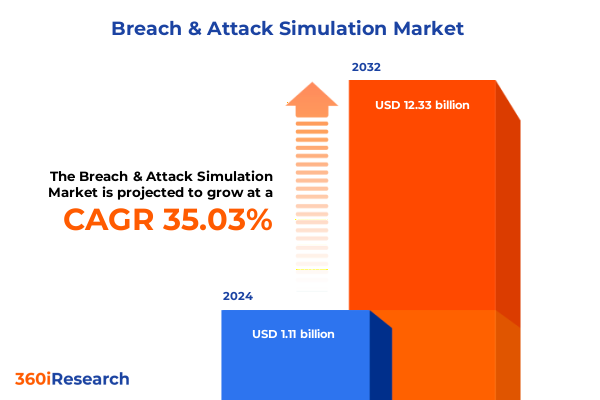
The Breach & Attack Simulation Market size was estimated at USD 1.48 billion in 2025 and expected to reach USD 1.98 billion in 2026, at a CAGR of 35.28% to reach USD 12.33 billion by 2032.
Unveiling the Critical Role of Breach and Attack Simulation in Strengthening Modern Cybersecurity Defenses Amidst Evolving Threats and Resilience
Breach and attack simulation has emerged as a pivotal discipline within cybersecurity, transforming how organizations anticipate and neutralize advanced threats. By emulating realistic attack scenarios, this approach exposes vulnerabilities that traditional testing methods often miss, bridging the gap between theoretical security and operational resilience. As threat actors leverage ever more sophisticated tactics, the capacity to simulate attacks in a controlled environment empowers defenders to validate security controls, refine incident response protocols, and reinforce organizational confidence. Consequently, organizations that embrace this methodology can achieve a proactive security stance rather than reacting post-incident.
Navigating the Emergence of AI-Driven Attack Vectors and Adaptive Simulation Strategies Shaping the Future of Cybersecurity Testing
The landscape of breach and attack simulation is undergoing transformative shifts driven by rapid advances in automation, machine learning, and cloud-native delivery models. Automation frameworks now facilitate continuous security testing, enabling security teams to execute simulated attacks with minimal manual intervention. This evolution not only accelerates the identification of emerging vulnerabilities but also harmonizes testing cycles with agile development pipelines. Concurrently, machine learning algorithms are enhancing threat emulation fidelity by analyzing vast datasets of real-world exploits and tailoring simulation campaigns to mirror actual adversary behaviors. These innovations have elevated breach and attack simulation from a periodic security exercise to a foundational element of a comprehensive, adaptive security program.
Assessing the Far-Reaching Consequences of 2025 United States Tariffs on Breach and Attack Simulation Technology Supply Chains and Adoption
In 2025, the United States introduced a series of targeted tariffs affecting the import of specialized hardware and software components critical to breach and attack simulation platforms. While designed to bolster domestic manufacturing, these measures have reverberated across global supply chains, affecting both vendors and end users. Elevated component costs have prompted leading solution providers to explore alternative procurement strategies and strategic partnerships with domestic integrators. At the same time, end users are evaluating the total cost of ownership more rigorously, balancing the benefits of advanced simulation capabilities against increased capital expenditures. The cumulative impact of these tariffs underscores the necessity for organizations to optimize resource allocation, diversify suppliers, and negotiate long-term service agreements to maintain budgetary discipline without compromising on security rigor.
Illuminating Critical Segmentation Perspectives in Breach and Attack Simulation Across Components Security Types End Users and Delivery Methods
The breach and attack simulation market is nuanced by distinct segmentation perspectives that shape vendor offerings and customer expectations. When viewed through the lens of component classifications, service-oriented solutions span deployment services, support services, and training and consulting, each designed to guide organizations through implementation, refine operational processes, and cultivate internal expertise. Conversely, software-driven solutions encompass automated threat simulation, compliance and reporting capabilities, continuous security testing, incident response simulation, and security controls validation, delivering a comprehensive suite that addresses both proactive and reactive needs.
A security type segmentation further highlights the spectrum of simulated threats, ranging from application security exercises that stress-test web and mobile applications to endpoint security simulations that delve into desktop and mobile attack vectors. Network security scenarios evaluate data loss prevention controls and intrusion prevention systems under simulated breach conditions. End-user segmentation reveals demand patterns across verticals such as aerospace and defense, financial services, energy and utilities, government, healthcare, hospitality, and retail, with each sector prioritizing specific simulation scenarios based on regulatory requirements and adversary profiles. Finally, delivery mode segmentation differentiates cloud-based, hybrid, and on-premises deployments, enabling organizations to align simulation strategies with data sovereignty concerns, integration needs, and resource constraints.
This comprehensive research report categorizes the Breach & Attack Simulation market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Security Type
- End User
- Delivery Mode
Exploring Regional Dynamics and Adoption Patterns Driving Breach and Attack Simulation Across the Americas EMEA and Asia-Pacific Markets
Regional dynamics exert a profound influence on the adoption and maturation of breach and attack simulation programs. In the Americas, a strong emphasis on regulatory compliance and a mature threat landscape have fostered robust uptake of both cloud-based and on-premises solutions, with organizations prioritizing continuous testing frameworks and advanced reporting metrics. Europe, the Middle East, and Africa exhibit diverse adoption curves driven by varying regulatory regimes and levels of cybersecurity awareness. Regulatory mandates such as GDPR and evolving national security strategies in EMEA encourage a hybrid deployment model, where data privacy concerns and cross-border threat collaborations shape simulation practices. In the Asia-Pacific region, rapid digital transformation initiatives coupled with escalating cyber threats have accelerated demand for scalable, cloud-native simulation platforms, prompting vendors to localize support services and forge alliances with regional integrators to address language, compliance, and performance requirements.
