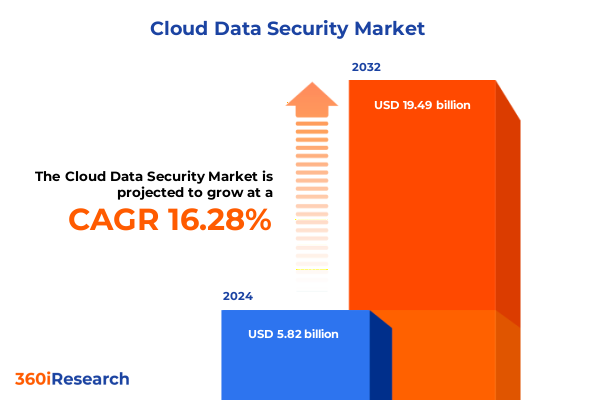
The Cloud Data Security Market size was estimated at USD 6.78 billion in 2025 and expected to reach USD 7.80 billion in 2026, at a CAGR of 16.28% to reach USD 19.49 billion by 2032.
Navigating the Complex Cloud Data Security Landscape to Empower Executives with Strategic Insights for Resilient Digital Transformation
Cloud data security has become a strategic imperative for organizations of all sizes as digital transformation accelerates across industries. The shift to cloud-native architectures, driven by the promise of scalability and agility, has introduced a complex threat landscape where data protection responsibilities are shared between cloud providers and enterprise security teams. Executives must navigate an intricate matrix of regulatory requirements, evolving compliance standards, and emerging risks such as supply chain vulnerabilities and sophisticated cyberattacks that exploit misconfigurations and identity breaches.
Against this backdrop, decision-makers are challenged to develop a holistic security strategy that aligns with business objectives while ensuring continuous visibility and control over sensitive information. Understanding the interplay between core security capabilities-from identity and access management to encryption, tokenization, and threat detection-is essential to building a resilient, zero-trust environment. This report synthesizes the latest industry developments, technological innovations, and regulatory dynamics, offering actionable insights that empower leaders to prioritize investments, optimize security architectures, and drive organizational resilience in the face of continuous digital disruption.
Understanding the Fundamental Transformative Shifts Redefining the Cloud Data Security Landscape Amid Rising Threats and Technological Innovation
The cloud data security ecosystem is undergoing a fundamental paradigm shift fueled by the convergence of artificial intelligence, zero-trust architectures, and an unprecedented volume of data generated at the edge. Organizations are moving beyond traditional perimeter-based defenses toward identity-centric models that verify every user, device, and workload before granting access to critical assets. This transformative shift is reinforced by the integration of machine learning and behavior analytics, enabling real-time threat detection and automated response workflows that drastically reduce dwell times for advanced persistent threats.
Simultaneously, we see the rise of converged security platforms that break down silos between cloud access security brokers, data loss prevention, and encryption technologies. These unified frameworks enable seamless policy enforcement across hybrid and multi-cloud environments, reducing complexity and operational overhead. Furthermore, growing adoption of Infrastructure as Code practices has empowered security teams to embed compliance controls early in the development lifecycle, ensuring that security is woven into applications from inception. As these trends accelerate, organizations that embrace cohesive, automation-driven security operations will gain a decisive advantage in safeguarding their cloud-native ecosystems.
Assessing the Cumulative Impact of 2025 United States Tariffs on Cloud Data Security Infrastructure, Costs, and Supply Chain Dynamics
In 2025, the cumulative impact of United States tariffs on cloud data security infrastructure has been profound, reshaping supply chains and elevating costs for essential hardware components. Duties levied under national security provisions have imposed up to 145% on certain Chinese imports and 32% on Taiwanese semiconductor-related hardware, driving enterprises to reevaluate sourcing strategies and seek alternate manufacturing hubs. Additionally, a 25% tariff on Canadian-manufactured networking equipment, effective March 4, 2025, has exacerbated delays for critical data center deployments while compelling providers to absorb higher capital expenditures or pass them on through service pricing.
These measures, intended to foster domestic manufacturing under the Section 232 review, have also triggered vendor realignments, with leading hyperscalers and security vendors accelerating investment in US-based production facilities. However, the transition is not seamless: extended lead times and component shortages have stretched project timelines by as much as a quarter compared to pre-tariff benchmarks, particularly for GPU-accelerated threat detection systems. As a result, cloud security firms and their enterprise clients are adapting by diversifying supply chains, extending hardware refresh cycles, and negotiating long-term contracts to mitigate price volatility and ensure continuity of service.
