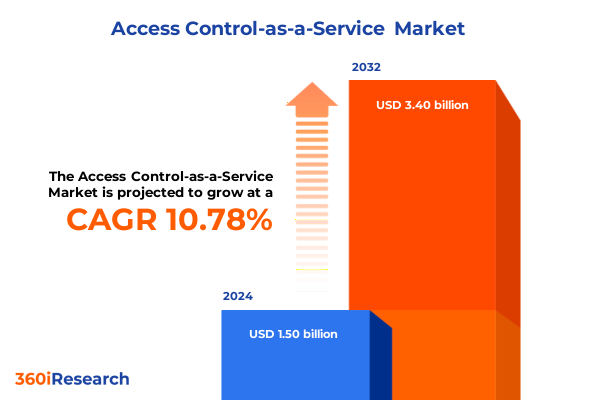
The Access Control-as-a-Service Market size was estimated at USD 1.64 billion in 2025 and expected to reach USD 1.81 billion in 2026, at a CAGR of 10.92% to reach USD 3.40 billion by 2032.
Unveiling Access Control-as-a-Service as the Cornerstone of Modern Security Ecosystems in an Increasingly Distributed Technology Landscape
In an era defined by hybrid work environments and rapidly evolving cyber threats, Access Control-as-a-Service has emerged as a foundational element for organizations seeking to unify security across distributed infrastructures. As enterprises shift workloads to cloud platforms and adopt remote collaboration models, traditional perimeter-based access controls no longer suffice. Instead, there is a growing imperative to centralize authorization policies in a scalable, policy-driven framework that can adapt in real time to contextual factors such as device posture, user behavior, and data sensitivity. This introduction provides an essential overview of why on-demand, cloud-native access governance is rapidly becoming the standard for securing modern digital ecosystems.
Transitioning from legacy, appliance-centric architectures to a service-based paradigm promises not only operational simplicity but also tighter integration with identity platforms, security analytics, and automated compliance workflows. By abstracting policy enforcement into a managed service, organizations can offload the complexity of patch management, scalability planning, and high-availability configurations, freeing internal teams to focus on strategic cybersecurity initiatives. Moreover, this shift aligns with the broader "security as code" movement, where access policies are versioned, tested, and deployed through DevOps pipelines, ensuring consistency and auditability across dynamic environments. The following sections examine the transformative market shifts, regulatory pressures, segmentation insights, and strategic recommendations that define the Access Control-as-a-Service landscape today.
Examining the Technological and Organizational Transformations Driving the Evolution of Access Control-as-a-Service Solutions across Industries
Today's security environment is undergoing a fundamental redefinition, driven by the convergence of cloud adoption, zero-trust philosophies, and the proliferation of edge computing. As organizations embrace multicloud strategies, the demand for centralized access governance that can span heterogeneous platforms has surged. This tectonic shift is further accelerated by zero-trust mandates, which require continuous verification of identities and devices before granting any level of resource access. The evolution from static, network-centric firewalls to dynamic, identity-driven control points marks one of the most significant paradigm shifts in cybersecurity.
Simultaneously, advances in artificial intelligence and machine learning are transforming how access decisions are made, enabling real-time risk scoring based on anomalous behavior or environmental changes. The integration of behavioral analytics, contextual awareness, and adaptive authentication is pushing service providers to innovate beyond simple credential checks toward holistic risk-based models. This emphasis on intelligence-led access management not only enhances protection against sophisticated threats but also optimizes user experience by reducing unnecessary friction. Through these technological and organizational transformations, Access Control-as-a-Service is redefining how enterprises secure data, applications, and infrastructure across all touchpoints.
