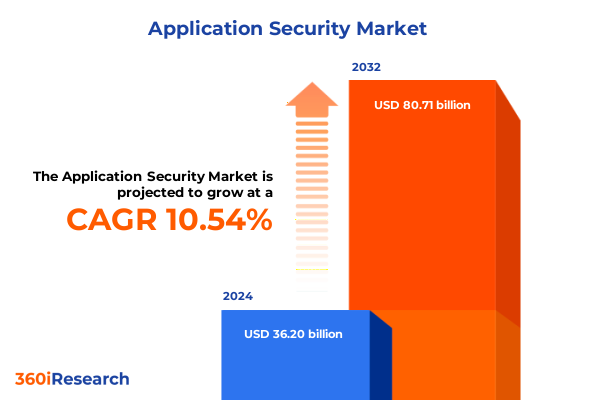
The Application Security Market size was estimated at USD 39.83 billion in 2025 and expected to reach USD 43.87 billion in 2026, at a CAGR of 10.61% to reach USD 80.71 billion by 2032.
Setting the stage for modern application security challenges and opportunities in a rapidly evolving digital ecosystem and threat environment
Organizations are confronting an unprecedented convergence of digital transformation, remote work, and innovation that has thrust application security into the spotlight. As software underpins nearly every customer interaction and internal process, vulnerabilities can lead to devastating breaches, financial losses, and reputational damage. The rapid proliferation of mobile and web applications has expanded the attack surface, while increasingly sophisticated threat actors exploit weaknesses across development pipelines and runtime environments.
Against this backdrop, security teams face pressure to shift from reactive patching to proactive, end-to-end protection strategies. Traditional perimeter defenses are no longer sufficient as applications reside in hybrid clouds, containerized environments, and edge deployments. Moreover, compliance requirements and stakeholder expectations continue to evolve, demanding rigorous testing, continuous monitoring, and adherence to best practices such as secure coding and threat modeling.
This executive summary synthesizes the prevailing forces reshaping application security, underscores the cumulative impact of policy changes, and provides segmentation and regional insights to guide decision-making. Through comprehensive analysis, leaders will discover how to navigate complexity, mitigate risk, and foster a security culture that keeps pace with innovation. As we embark on this journey, the insights presented here lay the groundwork for understanding both the challenges and opportunities that define modern application security landscapes.
Exploring the transformative shifts redefining application security from traditional perimeter defenses to integrated DevSecOps and AI-driven protection
The application security landscape is undergoing transformative shifts driven by technological advancements and changing development methodologies. Adoption of DevSecOps has blurred the lines between development, operations, and security teams, embedding security earlier in the software development lifecycle. This integration accelerates delivery while ensuring that vulnerabilities are identified and remediated continuously, significantly reducing time to detection and resolution.
Artificial intelligence and machine learning are also playing a pivotal role, automating threat detection, prioritizing vulnerabilities, and analyzing vast volumes of telemetry data in real time. Security orchestration, automation, and response platforms are streamlining workflows, allowing teams to focus on high-impact tasks rather than repetitive manual processes. Additionally, the rise of API-based architectures and microservices introduces new attack vectors, prompting organizations to adopt specialized API security solutions and runtime application self-protection mechanisms.
Concurrently, supply chain security has emerged as a critical concern. The systemic risk posed by third-party components and open-source libraries has prompted greater emphasis on software composition analysis and vulnerability disclosure programs. As enterprises embrace cloud-native development and distributed architectures, they must also navigate regulatory landscapes that mandate secure software practices and transparency. These transformative shifts, taken together, demand a holistic, adaptive approach to protecting applications in dynamic environments.
Cumulative assessment of United States tariffs in 2025 on application security supply chains costs and the strategic priorities of leading organizations
In 2025, the United States implemented a series of tariffs targeting technology imports that are integral to application security solutions. These cumulative policy measures have implications that ripple across hardware procurement, software licensing, and service delivery models. Organizations now face elevated costs for security appliances, development kits, and server infrastructure, compelling many to reevaluate budget allocations and procurement strategies.
The increased expenses associated with imported hardware devices have driven some providers to seek alternative sourcing or to shift production domestically. This pivot, however, introduces complexity in vendor management and can lengthen fulfillment cycles. On the software front, licensing fees for key security testing tools and runtime protection platforms have adjusted upward to reflect higher operational costs, directly impacting total cost of ownership.
Meanwhile, managed service providers are passing through tariff-related increases in professional and managed services contracts. This trend has heightened interest in subscription-based and cloud-native offerings that spread costs over time and reduce upfront capital expenditure. Organizations must also consider potential impacts on support agreements, patch cycles, and lifecycle management as global supply chains adapt to tariff-induced constraints. Understanding these tariff-driven shifts is critical for aligning security investments with strategic objectives and maintaining resilience in a rapidly changing economic environment.
