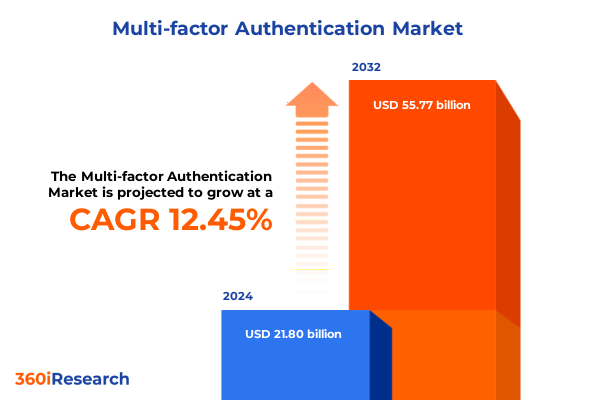
The Multi-factor Authentication Market size was estimated at USD 24.55 billion in 2025 and expected to reach USD 27.36 billion in 2026, at a CAGR of 12.43% to reach USD 55.77 billion by 2032.
Unveiling the critical role of multi-factor authentication in fortifying digital perimeters against escalating threats and emerging regulatory demands
As organizations grapple with an evolving digital terrain marked by sophisticated cyber threats and stringent regulatory landscapes, multi-factor authentication has emerged as an indispensable pillar of modern security strategies. The foundational significance of MFA lies in its ability to transcend traditional password-only paradigms by integrating multiple verifiable factors, thereby imbuing access controls with layers of assurance. Against a backdrop of accelerating cloud adoption and remote work proliferation, enterprises and public institutions alike are recalibrating their identity management approaches to fortify digital perimeters and safeguard sensitive information.
In recent years, the convergence of digital transformation initiatives and relentless threat actor innovation has compelled security leaders to reevaluate legacy authentication mechanisms. This has spurred a migration toward solutions that combine knowledge-based credentials with possession-based tokens, biometric identifiers, and contextual risk analysis. By leveraging a spectrum of factors, from time-based one-time passcodes to advanced behavioural analytics, MFA architectures now deliver adaptive risk assessments that can dynamically adjust authentication requirements in real time.
Moreover, heightened regulatory mandates-spanning financial services directives to data protection frameworks-have intensified the impetus for robust authentication controls. Organizations are no longer afforded the luxury of deferred security investments; instead, they must proactively embed MFA into critical workflows, including privileged account management, remote access gateways, and high-risk transaction validations. This introduction lays the groundwork for understanding how the multi-factor authentication landscape has evolved and why it constitutes a strategic imperative for entities committed to resilience and compliance.
Exploring how rapid technological advances and evolving threat vectors are reshaping authentication paradigms into seamless, adaptive, and user-centric security solutions
The authentication landscape is undergoing a profound transformation fueled by technological breakthroughs and shifting user expectations. Traditional static password methodologies are being supplanted by seamless, adaptive frameworks that reconcile stringent security requirements with the demand for frictionless access. As organizations strive to uphold stringent protections without compromising user productivity, they are increasingly embracing passwordless modalities, which leverage cryptographic key pairs and biometric validation to eliminate reliance on memorized secrets.
Parallel to the rise of passwordless strategies, risk-based authentication models have garnered traction by contextualizing each login attempt. These solutions analyze a confluence of parameters-device posture, geolocation, behavioural patterns, and network reputation-to assign trust scores in real time. Such dynamic approaches enable targeted escalation of authentication strength only when anomalies are detected, thereby optimizing user experience without sacrificing security.
In addition, the integration of artificial intelligence and machine learning has catalyzed the development of predictive threat detection within authentication flows. By continuously learning from authentication telemetry, these systems can preempt sophisticated attack vectors such as credential stuffing and man-in-the-middle exploits. Consequently, security teams are empowered with proactive alerts and automated mitigation workflows, ensuring that adaptive authentication paradigms evolve in lockstep with emergent risks.
Furthermore, the adoption of open standards like FIDO2 has galvanized interoperability across devices and platforms, fostering an ecosystem in which hardware authenticators, mobile authenticators, and software-based tokens coexist harmoniously. This standardization accelerates enterprise deployments and streamlines end-user experiences, marking a pivotal shift toward user-centric authentication architectures that can scale across diverse digital environments.
