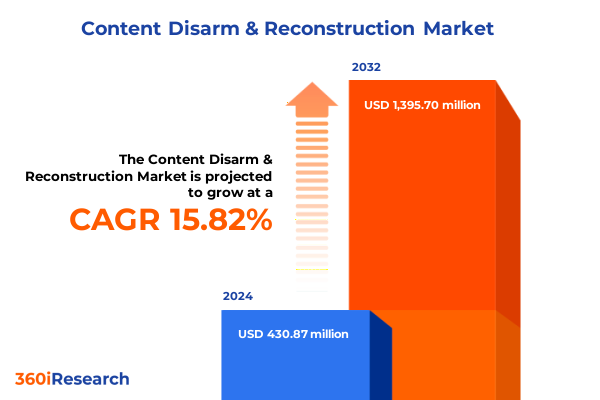
The Content Disarm & Reconstruction Market size was estimated at USD 496.14 million in 2025 and expected to reach USD 572.10 million in 2026, at a CAGR of 15.92% to reach USD 1,395.70 million by 2032.
Driving Unprecedented Protection through Content Disarm and Reconstruction with Emphasis on Data Integrity and Fortified Cyber Resilience
Content Disarm and Reconstruction (CDR) has emerged as a cornerstone technology for organizations seeking to neutralize file-based threats without reliance on traditional signature or heuristic detection. By systematically deconstructing incoming files, stripping potentially malicious elements, and then rebuilding them into safe, clean versions, CDR eliminates zero-day exploits and embedded malware that often bypass conventional defenses. As cyber threats grow more sophisticated, enterprises across sectors increasingly recognize that proactive removal of attack vectors at the point of entry offers a more robust safeguard than retrospective detection and remediation. This section introduces the core principles and strategic necessity of CDR within a modern, layered cybersecurity framework.
As enterprises embrace digital transformation and expand data collaboration beyond traditional network perimeters, the risk surface for file-based attacks widens. Remote work initiatives, cloud-based file sharing, and reliance on third-party content sources heighten exposure to weaponized documents, malicious attachments, and compromised multimedia. Against this backdrop, CDR serves as a pivotal preventive control that integrates seamlessly with existing security stacks, delivering sanitized content without disrupting user workflows. Moreover, the ability to tailor reconstruction policies according to file types and organizational risk appetite ensures that the balance between security and usability remains optimized. Looking ahead, the role of CDR is set to evolve further, incorporating machine learning for context-aware sanitization and deeper integration with zero trust paradigms to secure the content supply chain.
Navigating the New Frontier of Evolving Threats and Distributed Workflows with Advanced Content Disarmament
The shifting cybersecurity landscape is characterized by a convergence of technological advances, evolving threat tactics, and changing organizational requirements. As artificial intelligence and machine learning become embedded in both offensive cyber toolkits and defensive architectures, the arms race between attackers and defenders escalates. In the context of CDR, this evolution translates into continuous refinement of algorithms that identify and excise malicious payloads while preserving file functionality. Simultaneously, the proliferation of cloud-native operations and hybrid work environments demands that CDR solutions deliver low-latency processing at scale, whether deployed on-premise or via SaaS offerings in distributed data centers.
Moreover, threat actors have diversified their tactics, increasingly incorporating social engineering lures that exploit trust in collaborative platforms and file-sharing services. In response, CDR solutions are adapting to scan a broader spectrum of file formats such as complex multimedia, containerized documents, and script-enabled materials. The integration of behavior-based analytics and sandboxing capabilities enhances the detection of polymorphic threats that intentionally evade static sanitization rules. Consequently, enterprises are witnessing a transformative shift toward unified content security platforms that combine disarmament, reconstruction, sandbox analysis, and threat intelligence feeds, enabling real-time orchestration of content inspection workflows across multiple channels.
Assessing the Multi-Dimensional Consequences of the 2025 U.S. Tariff Adjustments on Content Security Infrastructure
In 2025, the United States implemented a series of updated tariffs affecting the import of hardware and software security components, with ripple effects throughout the cybersecurity supply chain. As suppliers adjust pricing to accommodate increased duties on specialized appliances and OEM modules, end customers face higher capital expenditures for deploying on-premise CDR infrastructure. Cloud-based service providers have also felt the impact, passing through marginal cost increases for managed content safety offerings, which has led many to reassess their procurement strategies.