Insightful segmentation analysis showing how type component vertical deployment mode and organization size influence application security adoption trends
Analyzing market segmentation provides valuable insights into where investment and innovation are concentrated. When viewing the landscape through the lens of application security type, mobile application security has gained prominence due to the surge in remote work and consumer demand for mobile services, while web application security remains a foundational component of comprehensive defenses. This dual focus underscores the necessity to tailor solutions to mobile-specific threats such as platform fragmentation and client-side attacks, even as traditional web vulnerabilities persist.
Considering components, the balance between services and solutions is instructive. Organizations continue to rely on managed services for ongoing monitoring, threat intelligence, and incident response, complemented by professional services that deliver bespoke security architecture and integration expertise. Meanwhile, solutions spanning runtime application self-protection, security testing tools, and web application firewalls address distinct phases of the application lifecycle. Enterprises are increasingly integrating these tools into CI/CD pipelines, ensuring that testing and protection are continuous rather than episodic.
From an industry vertical standpoint, sectors with stringent regulatory and risk profiles-such as banking, financial services, and insurance-lead in adoption, leveraging advanced security frameworks and automation. Government and defense entities prioritize hardened environments and compliance with national standards, while healthcare organizations focus on safeguarding patient data amid complex ecosystems. IT and telecom firms, along with retail enterprises, employ scalable solutions to secure high-volume transactions and user interactions. Together, these segmentation perspectives illustrate the multifaceted nature of application security and the imperative to align strategies with specific operational contexts.
This comprehensive research report categorizes the Application Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Type
- Component
- Industry Vertical
- Deployment Mode
- Organization Size
Regional insights illustrating distinct application security adoption patterns across Americas Europe Middle East and Africa and Asia Pacific markets
Regional dynamics play a crucial role in shaping application security strategies. In the Americas, enterprises benefit from mature cybersecurity frameworks and a competitive market that drives continuous innovation. Adoption here is characterized by early investment in cloud-native security solutions and a robust ecosystem of managed service providers. North American firms, in particular, are quick to integrate advanced capabilities such as machine learning-powered testing and orchestration platforms into their development pipelines.
Europe, Middle East, and Africa demonstrate diverse regulatory environments, from stringent data protection mandates in EU member states to nascent security requirements in emerging markets. This variation has led vendors to offer localized compliance modules and region-specific consulting services. Organizations in this region often prioritize end-to-end encryption, privacy by design, and transparency in software supply chains as core elements of their security postures.
Across Asia-Pacific, rapid digitalization and mobile-first initiatives have accelerated demand for both cloud-based and on-premise application security offerings. Enterprises in this region navigate complex public-private partnerships and evolving standards while managing high-growth trajectories. The convergence of mature and developing economies yields hybrid security models that blend global best practices with local market nuances. These regional insights underscore the importance of adapting application security investments to align with geographic priorities and operational realities.
This comprehensive research report examines key regions that drive the evolution of the Application Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Revealing company insights highlighting leadership approaches product innovations and competitive dynamics reshaping application security
Leading organizations are differentiating themselves through strategic technology roadmaps and targeted investments in application security. Market frontrunners are expanding global portfolios of security testing and runtime protection tools while deepening partnerships with orchestration and analytics providers. This collaborative ecosystem accelerates time to value by streamlining integration and ensuring interoperable solutions across multi-vendor environments.
In parallel, top firms are emphasizing talent development and community engagement. They sponsor secure coding academies, support threat intelligence sharing consortiums, and invest in continuous learning programs to cultivate expertise both internally and across their customer bases. These efforts foster a culture where security champions are embedded within development teams, driving awareness and accountability.
Innovation remains a key differentiator. Companies introducing advanced behavioral analysis, zero-trust enforcement, and self-healing mechanisms are setting new benchmarks for resilience. By combining proactive testing, real-time monitoring, and adaptive protection, they deliver a unified defense strategy that addresses both known vulnerabilities and emerging threat scenarios. Through these strategic initiatives, industry leaders are not only safeguarding assets but also creating competitive advantage by enabling faster, more secure application delivery.
This comprehensive research report delivers an in-depth overview of the principal market players in the Application Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Acunetix, Ltd. by Invicti
- Akamai Technologies
- Barracuda Networks
- Checkmarx, Inc.
- Contrast Security
- F5 Networks
- Fortinet
- Hewlett Packard Enterprise
- International Business Machines Corporation
- Lookout, Inc.
- Micro Focus International PLC
- Microsoft Corporation
- Onapsis, Inc.
- Oracle Corporation
- Palo Alto Networks
- PortSwigger, Ltd.
- Progress Software Corporation
- Pulse Secure LLC
- Qualys, Inc.
- Salesforce, Inc.
- Synopsys, Inc.
