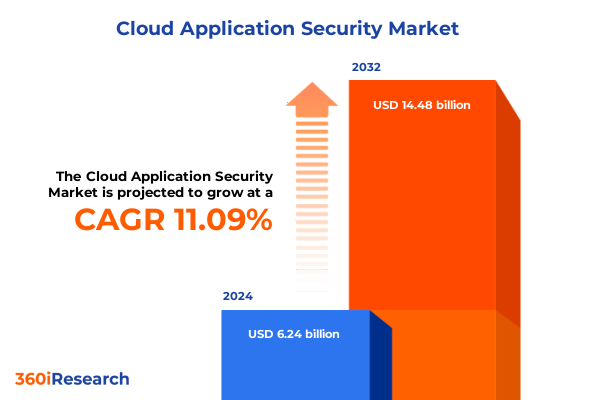
The Cloud Application Security Market size was estimated at USD 6.92 billion in 2025 and expected to reach USD 7.67 billion in 2026, at a CAGR of 11.11% to reach USD 14.48 billion by 2032.
Understanding the Rapid Evolution and Strategic Imperatives of Cloud Application Security Amid Escalating Threats and Regulatory Complexities
The proliferation of cloud-native applications and services has redefined the digital enterprise landscape, demanding a parallel evolution in security strategy. As organizations continue to migrate critical workloads to public, private, and hybrid cloud environments, traditional perimeter defenses have proven insufficient to counter sophisticated, distributed attacks. Consequently, there is a pressing need for robust, integrated cloud application security frameworks that blend proactive threat detection, real-time compliance monitoring, and adaptive access controls. This executive summary synthesizes the most pertinent developments in cloud application security, contextualizing technological advances, regulatory shifts, and market dynamics that will shape vendor and customer strategies through 2025 and beyond.
Against this backdrop of rapid change, stakeholders across financial services, healthcare, manufacturing, and retail industries are grappling with increasing complexity in managing security across multi-cloud and distributed application architectures. Clouds are no longer mere infrastructure platforms; they are strategic catalysts for digital innovation, enabling agile development cycles, global scalability, and data-driven decision-making. However, this agility comes with new attack surfaces and persistent risks, from misconfigured workloads to compromised identities. In response, enterprises are demanding integrated solutions-combining Cloud Access Security Brokers, posture management tools, and AI-driven threat intelligence-to enforce consistent protection without impeding business velocity.
Examining the Transformative Technological, Threat Landscape, and Regulatory Shifts Reshaping Cloud Application Security Strategies
The landscape of cloud application security is being reshaped by several concurrent transformative forces. Technologically, the integration of machine learning and behavioral analytics into security platforms is enabling more precise anomaly detection and automated remediation workflows. Rather than relying on signature-based methods, next-generation systems leverage real-time telemetry from workloads, APIs, and user behaviors to predict and preempt emerging attack vectors. As a result, organizations are shifting from reactive incident response models toward adaptive, preventive architectures that can scale dynamically with changing application footprints.
Meanwhile, the threat landscape has evolved hand in hand with enablement technologies. Adversaries are increasingly exploiting supply chain vulnerabilities and credential stuffing attacks to infiltrate cloud environments. Sophisticated malware campaigns leverage serverless compute and containerized deployments to obfuscate payloads and evade traditional detection mechanisms. These developments underscore the necessity for cloud-native security tools that can secure ephemeral workloads and distributed microservices topologies without creating blind spots.
In parallel, regulatory bodies worldwide are enacting stricter data protection and cybersecurity mandates, compelling organizations to adopt prescriptive security controls and conduct continuous compliance assessments. Initiatives such as the European Cyber Resilience Act and updated guidance from the U.S. Securities and Exchange Commission are broadening the scope of audit requirements and liability for cloud breaches. Consequently, enterprises are prioritizing platforms that seamlessly integrate compliance reporting with threat defense, ensuring that security measures not only block malicious activity but also demonstrate adherence to evolving legal frameworks. Together, these technological, threat-driven, and regulatory shifts are revolutionizing the way enterprises architect, deploy, and manage cloud application security.
Analyzing the Cumulative Effects of the 2025 United States Tariff Regime on Cloud Security Infrastructure Costs and Provider Strategies
In 2025, the cumulative impact of newly implemented and extended United States tariffs has reverberated across the cloud security infrastructure market, influencing vendor supply chains and customer procurement strategies. Tariffs on imported hardware components-ranging from specialized encryption modules to network appliances-have increased capital expenditures for on-premises security deployments, incentivizing a shift toward fully managed cloud-based services. This cost pressure has accelerated adoption of SaaS-centric security offerings, as organizations seek to mitigate tariff-related price increases by offloading infrastructure management and benefiting from scalable, pay-as-you-go models.
