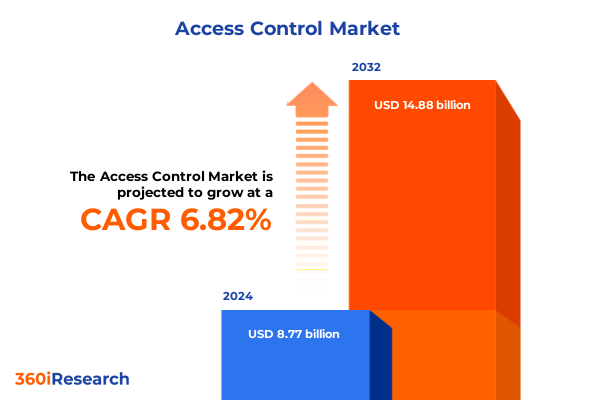
The Access Control Market size was estimated at USD 9.38 billion in 2025 and expected to reach USD 9.89 billion in 2026, at a CAGR of 6.80% to reach USD 14.88 billion by 2032.
Exploring the Evolution of Access Control Solutions and Their Pivotal Role in Strengthening Modern Organizational Security Infrastructures
Access control has evolved from simple lock-and-key mechanisms into sophisticated, integrated platforms that form the backbone of modern organizational security. As enterprises navigate an increasingly complex threat landscape, the demand for versatile solutions that span hardware, software, and services continues to surge. This transformation reflects the convergence of cybersecurity principles with physical security imperatives, compelling organizations to rethink traditional perimeters in favor of dynamic, risk-based access strategies.
In this context, access control is no longer an isolated tool but a critical component of a broader security ecosystem. From biometric authentication to cloud-native management consoles, the latest innovations enable seamless interoperability across building management, video surveillance, and identity management systems. Consequently, security leaders are realigning budgets and operational priorities to emphasize holistic platforms over siloed point solutions. This shift underscores the vital role that access control plays in ensuring operational continuity, regulatory compliance, and employee safety.
Uncovering the Transformative Technological and Operational Shifts Redefining Access Control Strategies Across Industries in Recent Years
The access control landscape has undergone profound shifts driven by technological advancements and evolving threat scenarios. Cloud adoption emerged as a catalyst for scalability, enabling remote administration of access privileges through intuitive web-based portals. Meanwhile, the proliferation of mobile credentials transformed user experiences by eliminating the need for physical cards and badges. These innovations have accelerated operational efficiency while introducing new considerations around interoperability and cybersecurity risk management.
Simultaneously, the integration of artificial intelligence and data analytics has revolutionized anomaly detection and incident response. Intelligent algorithms now correlate access events with behavioral baselines, automatically flagging unauthorized or suspicious activity for rapid investigation. Furthermore, interoperability standards such as ONVIF and OSDP have facilitated seamless data exchange between disparate security systems, fostering unified platforms that support proactive threat mitigation. As organizations prioritize resilience and agility, these transformative shifts have become central to strategic planning and investment decisions in access control.
Assessing the Ripple Effects of 2025 Tariff Measures on Access Control Supply Chains Pricing Strategies and Procurement Dynamics in the United States
In 2025, a series of tariff adjustments on imported security components introduced new cost considerations for access control manufacturers and end users across the United States. The heightened duties on controllers, card readers, and biometric modules disrupted established supply chains, compelling vendors to reassess sourcing strategies and negotiate alternative partnerships. Consequently, many leading providers accelerated efforts to localize production, seeking to mitigate exposure to escalating import expenses and maintain competitive pricing.
These tariff pressures have also influenced procurement cycles among enterprise clients. Capital planning timelines have extended as organizations weigh the total cost of ownership against projected duty increases. Security integrators and consultants have responded by offering modular deployment models that allow phased rollouts, thereby spreading capital expenditure and reducing upfront financial burden. Looking forward, the interplay between trade policy and technology adoption will continue to shape the access control market’s evolution, underscoring the importance of supply chain agility and strategic vendor alliances in navigating tariff-induced headwinds.
