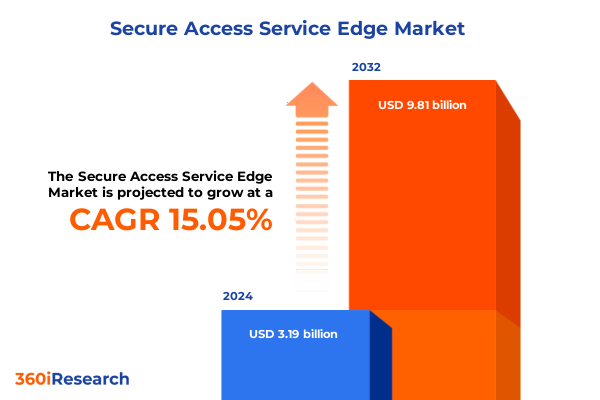
The Secure Access Service Edge Market size was estimated at USD 3.65 billion in 2025 and expected to reach USD 4.18 billion in 2026, at a CAGR of 15.14% to reach USD 9.81 billion by 2032.
Navigating the Convergence of Networking and Security in a Rapidly Evolving SASE Ecosystem to Empower Enterprise Connectivity
Enterprises today face an unprecedented convergence of network performance demands and security imperatives, driven by the shift to distributed workforces and the rapid adoption of cloud services. As organizations navigate this evolving landscape, traditional perimeter-based defenses are proving insufficient to safeguard diverse user populations, applications, and data flows. Secure Access Service Edge, commonly abbreviated as SASE, emerges as a holistic framework that unifies networking and security functions into a cloud-native architecture, enabling consistent policy enforcement and optimized connectivity across any edge.
By embedding security services directly into the fabric of wide area networking, SASE eliminates the complexities and latency inherent in backhauling traffic through centralized firewalls. Organizations can thereby preserve user experience, enhance threat protection, and simplify operational overhead. Moreover, the inherent scalability of cloud-delivered security aligns with the dynamic requirements of hybrid and multi-cloud environments, allowing enterprises to adapt to fluctuating workloads without the burden of capital expenditures on proprietary appliances. Consequently, SASE is redefining how businesses architect secure access and connectivity in the digital era.
Embracing Zero Trust and Cloud-Native Architectures as Foundational Shifts Driving the Next Wave of Secure Access Service Edge Transformations
The SASE paradigm has catalyzed a series of transformative shifts in how enterprises think about secure connectivity. First, the repudiation of the traditional network perimeter in favor of identity-driven access controls has ushered in Zero Trust principles as central tenets. Zero Trust Network Access (ZTNA) enforces continuous verification of user and device credentials, irrespective of location, ensuring that every session is adhering to the least-privilege model and thereby reducing the attack surface.
Furthermore, the integration of Software-Defined Wide Area Networking with cloud-native security services has morphed into a unified operating model. Software-Defined WAN capabilities now work in concert with Secure Web Gateways and Cloud Access Security Brokers to deliver consolidated policy management and threat intelligence. This fusion streamlines workflows and enhances visibility across the network fabric, enabling IT teams to enforce consistent security posture across branch offices, remote endpoints, and cloud assets.
Moreover, artificial intelligence and machine learning are being embedded into SASE offerings to automate threat detection and response. AI-driven analytics continuously monitor behavioral patterns and surface anomalies, reducing dwell time for advanced threats and lowering the burden on SOC teams. As a result, SASE solutions are increasingly positioning themselves as adaptive platforms capable of evolving with emerging threat vectors and hybrid work models.
Assessing the Ripple Effects of Newly Imposed U.S. Tariffs on 2025 Enterprise Security Infrastructure and Supply Chain Dynamics
The United States’ 2025 tariff landscape has introduced significant headwinds for SASE infrastructure deployments that rely on hardware appliances. Broadly, tariffs ranging from 20% to 25% have been applied to networking components sourced from key manufacturing regions, including firewalls, routers, and SD-WAN devices, pushing up procurement costs and extending project timelines. In parallel, steep duties of up to 145% on advanced telecom equipment have disrupted supply chains for edge data center gear and critical network transceivers, prompting some organizations to reevaluate their supplier strategies and accelerate stockpiling ahead of tariff enforcement dates.