Assessing how recent United States import tariffs introduced in 2025 are redefining hardware token costs and global supply chain logistics for authentication solutions
The introduction of new United States import tariffs in 2025 has reverberated across global supply chains for hardware security tokens, prompting organizations to reevaluate cost structures and procurement strategies. Tariffs levied on electronic components and manufacturing equipment have incrementally driven up the landed cost of key-fob authenticators and smartcard modules, leading many security teams to explore alternative deployment models that reduce dependency on imported hardware.
As a direct consequence, software-based authentication factors have gained renewed prominence. By migrating critical components to cloud-native environments and mobile applications, enterprises can circumvent escalating import duties while maintaining the integrity of possession-based authentication. This shift has accelerated the adoption of mobile push notifications, time-based one-time passwords delivered via secure applications, and certificate-based credentials delivered through device management frameworks.
Moreover, hardware token vendors have responded by diversifying their manufacturing footprints, establishing assembly lines closer to end markets, and negotiating revised supply agreements to mitigate tariff impacts. These strategic adjustments have engendered more resilient procurement pipelines, though organizations are advised to conduct rigorous vendor due diligence to ensure continuity of supply and compliance with international trade regulations.
In parallel, regional distributors and systems integrators have begun factoring tariff-induced cost fluctuations into their service offerings. This has fostered an environment in which hybrid authentication deployments-combining on-premise hardware tokens for high-security use cases with cloud-based factors for scalable user access-have emerged as a best practice. The cumulative impact of the 2025 tariff changes underscores the critical need for adaptable authentication architectures that can seamlessly integrate both software and hardware components in response to shifting economic conditions.
Diving into segmentation dynamics that reveal distinctive authentication preferences shaped by organizational demand, deployment modalities, and sectoral requirements
Segmentation insights reveal that authentication requirements vary significantly based on the factors employed, organizational scale, deployment preferences, and industry verticals. In environments where high-assurance access is imperative, solutions that incorporate five-factor authentication predominate, leveraging a combination of knowledge, possession, inherence, location, and time-based attributes. Conversely, segments seeking a balance between security and usability often deploy three-factor or two-factor authentication, optimizing workflows for broad user adoption without compromising baseline protection.
Organizational size further shapes authentication strategies. Large enterprises frequently invest in comprehensive identity orchestration platforms that unify multiple authentication factors under a centralized management console. In contrast, smaller and medium-sized enterprises tend toward streamlined solutions that prioritize ease of deployment and cost-effectiveness, often selecting cloud-delivered authentication services that abstract infrastructure management.
Deployment mode exerts its own influence on solution architecture. Cloud-based authentication offerings are lauded for their rapid scalability and automatic updates, making them particularly attractive to organizations undergoing digital transformation initiatives. Meanwhile, on-premise modalities remain prevalent in sectors where strict data sovereignty and legacy system integration are non-negotiable, ensuring that authentication workflows comply with internal governance policies.
Vertical industry dynamics also govern factor utilization and solution design. Financial institutions and government agencies prioritize multi-layered, cryptographically secure mechanisms to meet regulatory mandates, while healthcare entities focus on balancing data privacy requirements with clinician efficiency. Information technology and telecommunications companies often serve as early adopters of advanced biometric methods, while retail organizations concentrate on frictionless consumer experiences to support high-volume transactional environments.
This comprehensive research report categorizes the Multi-factor Authentication market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Model
- Deployment Mode
- Organization Size
- Vertical
Highlighting regional authentication adoption patterns driven by regulatory environments, digital maturity, and evolving threat landscapes across global markets
Regional market dynamics are heavily influenced by distinct regulatory frameworks, technological capacities, and threat landscapes. In the Americas, stringent data privacy regulations and high-profile breach incidents have galvanized organizations to adopt multi-factor authentication as a foundational security control. This has been particularly evident in North America, where enterprise-led digital transformation initiatives and widespread cloud migration have accelerated the replacement of single-factor methods with adaptive, multi-layered authentication solutions.
Across Europe, Middle East & Africa, compliance with regulations such as the General Data Protection Regulation and local cybersecurity mandates has driven broad-based adoption of multi-factor authentication, especially within financial services and government verticals. Enterprises in the EMEA region demonstrate a strong preference for solutions that support hardware-based tokens alongside software authenticators to satisfy both security and data sovereignty requirements.