Nonetheless, these tariff-driven cost pressures have also stimulated innovation among domestic vendors, who are accelerating development of software-defined CDR capabilities that minimize reliance on imported hardware. Through partnerships with federal research agencies and strategic investments in localized manufacturing, several solution providers have begun to offer hybrid appliances that leverage commodity servers with detachable security modules produced domestically. Consequently, organizations have more flexible deployment pathways, selecting between fully managed cloud services, localized on-premise systems, or hybrid models that best align with budget constraints and regulatory compliance mandates.
Unveiling Critical Segmentation Dynamics Highlighting Component Choices File Types Deployment Models and Sector-Specific Applications
The market’s segmentation across component categories reveals distinct preferences between solution and service offerings. Service customers prioritize managed services when they require continuous monitoring and expert oversight, whereas enterprises seeking one-time integration projects gravitate toward professional services, particularly consulting engagements to design tailored sanitization policies followed by deployment and integration phases, supplemented by training and support to operationalize the solution. Meanwhile, organizations with well-defined security teams increasingly invest directly in standalone CDR platforms or broader integrated security suites that embed disarmament within unified threat management.
File type segmentation highlights that document-based content-such as PDFs and Office files-remains a primary focus due to the high frequency of these formats in email and collaboration tools. Email attachments account for a significant portion of inbound malicious payloads, prompting security teams to enforce stringent reconstruction workflows. Executables and script-enabled files demand deeper inspection logic to ensure that macro-based exploits and embedded code snippets are fully neutralized. Image files and web content necessitate specialized sanitization to remove hidden scripts and metadata-based threats without degrading user experience.
The choice of deployment model continues to bifurcate between cloud and on-premise environments. Enterprises with stringent data sovereignty requirements or high-throughput needs often opt for on-premise appliances, while distributed and remote-centric organizations favor cloud-hosted CDR services for scalability and ease of updates. When examining organization size, large enterprises leverage a combination of internal professional services and managed service subscriptions to maintain comprehensive coverage, whereas small and medium enterprises tend toward bundled solution offerings with built-in onboarding support.
Application-specific usage illustrates that content collaboration and sharing platforms integrate CDR at multiple touchpoints-particularly within zero trust architectures where file transfer security and email security converge. Document management systems incorporate embedded reconstruction APIs to sanitize archived records, while web security gateways deploy inline CDR for downloaded content. Ultimately, organizations across BFSI, education, energy and utilities, government and defense, healthcare and life sciences, IT and telecom, manufacturing, and retail and e-commerce each calibrate their CDR strategies according to regulatory pressures, data sensitivity requirements, and threat landscapes.
This comprehensive research report categorizes the Content Disarm & Reconstruction market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- File Type
- Deployment Model
- Organization Size
- Application
- End-User
Mapping Regional Momentum in Content Disarm and Reconstruction Amidst Varied Regulatory and Technological Landscapes
When examining regional trends, the Americas lead in both technological innovation and regulatory alignment around data protection. North American financial institutions and government entities spearhead adoption of CDR as part of broad zero trust initiatives, while Latin American enterprises, contending with a surge in ransomware and advanced persistent threat campaigns, are ramping up investments in cloud-based sanitization services. Across the continent, collaboration between public and private sectors has accelerated standardization of content security guidelines, fostering rapid integration of CDR within national cybersecurity frameworks.
In Europe, Middle East, and Africa, a diverse mosaic of regulatory regimes-from the European Union’s stringent data governance mandates to emerging cybersecurity strategies in the Gulf and South Africa-drives heterogeneous adoption rates. The EU’s emphasis on data integrity and privacy by design has led many organizations to embed CDR directly into content collaboration suites, whereas Middle Eastern governments invest heavily in localized on-premise solutions to meet data residency requirements. In Africa, the growing digital economy among financial services and telecommunications players fuels demand for managed CDR offerings that address constrained internal security resources.