Moreover, certain software-based security tools bundled with hardware appliances have experienced indirect cost escalations due to upstream tariff pass-through effects. As a result, vendors are re-engineering solution architectures to decouple software functionality from proprietary hardware, embracing virtualization and container-native designs. This trend not only alleviates tariff exposure but also fosters portability across public and private cloud estates, enabling consistent policy enforcement irrespective of underlying infrastructure cost fluctuations.
On the customer side, large enterprises and government agencies are reevaluating multi-year subscription contracts and procurement cycles to account for currency volatility and tariff contingencies. Forward-thinking organizations are negotiating flexible pricing clauses tied to geopolitical risk indicators, while smaller enterprises are gravitating toward federated security services marketplaces that aggregate solutions under unified procurement frameworks. These dynamics underscore how tariff policy can catalyze long-term architectural realignment, driving both vendors and customers toward more modular, cloud-first security paradigms that are resilient to external economic shocks.
Uncovering Critical Insights Across Components, Deployment Models, Industry Verticals, and Enterprise Sizes Driving Cloud Security Adoption
Component-driven analysis reveals divergent growth trajectories between security services and embedded solution frameworks. Within the services category, the demand mix between managed services and professional services is shifting as organizations prioritize continuous monitoring and rapid incident response over one-time assessments. Managed service providers are expanding their offerings to include 24/7 cloud security operations centers, while professional services teams focus on strategic advisory engagements around Zero Trust implementation and cloud migration risk assessments. Conversely, the solutions segment is experiencing robust interest across a spectrum of specialized tools, from Cloud Access Security Brokers that govern API interactions to Cloud Security Posture Management platforms that automate configuration audits. Encryption and tokenization technologies are gaining traction as zero knowledge architectures become a baseline expectation, and identity and access management platforms are central to enforcing fine-grained, context-aware controls. Additionally, secure web gateway solutions are being enhanced with integrated threat intelligence feeds to mitigate browser-based exploits, while web application firewalls are evolving into distributed enforcement points at the network edge for microservices environments.
Deployment model considerations further nuance adoption patterns. Enterprises with stringent data residency and compliance requirements are gravitating toward private cloud deployments, often in conjunction with on-premises security stacks to maintain granular control. In contrast, public cloud-native organizations leverage CSPM and SWG services embedded within hyperscaler marketplaces for elastic scaling and native integration benefits. The hybrid interplay between these deployment modalities is fostering interoperable architectures, where policy orchestration layers bridge private and public domains seamlessly.
Industry vertical analysis underscores varying risk priorities. Regulated sectors such as banking, financial services, and insurance emphasize encryption, tokenization, and continuous compliance monitoring to meet stringent audit mandates. Government and defense entities focus on hardened IAM and threat intelligence platforms to counter advanced persistent threats. Healthcare providers are prioritizing data privacy controls and endpoint security to protect sensitive patient records, while technology and telecom operators integrate CASB and WAF solutions to secure developer pipelines and customer-facing applications. Manufacturing organizations are adopting secure gateways and IoT security extensions to safeguard operational technology networks, and retail and consumer goods players seek holistic web application and threat protection solutions to defend e-commerce platforms during peak traffic periods.
Finally, enterprise size significantly influences purchasing behavior. Large enterprises, wielding substantial security budgets, are investing in end-to-end platforms that provide centralized security orchestration and governance across complex multi-cloud estates. In contrast, small and medium-sized enterprises are increasingly reliant on turnkey, SaaS-based point solutions that offer rapid deployment, minimal overhead, and subscription-based pricing models. This delineation highlights a bifurcated market, where scalability and manageability requirements guide solution selection and partner ecosystem engagements.
This comprehensive research report categorizes the Cloud Application Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Deployment Model
- End Use Industry
- Enterprise Size
Comparative Regional Dynamics Highlighting Adoption Patterns and Security Investments Across Americas, EMEA, and Asia-Pacific Markets
Regional dynamics present a tapestry of adoption drivers and regulatory landscapes that influence cloud application security investments worldwide. In the Americas, mature markets in North America are leading the transition to advanced threat detection platforms and posture management tools, driven by high-profile breach incidents and comprehensive regulatory frameworks such as CCPA and various state-level cybersecurity mandates. Meanwhile, Latin American organizations are in a rapid catch-up phase, adopting cloud security services via local managed service providers to accelerate digital transformation while navigating data sovereignty concerns.
