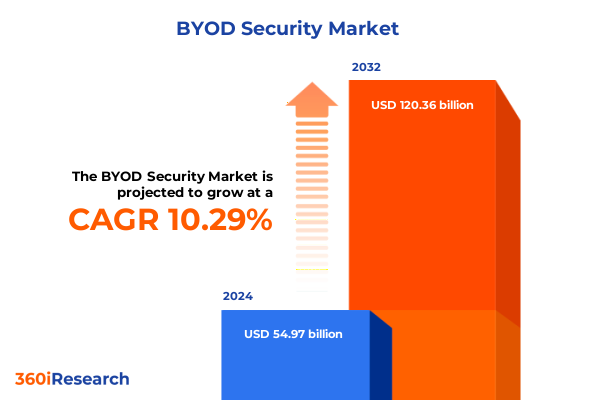
The BYOD Security Market size was estimated at USD 60.64 billion in 2025 and expected to reach USD 66.90 billion in 2026, at a CAGR of 10.28% to reach USD 120.36 billion by 2032.
Charting the Future of BYOD Security: Understanding Emerging Threats, Policy Dynamics, and Strategic Imperatives Shaping Enterprise Mobility
The rapid proliferation of personal mobile devices in professional environments has fundamentally reshaped enterprise IT strategies, compelling organizations to reconcile productivity gains with emergent security vulnerabilities. As employees increasingly rely on smartphones, tablets, and laptops to access corporate resources from diverse locations, IT leaders face an expanded threat surface that demands sophisticated controls and policies. This growing reliance on Bring Your Own Device paradigms underscores the necessity for robust security frameworks that preserve user experience while safeguarding sensitive data.
In response to this multifaceted challenge, enterprises are reevaluating traditional perimeter-centric defenses and pivoting towards adaptive security approaches that integrate policy enforcement, endpoint visibility, and continual risk assessment. This section delves into the forces driving BYOD adoption-from workforce mobility expectations to cost efficiencies-while highlighting the strategic imperatives guiding security architects in designing resilient, scalable solutions tailored to modern business demands.
Transformative Shifts in BYOD Security: Unveiling the Impact of Artificial Intelligence, Zero Trust Frameworks, and User-Centric Policies
In recent years, artificial intelligence and machine learning have emerged as cornerstone technologies for advanced threat detection and automated response within BYOD environments. By leveraging behavioral analytics and anomaly detection, enterprises can identify compromised devices and malicious activities in real time, dramatically reducing dwell time for sophisticated adversaries. Concurrently, the adoption of Zero Trust frameworks is reshaping how network access is granted, emphasizing continuous verification over implicit trust and reinforcing the principle of least privilege across device interactions.
Furthermore, the convergence of cloud computing and edge infrastructures is enabling secure application delivery closer to end users, minimizing latency while preserving comprehensive policy enforcement. As mobile application management strategies evolve, containerization techniques are increasingly deployed to isolate corporate data within secure application sandboxes, enhancing privacy controls and streamlining governance. Together, these shifts are driving a paradigm where security is deeply integrated into every layer of the mobile ecosystem, setting new benchmarks for resilience and agility in the face of advanced threat landscapes.
Assessing the Cumulative Impact of 2025 United States Tariffs on BYOD Security Infrastructure Costs, Supply Chain Dynamics, and Vendor Strategies
Throughout 2025, the United States has enacted a series of tariff measures targeting electronic devices and network components imported from key manufacturing hubs. Cumulatively, these duties have incrementally increased the landed cost of smartphones, tablets, and portable networking equipment, compelling vendors to reassess pricing models and supply chain configurations. In response, several leading security solution providers have absorbed marginal cost increases to maintain competitive pricing, while others have strategically diversified manufacturing footprints by shifting assembly operations to regions unaffected by the new tariff schedule.
This recalibration has also accelerated nearshoring initiatives, enabling streamlined logistics and reduced exposure to geopolitical risks. At the same time, procurement teams are renegotiating supplier contracts to incorporate tariff contingency clauses and seeking alternative hardware partnerships with domestic or allied manufacturers. These adaptive strategies are critical for companies aiming to deploy mobile security infrastructure on budget while ensuring hardware compatibility with advanced software and managed services offerings.