Asia-Pacific continues to showcase rapid growth in cloud-native CDR deployments, driven by technology-forward markets such as Singapore, Australia, and Japan, where leading enterprises incorporate AI-enhanced sanitization into their broader security orchestration. Meanwhile, emerging economies including India and Indonesia are balancing cost-sensitive procurement with the need to mitigate sophisticated state-sponsored and hacktivist campaigns targeting critical infrastructure. As regional interoperability standards evolve, multinational organizations must architect CDR workflows that harmonize with varied compliance obligations and latency considerations across geographies.
This comprehensive research report examines key regions that drive the evolution of the Content Disarm & Reconstruction market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Dissecting Competitive Dynamics and Partnership Innovations Driving the Content Disarm and Reconstruction Market
The competitive landscape is populated by established cybersecurity vendors and specialized pure-play CDR providers, each adopting distinct strategies to capture market share. Leading endpoint security and unified threat management providers are embedding disarmament capabilities into broader platform suites, leveraging pre-existing customer relationships to cross-sell integrated modules that offer centralized policy management. Conversely, niche CDR specialists focus on deep file inspection expertise, investing in advanced reconstruction algorithms and extensive file format libraries to differentiate on efficacy and performance.
Strategic partnerships have emerged as a key tactic for both categories of vendors: alliances between cloud service providers and pure-play CDR companies enable seamless API-based integration for enterprise customers, while collaborations with systems integrators and value-added resellers expand reach into vertical markets such as healthcare and BFSI. Furthermore, mergers and acquisitions have accelerated, with larger cybersecurity conglomerates acquiring boutique CDR startups to bolster their content security portfolios, and specialized CDR firms partnering with threat intelligence vendors to enhance contextual awareness during file sanitization.
Innovation remains a critical battleground, as vendors race to incorporate machine learning for predictive threat identification, behavior analytics for zero-day file anomalies, and sandbox-based validation engines. Performance differentiation through parallelized processing, GPU acceleration, and edge-based microservices positions certain players to address high-volume environments like financial trading floors and media production workflows. Ultimately, success hinges on the ability to deliver seamless user experiences while maintaining robust, policy-driven security controls across complex, distributed ecosystems.
This comprehensive research report delivers an in-depth overview of the principal market players in the Content Disarm & Reconstruction market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Deep Secure Ltd.
- Everfox LLC
- Fortinet, Inc.
- Gatefy
- Glasswall Solutions Limited
- Jiranji Security Co., Ltd.
- OPSWAT Inc.
- Palo Alto Networks, Inc.
- Peraton Inc.
- Re-Sec Technologies Ltd.
- Sasa Software
- SoftCamp Co., Ltd.
- Trend Micro Incorporated
- Votiro Cybersec Ltd.
- YazamTech
- Zscaler, Inc.
Leveraging Zero Trust Alignment and Hybrid Deployment Tactics for Elevated Content Security Efficacy
Industry leaders can elevate their cybersecurity posture by integrating content disarmament into overarching zero trust frameworks. This involves aligning CDR policies with identity and access management controls to ensure only authenticated, authorized users can request reconstructed files. Organizations should also conduct periodic policy reviews to accommodate new file formats and emerging exploit techniques, thereby maintaining comprehensive coverage. Collaboration between security operations and application development teams can streamline the integration of CDR APIs into existing DevSecOps pipelines, enabling early sanitization of content during build and deployment stages.
To maximize return on security investments, CISOs should evaluate hybrid deployment models that combine on-premise appliances for high-throughput, latency-sensitive use cases with cloud-based services for branch offices and remote employees. Establishing robust service-level agreements with managed service providers ensures consistent uptime and performance, while embedding CDR within security incident and event management platforms enhances centralized monitoring and automated response. Furthermore, organizations must invest in user awareness programs that explain the value of content sanitization, fostering a security culture that balances risk mitigation with operational efficiency.
Finally, industry leaders are encouraged to participate in standards bodies and threat intelligence sharing communities to stay abreast of evolving content-based exploit trends. By contributing anonymized telemetry and reconstruction efficacy data, companies can collaboratively refine best practices and influence interoperability standards, ultimately reducing overall costs and improving collective defense against malicious file campaigns.