Transitioning to Europe, Middle East, and Africa, a diverse regulatory environment-from GDPR enhancements in Europe to emerging operational resilience requirements in the Middle East-has elevated the importance of integrated compliance and security solutions. European enterprises are pioneering data-centric security models, emphasizing encryption and tokenization across private and public cloud environments. In parallel, Gulf Cooperation Council countries are investing heavily in national cybersecurity strategies, fostering partnerships with global vendors to build robust cloud security infrastructures. African markets, though nascent in cloud adoption, are showing pockets of rapid growth in public sector modernization initiatives that incorporate secure, cloud-native application architectures.
In Asia-Pacific, the market is characterized by a mix of hyper-scale public cloud adoption in advanced economies such as Australia, Japan, and South Korea, and emerging opportunities in Southeast Asia driven by digital banking expansion and e-commerce growth. Regulatory initiatives like Japan’s My Number Act updates and Australia’s revised Security of Critical Infrastructure Act have intensified demand for continuous monitoring and real-time compliance reporting tools. Meanwhile, regional cloud service providers are collaborating with security vendors to deliver localized solutions that meet language, data residency, and cultural requirements. These varied regional trends underscore the necessity for vendors to tailor their go-to-market and solution portfolios to local regulatory mandates, maturity levels, and threat landscapes.
This comprehensive research report examines key regions that drive the evolution of the Cloud Application Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Leading Cloud Application Security Innovators, Their Differentiating Technologies, Strategic Alliances, and Anticipated Growth Trajectories
Leading market participants are differentiating through strategic technology integrations, ecosystem partnerships, and focused investments in innovation. Established players in network security have expanded their cloud portfolios by embedding CASB and CSPM capabilities into existing secure web gateway frameworks, thereby offering unified policy enforcement across on-premises and cloud environments. Pure-play cloud security vendors, in contrast, are leveraging microservices architectures and container-native designs to deliver lightweight agents and API-centric controls that minimize performance overhead and accelerate time to value.
Strategic alliances are reshaping competitive dynamics. Several vendors have entered co-development agreements with major hyperscale providers to embed threat intelligence and posture management services directly within cloud marketplaces, enhancing interoperability and streamlining procurement for end users. Others have formed partnerships with identity management platforms and DevSecOps tooling vendors to integrate security earlier in the development lifecycle, reinforcing shift-left principles and reducing remediation costs.
Investment in AI and automation remains a key differentiator. Companies that have successfully integrated self-learning threat detection engines with automated playbook orchestration are reporting significant improvements in mean time to detect and mean time to respond metrics. Concurrently, a subset of innovators is advancing toward predictive security analytics, leveraging anomaly forecasting to anticipate misconfigurations and compliance drift before violations occur. These initiatives highlight the competitive imperative to move beyond point solutions and deliver comprehensive, AI-driven platforms that can adapt dynamically to evolving application architectures and threat patterns.
This comprehensive research report delivers an in-depth overview of the principal market players in the Cloud Application Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Akamai Technologies, Inc.
- Amazon Web Services, Inc. (AWS)
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- CrowdStrike Holdings, Inc.
- CyberArk Software Ltd.
- F5 Networks, Inc.
- Fortinet, Inc.
- GitHub, Inc.
- Google LLC
- Imperva, Inc.
- McAfee Corp.
- Microsoft Corporation
- Netskope, Inc.
- Oracle Corporation
- Palo Alto Networks, Inc.
- Proofpoint, Inc.
- Qualys, Inc.
- Rapid7, Inc.
- Sophos Group Plc
- Symantec Corporation
- Tenable Holdings, Inc.
- Trend Micro Inc.
- VMware, Inc.
- Zscaler, Inc.
Actionable Strategic Recommendations for Industry Leaders to Enhance Cloud Application Security Posture and Drive Competitive Advantage
To navigate the increasingly complex cloud security landscape, industry leaders should adopt a multi-faceted strategic approach that balances proactive risk management with business agility. First, embedding security into the development lifecycle-by integrating security tooling directly into CI/CD pipelines and adopting infrastructure-as-code best practices-will reduce vulnerabilities early and accelerate remediation cycles. This shift-left methodology not only mitigates risk but also fosters a culture of shared responsibility between security and engineering teams.
Second, organizations should champion a Zero Trust paradigm for cloud applications, enforcing identity-centric controls, micro-segmentation, and continuous authentication. By leveraging adaptive, context-aware policies that evaluate device posture, user behavior, and data sensitivity, enterprises can minimize lateral movement and maintain granular oversight across dynamic workloads.