Unveiling Key Segmentation Insights to Decode Cloud Data Security Adoption Drivers Across Components, Deployment Models, Services, and Industry Verticals
A multidimensional view of the cloud data security market reveals distinct adoption patterns across core solution categories, deployment models, service frameworks, organizational scale, and industry verticals. In the component domain, identity and access management has surged as a critical control layer, complemented by robust encryption and tokenization services that safeguard data both at rest and in transit. Meanwhile, cloud access security brokers are evolving into API-first architectures that provide granular visibility across SaaS applications, whereas data loss prevention platforms are transitioning from reactive endpoint and network controls to proactive contextual analysis.
Deployment preferences underscore the prominence of hybrid cloud architectures, where enterprises leverage on-premises security investments alongside public cloud scalability to maintain data sovereignty and performance. The service model layer further differentiates market dynamics, as organizations increasingly favor SaaS-based security offerings for rapid deployment and streamlined management, while infrastructure- and platform-focused services retain strategic value for bespoke, high-performance environments. Organizational size shapes investment priorities as well, with large enterprises driving comprehensive security frameworks and smaller firms selectively adopting modular solutions. Across industry verticals, heavily regulated sectors such as banking and healthcare demand the most rigorous controls, whereas retail and IT service providers balance agility with essential compliance safeguards.
This comprehensive research report categorizes the Cloud Data Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component Type
- Service Model
- Deployment Model
- Organization Size
- Industry Vertical
Examining Key Regional Insights That Highlight Diverse Cloud Data Security Priorities and Adoption Patterns Across Americas, EMEA, and Asia-Pacific Markets
Regional imperatives play a pivotal role in shaping cloud data security strategies and investment priorities. The Americas market continues to lead in early adoption of advanced security capabilities, supported by mature regulatory frameworks such as GDPR and the California Consumer Privacy Act, as well as significant public cloud penetration. North American organizations are at the forefront of integrating AI-driven security automation and zero-trust models, while Latin American enterprises are accelerating cloud migration to modernize legacy infrastructures under cost constraints.
In Europe, the Middle East, and Africa, diverse compliance regimes and varying digital maturity levels drive differentiated approaches; Western Europe emphasizes stringent data residency and privacy controls, whereas emerging markets within the region prioritize foundational security hygiene and cloud-native resilience. Regulatory initiatives such as the EU’s NIS2 directive are catalyzing investment in unified security operations centers and cloud-native threat intelligence. Meanwhile, Asia-Pacific exhibits the fastest growth trajectory as governments across the region invest in digital economies and smart city projects, heightening demand for scalable, regionally compliant security frameworks. Cross-border data flow regulations and national cloud policies further influence the adoption cadence, compelling vendors and enterprises to align solutions with local governance and performance requirements.
This comprehensive research report examines key regions that drive the evolution of the Cloud Data Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Analyzing Leading Industry Players’ Strategic Moves and Innovations Driving Competitive Strength in the Global Cloud Data Security Sector
Leading technology and security vendors are actively shaping the competitive landscape through strategic partnerships, product innovation, and targeted acquisitions. Cloud access security broker pioneers have expanded their portfolios with API-based integrations, advanced threat analytics, and inline proxy capabilities to meet the requirements of modern SaaS ecosystems. Data loss prevention innovators are embedding machine learning to detect anomalous patterns in unstructured data, while encryption and tokenization providers are offering transparent, policy-driven solutions that integrate directly with development pipelines.
In the identity and access management arena, vendors are capitalizing on biometric authentication, passwordless access, and orchestration of privileged credentials to counter sophisticated identity-based threats. At the same time, key management providers are enhancing hardware security module offerings with cloud-based key lifecycle management services that support multi-cloud deployments. Furthermore, competitive differentiation is increasingly achieved through managed security services and threat intelligence partnerships, enabling vendors to deliver end-to-end security operations for enterprises lacking in-house expertise. M&A activity in the sector underscores a drive toward consolidated platforms that streamline policy enforcement and reduce integration overhead.
This comprehensive research report delivers an in-depth overview of the principal market players in the Cloud Data Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Amazon Web Services, Inc.
- Aqua Security Software Ltd.
- Check Point Software Technologies Ltd.
- CrowdStrike Holdings, Inc.
- Darktrace plc
- Fortinet, Inc.
- Google LLC
- International Business Machines Corporation
- McAfee Corp.
- Microsoft Corporation
- Netskope, Inc.
- Oracle Corporation
- Palo Alto Networks, Inc.
- Proofpoint, Inc.
- Qualys, Inc.
- SentinelOne, Inc.
- Sophos Ltd.
