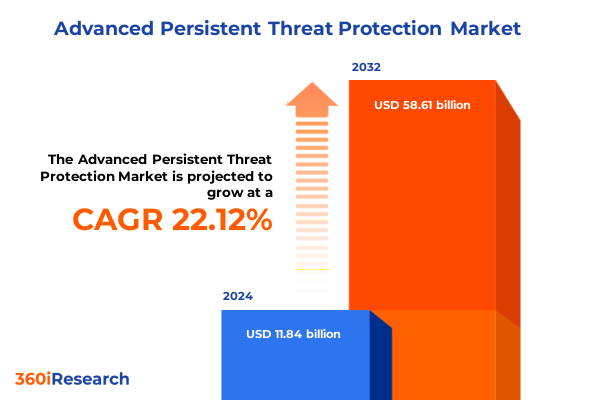
The Advanced Persistent Threat Protection Market size was estimated at USD 14.44 billion in 2025 and expected to reach USD 17.62 billion in 2026, at a CAGR of 22.14% to reach USD 58.61 billion by 2032.
Charting the Evolution of Persistent Threat Protection Strategies Amid Escalating Cyberattacks and Rapid Technological Innovation Impacting Enterprises
Advanced persistent threat protection has become an indispensable cornerstone of modern enterprise cybersecurity as threat actors continuously refine their tactics to evade traditional defenses. These threats are characterized by sustained and targeted campaigns that leverage sophisticated attack vectors often orchestrated by state-sponsored groups or highly organized criminal syndicates. Effective protection strategies now span an array of technologies and services designed to detect concealment techniques correlate cross-domain telemetries and enable rapid response.
Organizations are compelled to reassess legacy security frameworks in favor of integrated detection and response platforms that unify endpoint cloud network and identity data under a single pane of glass. This holistic approach reduces alert fatigue and accelerates incident resolution by providing security teams with cohesive insights and automated playbooks. As digital transformation accelerates workforce mobility and hybrid infrastructures become the norm the imperative for resilient protection paradigms has never been greater.
Emerging Dynamics and Disruptive Innovations Reshaping How Organizations Confront Advanced Persistent Threats in an Increasingly Complex Digital Ecosystem
The advanced persistent threat protection domain is undergoing a profound shift as next-generation technologies and evolving risk profiles converge to reshape defensive perimeters. AI-driven analytics have emerged as a critical enabler for automated threat hunting and anomalous behavior detection proactively identifying indicators of compromise before they escalate into full-scale incidents. Industry leaders are embedding machine learning models within endpoint and network sensors to correlate trillions of security events in real time and deliver contextualized intelligence to security operations centers.
Simultaneously cloud-native design principles are disrupting legacy on-premises architectures by offering elastic scalability and continuous updates that close detection gaps and block mutation-based evasions. Platform consolidation strategies are also gaining momentum as enterprises seek to minimize integration overhead and streamline procurement. By unifying disparate controls such as endpoint detection and response with cloud workload protection and secure email gateways, vendors are reducing operational complexity and enhancing cross-surface threat visibility.
Furthermore, regulatory drivers such as Europe’s NIS2 directive and evolving U.S. data privacy acts are compelling organizations to prioritize advanced threat protections that can demonstrate compliance, reporting and audit readiness. These compliance pressures, combined with reputational concerns and potential financial penalties, have elevated board-level dialogues on investing in resilient security frameworks.
Assessing the Broad Repercussions of Recent United States Tariff Policies on Advanced Persistent Threat Protection Capabilities and Supply Chains
Recent U.S. tariff policies have introduced new variables for cybersecurity vendors and end users alike by placing additional cost pressures on hardware components essential to advanced threat protection solutions. The implementation of a 25% levy on Canadian imports and a baseline 10% tariff on Chinese technology products has driven up the prices of on-premises appliances including firewalls, intrusion detection systems and specialized network security appliances. In response, some vendors have postponed hardware refresh cycles or shifted inventory strategies to mitigate the impact of escalating duties.
Given that many security providers operate hybrid models combining cloud-delivered SaaS offerings with physically deployed sensors, the cumulative effect of these tariffs has rippled across supply chains. Cloud-native vendors have adjusted subscription pricing while managed service providers have recalibrated engagement models to ensure cost predictability. These shifts have heightened the appeal of pure-play software solutions and lightweight agents, reducing dependency on customs-sensitive hardware imports ﹙Kharam, Evgeniy, Cybersecurity Architect and Evangelist﹚.
Complicating the landscape further, recent judicial rulings have challenged the executive branch’s authority to impose broad-based emergency tariffs under the International Emergency Economic Powers Act. On May 28, 2025, the U.S. Court of International Trade ruled that the administration’s “Liberation Day” tariffs exceeded statutory powers, leading to a temporary stay and ongoing appeals that create uncertainty over duty rates. Security organizations are now closely monitoring these legal developments to determine whether imported components will see retroactive duty adjustments or relief in the months ahead.
