
- RSA Security LLC
- SAI Global Limited
- SAP SE
- Thomson Reuters Corporation
- Wolters Kluwer N.V.
Empowering Organizations to Embed Security and Compliance Across Development Lifecycles Through Integrated Analytics, Automation, and Cross-Functional Governance
Industry leaders seeking to fortify their application control posture should begin by embedding governance principles early in the development lifecycle. By aligning control design with DevSecOps practices, teams can shift security and compliance left, ensuring that preventive and detective mechanisms are codified alongside functional requirements. This approach reduces costly retrofits and fosters a culture of shared responsibility across development, operations, and security stakeholders.
Organizations should also invest in integrated analytics platforms that correlate logs, user behaviors, and system metrics to generate actionable intelligence. Continuous monitoring dashboards, powered by machine learning algorithms, enable rapid identification of anomalous patterns and streamline incident response workflows. Prioritizing automation not only accelerates threat detection and remediation but also alleviates resource constraints on security teams, allowing them to focus on strategic initiatives.
Moreover, establishing cross-functional governance councils can drive consistency in control policy enforcement and accommodate the diverse regulatory demands of different business units. Regular tabletop exercises and simulation drills reinforce preparedness, while periodic architecture reviews ensure that evolving technologies-such as edge computing and containerization-are supported by appropriate control constructs. By adopting this holistic, proactive stance, industry leaders will transform application controls from reactive safeguards into strategic enablers of innovation and compliance.
Leveraging a Blend of Executive Interviews, Regulatory Analyses, and Technology Audits to Deliver Rigorous and Actionable Application Control Insights
The insights presented in this report derive from a rigorous research methodology that combines both primary and secondary investigative techniques. Primary research encompassed structured interviews with C-level executives, IT security directors, and compliance officers across diverse industry verticals. These dialogues provided nuanced perspectives on emerging control challenges, procurement preferences, and the tangible impact of regulatory changes on application governance.
Secondary research involved an exhaustive review of publicly available regulatory frameworks, whitepapers, technical standards, and vendor documentation. This phase also incorporated analysis of patent filings, cybersecurity incident databases, and technology roadmaps to validate market trends and identify innovation hotspots. Data triangulation was achieved by cross-referencing survey findings with documentary evidence, ensuring the robustness and reliability of our conclusions.
Throughout the methodology, ethical considerations for data privacy and confidentiality were strictly observed, with all participants providing informed consent. The iterative synthesis of qualitative insights and quantitative benchmarks facilitated the development of a comprehensive narrative, designed to guide decision-makers in deploying effective, future-ready application control strategies.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Application Controls market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Application Controls Market, by Control Type
- Application Controls Market, by Industry Vertical
- Application Controls Market, by Deployment Mode
- Application Controls Market, by Organization Size
- Application Controls Market, by Region
- Application Controls Market, by Group
- Application Controls Market, by Country
- United States Application Controls Market
- China Application Controls Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 1908 ]
Synthesizing Strategic Imperatives for Resilient, Intelligence-Driven Application Control Strategies That Fuel Innovation and Trust Across Enterprises
As organizations navigate an era marked by rapid digital transformation and heightened security demands, the role of application controls transcends mere compliance checkboxes to become fundamental building blocks of resilient architectures. The evolving confluence of cloud services, AI-driven analytics, and regulatory complexity necessitates adaptive control frameworks that balance agility with robust governance.
By understanding the interplay of tariffs, geopolitical dynamics, and sector-specific requirements, decision-makers can craft strategies that not only safeguard against current threat vectors but also anticipate future challenges. Segmentation across industry verticals, deployment models, organizational scale, and control types reveals nuanced adoption patterns, guiding tailored investments that optimize both risk mitigation and operational efficiency.
Ultimately, the competitive edge in today’s marketplace hinges on the ability to integrate security seamlessly into every layer of application delivery. Leaders who embrace proactive, intelligence-driven controls will not only fortify their defenses but also pave the way for innovation, unlocking new value streams while maintaining the highest standards of integrity and trust.
Partner Directly with Ketan Rohom to Transform Application Control Frameworks into Strategic Assets That Drive Resilience and Long-Term Business Growth
Embarking on a journey to fortify your organization’s application control framework starts with a decisive step toward engaging experts who understand the intricate balance between security, efficiency, and compliance. By partnering directly with Ketan Rohom, Associate Director of Sales & Marketing, you will gain personalized guidance tailored to your unique operational landscape. Ketan brings a wealth of experience in translating complex research into actionable solutions, ensuring that your investment delivers meaningful impact across every layer of your enterprise.
Initiating this partnership is seamless: you will receive an in-depth consultation that aligns the insights from the comprehensive market research report with your strategic priorities. This collaborative approach will unveil hidden opportunities for optimizing control processes and mitigating emerging risks specific to your sector. The result is a roadmap that not only leverages industry best practices but also anticipates the evolving regulatory and technological environment.
Make the move to secure your organization’s future by tapping into the premium intelligence encapsulated in this market research report. Engage with Ketan Rohom today to unlock access to detailed analyses, customized recommendations, and continued advisory support. Together, you will transform control frameworks into dynamic assets that drive resilience, innovation, and long-term growth across the enterprise.

- How big is the Application Controls Market?
- What is the Application Controls Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