Deriving Actionable Insights from Comprehensive Product Type Organization Size and End User Industry Segmentation to Optimize Access Control Offerings
Analyzing the market through the lens of product type reveals distinct growth vectors. Hardware continues to underpin core access control architectures, particularly controllers, panels, and readers that deliver reliable credential validation at entry points. Services have emerged as a complementary force, with consulting engagements laying the groundwork for tailored security policies, installation teams ensuring seamless integration, and maintenance contracts preserving system uptime and performance. Meanwhile, software platforms drive innovation by offering cloud-based management, advanced analytics, and remote provisioning capabilities.
When evaluating organizational size, large enterprises often prioritize end-to-end solutions that encompass enterprise-grade hardware deployments and comprehensive managed services. These clients demand high-availability architectures and robust support frameworks. In contrast, small and medium enterprises favor modular offerings that deliver essential functionality without significant capital outlay, often opting for subscription-based software-as-a-service models that scale with business needs. End user industries further diversify these requirements. Financial institutions seek biometric and multi-factor authentication to comply with stringent regulatory standards, while energy and utilities companies require rugged hardware that performs reliably in harsh operational environments. Government and defense organizations emphasize secure, mission-critical systems with encryption and audit trail capabilities. Healthcare providers look to streamline patient access and regulatory reporting, leveraging software integrations with electronic health records. Information technology and telecommunications firms focus on remote credential management for distributed workforces, and manufacturing organizations prioritize integration with operational technology to safeguard production lines. Retail and e-commerce enterprises strive for frictionless customer experiences, integrating access credentials with loyalty programs and point-of-sale systems.
This comprehensive research report categorizes the Access Control market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Product Type
- Organization Size
- End User Industry
Highlighting Distinctive Regional Dynamics and Growth Drivers Shaping Access Control Market Evolution Across the Americas EMEA and Asia-Pacific Zones
Across the Americas, access control adoption is driven by technological modernization initiatives and heightened regulatory expectations around data privacy. North American enterprises often lead in piloting emerging technologies such as biometric entry and mobile-based credentials, supported by mature vendor ecosystems and strong channel partnerships. Latin American markets, meanwhile, demonstrate growing interest in cost-effective solutions that address urban security challenges and support rapid infrastructure development.
In Europe, the Middle East, and Africa, diverse socioeconomic conditions shape regional dynamics. Western European nations emphasize compliance with stringent data protection regulations and lean toward integrated platforms that unify physical and logical access. In contrast, markets in the Middle East invest heavily in smart city and infrastructure projects, deploying access control as part of large-scale digital transformation agendas. African markets, characterized by a mix of emerging economies, often adopt modular, service-driven models to balance security needs with budget constraints.
The Asia-Pacific region exhibits robust demand fueled by manufacturing expansion, urbanization, and public safety initiatives. Advanced economies such as Japan and Australia continue to refine access control standards and embrace IoT-enabled devices. Meanwhile, Southeast Asian countries are rapidly scaling deployments in sectors ranging from retail to transportation, reflecting a broader trend toward connected, smart infrastructure.
This comprehensive research report examines key regions that drive the evolution of the Access Control market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Leading Access Control Vendors and Innovators Driving Competitive Differentiation through Technological Leadership and Strategic Collaborations
The competitive landscape features a blend of established global players and agile niche innovators. Industry leaders distinguish themselves through end-to-end portfolios that span hardware manufacturing, cloud-native software, and professional services. Strategic partnerships with cloud service providers and cybersecurity firms have become a hallmark of these companies, enabling them to offer comprehensive solutions that address both physical and cyber threats.
Emerging vendors, on the other hand, often focus on specialized segments. Some introduce AI-driven analytics that overlay behavioral biometrics onto traditional access events, enhancing anomaly detection. Others develop open-platform software that prioritizes interoperability, allowing organizations to integrate best-of-breed hardware components. Across the board, successful players leverage channel ecosystems to extend reach into vertical markets and provide localized support. This collaborative approach affords customers tailored solutions that reflect specific regulatory and operational requirements, driving differentiation in an increasingly crowded market.
This comprehensive research report delivers an in-depth overview of the principal market players in the Access Control market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Acre Security
- ADT
- Allegion plc
- ASSA ABLOY
- Avigilon
- Axis Communications
- Bosch Security
- Brivo
- ButterflyMX
- dormakaba Group
- Genetec
- Honeywell
- Johnson Controls
- Kisi
- Matrix Cosec
- Nedap N.V.
- Paxton Access Ltd.