Uncovering Critical Market Segmentation Insights Spanning Components Deployment Models Organization Sizes Verticals Distribution Channels and Threat Typologies
Effective market segmentation reveals distinct demand drivers and solution preferences across multiple dimensions of the advanced persistent threat protection landscape. When evaluating components, enterprises increasingly allocate budgets to cloud-centric modules such as Cloud Access Security Brokers and Cloud Workload Protection, while also investing in multilayered email defenses including anti-phishing platforms and secure email gateways. Endpoint security remains foundational with a balanced emphasis on antivirus and advanced endpoint detection and response capabilities, and network security continues to evolve around next-generation firewalls and integrated intrusion detection and prevention offerings.
The mode of deployment-whether cloud, hybrid or on-premises-further influences customer purchasing patterns. Purely cloud-native organizations are gravitating toward SaaS-delivered analytics and telemetry consolidation, whereas enterprises with strict data residency and regulatory requirements adopt hybrid architectures or fully on-premises implementations to maintain control over sensitive workloads.
Organization size correlates strongly with both solution scope and purchasing cadence. Large enterprises demand fully managed services and global threat intelligence feeds, medium-sized businesses seek modular platforms that offer balance between customization and cost, and smaller organizations prioritize turnkey deployments with minimal management overhead. Across industry verticals such as banking, healthcare, retail, telecommunications and defense, specific regulatory and operational risk profiles drive bespoke configurations and selected service tiers.
Distribution strategies also vary, with channel partners-including distributors, system integrators and value added resellers-serving as critical conduits for solution bundling and localized managed security expertise, while direct vendor engagements appeal to customers seeking immediate access to product roadmaps and advanced support options. Threat type specialization adds another layer of segmentation, as solutions tailored to combat malware variants like Trojans, viruses and worms coexist alongside dedicated anti-phishing, anti-ransomware and zero-day exploit mitigation toolkits.
This comprehensive research report categorizes the Advanced Persistent Threat Protection market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Organization Size
- Threat Type
- Deployment Mode
- Industry Vertical
- Distribution Channel
Analyzing Distinct Regional Market Dynamics Across the Americas EMEA and Asia Pacific in Advanced Persistent Threat Protection Adoption and Resilience Strategies
Regional market dynamics in advanced persistent threat protection reflect divergent regulatory frameworks, threat landscapes and technology adoption curves. In the Americas, robust investment in cybersecurity is driven by large financial services firms, critical infrastructure operators and government agencies seeking advanced analytics and rapid incident response capabilities. The U.S. government’s emphasis on critical infrastructure resilience and data privacy acts has led to widespread adoption of integrated detection platforms and managed detection and response offerings.
Europe Middle East and Africa exhibit a heightened focus on compliance and centralized security architectures. The implementation of directives such as NIS2 has catalyzed cross-border information sharing initiatives and strengthened incident reporting obligations. This regulatory environment has accelerated deployment of unified threat management systems that provide comprehensive visibility and audit-ready reporting across multinational operations.
Asia-Pacific is marked by a dynamic blend of emerging digital economy players and established enterprises navigating a complex threat vector ecosystem. Rapid digital transformation across industries including telecom, manufacturing and retail has resulted in a proliferation of connected devices and cloud-native workloads. This expansion has elevated demand for scalable cloud workload protection and AI-driven reconnaissance detection capabilities tailored to local threat profiles.
This comprehensive research report examines key regions that drive the evolution of the Advanced Persistent Threat Protection market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Examining Leading Industry Players and Their Strategic Differentiators Driving Innovation in Advanced Persistent Threat Protection Solutions Worldwide
Leading providers in the advanced persistent threat protection market continue to innovate by integrating AI driven threat intelligence with unified analytics platforms. CrowdStrike stands out with its cloud native Falcon offering that leverages a global threat graph and continuous endpoint telemetry to detect novel attack patterns and automate remediation workflows. Palo Alto Networks differentiates through its Cortex XDR platform and AutoFocus threat intelligence module which aggregate indicators from a vast ecosystem of adversary campaigns facilitating precise attribution and faster investigative processes.
Complementing these cloud centric approaches, established network security vendors such as Check Point and Fortinet continue to advance their next generation firewalls with embedded sandboxing, threat emulation and AI powered inspection engines. SentinelOne has gained market traction by offering a slick AI driven endpoint platform that consolidates detection, hunting and rollback capabilities within a lightweight agent architecture. Meanwhile identity security specialists such as SailPoint and Qualys are expanding into adjacent threat hunting and configuration management domains, underscoring the trend toward platform convergence.
This comprehensive research report delivers an in-depth overview of the principal market players in the Advanced Persistent Threat Protection market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- CrowdStrike Holdings, Inc.
- FireEye, Inc.
- Fortinet, Inc.
- International Business Machines Corporation
- McAfee Corp.