Uncovering Key Segmentation Insights Revealing How Solution, Deployment Mode, Organization Size, and Industry Vertical Shape BYOD Security Adoption
When viewed through the lens of solution segmentation, managed services and professional services have emerged as pivotal drivers of BYOD security adoption. Incident management and monitoring support ensure continuous visibility and rapid remediation, while consulting and integration engagements lay the foundation for cohesive policy implementation across diverse device estates. On the software side, mobile application management and device management platforms deliver centralized controls, enabling consistent enforcement of encryption, authentication, and compliance standards.
Deployment mode further influences adoption patterns as organizations balance the agility of cloud-native offerings against the control afforded by on-premise or hybrid architectures. Larger enterprises prioritize end-to-end integration with existing security information and event management systems, while mid-market and smaller entities often gravitate towards turnkey cloud solutions that minimize upfront investments. Industry verticals also shape priorities; financial services and healthcare demand rigorous access controls and data encryption, whereas education and retail focus on scalability and user experience. Underpinning these choices, emerging capabilities such as containerization, network access control, and virtual private networks continue to expand the toolkit available to IT teams, enabling bespoke BYOD strategies to address unique operational requirements.
This comprehensive research report categorizes the BYOD Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Solution
- Solution Component
- Organization Size
- Deployment Mode
- End User
Analyzing Regional Variations in BYOD Security Strategies Across Americas, Europe Middle East & Africa, and Asia-Pacific Markets
Across the Americas, mature regulatory frameworks and high mobile penetration have fostered robust BYOD security ecosystems. Enterprises in North America are expanding investments in unified endpoint management and zero trust architectures, driven by stringent data privacy statutes and sophisticated threat actors. Latin American markets, while still maturing, are experiencing surges in cloud adoption and mobile workforce expansion, prompting regional service providers to offer tailored managed security packages to address infrastructure gaps.
In Europe, Middle East, and Africa, data residency requirements and GDPR compliance have catalyzed demand for advanced encryption and identity federation solutions, particularly within financial and public sector institutions. Simultaneously, Asia-Pacific is witnessing rapid digital transformation that is outpacing legacy security models. Governments across the region are introducing tighter mobile security guidelines, and enterprises are responding by integrating automated compliance checks and adaptive access controls. This diverse landscape underscores the need for flexible strategies that align with regional regulations, as well as cultural expectations surrounding privacy and technology adoption.
This comprehensive research report examines key regions that drive the evolution of the BYOD Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Key Company Strategies in the BYOD Security Market Highlighting Innovation, Partnership Models, and Competitive Differentiators Driving Industry Leadership
Leading technology vendors have adopted distinct approaches to capture market share in the evolving BYOD space. Established incumbents are deepening partnerships with telecommunications providers to embed security controls at the network level, offering end-to-end solutions that unify device management, application security, and threat intelligence feeds. Simultaneously, cloud-native challengers are capitalizing on platform extensibility, integrating artificial intelligence modules that deliver predictive risk assessments and automated policy adjustments.
Strategic alliances between hardware manufacturers and security software firms are further enhancing interoperability, enabling seamless onboarding of new devices and streamlining firmware updates that reinforce endpoint protection. In parallel, specialist cybersecurity boutiques are differentiating by focusing on industry-specific solutions, such as secure mobile frameworks for highly regulated sectors. This dynamic competitive landscape is fostering rapid innovation cycles, where agility and strategic differentiation remain key for firms vying to establish leadership in the BYOD security domain.
This comprehensive research report delivers an in-depth overview of the principal market players in the BYOD Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Alcatel–Lucent S.A.
- AO Kaspersky Lab
- Avaya Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Citrix Systems, Inc.
- Forcepoint LLC
- Forescout Technologies, Inc.
- Hewlett Packard Enterprise Development LP
- International Business Machines Corporation
- Island Technology, Inc.
- Laya Tech Private Ltd.
- LayerX Security Ltd.
- McAfee Corp.
- Oracle Corporation
- Perception Point Inc.
- Portnox Security LLC
- SAP SE
- Scalefusion by ProMobi Technologies
- Sophos Ltd.