- SALTO Systems
- Suprema Inc.
- Vanderbilt Industries
Strategic Imperatives for Industry Leaders to Capitalize on Emerging Trends and Navigate Complex Market Challenges in the Access Control Landscape
To secure a leadership position, organizations must align their strategic roadmaps with the latest industry inflection points. Investing in scalable cloud-native architectures enables rapid adaptation to evolving operational demands and facilitates remote management. At the same time, integrating advanced analytics and AI into access control platforms yields actionable intelligence that informs risk-based policies and enhances incident response capabilities.
Leaders should cultivate partnerships across technology, consulting, and service domains to create holistic value propositions. By offering end-to-end solutions, they can simplify procurement processes and deepen customer relationships. Moreover, embracing open standards and APIs ensures seamless interoperability, reducing vendor lock-in and accelerating time to deployment. Finally, cultivating a talent pipeline skilled in both physical security and cybersecurity disciplines will be critical for sustaining innovation and maintaining competitive differentiation in the years ahead.
Outlining Rigorous Methodological Approaches and Data Validation Techniques That Ensure Robustness Credibility and Relevance of Access Control Market Insights
This analysis integrates a rigorous blend of secondary and primary research methodologies to ensure comprehensive and credible insights. Initially, a wide-ranging review of industry publications, white papers, and regulatory documents established foundational context and identified emerging trends. This desk research was followed by detailed examinations of company reports and technical specifications to map vendor capabilities and solution architectures.
Primary validation included in-depth interviews with security architects, IT directors, and operations leaders across key end user segments. These conversations illuminated real-world deployment challenges, technology adoption drivers, and procurement considerations. Data triangulation techniques then reconciled qualitative insights with publicly available vendor announcements, press releases, and case studies. Advanced data validation steps, including cross-checking against industry benchmarks and peer-reviewed research, reinforced the robustness of the findings. This methodological rigor ensures that the conclusions and recommendations presented herein are both actionable and aligned with stakeholder requirements.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Access Control market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Access Control Market, by Product Type
- Access Control Market, by Organization Size
- Access Control Market, by End User Industry
- Access Control Market, by Region
- Access Control Market, by Group
- Access Control Market, by Country
- United States Access Control Market
- China Access Control Market
- Competitive Landscape
- List of Figures [Total: 15]
- List of Tables [Total: 1590 ]
Synthesizing Core Findings and Implications to Illuminate Critical Takeaways and Future Trajectories for Stakeholders in Access Control Ecosystem
The synthesis of key findings underscores the centrality of integrated, cloud-enabled access control solutions within modern security frameworks. Technological innovations, from AI-driven analytics to mobile credentialing, have expanded the definition of access control beyond perimeter security, making it an indispensable part of enterprise risk management. Furthermore, shifting trade policies and tariff landscapes have highlighted the importance of supply chain diversification and agile procurement practices.
Segmentation insights reveal that while hardware remains the foundational element, value-added services and software platforms are driving differentiation. Regional dynamics attest to the variability in adoption rates, yet they also reflect universal imperatives around regulatory compliance, digital transformation, and operational resilience. Ultimately, organizations that embrace open standards, strategic partnerships, and talent development will be best positioned to navigate the complexities of the access control ecosystem and harness its full potential.
Engaging with Ketan Rohom to Unlock Comprehensive Access Control Market Intelligence and Drive Informed Decision Making for Strategic Growth
To explore the full range of strategic intelligence on the access control market, reach out directly to Ketan Rohom, Associate Director, Sales & Marketing. Engaging with Ketan provides a tailored consultation to address your organization’s specific security challenges, offering deep dives into product innovations, regional dynamics, and competitive landscapes. Through this conversation, you will gain clarity on how to leverage the latest market developments to achieve operational excellence and safeguard critical assets.
By initiating this dialogue, you secure a privileged preview of proprietary research findings and gain access to exclusive advisory support. Ketan’s expertise in aligning market research insights with real-world business objectives ensures that your investments in access control technologies yield measurable returns and sustainable growth. Don’t miss the opportunity to convert strategic data into actionable roadmaps-connect with Ketan Rohom today and empower your decision-making with the most comprehensive access control market intelligence available.

- How big is the Access Control Market?
- What is the Access Control Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