In the Asia-Pacific region, rapid digitalization, expanding e-commerce sectors, and mobile-first consumer behaviors have fueled demand for flexible authentication frameworks. Organizations in APAC are increasingly deploying biometric and contextual authentication methods to manage high-volume user access while addressing regulatory pressures related to data residency and privacy.
Furthermore, each region exhibits unique supply chain considerations influenced by tariff regimes, manufacturing hubs, and vendor partnerships. As a result, enterprises operating across multiple geographies are adopting hybrid approaches that blend cloud-based authentication services with localized hardware deployments to ensure consistent user experiences and regulatory compliance across all jurisdictions.
This comprehensive research report examines key regions that drive the evolution of the Multi-factor Authentication market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling leading solution providers innovating through strategic partnerships, advanced biometrics, and cloud-native architectures to dominate the authentication space
A cadre of leading vendors is driving innovation in the authentication ecosystem through strategic technology partnerships, platform integrations, and continuous feature enhancements. Prominent cloud-native identity providers have distinguished themselves by embedding biometric verification and risk-based analytics directly into their authentication workflows, streamlining deployment for global customers.
Meanwhile, established security technology firms have broadened their portfolios to include identity orchestration capabilities, enabling seamless federation across on-premise directories, cloud services, and third-party applications. This consolidation of identity and access management functions is positioning these vendors as one-stop shops for comprehensive authentication solutions.
Collaborations between hardware token manufacturers and mobile operating system providers have also emerged as a notable trend, leveraging secure element technology and device attestation to fortify possession-based factors. These partnerships facilitate the integration of hardware-backed credentials into enterprise mobility management frameworks, reducing friction for end users.
Furthermore, specialist authentication startups are carving out niches in areas such as behavioural biometrics, continuous identity verification, and passwordless passport systems. By focusing on next-generation use cases and providing developer-centric APIs, these agile competitors are challenging incumbents and accelerating the overall evolution of multi-factor authentication capabilities.
This comprehensive research report delivers an in-depth overview of the principal market players in the Multi-factor Authentication market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Broadcom Inc
- Cisco Systems Inc
- CyberArk Software Ltd
- Entrust Corporation
- Fujitsu Group
- Google LLC
- HID Global Corporation
- IBM Corporation
- LastPass
- ManageEngine
- Microsoft Corporation
- NEC Corporation
- Okta Inc
- OneSpan Inc
- Oracle Corporation
- Ping Identity Corporation
- RSA Security LLC
- Salesforce
- Secret Double Octopus
- SecureAuth Corporation
- SecureEnvoy Limited
- Silverfort
- Thales Group
- WatchGuard Technologies
- Yubico AB
Strategic imperatives for decision makers to integrate adaptive authentication frameworks, optimize user experience, and align security investments with emerging risks
Industry leaders must embrace a strategic roadmap that aligns authentication architectures with broader security objectives and business imperatives. Adopting a zero trust framework is essential, as it mandates continuous verification of user identities and contextual risk assessments at every access juncture. By integrating adaptive authentication engines into identity governance systems, organizations can dynamically calibrate assurance levels based on transaction risk and environmental factors.
In addition, shifting toward passwordless experiences is critical for reducing attack surface and bolstering user satisfaction. Companies should prioritize investments in hardware-backed authenticators, mobile credential applications, and biometric sensors, ensuring that users can seamlessly verify their identities without the vulnerabilities associated with static passwords.
Given the impact of recent tariff changes on hardware token economics, security teams are advised to diversify their vendor ecosystem and explore software-centric authentication alternatives. Negotiating volume licensing agreements with multiple providers can mitigate supply chain disruptions and cost escalations, while maintaining a balanced portfolio of hardware and cloud-based factors.
Finally, continuous monitoring and analytics are pivotal for preempting sophisticated threat vectors. Implementing machine learning–driven anomaly detection within authentication pipelines allows for rapid identification of credential misuse and automated mitigation workflows. By coupling these technical measures with regular tabletop exercises and incident response drills, organizations can cultivate resilience against emerging cyber risks and ensure that authentication strategies remain aligned with evolving threat landscapes.