Assessing the Multifaceted Effects of 2025 United States Tariffs on Service Providers, Supply Chains, and Security Cost Structures in Access Control-as-a-Service
In 2025, the introduction of revised United States tariffs on technology components has created ripple effects throughout global supply chains, particularly affecting providers of cloud-based access control services. Key hardware elements-ranging from biometric sensors and card readers to physical security appliances-have experienced increased import duties, leading suppliers to reevaluate sourcing strategies and cost structures. As a result, service providers have accelerated partnerships with domestic manufacturers and regional distributors to mitigate supply chain disruptions and maintain competitive pricing for enterprise customers.
Beyond hardware, these tariffs have influenced the overall economics of deploying on-premises gateways that interoperate with cloud management consoles. Organizations are increasingly aware that dependency on imported devices can translate into higher total cost of ownership, prompting migration toward purely cloud-native enforcement points. Meanwhile, service vendors are diversifying their component portfolios by incorporating open-standard, software-defined access modules that reduce reliance on specialized imported hardware. This strategic pivot underscores the resilience of cloud-delivered access control offerings in the face of trade policy shifts and highlights the importance of supply chain agility in maintaining service continuity.
Decoding Core Market Segmentation Dynamics by Model Type, Service Type, Authentication Model, Access Points, Deployment, Organization Size, and End-User Verticals
Market segmentation within Access Control-as-a-Service reveals critical differences in how enterprises evaluate and adopt specific control frameworks. When dissecting Model Type, the space spans Attribute-Based Access Control platforms with advanced policy engines capable of attribute evaluation and condition matching, Discretionary Access Control systems emphasizing ownership-based control and permission granting, Identity-Based Access Control architectures that prioritize credential authentication and identity validation, Mandatory Access Control solutions built around security clearance and sensitivity label paradigms, and Role-Based Access Control implementations focused on role assignment and role authorization. These distinctions inform purchasing criteria, with some organizations valuing the granularity of attribute-driven policies while others seek the simplicity of role-centric models.
Service Type segmentation further differentiates the landscape, wherein pure Hosted solutions offer fully managed, cloud-native deployments; Hybrid configurations deliver a blend of on-premises enforcement points integrated with centralized cloud consoles; and Managed services extend to include professional oversight, customization, and ongoing optimization. The choice between Single-Factor and Multi-Factor Authentication models underscores varying risk tolerances, with two-factor and three-factor authentication options enabling stronger security postures for regulated industries. Access Points considerations cover a spectrum from mobile applications and responsive web interfaces to physical systems powered by biometric readers and card-based access, as well as browser extensions and dedicated web portals for digital resource control. Organizational scale shapes deployment preferences, as large enterprises often leverage private or hybrid clouds to align with data sovereignty and compliance requirements, while small and medium enterprises gravitate toward public cloud offerings for cost-effectiveness and simplicity. Finally, End-User segmentation spans highly regulated sectors such as aerospace and defense, critical infrastructure domains in energy and utilities, customer-centric verticals like consumer goods and retail, and emerging technology arenas in information and communication services, each with unique security imperatives driving their Access Control-as-a-Service adoption patterns.
This comprehensive research report categorizes the Access Control-as-a-Service market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Model Type
- Service Type
- Authentication Model
- Access Points
- Organization Size
- Deployment Model
- End-User
Unraveling Distinct Regional Patterns and Growth Drivers in Americas, Europe Middle East Africa, and Asia-Pacific for Access Control-as-a-Service Adoption
Across the Americas, the United States remains at the forefront of Access Control-as-a-Service adoption, driven by a mature regulatory framework and a strong emphasis on data privacy and cybersecurity standards. Canada’s market growth is underpinned by public sector modernization initiatives and cross-border data protection agreements, while Brazil is emerging as a high-growth opportunity as enterprises invest in cloud-native identity solutions to support digital transformation programs. The convergence of stringent compliance requirements and robust venture capital investment has solidified the Americas as a leading region for innovative access governance platforms.