Third, investing in advanced analytics and automation is critical. Security operations teams must evolve from manual, alert-driven workflows to AI-augmented platforms that prioritize critical events, automate routine tasks, and provide actionable insights. This will require re-skilling personnel and forging partnerships with vendors offering mature orchestration and response capabilities.
Moreover, leaders must engage in collaborative threat intelligence sharing within industry consortia and public-private partnerships to stay ahead of emerging attack patterns. By contributing anonymized telemetry and receiving curated threat indicators, organizations can enhance detection accuracy and collectively elevate the security posture of their ecosystems.
Finally, fostering a flexible procurement strategy-one that accommodates shifting regulatory frameworks, tariff contingencies, and evolving business requirements-will ensure that security investments remain aligned with organizational priorities. Negotiating outcome-based contracts, leveraging cloud service marketplaces, and adopting modular architectures will provide the agility needed to adapt to future disruptions.
Outlining the Rigorous Primary and Secondary Research Methodology Underpinning the Comprehensive Cloud Application Security Analysis
This report synthesizes insights from a systematic research framework that combines rigorous primary engagements and exhaustive secondary analyses. Initially, in-depth discussions were conducted with senior security executives, solution architects, and risk management professionals across diverse industry verticals to validate key pain points, adoption drivers, and technology preferences. These interviews were complemented by workshops with leading cloud service providers, independent software vendors, and cybersecurity specialists to examine emerging roadmap priorities and integration challenges.
In parallel, secondary research involved a comprehensive review of regulatory filings, vendor whitepapers, technical documentation, and industry thought leadership sources to map the competitive landscape and benchmark solution capabilities. Publicly available patent databases and technology forums were analyzed to identify innovation hotspots in AI-driven threat detection, container security, and identity governance.
Quantitative data was triangulated through an aggregation of anonymized usage statistics from industry surveys, cloud marketplace metrics, and publicly disclosed financial reports. Cross-validation techniques were applied to ensure consistency between interview findings and documented market trends, while iterative validation loops with subject-matter experts refined the final conclusions. This multi-pronged approach ensures that the report’s insights are grounded in real-world experiences, validated by empirical data, and reflective of both current realities and future trajectories in cloud application security.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Cloud Application Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Cloud Application Security Market, by Component
- Cloud Application Security Market, by Deployment Model
- Cloud Application Security Market, by End Use Industry
- Cloud Application Security Market, by Enterprise Size
- Cloud Application Security Market, by Region
- Cloud Application Security Market, by Group
- Cloud Application Security Market, by Country
- United States Cloud Application Security Market
- China Cloud Application Security Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 1113 ]
Synthesizing Strategic Takeaways to Navigate Evolving Threats, Regulatory Shifts, and Market Dynamics in Cloud Application Security
The current cloud application security landscape is defined by accelerating innovation, heightened regulatory scrutiny, and an ever-expanding threat surface. As organizations grapple with the operational complexities of multi-cloud environments, the imperative for integrated, automated, and AI-driven security frameworks has never been greater. Market leaders are those who can seamlessly blend deep visibility with adaptive controls, ensuring that security enhances rather than impedes business transformation.
Looking ahead, the convergence of advanced analytics, identity-centric architectures, and policy orchestration across hybrid ecosystems will set the benchmark for next-generation security platforms. Enterprises that adopt flexible, outcome-based procurement models and invest in strategic partnerships will unlock the full potential of cloud security while maintaining cost efficiency and regulatory compliance.
Ultimately, success in this dynamic market will hinge on the ability to anticipate threat evolutions, leverage cross-industry collaboration, and embed security intelligence at every layer of the application stack. Organizations that act decisively on the insights presented here will be well positioned to safeguard their digital assets, maintain stakeholder trust, and achieve sustainable competitive advantage.
Engage with Ketan Rohom to Secure Your Competitive Edge Through a Comprehensive Cloud Application Security Market Research Report
To explore how these insights translate into tangible business value and fortify your organization’s defenses against evolving cloud security challenges, reach out to Ketan Rohom at the associate director level for expert guidance and tailored solutions. As a trusted partner in market analysis and strategic advisory, he will provide you with an in-depth understanding of emerging threats, competitive landscapes, and technology roadmaps. Engage in a collaborative dialogue that aligns your security initiatives with broader organizational objectives and future-proofs your cloud investments. Take the next step toward comprehensive risk mitigation and accelerated innovation by contacting Ketan Rohom and securing your copy of the definitive market research report.

- How big is the Cloud Application Security Market?
- What is the Cloud Application Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