Describing the rigorous research approach combining qualitative interviews, secondary data analysis, and supply chain assessments to ensure comprehensive market understanding
This research leverages a rigorous methodology that blends primary qualitative interviews, comprehensive secondary data analysis, and detailed supply chain assessments to deliver actionable market insights. Primary research involved structured dialogues with leading CISOs, IT directors, and security architects across enterprise and government organizations, gathering firsthand perspectives on authentication challenges, adoption drivers, and technology preferences.
Secondary sources comprised technical white papers, regulatory guidelines, and vendor technical documentation, which were systematically reviewed to verify emerging trends and product roadmaps. This process ensured alignment with industry standards and compliance mandates while avoiding reliance on proprietary market sizing data.
Supply chain assessments focused on the impact of 2025 tariff regulations, including import duty schedules, geographic manufacturing distributions, and vendor sourcing strategies. By mapping component origins, distribution networks, and cost pass-through mechanisms, the research delineates the operational considerations that influence hardware token availability and pricing dynamics.
Data triangulation was achieved through cross-referencing primary insights with vendor press releases and independent cybersecurity research publications. Quality assurance workflows included peer reviews by subject matter experts and iterative validation sessions to confirm the accuracy of thematic findings. The methodology’s transparency and rigor ensure that conclusions are grounded in credible evidence and reflective of real-world deployment scenarios.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Multi-factor Authentication market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Multi-factor Authentication Market, by Model
- Multi-factor Authentication Market, by Deployment Mode
- Multi-factor Authentication Market, by Organization Size
- Multi-factor Authentication Market, by Vertical
- Multi-factor Authentication Market, by Region
- Multi-factor Authentication Market, by Group
- Multi-factor Authentication Market, by Country
- United States Multi-factor Authentication Market
- China Multi-factor Authentication Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 795 ]
Concluding insights emphasizing the strategic necessity of robust multi-factor authentication frameworks in safeguarding digital assets and ensuring regulatory compliance
As digital ecosystems become increasingly interconnected and threat actors continue to refine their tactics, multi-factor authentication has transitioned from a supplementary control to a core component of any resilient security architecture. Organizations that embrace adaptive, multi-layered authentication models position themselves to thwart unauthorized access, safeguard sensitive assets, and maintain regulatory compliance in complex environments.
The convergence of hardware and software factors, bolstered by behavioral analytics and AI-driven risk assessments, underscores a broader shift toward continuous identity verification. This approach not only enhances security posture but also streamlines user access, fostering a culture of trust and efficiency that underpins digital transformation initiatives.
Looking ahead, the interplay between regulatory mandates, economic considerations such as tariffs, and technological innovations will continue to shape authentication strategies. Entities that adopt flexible architectures capable of integrating emerging factors will be best positioned to address evolving threat landscapes and operational exigencies.
In summary, robust multi-factor authentication frameworks constitute a strategic imperative for organizations committed to protecting digital assets and sustaining competitive advantage. The insights presented herein equip decision makers with the knowledge required to architect, implement, and refine authentication solutions that meet both current and future security demands.
Empower your strategic security initiatives by contacting the Associate Director of Sales & Marketing to acquire the definitive multi-factor authentication market research report today
Are you ready to gain the granular insights that will empower your organization to navigate an increasingly complex security landscape with confidence? Reach out today to connect with Ketan Rohom, the Associate Director of Sales & Marketing, and discover how our comprehensive market research report delivers tailored intelligence on emerging multi-factor authentication technologies, regulatory developments, and regional adoption trends. Engage directly with an experienced industry liaison who can provide you with customized data presentations, in-depth briefing sessions, and strategic recommendations aligned with your enterprise’s unique risk profile. Secure your competitive edge by obtaining access to proprietary analyses of segmentation patterns, supply chain considerations, and vendor performance metrics-essential knowledge that will inform procurement strategies, partnership decisions, and long-term security roadmaps. Don’t delay: this authoritative report is the definitive resource for decision makers committed to strengthening digital defenses and achieving compliance objectives. Contact Ketan Rohom today to learn more about pricing options, delivery formats, and consultation packages-and take the decisive step toward safeguarding your organization’s digital assets with unparalleled market intelligence.

- How big is the Multi-factor Authentication Market?
- What is the Multi-factor Authentication Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