- Tenable, Inc.
- Trustwave Holdings, Inc.
- Veracode, Inc.
- WhiteHat Security, Inc.
Actionable recommendations for industry leaders to enhance application security resilience through innovation collaboration and strategic investment priorities
Industry leaders should prioritize the integration of security throughout the development lifecycle, embedding automated testing and policy enforcement into each CI/CD stage to detect vulnerabilities earlier and accelerate remediation. By deploying runtime application self-protection alongside security testing tools, organizations can achieve layered defenses that respond in real time to anomalous behavior.
Investing in AI-driven analytics for threat detection and prioritization enables teams to focus on high-risk issues, reducing alert fatigue and optimizing resource allocation. Complementary to technology investments, cultivating a security-first culture through targeted training programs and executive sponsorship will ensure that security objectives align with broader business goals and drive measurable outcomes.
Enterprises should also evaluate procurement strategies in light of the 2025 tariff environment, considering subscription-based models and cloud-native deployments to mitigate upfront costs. Collaborative vendor partnerships can unlock access to shared threat intelligence and joint innovation roadmaps, further enhancing resilience. By adopting a risk-based approach, leaders can allocate budget and personnel to protect mission-critical assets and maintain competitive agility in an ever-changing threat landscape.
Comprehensive research methodology detailing data collection analysis validation and triangulation approaches underpinning the application security insights
This analysis is underpinned by a rigorous research methodology combining primary and secondary data sources. Primary research consisted of in-depth interviews with CISOs, security architects, and DevOps leaders across multiple industry verticals, capturing firsthand perspectives on current challenges and future priorities. Complementing these insights, a detailed survey of IT decision-makers provided quantitative validation and trend corroboration.
Secondary research involved a comprehensive review of regulatory publications, vendor white papers, threat intelligence reports, and academic studies to map the evolving threat landscape and emerging solution capabilities. Data triangulation was employed to cross-verify findings, ensuring accuracy and consistency across diverse information streams.
Analytical frameworks such as SWOT, PESTLE, and Porter’s Five Forces facilitated evaluation of market dynamics, while scenario planning exercises helped anticipate shifts driven by policy changes and technological breakthroughs. Throughout the process, expert validation sessions were conducted to refine assumptions and confirm the applicability of insights across global markets.
Together, these research steps provide a robust foundation for the insights presented, offering decision-makers confidence in the depth, relevance, and reliability of the analysis.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Application Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Application Security Market, by Type
- Application Security Market, by Component
- Application Security Market, by Industry Vertical
- Application Security Market, by Deployment Mode
- Application Security Market, by Organization Size
- Application Security Market, by Region
- Application Security Market, by Group
- Application Security Market, by Country
- United States Application Security Market
- China Application Security Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1272 ]
Conclusion synthesizing key findings emerging trends and strategic imperatives to guide informed decision making in application security initiatives
The convergence of DevSecOps integration, AI-driven automation, and cloud-native architectures has fundamentally reshaped the application security landscape. Organizations that embrace continuous testing, runtime protection, and adaptive defenses are better positioned to mitigate risks and support rapid innovation. At the same time, evolving regulatory requirements and tariff-induced cost pressures underscore the need for flexible procurement strategies and localized compliance solutions.
Segmentation analysis reveals that adoption trends vary significantly by application type, component preferences, industry verticals, deployment modes, and organization sizes, highlighting the importance of context-specific security roadmaps. Regional insights further amplify this point, demonstrating how geographic nuances influence investment choices and implementation approaches.
Key companies are raising the bar through collaborative ecosystems, talent development, and advanced threat analytics, while actionable recommendations emphasize the importance of embedding security across development lifecycles and leveraging subscription models to manage costs. This executive summary equips stakeholders with a synthesized view of critical market forces, enabling informed decision-making.
As the threat landscape continues to evolve, sustained vigilance, strategic partnerships, and a culture of security innovation will be vital. Armed with these insights, organizations can navigate uncertainty with confidence, ensuring their applications remain secure, compliant, and resilient in the face of tomorrow’s challenges.
Take actionable steps today by connecting with Ketan Rohom Associate Director Sales and Marketing to secure your application security market research report
Engaging with Ketan Rohom offers a direct pathway to equip your organization with in-depth insights and practical strategies that will drive your application security initiatives forward. By reaching out to Ketan Rohom, Associate Director Sales and Marketing, you gain personalized guidance on report contents, pricing options, and implementation support. This conversation ensures that you receive the precise intelligence you need to strengthen your security posture, accelerate time to value, and align defenses with evolving business priorities. Don’t miss this opportunity to invest in a resource that translates complex data into actionable roadmaps tailored to your unique environment. Connect today to secure your copy of the application security market research report and begin transforming insights into impact.

- How big is the Application Security Market?
- What is the Application Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