In Europe, the Middle East, and Africa, regulatory drivers such as GDPR and evolving national privacy laws are creating demand for solutions that deliver advanced audit trails and fine-grained policy controls. Western European markets exhibit strong uptake of zero-trust frameworks, while the Gulf Cooperation Council countries prioritize solutions that support localized deployment and regional data residency. Sub-Saharan Africa is witnessing nascent growth, spurred by digital inclusion initiatives and increased connectivity, which in turn elevates the need for scalable, cloud-based access management. Together, the EMEA region presents a mosaic of regulatory and maturity levels that require adaptable service models.
Asia-Pacific dynamics are marked by rapid digitalization in China, India, and Southeast Asia, with government-led smart city and digital economy projects catalyzing investment in secure access platforms. Japan and South Korea demonstrate early adoption of AI-driven risk scoring and biometric integrations, reflecting a technology-forward culture. Australia’s strong cybersecurity mandates for critical infrastructure add further momentum, while emerging markets in Southeast Asia emphasize cost-efficient, public cloud-based service offerings. These regional patterns underscore the necessity for providers to tailor deployment and compliance features to meet diverse market requirements.
This comprehensive research report examines key regions that drive the evolution of the Access Control-as-a-Service market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Strategic Moves, Innovation Strategies, and Competitive Positioning of Leading Corporations in the Access Control-as-a-Service Marketplace
Key players in the Access Control-as-a-Service market are pursuing innovative integration strategies to solidify their competitive advantage. Established cloud identity providers are enhancing their native access governance capabilities through strategic acquisitions of specialty vendors focused on attribute-based policy engines and biometric authentication modules. At the same time, security-centric organizations are expanding their portfolios by embedding access control services into broader extended detection and response platforms, delivering a unified security operations experience.
Tech conglomerates are leveraging ecosystem partnerships to seamlessly connect access policies with cloud platforms, endpoint protection suites, and network security appliances. These collaborations facilitate cross-product policy synchronization, reducing administrative overhead for global enterprises. Meanwhile, emerging startups specializing in risk-based authentication are fostering integrations with major identity providers’ developer platforms, enabling rapid uptake among application teams adopting agile development practices. This competitive interplay between incumbents and niche innovators is accelerating feature roadmaps and driving differentiation across ease-of-use, analytics sophistication, and developer-friendly interfaces.
This comprehensive research report delivers an in-depth overview of the principal market players in the Access Control-as-a-Service market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Acre Security
- Allegion Plc
- Allied Universal
- Assa Abloy AB
- Brivo Inc.
- Broadcom Inc.
- Cisco Systems, Inc.
- Cloudastructure Inc.
- Datawatch Systems, Inc.
- Delinea Inc.
- dormakaba Group
- DSX Access Systems, Inc
- Forcefield
- Genetec Inc.
- Honeywell International Inc.
- IDENTIV, INC.
- International Business Machines Corporation
- Johnson Controls International plc
- Kastle Systems
- Kisi Inc.
- M3T Corporation
- Microsoft Corporation
- Motorola Solutions, Inc.
- Oracle Corporation
- Palo Alto Networks, Inc.
- Robert Bosch GmbH
- SALTO Systems, S.L.
- Securitas Technology
- ServiceNow, Inc.
- Spica International d. o. o.
- Tata Consultancy Services Limited
- Telcred
- Thales Group
- Vector Security, Inc.
- Zhejiang Dahua Technology Co., Ltd.
Providing Targeted Strategic Guidelines and Operational Tactics for Industry Leaders to Capitalize on Emerging Trends in Access Control-as-a-Service
To capitalize on the momentum in Access Control-as-a-Service, organizations should prioritize the development of a holistic security strategy that embeds policy orchestration into existing enterprise workflows. This begins with conducting a comprehensive maturity assessment to identify gaps in identity lifecycle management, policy enforcement coverage, and incident response alignment. Armed with these insights, IT leaders can launch phased pilot programs that validate attribute-driven policy frameworks in high-stakes environments before scaling them across broader user populations.