In response to these measures, leading manufacturers have cited price adjustments between 8% and 20% on enterprise hardware. For example, HPE ProLiant servers have seen tariff-driven surcharges in the teens, while Cisco Catalyst switches are anticipated to cost approximately 5% to 10% more by mid-2025. These incremental increases have a cascading effect: higher capital expenses translate into greater total cost of ownership and alter return-on-investment analyses for network modernization initiatives. To mitigate these impacts, some companies are extending hardware refresh cycles and leaning further into cloud-delivered SASE components, reducing reliance on on-premises appliances.
Nevertheless, the broader uncertainty surrounding the longevity of these tariffs-reinforced by legal challenges at the U.S. Court of International Trade-continues to influence vendor roadmaps and enterprise purchasing frameworks. While the appeal process may eventually ease some duties, interim volatility underscores the importance of agile procurement strategies and diversified vendor portfolios to sustain seamless secure access deployments.
Uncovering Critical Component, Deployment and Industry Segmentation Insights to Illuminate Diverse Use Cases within the SASE Market
When evaluating Secure Access Service Edge solutions, it becomes evident that the competitive landscape is defined by nuanced participant roles based on specific functional and deployment criteria. Component diversity spans from secure web gateways and cloud access security brokers to zero trust network access capabilities and software-defined wide area networking offerings. Each component brings unique operational value, whether it is granular control over web traffic, comprehensive visibility into cloud-delivered applications, policy-centric user authentication, or optimized routing across distributed locations. Consequently, successful SASE strategies often balance these components to weave an integrated tapestry of performance and protection.
Beyond core functionalities, the mode of deployment profoundly shapes adoption pathways. Cloud‐native SASE platforms appeal to organizations seeking rapid scalability and simplified provisioning, especially those with dynamic workloads and rapid growth trajectories. Conversely, on-premise implementations retain their foothold in highly regulated sectors or environments with stringent latency and data sovereignty requirements, where localized policy enforcement remains paramount. In practice, many enterprises gravitate toward hybrid models that leverage both cloud and localized SASE instances, aligning with their unique compliance, performance, and resilience needs.
Finally, industry context is a significant driver of SASE adoption priorities. Financial institutions often emphasize rigorous identity controls and comprehensive audit trails to satisfy regulatory mandates, whereas manufacturing enterprises may focus on securing a sprawling network of operational technology devices. Healthcare and government sectors increasingly prioritize data loss prevention and continuity of care, while technology and telecom companies integrate SASE to support high-volume traffic and rapid service turn-up. Energy, utilities, and retail verticals likewise tailor component mixes and deployment strategies to align with their respective risk profiles, operational rhythms, and digital transformation roadmaps.
This comprehensive research report categorizes the Secure Access Service Edge market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Offering Type
- Deployment Mode
- End-Use Industry
Exploring Regional Dynamics and Strategic Drivers across the Americas, Europe Middle East Africa and Asia-Pacific SASE Landscapes
Regional nuances play a pivotal role in how organizations adopt and evolve their SASE initiatives. In the Americas, expansive geographical footprints and mature cloud ecosystems drive a preference for cloud-native SASE services that can flexibly route traffic and apply unified security policies across multiple jurisdictions. This region’s regulatory environment, characterized by evolving privacy statutes and industry-specific requirements, further incentivizes solutions with advanced data protection and compliance modules.
Conversely, the Europe, Middle East and Africa landscape exhibits pronounced regulatory heterogeneity, from GDPR in the European Union to divergent telecommunication standards across the Middle East. Enterprises in this region often adopt a hybrid SASE posture, combining cloud-hosted controls with localized on-premise elements to satisfy data residency mandates and network latency constraints. The growing focus on digital sovereignty has catalyzed investments in regionally positioned secure gateways and edge nodes.
