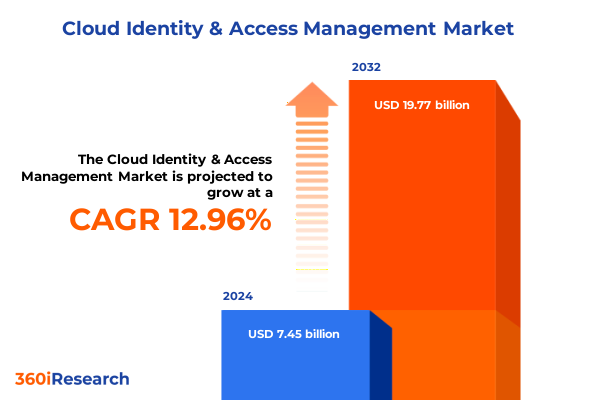
The Cloud Identity & Access Management Market size was estimated at USD 8.40 billion in 2025 and expected to reach USD 9.47 billion in 2026, at a CAGR of 13.01% to reach USD 19.77 billion by 2032.
How Cloud Identity and Access Management Is Redefining Enterprise Security Through Seamless User Verification, Operational Efficiency, and Resilience Against Emerging Threats
Cloud Identity and Access Management (IAM) has emerged as an indispensable pillar of enterprise security in the digital era. Organizations are increasingly relying on IAM solutions to authenticate users, authorize resource access, and maintain compliance mandates while supporting remote workforces. As attackers refine their tactics and regulatory pressures intensify, robust cloud-based IAM frameworks are no longer optional-they are essential to safeguarding critical assets, ensuring operational continuity, and fostering stakeholder trust.
In recent years, advances in cloud architectures have catalyzed significant improvements in scalability, agility, and cost-efficiency. Modern IAM platforms leverage APIs, microservices, and containerization to deliver seamless integration with diverse applications and infrastructure layers. These capabilities empower security teams to orchestrate identity workflows at scale, automate privilege escalations, and centralize policy enforcement. Consequently, enterprises can adapt more rapidly to evolving business requirements and threat landscapes.
Moreover, the rise of hybrid work models and distributed environments has spotlighted the limitations of traditional perimeter-based defenses. As cloud adoption accelerates, identity has become the new control plane for securing resources and verifying user intent. This shift underscores IAM’s strategic importance in enabling secure digital interactions, from employee access to partner collaborations. By adopting cloud-native identity controls, organizations can achieve a unified security stance that aligns with modern operational realities and supports long-term growth.
Transformative Shifts in Cloud Identity Architecture Driven by Zero Trust Models, Artificial Intelligence, and Hybrid Deployment Strategies
The landscape of Cloud IAM is undergoing profound transformation, fueled by converging innovations in zero trust security, artificial intelligence, and hybrid infrastructure models. As organizations transition from legacy, network-centric defenses, they are embracing zero trust principles that validate every access request irrespective of user location or device context. This paradigm shift has elevated identity from a mere user credential to a dynamic risk indicator that informs real-time access decisions.
Simultaneously, artificial intelligence and machine learning capabilities are enhancing threat detection and adaptive authentication within IAM platforms. By analyzing behavioral patterns, transaction histories, and environmental signals, AI-driven engines can identify anomalous access attempts and calibrate authentication requirements accordingly. This fusion of intelligence and automation not only reduces reliance on static credentials but also streamlines user experiences through context-aware verification steps.
Meanwhile, hybrid deployment strategies are enabling organizations to leverage the flexibility of cloud-native IAM services alongside on-premises controls where necessary. Whether integrating with legacy directories, supporting edge computing use cases, or complying with data residency regulations, hybrid IAM architectures offer a balanced approach. They ensure that organizations can extend security controls across multi-cloud and distributed environments while maintaining consistent policies and centralized visibility.
Assessing the Cumulative Impact of 2025 United States Tariffs on Cloud Identity Deployments, Hardware Security Tokens, and Global Supply Chain Economics
In 2025, the United States implemented a series of tariffs targeting imported security hardware components, including smart cards, biometric readers, and hardware security modules commonly used in identity management infrastructures. These measures have exerted upward pressure on procurement costs for on-premises IAM solutions that rely on specialized devices. As a result, many organizations face higher capital expenditures when modernizing or scaling physical access controls.
The cumulative effect of these tariffs has accelerated migration toward software-based authentication mechanisms and cloud-hosted IAM services. Enterprises are finding that virtualized attestations and mobile-based factor options circumvent the need for expensive hardware, mitigating tariff-induced cost escalations. This dynamic has reshaped procurement strategies, prompting a shift in vendor roadmaps toward more adaptable, hardware-agnostic authentication modules.
Furthermore, global supply chain complexities have been magnified as manufacturers of security tokens and cryptographic appliances adjust to tariff regimes. Lead times for critical hardware have lengthened, spurring organizations to reconsider just-in-time inventory models for on-premises deployments. Consequently, cloud IAM adoption has advanced not only as a cost optimization lever but also as a means to ensure continuity of access security during periods of supply volatility.