- Trend Micro Incorporated
- Wiz, Inc.
- Zscaler, Inc.
Actionable Recommendations for Industry Leaders to Fortify Cloud Data Security Strategies, Drive Innovation, and Navigate Emerging Threats with Confidence
Industry leaders must prioritize the integration of security capabilities across the cloud data lifecycle to address evolving threat vectors and operational challenges. Embedding zero-trust principles-continuous verification of every interaction-within application development and infrastructure provisioning will ensure that security controls are enforced consistently, regardless of where data resides. Furthermore, adopting converged security platforms that unify access brokers, data loss prevention, and encryption under a single policy framework simplifies management and enhances visibility across hybrid environments.
To mitigate supply chain risks and pricing volatility exacerbated by global trade policies, organizations should diversify hardware sourcing, negotiate long-term component agreements, and extend maintenance lifecycles through proactive refresh planning. Investing in AI-driven threat detection and response technologies can accelerate incident containment and reduce manual burden on security operations teams. Finally, fostering a security-centric culture through continuous training, cross-functional collaboration, and executive sponsorship will drive sustained adoption of best practices and ensure that cloud data security remains an enterprise-wide priority rather than a siloed IT initiative.
Exploring the Rigorous Research Methodology Underpinning This Report to Ensure Comprehensive, Validated, and Actionable Cloud Data Security Insights
This report’s findings and insights are grounded in a comprehensive research methodology designed to ensure accuracy, relevance, and actionable value. Primary research included detailed interviews with senior security and IT decision-makers across enterprises, cloud service providers, and solution vendors, capturing diverse perspectives on real-world challenges and strategic priorities. Secondary research encompassed an extensive review of vendor documentation, white papers, regulatory guidelines, and peer-reviewed publications to identify prevailing technology trends and compliance requirements.
Market dynamics and segmentation analyses were validated through a triangulation process, cross-referencing quantitative data points with qualitative feedback from industry experts. Vendor and solution profiles were assessed based on technology maturity, go-to-market strategies, and customer reference evaluations. Throughout the research, rigorous data cleansing and peer review ensured that conclusions reflect the most current developments and offer robust guidance for executives seeking to optimize their cloud data security posture.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Cloud Data Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Cloud Data Security Market, by Component Type
- Cloud Data Security Market, by Service Model
- Cloud Data Security Market, by Deployment Model
- Cloud Data Security Market, by Organization Size
- Cloud Data Security Market, by Industry Vertical
- Cloud Data Security Market, by Region
- Cloud Data Security Market, by Group
- Cloud Data Security Market, by Country
- United States Cloud Data Security Market
- China Cloud Data Security Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1908 ]
Concluding Perspectives on the Imperative of Cloud Data Security Resilience and Strategic Readiness in an Evolving Risk Environment
The accelerating shift to cloud-first operations presents both unparalleled opportunities and complex security challenges for organizations worldwide. As threats evolve in tandem with technology innovations-driven by AI, edge computing, and digital ecosystems-maintaining robust data security requires a dynamic, integrated approach. Leaders who adopt zero trust frameworks, leverage converged security platforms, and invest in advanced analytics will be best positioned to protect sensitive information, uphold regulatory compliance, and drive digital transformation initiatives with confidence.
In an environment where supply chain disruptions and trade policies can reverberate across infrastructure planning, diversifying sourcing strategies and embracing automation are critical success factors. By aligning security investments with business objectives and fostering a culture of shared responsibility, enterprises can achieve a resilient cloud security posture that supports agility and innovation. Ultimately, the journey toward comprehensive cloud data protection is continuous, demanding vigilant adaptation and strategic foresight to safeguard organizational value and trust.
Take Decisive Action with Expert Guidance to Secure Your Cloud Data Infrastructure—Contact Ketan Rohom to Access the Complete Market Research Report
To gain unparalleled insights into securing your cloud data assets in an era of rapid transformation and evolving threats, reach out to Ketan Rohom, Associate Director, Sales & Marketing. Engage in a personalized consultation to explore how our comprehensive market research report can inform your strategic planning, accelerate decision-making, and ensure robust protection across your hybrid and multi-cloud environments. Whether you are evaluating next-generation encryption and tokenization solutions, refining identity and access management frameworks, or navigating the implications of global trade policies, Ketan will guide you through the report’s actionable findings and industry benchmarks. Take this crucial step toward fortifying your cloud data security posture and sustaining competitive advantage by contacting Ketan today for exclusive access to the full analysis.

- How big is the Cloud Data Security Market?
- What is the Cloud Data Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