Meanwhile, the Asia-Pacific region presents a dynamic growth trajectory fueled by digital infrastructure expansion and a surge in mobile workforce enablement. Organizations here prioritize scalable, consumption-based SASE offerings that can accommodate rapid user proliferation and the integration of emerging technologies like edge AI. Local regulatory variances, particularly in Southeast Asia, underscore the need for adaptable policy frameworks that can be rapidly tailored to country-specific data privacy and cybersecurity directives.
This comprehensive research report examines key regions that drive the evolution of the Secure Access Service Edge market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Leading SASE Providers and Innovators Shaping Tomorrow’s Secure Access Service Edge Market with Pioneering Technologies
A cadre of established cybersecurity vendors and innovative newcomers are vying for leadership in the SASE domain. Early pioneers have evolved their hardware-centric portfolios to embrace cloud-native architectures, unifying SD-WAN, firewall as a service and secure web gateway functionalities under single-vendor umbrellas. This streamlined approach simplifies procurement and management, enabling organizations to avoid fragmented point solutions.
In parallel, pure-play cloud security providers are rapidly augmenting their platform capabilities with networking services, leveraging multi-tenant infrastructure to deliver elastic throughput and integrated threat intelligence. These cloud-first players often excel in delivering rapid time to value, though they may face challenges addressing specialized on-premise requirements in highly regulated industries. Additionally, strategic partnerships between network equipment manufacturers and security software companies are emerging, delivering co-engineered SASE appliances for enterprises demanding on-premise performance with cloud-backed policy orchestration.
Collectively, these market participants are charting differentiated paths: some double down on AI-powered analytics and automated policy remediation, while others pursue edge-optimized architectures to reduce latency for critical applications. As competition intensifies, interoperability, unified licensing models and streamlined deployment tools are becoming key differentiators for next-generation SASE offerings.
This comprehensive research report delivers an in-depth overview of the principal market players in the Secure Access Service Edge market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Akamai Technologies, Inc.
- Aryaka Networks, Inc.
- Barracuda Networks, Inc. by KKR
- Broadcom, Inc.
- BT Group
- Cato Networks, Ltd.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Cloud Software Group, Inc.
- Cloud4C Services
- Cloudflare, Inc.
- Ericom Software, Inc.
- Exclusive Networks SA
- Forcepoint LLC
- Fortinet, Inc.
- Hewlett Packard Enterprise Development LP
- International Business Machines Corporation
- Juniper Networks, Inc.
- McAfee, LLC
- Microsoft Corporation
- Netskope, Inc.
- NTT Ltd.
- Open Systems AG by Emerson Electric Co.
- Palo Alto Networks, Inc.
- Perimeter 81 Ltd.
- SentinelOne, Inc.
- SonicWall Inc.
- Twingate Inc.
- Verizon Communications Inc.
- Versa Networks, Inc.
- VMware, Inc.
- Zentera Systems, Inc.
- Zscaler, Inc.
Delivering Strategic Action Plans and Operational Recommendations to Enhance Security Postures and Network Agility for Modern Enterprises
Industry leaders should realign their network and security strategies around a unified SASE framework to eliminate operational silos and enhance chassis-level resilience. To start, organizations must conduct comprehensive infrastructure audits to identify legacy choke points in branch connectivity and cloud access, enabling targeted migration of workloads to software-defined and cloud-delivered services. This phased approach not only reduces risk but also smooths budgetary impacts by staggering transition costs.
Concurrently, security and networking teams should collaborate on defining consistent policy templates that align with regulatory mandates and business objectives. By leveraging centralized orchestration consoles, administrators can enforce granular access controls while maintaining full visibility across all edges. Furthermore, it is imperative to integrate advanced analytics and threat intelligence feeds to automate the identification and remediation of anomalous behaviors, thereby accelerating mean time to detect and respond.