In parallel, it is essential to cultivate strategic relationships with multiple service providers to ensure sourcing flexibility and to negotiate service-level agreements that reflect risk tolerance and performance requirements. Organizations should also invest in training programs that upskill security and operations teams on the nuances of policy-as-code and zero-trust architectures. Finally, embedding continuous feedback loops between security operations, identity management, and application development teams will accelerate the refinement of dynamic access policies and enable rapid response to evolving threats.
Outlining Rigorous Research Framework, Data Collection Techniques, and Analytical Approaches Employed in the Comprehensive Access Control-as-a-Service Study
This study was underpinned by a rigorous research framework combining primary and secondary data sources to ensure comprehensive coverage of market dynamics. Primary research included structured interviews with senior security architects, identity and access management leaders, and industry analysts, supplemented by detailed surveys to capture deployment preferences, technology drivers, and purchasing criteria. Secondary research encompassed an exhaustive review of publicly available vendor materials, technical white papers, and regulatory publications, as well as analyses of technology forums and developer communities.
Quantitative data were triangulated by cross-referencing financial reports, transaction announcements, and investment trends, while qualitative insights derived from expert roundtables and advisory panels informed the understanding of emerging use cases and innovation priorities. Analytical methodologies included benchmarking vendor capabilities against established criteria, mapping feature adoption curves, and assessing competitive positioning through a multi-dimensional scoring model. The resulting research deliverables were validated through peer review and subject-matter expert feedback to ensure accuracy, relevance, and actionable value for decision makers.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Access Control-as-a-Service market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Access Control-as-a-Service Market, by Model Type
- Access Control-as-a-Service Market, by Service Type
- Access Control-as-a-Service Market, by Authentication Model
- Access Control-as-a-Service Market, by Access Points
- Access Control-as-a-Service Market, by Organization Size
- Access Control-as-a-Service Market, by Deployment Model
- Access Control-as-a-Service Market, by End-User
- Access Control-as-a-Service Market, by Region
- Access Control-as-a-Service Market, by Group
- Access Control-as-a-Service Market, by Country
- United States Access Control-as-a-Service Market
- China Access Control-as-a-Service Market
- Competitive Landscape
- List of Figures [Total: 19]
- List of Tables [Total: 2703 ]
Synthesizing Critical Findings and Forward-Looking Perspectives to Chart the Future Trajectory of Access Control-as-a-Service Technologies
The collective findings underscore that Access Control-as-a-Service has matured from a niche offering into a strategic imperative for organizations charting their digital transformation journeys. Key takeaways reveal an industry moving decisively toward attribute-centric, risk-based policy enforcement, underpinned by AI-driven analytics and adaptive authentication methods. While trade policy shifts such as the 2025 United States tariffs have introduced supply chain complexities, they have also catalyzed innovative sourcing strategies and a move toward software-defined access modules.
Market segmentation insights demonstrate that no single model type or deployment approach serves all use cases; instead, organizations must align their security architecture choices with their unique risk profiles, regulatory landscapes, and operational constraints. Regional analysis highlights varying maturity levels and compliance drivers, further emphasizing the need for flexible service models. Finally, competitive intelligence reveals an active marketplace where incumbents and disruptors alike are racing to deliver unified, developer-friendly, and highly automated access governance platforms. Together, these conclusions point toward a future in which seamless, context-aware access controls will be integral to organizational resilience and business agility.
Engage with Ketan Rohom to Secure Exclusive Access to In-Depth Insights and Customizable Analyses in the Definitive Access Control-as-a-Service Report
To explore the full breadth of insights and actionable strategies in this definitive analysis of Access Control-as-a-Service, you are invited to connect directly with Ketan Rohom, Associate Director of Sales & Marketing. By engaging with him, you can secure immediate access to the complete report, request customized data highlights tailored to your organization’s unique priorities, and schedule a personalized briefing to align these findings with your strategic goals. Reach out today to transform how your enterprise secures and governs access in an evolving digital world and gain a competitive edge through data-driven decision making

- How big is the Access Control-as-a-Service Market?
- What is the Access Control-as-a-Service Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