This comprehensive research report examines key regions that drive the evolution of the Breach & Attack Simulation market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Strategic Movements and Innovations by Leading Companies Propelling the Breach and Attack Simulation Sector Forward
Leading providers play a pivotal role in driving technological innovation and setting industry benchmarks. Vendors such as SafeBreach pioneered emulation frameworks that map the entire attack kill chain, enabling granular visibility into defense efficacy, while AttackIQ introduced open architecture platforms that integrate with diverse security ecosystems to foster automation across testing processes. XM Cyber and Cymulate have advanced continuous simulation models that leverage AI-driven orchestration to identify compound vulnerabilities, urging enterprises to adopt perpetual testing cycles. Other notable innovators like Picus Security have concentrated on risk quantification, translating simulation outcomes into business-centric risk scores to guide strategic investment decisions. Collectively, these companies elevate industry standards by introducing advanced analytics, seamless orchestration, and robust ecosystem integrations that empower organizations to evolve their security postures.
This comprehensive research report delivers an in-depth overview of the principal market players in the Breach & Attack Simulation market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- AttackIQ
- BreachLock
- Cisco
- CyCognito
- Cymulate
- Fortinet
- IBM Security Randori
- Keysight Technologies
- Mandiant
- NetSPI
- Pentera
- Picus Security
- Qualys
- Rapid7
- ReliaQuest
- SafeBreach
- Scythe
- Skybox Security
- Sophos
- XM Cyber
Delivering Targeted and Pragmatic Recommendations to Help Industry Leaders Elevate Their Breach and Attack Simulation Capabilities and Resilience
To capitalize on the transformative potential of breach and attack simulation, industry leaders should first integrate simulation outputs with security orchestration and automated response workflows, thereby ensuring that identified weaknesses trigger immediate remediation actions. Next, aligning simulation scenarios with specific regulatory and compliance frameworks will enhance audit readiness and streamline reporting obligations. Investing in cross-functional training initiatives that encompass governance, risk, and compliance stakeholders alongside security operations teams fosters a shared understanding of threat dynamics and elevates organizational cyber maturity. Furthermore, adopting a risk-based prioritization model empowers decision-makers to allocate resources toward high-impact simulation campaigns, optimizing return on security investments. Finally, establishing a feedback loop between simulation results and real-world incident response playbooks ensures continuous refinement and accelerates time to containment for emerging attack vectors.
Detailing a Robust and Transparent Research Methodology Underpinning the Insights and Analysis Presented in the Breach and Attack Simulation Report
The insights and analysis presented in this report are underpinned by a rigorous and transparent research methodology designed to capture both breadth and depth of market dynamics. Primary research included in-depth interviews with senior security practitioners, solution architects, and industry analysts to glean qualitative insights into emerging use cases and deployment challenges. Complementing this, a comprehensive secondary research phase involved the systematic review of public filings, white papers, regulatory frameworks, and vendor documentation to establish a factual foundation. Data triangulation techniques were applied to reconcile discrepancies across sources, while expert advisory panels provided validation on critical findings and trend forecasts. This multi-faceted approach ensures that the report’s conclusions are both defensible and reflective of real-world adoption patterns.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Breach & Attack Simulation market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Breach & Attack Simulation Market, by Component
- Breach & Attack Simulation Market, by Security Type
- Breach & Attack Simulation Market, by End User
- Breach & Attack Simulation Market, by Delivery Mode
- Breach & Attack Simulation Market, by Region
- Breach & Attack Simulation Market, by Group
- Breach & Attack Simulation Market, by Country
- United States Breach & Attack Simulation Market
- China Breach & Attack Simulation Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 1431 ]
Summarizing Core Findings and Emphasizing the Strategic Imperatives for Maximizing the Value of Breach and Attack Simulation Across Enterprise Environments
The evolving threat landscape and rapid technological advances underscore the imperative for organizations to adopt breach and attack simulation as a core element of their security strategy. Key findings reveal that continuous, automated testing integrated with response orchestration dramatically enhances resilience, while nuanced segmentation insights highlight the importance of tailoring simulation exercises to specific components, security types, end-user profiles, and delivery preferences. Regional analysis further demonstrates that compliance pressures and digital transformation initiatives are primary drivers of adoption, and leading vendors continue to push innovation boundaries through AI-driven analytics and risk quantification. Together, these insights form a strategic blueprint for enterprises seeking to fortify defenses, optimize resource allocation, and maintain an adaptive security posture in the face of escalating adversary sophistication.
Connect with Ketan Rohom to Secure Your Comprehensive Breach and Attack Simulation Market Research Report and Gain Actionable Intelligence Today
To gain an in-depth understanding of breach and attack simulation trends and adopt proven strategies that drive resilience, reach out directly to Ketan Rohom, Associate Director of Sales & Marketing. Engaging with Ketan will ensure a tailored consultation that aligns the research findings with your organization’s unique security posture and objectives. Through this personalized approach, you can secure immediate insights into emerging threats, optimized deployment pathways, and best practices distilled from leading practitioners. Position your team to stay ahead in a rapidly evolving threat environment by acquiring the comprehensive market research report today and transforming strategic intent into measurable security outcomes.

- How big is the Breach & Attack Simulation Market?
- What is the Breach & Attack Simulation Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