Revealing Critical Market Segmentation Dynamics in Cloud Identity Solutions Across Component Types, Company Sizes, Deployment Modalities, and Vertical Industries
A comprehensive analysis of Cloud IAM reveals distinct segments that shape solution adoption and service delivery models. Component segmentation differentiates between Services and Solutions. Within Services, organizations choose between Managed Services to outsource daily administration, Professional Services for implementation and training and education, and Support Services for ongoing assistance. Solutions encompass Access Management, Identity Governance, Multi-Factor Authentication, and Privileged Access Management, each addressing specific facets of identity security.
Organizational size further stratifies the market into large enterprises and small to medium enterprises. Large enterprises often pursue end-to-end IAM deployments, integrating multiple modules to meet stringent compliance requirements and to unify identity controls across global operations. In contrast, small and medium enterprises typically prioritize modular, cloud-hosted solutions that deliver rapid time-to-value and reduced infrastructure overhead, enabling them to deploy critical functionalities without extensive internal resources.
Deployment type and end-user vertical also influence IAM strategies. Organizations can opt for cloud-native services to leverage scalability and minimal maintenance, or on-premises installations when regulatory or performance considerations demand local control. Vertically, financial services and government entities emphasize governance and auditability, healthcare and education focus on user experience and privacy, IT and telecom sectors prioritize integration with legacy systems, while manufacturing and retail seek streamlined access for distributed workforces and partner ecosystems.
This comprehensive research report categorizes the Cloud Identity & Access Management market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Deployment Model
- Identity Type
- Pricing Model
- Service Engagement Model
- Industry Vertical
- Organization Size
Analyzing Regional Divergence in Cloud Identity Adoption and Maturity Across Americas, Europe Middle East and Africa, and Asia Pacific Markets
The Americas region leads global Cloud IAM adoption, driven by robust investments in digital transformation, stringent regulatory frameworks, and innovative service provider ecosystems. North America, in particular, showcases mature use cases for zero trust and identity governance, fueled by compliance obligations such as HIPAA, SOX, and regional data protection laws. Latin American markets are rapidly catching up, spurred by cloud-first strategies within financial services and telecommunications sectors.
In Europe, the Middle East, and Africa, regulatory catalysts such as GDPR and emerging data sovereignty mandates have been pivotal in shaping IAM priorities. European enterprises increasingly integrate identity governance capabilities to demonstrate compliance, while Middle Eastern governments adopt federated identity frameworks to harmonize cross-agency access. African markets, although nascent, are benefiting from public cloud initiatives that lower entry barriers and encourage adoption among local enterprises.
Asia-Pacific stands out for its hybrid approach, where strong demand in China, Japan, and Australia is complemented by burgeoning requirements in Southeast Asia and India. Governments across the region are investing in national identity programs, fostering interoperability and trust frameworks that accelerate corporate IAM deployments. Organizations in manufacturing, retail, and education leverage cloud IAM platforms to support digital ecosystems, enhance collaboration, and secure a diverse array of user populations.
This comprehensive research report examines key regions that drive the evolution of the Cloud Identity & Access Management market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Illuminating Competitive Strategies and Innovations of Leading Cloud IAM Providers Shaping Tomorrow’s Security Landscape
Leading providers in the Cloud IAM space are distinguished by their strategic investments in platform extensibility, partner ecosystems, and research-driven innovation. Major players offer comprehensive suites that unify access management, identity governance, multi-factor authentication, and privileged access controls under a singular management plane. Their roadmaps emphasize modular architectures that allow customers to adopt incremental capabilities while maintaining architectural consistency.
Innovation pipelines are centered on embedding artificial intelligence for anomaly detection, enhancing developer experiences through open APIs and SDKs, and deepening integrations with security information and event management platforms. Additionally, strategic acquisitions have consolidated offerings around specialized use cases, such as decentralized identity protocols and blockchain-based credentialing, broadening the competitive landscape.
Competition also hinges on managed service capabilities and global delivery footprints. Enterprises with complex or resource-constrained environments are gravitating toward providers that can deliver turnkey IAM operations, from initial design through continuous monitoring. This trend highlights the growing importance of professional services and support models as differentiators in a market where feature parity is rapidly diminishing.
This comprehensive research report delivers an in-depth overview of the principal market players in the Cloud Identity & Access Management market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Accenture plc
- Amazon Web Services, Inc.
- Avatier Corporation
- Broadcom Inc.
- Cognizant Technology Solutions Corporation
- CyberArk Software Ltd.
- Duo Security by Cisco Systems, Inc.
- Eviden SAS
- Google LLC by Alphabet Inc.
- HID Global Corporation
- IBsolution GmbH
- International Business Machines Corporation
- Microsoft Corporation
- NTT DATA CORPORATION
- Okta, Inc.
- OneLogin, Inc. by One Identity LLC
- Open Text Corporation
- Oracle Corporation
- Ping Identity Holding Corp.
- RSA Security LLC by EMC Corporation
- SailPoint Technologies, Inc.
- SAP SE
- Saviynt, Inc.
