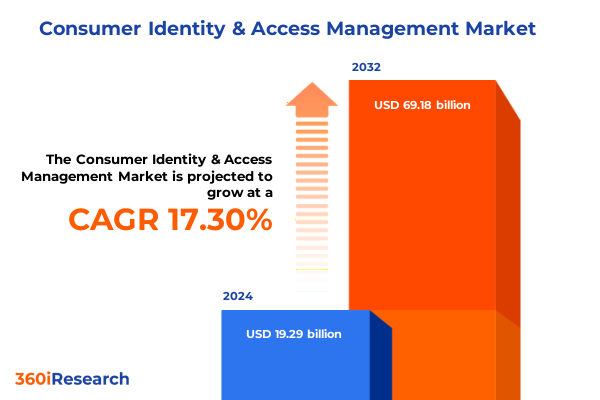
The Consumer Identity & Access Management Market size was estimated at USD 9.99 billion in 2025 and expected to reach USD 11.37 billion in 2026, at a CAGR of 14.87% to reach USD 26.38 billion by 2032.
Introducing the Evolving Landscape of Consumer Identity and Access Management: Key Drivers, Challenges, and Strategic Opportunities Shaping the Future
The introduction to Consumer Identity and Access Management (CIAM) underscores its critical role in today’s digital ecosystem. As enterprises strive to deliver seamless user experiences while safeguarding sensitive information, CIAM solutions have emerged as a foundational element in orchestrating secure interactions between consumers, partners, and workforces. A robust CIAM framework not only facilitates frictionless authentication and authorization but also fosters customer loyalty by enabling personalized engagements. This opening segment lays the groundwork by highlighting the intersection of evolving consumer expectations, stringent regulatory standards, and the intensifying threat landscape that collectively drive the adoption of advanced CIAM strategies.
Transitioning from traditional identity models, modern CIAM platforms leverage adaptive authentication and context-aware decisioning to balance security imperatives with user convenience. Organizations are compelled to reassess legacy infrastructures as digital transformation accelerates across sectors ranging from retail to healthcare. In this context, the introduction explores the strategic imperatives for deploying solutions that encompass both identity management and access management capabilities. By framing the discussion within the broader narrative of digital trust and data privacy, this section sets the stage for a deeper analysis of the transformative shifts, tariff impacts, segmentation frameworks, and regional dynamics that collectively shape the CIAM market.
Exploring the Transformative Shifts Altering the Consumer Identity and Access Management Landscape in the Wake of Digital Acceleration and Regulatory Changes
In recent years, several transformative shifts have fundamentally altered the CIAM landscape. Foremost among these is the migration from on-premises deployments to cloud-native architectures, empowering organizations to scale authentication processes dynamically and respond rapidly to fluctuating user demands. This shift is closely complemented by the emergence of passwordless authentication and risk-based adaptive MFA, which collectively reduce friction without compromising security.
Simultaneously, privacy regulations such as CCPA and GDPR have exerted profound influence on identity governance, compelling businesses to embed consent management and data subject rights into their CIAM frameworks. The proliferation of mobile and API-driven applications has further necessitated robust developer tools and secure API gateways to manage identities at scale. As digital identity ecosystems expand to incorporate social logins and decentralized identity models, interoperability standards like OAuth and OpenID Connect have become indispensable.
These converging trends highlight a market in transition: organizations must realign their CIAM strategies to accommodate emerging authentication paradigms, regulatory constraints, and the imperative for seamless omnichannel experiences. This section delves into these pivotal shifts, illustrating how they collectively reshape security architectures and inform the next generation of identity management solutions.
Assessing the Cumulative Impact of 2025 United States Tariffs on the Consumer Identity and Access Management Market Dynamics and Supply Chain Efficiencies
The imposition of new United States tariffs in 2025 has injected additional complexity into the CIAM market, affecting both hardware procurement and software licensing costs. Components such as specialized authentication devices and on-premises servers have experienced upward price pressures, driving some enterprises to reconsider their deployment strategies in favor of subscription-based cloud services. As a result, cloud adoption has accelerated, enabling organizations to offload capital expenditure while benefiting from predictable operational expenses and continuous feature updates.
Beyond cost implications, the tariffs have prompted CIAM vendors to reevaluate supply chain dependencies and diversify manufacturing footprints. Global service providers are increasingly establishing data center nodes in tariff-neutral regions to mitigate tariff exposure and ensure service continuity. These strategic realignments have implications for data residency, latency, and compliance, especially for multinational enterprises navigating a mosaic of regional regulations.
This section offers a nuanced examination of how the cumulative impact of the 2025 U.S. tariffs is reshaping the CIAM value chain. It underscores the imperative for decision-makers to factor tariff dynamics into vendor selection, infrastructure planning, and total cost of ownership assessments, thereby enabling resilient and cost-effective identity management deployments.