- Microsoft Corporation
- Palo Alto Networks, Inc.
- Sophos Group plc
- Trend Micro Incorporated
- Zscaler, Inc.
Strategic Imperatives and Actionable Recommendations to Empower Industry Leaders in Strengthening Enterprise Resilience Against Advanced Persistent Threats
Industry leaders should prioritize the integration of AI and machine learning capabilities within security operations to accelerate detection accuracy and reduce manual investigation workloads. By adopting a unified platform approach that seamlessly blends endpoint, network and cloud telemetry, security teams can eliminate silos and expedite threat triage and containment. It is also critical to invest in threat intelligence sharing partnerships and leverage community driven indicators of compromise to enhance early warning mechanisms against emerging attack campaigns.
Organizations must reassess supply chain resilience by diversifying hardware sourcing strategies and negotiating flexible deployment models that limit exposure to fluctuating tariff regimes. Strengthening third party risk management processes and embedding security requirements within vendor contracts will minimize the risk posed by compromised or counterfeit components.
Finally fostering a culture of continuous learning through red teaming exercises, purple teaming collaborations and formal incident response rehearsals will ensure that both human and technical defenses are battle tested and capable of responding to sophisticated persistent threat scenarios. A proactive posture combined with rigorous process discipline and automated tooling forms the cornerstone of a resilient advanced threat protection strategy.
Outlining a Rigorous Research Methodology to Ensure Comprehensive Analysis of Emerging Trends and Resilient Strategies in Advanced Persistent Threat Protection
This analysis leverages a multi stage research methodology combining both secondary data gathering and primary expert validation. Initial insights were derived from an extensive review of regulatory publications industry whitepapers judicial rulings and vendor disclosures. This desk research provided a foundational understanding of tariff implications technology adoption trends and competitive landscapes.
Subsequently qualitative interviews were conducted with leading cybersecurity architects, security operations center analysts and industry consultants to corroborate emerging themes and validate the practical implications of technological shifts. Data triangulation techniques were applied to reconcile findings across multiple sources, ensuring the research narrative reflects consensus viewpoints and mitigates single source biases.
Finally the aggregated insights were synthesized into thematic categories aligned with industry segmentation dimensions, regional considerations and organizational imperatives. This structured approach ensures comprehensive coverage of advanced persistent threat protection dynamics and actionable relevance for decision makers.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Advanced Persistent Threat Protection market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Advanced Persistent Threat Protection Market, by Component
- Advanced Persistent Threat Protection Market, by Organization Size
- Advanced Persistent Threat Protection Market, by Threat Type
- Advanced Persistent Threat Protection Market, by Deployment Mode
- Advanced Persistent Threat Protection Market, by Industry Vertical
- Advanced Persistent Threat Protection Market, by Distribution Channel
- Advanced Persistent Threat Protection Market, by Region
- Advanced Persistent Threat Protection Market, by Group
- Advanced Persistent Threat Protection Market, by Country
- United States Advanced Persistent Threat Protection Market
- China Advanced Persistent Threat Protection Market
- Competitive Landscape
- List of Figures [Total: 18]
- List of Tables [Total: 2067 ]
Consolidating Key Learnings and Strategic Takeaways to Guide Future Investments in Advanced Persistent Threat Protection Initiatives Across Enterprises
The convergence of AI powered analytics, cloud native platforms and regulatory mandates has fundamentally reshaped how organizations approach advanced persistent threat protection. Vendors and end users alike are navigating cost pressures stemming from tariff policies while balancing the need for real time detection and agile response capabilities. Distinct segmentation profiles, regional priorities and specialized threat vectors underscore the importance of tailored protection frameworks that address both global and local risk drivers.
By examining leading companies, transformative shifts and actionable recommendations, industry stakeholders can make informed decisions to optimize security investments and fortify defenses. A proactive approach to threat intelligence integration, supply chain diversification and continuous validation of security postures ensures sustained resilience against the evolving tactics of persistent threat actors.
Take the Next Step to Secure Your Organization’s Future Engage with Our Associate Director for In-Depth Advanced Persistent Threat Protection Research Report Purchase Options
To explore the full breadth of advanced persistent threat protection market insights and obtain a tailored research report that aligns with your organization’s strategic objectives reach out to Ketan Rohom. As the Associate Director of Sales and Marketing with extensive experience in cybersecurity research analysis Ketan can guide you through the report’s methodologies and findings offering expert advice on how to leverage these insights for maximum impact.
Contacting Ketan will provide you with personalized support to ensure your organization acquires the most relevant data actionable recommendations and comprehensive market understanding needed to stay ahead of evolving threat actors. Secure your competitive advantage by engaging with our specialist and gain immediate access to the in-depth analysis that empowers decisive investment decisions.

- How big is the Advanced Persistent Threat Protection Market?
- What is the Advanced Persistent Threat Protection Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