- SecureAuth Corporation
- Thales Group
- Zoho Corporation Pvt. Ltd.
Strategic Recommendations for Industry Leaders to Strengthen Cloud Identity Frameworks and Harness Emerging Technology Trends Effectively
Organizations seeking to fortify their identity frameworks should adopt a zero trust architecture as a foundational principle, continuously validating user and device attributes to mitigate insider and external threats. Integrating behavioral analytics and risk-based adaptive authentication will further refine access decisions in real time, ensuring elevated threats trigger appropriate countermeasures without compromising user productivity.
Industry leaders must also prioritize workforce readiness by investing in targeted training and change management programs. Transitioning from legacy identity systems to cloud-native IAM requires upskilling IT teams on API integrations, cloud service configurations, and DevSecOps practices. Engaging in vendor-led certification courses and industry consortiums can accelerate proficiency and foster a security-first mindset across the organization.
Finally, enterprises should cultivate strategic partnerships with managed service providers and technology integrators that offer end-to-end support. By aligning with third-party experts, organizations can accelerate deployment timelines, optimize configurations according to best practices, and maintain continuous compliance posture. This collaborative approach ensures that IAM initiatives deliver measurable value and remain resilient against evolving threat vectors.
Innovative and Rigorous Research Methodology Employed to Illuminate Insights on Cloud Identity and Access Management Market Structures
This research leverages a blend of primary and secondary data collection to ensure depth and rigor. Primary inputs include structured interviews with senior security executives, solution architects, and technology vendors to capture firsthand perspectives on adoption drivers, implementation challenges, and emerging priorities. These insights are complemented by roundtable discussions with industry analysts and thought leaders to validate hypotheses and identify forward-looking trends.
Secondary research encompasses a comprehensive review of publicly available documents, white papers, regulatory guidelines, and peer-reviewed articles. Additionally, proprietary databases tracking vendor press releases, patent filings, and partner certifications were analyzed to corroborate innovation roadmaps and partnership strategies. This triangulation of sources enhances the credibility of the findings and ensures alignment with market realities.
Quantitative data modeling and thematic analysis were applied to synthesize disparate inputs into coherent narratives and actionable insights. Data points were cross-checked across multiple sources to eliminate biases and validate key observations. The methodology emphasizes transparency and reproducibility, enabling stakeholders to trace the research logic and adapt the approach for future studies in adjacent domains.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Cloud Identity & Access Management market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Cloud Identity & Access Management Market, by Component
- Cloud Identity & Access Management Market, by Deployment Model
- Cloud Identity & Access Management Market, by Identity Type
- Cloud Identity & Access Management Market, by Pricing Model
- Cloud Identity & Access Management Market, by Service Engagement Model
- Cloud Identity & Access Management Market, by Industry Vertical
- Cloud Identity & Access Management Market, by Organization Size
- Cloud Identity & Access Management Market, by Region
- Cloud Identity & Access Management Market, by Group
- Cloud Identity & Access Management Market, by Country
- United States Cloud Identity & Access Management Market
- China Cloud Identity & Access Management Market
- Competitive Landscape
- List of Figures [Total: 19]
- List of Tables [Total: 3180 ]
Summarizing the Pivotal Role of Cloud Identity Evolution in Reinforcing Enterprise Security, Operational Agility, and Regulatory Compliance Mandates
The evolution of Cloud Identity and Access Management signifies a paradigm shift in how organizations secure their digital frontiers. From the rise of zero trust frameworks to the integration of artificial intelligence and the impact of geopolitical forces like tariffs, IAM has expanded beyond mere authentication to become a strategic enabler of resilient, compliant, and scalable operations. As enterprises navigate increasingly complex environments, the role of identity as the central security control plane will only intensify.
Segmentation and regional analyses demonstrate that while adoption pathways differ, the overarching imperatives remain consistent: unify identity controls, automate policy enforcement, and deliver frictionless user experiences. Competitive dynamics underscore the importance of innovation, partnerships, and service excellence, reflecting a market where differentiation is driven by the ability to integrate advanced functionalities and deliver comprehensive lifecycle management.
Looking ahead, organizations that embrace proactive identity governance, continuous risk assessment, and collaborative security models will be best positioned to harness digital opportunities while mitigating emerging threats. The interplay between technological evolution, regulatory landscapes, and operational imperatives will define the next chapter of IAM, making strategic alignment and adaptability critical success factors.
Engage with Ketan Rohom to Acquire the Definitive Market Research Report on Cloud Identity and Access Management for Strategic Decision Making
To obtain the comprehensive market research report on Cloud Identity and Access Management and unlock strategic insights for your organization, please engage with Ketan Rohom, the Associate Director of Sales & Marketing at 360iResearch. With expert guidance and a deep understanding of the cloud security ecosystem, Ketan will help tailor the report to your unique business objectives and ensure you receive the timely intelligence needed to make informed decisions. Connect with him today to secure your copy of the definitive analysis, stay ahead of emerging threats, and drive your digital transformation agenda forward.

- How big is the Cloud Identity & Access Management Market?
- What is the Cloud Identity & Access Management Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