Revealing Actionable Segmentation Insights Illustrating How End User Types, Deployment Modes, Components, and Authentication Approaches Drive Market Differentiation
Adopting a granular segmentation perspective illuminates the diverse requirements and adoption patterns within the CIAM market. When viewed through the lens of end user type, organizations must balance consumer-centric self-service workflows with partner portals that uphold federated identity standards, all while securing internal workforce access against increasingly sophisticated threat vectors. Deployment preferences further divide the market: some entities prioritize the agility and scalability of cloud environments, whereas others maintain on-premises solutions to satisfy stringent data sovereignty mandates.
Breaking down the architecture components reveals that access management capabilities are frequently leveraged to enforce real-time policy evaluation, while identity management modules deliver lifecycle orchestration and governance controls. Enterprises of varying scales exhibit distinct priorities, as large organizations often require intricate role-based access controls and advanced analytics, whereas small and medium enterprises seek easily deployable, low-maintenance solutions. Application contexts introduce additional complexity; API security, mobile authentication, and web-based portals each present unique threat profiles and user experience needs.
Authentication modalities represent another critical axis: multi-factor approaches spanning email-based OTPs, SMS and time-based passcodes, and push notifications coexist with traditional password models and emerging passwordless innovations. Across verticals such as banking, public sector, and retail, the convergence of these segmentation dimensions underscores the importance of customizable CIAM platforms that can adapt to diverse organizational contexts and use-case scenarios.
This comprehensive research report categorizes the Consumer Identity & Access Management market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Authentication Type
- Application Type
- End User Type
- Deployment Mode
- Enterprise Size
- Industry Vertical
Uncovering Critical Regional Insights Across Americas, Europe Middle East Africa and Asia Pacific to Navigate Diverse Consumer Identity Management Demands
Regional analyses demonstrate how market maturity and regulatory landscapes influence CIAM adoption. In the Americas, organizations benefit from a mature cloud infrastructure and advanced digital payment ecosystems that accelerate the deployment of modern identity services. The prevalence of stringent privacy legislation in several U.S. states has also driven demand for consent management and identity governance features, compelling local vendors to embed robust compliance tools into their offerings.
Conversely, Europe, the Middle East, and Africa exhibit a more heterogeneous tapestry of requirements. GDPR remains the cornerstone for data protection across Europe, shaping vendor roadmaps to prioritize data subject access requests and breach notification workflows. In parts of the Middle East and Africa, digital transformation initiatives are intensifying, with governments spearheading national identity programs and encouraging private sector adoption of CIAM for e-government services.
In Asia-Pacific, rapid digitization across industries such as e-commerce, telecom, and public services has driven significant CIAM uptake. Regional governments are enhancing regulatory frameworks to address cybersecurity concerns, while consumer preferences for mobile and social logins have spurred investments in frictionless authentication. This section distills these regional dynamics, showcasing how geographic nuances inform strategic positioning and deployment considerations for global and local vendors alike.
This comprehensive research report examines key regions that drive the evolution of the Consumer Identity & Access Management market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Market Leaders and Innovators Shaping the Future of Consumer Identity and Access Management through Differentiated Offerings and Strategic Partnerships
A review of leading CIAM providers highlights differentiated strategies that shape competitive dynamics. Some vendors have focused on building comprehensive platforms that integrate identity orchestration, risk analytics, and consent management, thereby offering end-to-end solutions for complex enterprise environments. Others have carved niches around developer-friendly APIs and SDKs, empowering digital-centric organizations to embed advanced authentication flows directly into their applications.
Strategic partnerships and acquisitions have further consolidated market positions, with several key players absorbing specialized authentication startups to bolster passwordless and adaptive MFA capabilities. Investments in artificial intelligence and machine learning have enabled real-time fraud detection and user behavior analytics, delivering contextual security while preserving user experience. Vendor roadmaps also reflect an increasing emphasis on decentralized and standards-based identity models, signaling a gradual shift toward user-centric control of personal data.
This section examines how these competitive approaches translate into differentiated value propositions for end users. It offers insights into vendor strengths, integration flexibility, and innovation trajectories, providing decision-makers with a nuanced understanding of the landscape and the strategic fit of each solution relative to specific organizational priorities.
This comprehensive research report delivers an in-depth overview of the principal market players in the Consumer Identity & Access Management market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Amazon Web Services, Inc.
- ForgeRock, Inc.
- Google LLC
- International Business Machines Corporation
- Microsoft Corporation
- Okta, Inc.
- Oracle Corporation
- Ping Identity Holding Corp.
- Salesforce, Inc.
- SAP SE
Strategic Actionable Recommendations for Industry Leaders to Strengthen Consumer Trust, Enhance Security, and Accelerate Adoption of Next Generation Access Management Solutions
Industry leaders aspiring to harness the full potential of CIAM should prioritize the convergence of security, compliance, and customer experience. The first actionable step involves adopting adaptive authentication frameworks that dynamically assess risk signals and tailor verification flows accordingly. Concurrently, embedding consent management and data privacy controls directly into user journeys can streamline regulatory adherence while maintaining transparency.