Ensuring Reliability through a Comprehensive Mixed Methodology Integrating Primary Interviews Secondary Analysis and Quantitative Validation
This research employs a mixed-methodology approach combining primary and secondary data sources to ensure validity and reliability of insights. Primary research involved in-depth interviews with cybersecurity practitioners, solution architects, and senior IT decision-makers across multiple industries, capturing perspectives on CDR use cases, deployment challenges, and strategic priorities. A series of workshops and questionnaires facilitated qualitative feedback on vendor performance criteria and emerging threat vectors.
Secondary research encompassed analysis of industry publications, regulatory frameworks, vendor white papers, and technical specifications, supplemented by review of publicly available threat intelligence reports. Data triangulation methods were utilized to cross-verify reported trends and reconcile disparate viewpoints. Vendor profiling was conducted through evaluation of solution capabilities, patent filings, and platform interoperability, while competitive benchmarking assessed partnership ecosystems, go-to-market strategies, and innovation roadmaps.
Quantitative data points regarding adoption patterns and perceived priorities were aggregated through an online survey of security professionals, with statistical analysis applied to highlight significant correlations between organizational characteristics and CDR investment drivers. Rigorous validation stages, including peer review by independent cybersecurity analysts, underpin the robustness of the findings and recommendations presented in this report.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Content Disarm & Reconstruction market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Content Disarm & Reconstruction Market, by Component
- Content Disarm & Reconstruction Market, by File Type
- Content Disarm & Reconstruction Market, by Deployment Model
- Content Disarm & Reconstruction Market, by Organization Size
- Content Disarm & Reconstruction Market, by Application
- Content Disarm & Reconstruction Market, by End-User
- Content Disarm & Reconstruction Market, by Region
- Content Disarm & Reconstruction Market, by Group
- Content Disarm & Reconstruction Market, by Country
- United States Content Disarm & Reconstruction Market
- China Content Disarm & Reconstruction Market
- Competitive Landscape
- List of Figures [Total: 18]
- List of Tables [Total: 1590 ]
Consolidating Insights on Preventive File-Based Controls and Strategic Integration for Unmatched Cyber Resilience
Throughout this report, the essential role of Content Disarm and Reconstruction in defending against file-based threats has been demonstrated through examination of evolving threat landscapes, tariff-induced supply chain shifts, and detailed segmentation and regional analyses. As organizations grapple with increasingly sophisticated exploits, CDR emerges as an indispensable preventive control that complements detection-centric defenses and aligns with zero trust principles. By understanding the nuanced requirements across components, file types, deployment models, organization sizes, applications, and end-user industries, security leaders are equipped with a holistic view of CDR strategies.
Regional disparities underscore the importance of tailoring CDR implementations to regulatory requirements and infrastructure considerations, while competitive dynamics highlight the value of vendor partnerships and technological innovation. Actionable recommendations for hybrid deployments, policy governance, DevSecOps integration, and community engagement offer clear paths for elevating content security postures. The methodological rigor of this research ensures that its insights are both practical and forward-looking.
In conclusion, enterprises that proactively integrate content disarmament into broader cybersecurity and data sovereignty initiatives will achieve greater resilience against file-based attacks, preserve user experience, and foster a security-first organizational culture. The strategic imperatives and best practices outlined herein provide a roadmap for navigating the complex CDR ecosystem with confidence.
Connect with Ketan Rohom to Secure Your Comprehensive Content Disarm and Reconstruction Market Report for Unparalleled Cybersecurity Intelligence
To explore the comprehensive Content Disarm and Reconstruction market research report and uncover actionable intelligence tailored to your organization’s security and compliance objectives, reach out directly to Ketan Rohom, Associate Director of Sales & Marketing. Engage with Ketan to discuss how this report aligns with your strategic priorities, gain clarity on specific industry challenges, and receive a personalized demonstration of the insights that can drive your next-generation cybersecurity initiatives. Elevate your decision-making with targeted data on evolving threats, deployment considerations, and best practices. Contact Ketan to secure your copy of the full report and position your enterprise at the forefront of secure content delivery and zero-trust implementation

- How big is the Content Disarm & Reconstruction Market?
- What is the Content Disarm & Reconstruction Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