- Talon Cyber Security Ltd.
- Trend Micro Inc.
- Venn Technology Corporation
- Verizon Communications Inc.
- VMware, Inc.
- Zscaler, Inc.
Actionable Recommendations for Industry Leaders to Strengthen BYOD Security Postures Through Policy, Technology Integration, and Workforce Empowerment
Industry leaders should prioritize the integration of Zero Trust principles across their BYOD environments, ensuring that every access request is evaluated based on contextual factors such as device posture, user behavior, and network integrity. By deploying continuous monitoring tools that leverage machine learning, organizations can transition from reactive threat response to proactive risk mitigation, significantly reducing time to detect and remediate anomalies.
Equally important is the establishment of cross-functional governance frameworks that unify IT, security, and business units around shared policies and performance metrics. Investing in comprehensive employee training programs that emphasize secure mobile practices and the rationale behind policy requirements can foster a security-conscious culture. Finally, evaluating hybrid deployment models that blend cloud agility with on-premise control can optimize scalability and compliance, positioning enterprises to adapt swiftly as BYOD trends continue to evolve.
Comprehensive Research Methodology Detailing Data Collection, Analytical Frameworks, and Validation Processes for Rigorous BYOD Security Insights
This research employs a hybrid methodology combining primary and secondary data sources to deliver a rigorous analysis of the BYOD security landscape. In-depth interviews were conducted with senior security executives and IT directors to capture firsthand insights into deployment challenges, strategic priorities, and vendor evaluation criteria. These qualitative findings were complemented by quantitative surveys of technology buyers across key industries to validate adoption trends and budgetary allocations.
Secondary research involved an extensive review of regulatory frameworks, industry white papers, vendor technical documentation, and case studies. Collected data underwent triangulation through comparative analysis to ensure validity and reliability. Advanced analytical frameworks, including SWOT and Porter’s Five Forces, were applied to contextualize competitive dynamics, while thematic coding of interview transcripts informed the identification of emerging patterns. This multifaceted approach underpins the credibility of the strategic recommendations and insights presented throughout this report.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our BYOD Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- BYOD Security Market, by Solution
- BYOD Security Market, by Solution Component
- BYOD Security Market, by Organization Size
- BYOD Security Market, by Deployment Mode
- BYOD Security Market, by End User
- BYOD Security Market, by Region
- BYOD Security Market, by Group
- BYOD Security Market, by Country
- United States BYOD Security Market
- China BYOD Security Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1590 ]
Concluding Perspectives on BYOD Security Emphasizing Strategic Priorities, Emerging Opportunities, and Future-Proofing Enterprise Mobility
In summary, the BYOD security terrain is being reshaped by converging forces of technological innovation, regulatory evolution, and shifting workforce dynamics. Organizations that embrace adaptive security architectures-anchored by Zero Trust, enriched by artificial intelligence, and tailored through detailed segmentation-will be best positioned to navigate emerging threats and capitalize on mobility-driven productivity gains. By aligning vendor strategies with regional requirements and tariff-driven supply chain considerations, enterprises can construct resilient BYOD frameworks that balance security imperatives with operational flexibility.
Looking ahead, continuous investment in employee awareness, iterative policy refinement, and strategic partnerships will be critical for sustaining secure mobile ecosystems. The insights outlined in this executive summary provide a foundational blueprint for decision-makers intent on fortifying their BYOD initiatives and advancing toward a future-ready mobility posture.
Drive Your BYOD Security Strategy Forward Contact Associate Director Sales & Marketing Ketan Rohom to Access Exclusive Market Research Insights
Begin a strategic collaboration to elevate your organization’s mobility security posture by accessing our comprehensive analysis and tailored intelligence. Engage directly with Ketan Rohom, Associate Director of Sales & Marketing, to discuss how this in-depth research aligns with your enterprise objectives, and secure immediate access to actionable insights that will inform your next generation of BYOD security initiatives. Unlock exclusive guidance on vendor selection, deployment strategies, and risk mitigation frameworks designed to fortify your mobile workforce, and position your organization at the forefront of secure mobility innovation.

- How big is the BYOD Security Market?
- What is the BYOD Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