Organizations should also consider leveraging cloud-native CIAM services to accelerate deployment timelines and optimize infrastructure costs. By selecting providers with established global footprints, enterprises can address data residency requirements and improve latency for international user bases. In parallel, creating cross-functional governance committees that include stakeholders from IT, legal, and marketing can ensure that identity initiatives align with broader strategic objectives.
Finally, cultivating a culture of continuous improvement through regular security audits and user experience testing will help organizations stay ahead of emerging threats and evolving consumer expectations. Gamifying security awareness programs and integrating feedback loops into design processes can foster greater adoption and drive sustained engagement. Together, these recommendations offer a roadmap for elevating identity and access management from a technical function to a strategic enabler of business growth.
Methodological Framework Detailing the Robust Qualitative and Quantitative Approaches Used to Generate Comprehensive Consumer Identity and Access Management Market Analysis
The research methodology underpinning this analysis combines rigorous qualitative and quantitative approaches to deliver comprehensive market insights. Primary research comprised in-depth interviews with senior executives, technical architects, and cybersecurity specialists across diverse industry verticals. These engagements provided first-hand perspectives on deployment challenges, technology priorities, and vendor selection criteria.
Secondary research involved systematic review of industry publications, regulatory documents, and technical whitepapers to contextualize primary findings within the broader CIAM ecosystem. Data triangulation techniques were employed to validate key trends and reconcile any discrepancies between public domain data and expert insights. Case studies highlighting successful CIAM implementations further enriched the analysis by illustrating real-world applications and measurable business outcomes.
Statistical modelling and thematic analysis enabled the identification of segmentation patterns and regional nuances, ensuring that the report captures both macro-level dynamics and micro-level variations. Robust quality assurance protocols, including peer reviews and methodological audits, were implemented throughout the research process to uphold the credibility and reliability of the findings.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Consumer Identity & Access Management market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Consumer Identity & Access Management Market, by Component
- Consumer Identity & Access Management Market, by Authentication Type
- Consumer Identity & Access Management Market, by Application Type
- Consumer Identity & Access Management Market, by End User Type
- Consumer Identity & Access Management Market, by Deployment Mode
- Consumer Identity & Access Management Market, by Enterprise Size
- Consumer Identity & Access Management Market, by Industry Vertical
- Consumer Identity & Access Management Market, by Region
- Consumer Identity & Access Management Market, by Group
- Consumer Identity & Access Management Market, by Country
- United States Consumer Identity & Access Management Market
- China Consumer Identity & Access Management Market
- Competitive Landscape
- List of Figures [Total: 19]
- List of Tables [Total: 1431 ]
Concluding Synthesis of the Consumer Identity and Access Management Sector Emphasizing Key Takeaways and the Imperative for Continued Strategic Focus
This concluding segment synthesizes the critical themes that have emerged throughout the report, reaffirming the strategic significance of CIAM in enabling secure, seamless digital interactions. The convergence of adaptive authentication, consent orchestration, and cloud scalability emerges as the cornerstone of next-generation identity frameworks. Organizations that successfully integrate these elements are poised to deliver superior user experiences while mitigating risk in an increasingly complex threat landscape.
Regional and segmentation insights underscore that there is no one-size-fits-all solution; rather, effective CIAM strategies must be tailored to specific end user profiles, deployment preferences, and regulatory environments. As tariffs and supply chain considerations introduce new cost variables, decision-makers must exercise diligence in vendor evaluation and infrastructure planning.
In essence, the future of CIAM hinges on the ability to balance evolving security mandates with user demands for simplicity and speed. By internalizing the recommendations and insights presented in this report, organizations can chart a clear path toward resilient, customer-centric identity ecosystems that support long-term digital growth.
Take Immediate Next Steps to Secure Your Competitive Advantage in Consumer Identity and Access Management by Engaging with Ketan Rohom to Acquire the Full Market Research Report
Unlock essential insights and secure your competitive edge in Consumer Identity and Access Management by engaging with Ketan Rohom to access the comprehensive market research report tailored for strategic decision-making. This report offers unparalleled depth into the evolving challenges and opportunities shaping identity and access management across industries. By partnering directly with the Associate Director of Sales & Marketing, you will receive personalized guidance on leveraging the data to optimize your security posture, enhance customer experiences, and accelerate digital transformation initiatives. Reach out now to obtain your copy and discover how these findings can empower your organization to mitigate emerging risks, capitalize on technological advancements, and drive sustainable growth. Don’t miss this opportunity to transform your strategic planning with actionable intelligence curated by industry experts.

- How big is the Consumer Identity & Access Management Market?
- What is the Consumer Identity & Access Management Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