Finally, to navigate tariff-induced supply chain pressures, procurement teams must pursue vendor diversification strategies. This entails evaluating single-vendor SASE suites alongside best-of-breed modular offerings, factoring in total cost of ownership, regional data sovereignty needs and projected hardware refresh cycles. By cultivating a balanced vendor ecosystem, organizations can safeguard against geopolitical and pricing volatility while sustaining continuous secure access capabilities.
Detailing Our Rigorous Mixed-Methods Research Approach Combining Primary Interviews and Secondary Analysis to Validate SASE Intelligence
Our analysis draws on a meticulously designed mixed-methods approach to ensure both breadth and depth of insights. Primary data was collected through structured interviews with Chief Information Security Officers, network architects and industry consultants across multiple regions, providing frontline perspectives on deployment challenges, performance benchmarks and regulatory considerations. These qualitative inputs were complemented by an extensive review of publicly available technical white papers, industry blogs and regulatory filings to validate emerging trends and solution roadmaps.
Quantitative data points were derived from a customized survey targeting IT decision-makers in banking, healthcare, manufacturing, retail and government sectors. Respondents provided detailed input on component adoption rates, deployment preferences and budgeting cycles, enabling statistical cross-analysis to uncover correlation patterns and segmentation variances. These findings were further triangulated with secondary market intelligence reports and trade association publications to contextualize regional and vertical dynamics.
Throughout the research process, rigorous data validation techniques were applied, including outlier analysis and response consistency checks, to uphold the integrity of our conclusions. This triangulated methodology ensures that the insights presented in this report accurately reflect the pulse of the SASE market and the strategic imperatives facing enterprise leaders.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Secure Access Service Edge market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Secure Access Service Edge Market, by Component
- Secure Access Service Edge Market, by Offering Type
- Secure Access Service Edge Market, by Deployment Mode
- Secure Access Service Edge Market, by End-Use Industry
- Secure Access Service Edge Market, by Region
- Secure Access Service Edge Market, by Group
- Secure Access Service Edge Market, by Country
- United States Secure Access Service Edge Market
- China Secure Access Service Edge Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 1272 ]
Synthesizing Key Takeaways to Reinforce the Strategic Importance of SASE in Securing Distributed Networks and Cloud Environments
As enterprises strive to secure distributed architectures in an era of hybrid work and cloud proliferation, SASE has emerged as the definitive blueprint for converging networking and security functions. The paradigm’s cornerstone principles-Zero Trust, cloud-native scalability, unified policy orchestration and AI-driven threat resilience-have redefined what it means to provide secure, performant access at the digital edge.
In navigating tariff-induced headwinds and region-specific regulatory nuances, organizations must adopt an agile, vendor-balanced approach. Segmenting strategies according to functional priorities, deployment models and industry regulations enables bespoke SASE architectures that align with both business objectives and compliance frameworks. Moreover, by embedding advanced automation and behavior analytics into these frameworks, enterprises can future-proof their environments against evolving threats and operational challenges.
Ultimately, the power of SASE lies in its holistic ethos: by bringing together network optimization, security enforcement and policy unification under a single umbrella, enterprises gain the visibility and control necessary to thrive in a rapidly shifting digital landscape. As this journey unfolds, the insights and recommendations contained herein will guide decision-makers in architecting resilient, agile and secure networks for years to come.
Engage with Ketan Rohom to Secure Comprehensive SASE Market Intelligence and Drive Informed Decision-Making for Enterprise Leaders
Ready to deepen your understanding of Secure Access Service Edge and leverage the latest market intelligence to strengthen your organization’s security and networking strategies? Connect with Ketan Rohom, Associate Director of Sales & Marketing at 360iResearch, to explore how this comprehensive report can empower your decision-making and drive sustainable competitive advantage. Reach out today to secure your copy and unlock actionable insights tailored to your enterprise needs.

- How big is the Secure Access Service Edge Market?
- What is the Secure Access Service Edge Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




