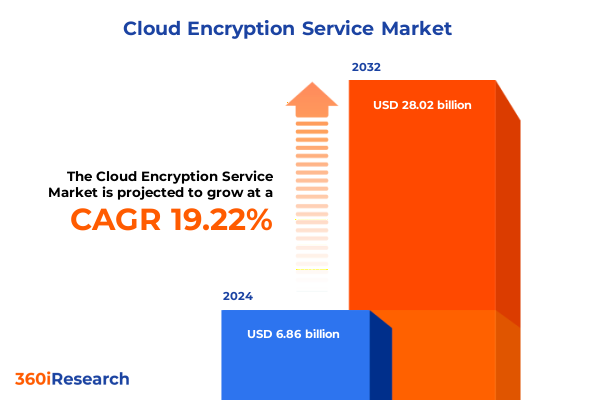
The Cloud Encryption Service Market size was estimated at USD 8.17 billion in 2025 and expected to reach USD 9.62 billion in 2026, at a CAGR of 19.24% to reach USD 28.02 billion by 2032.
Exploring the Convergence of Cryptographic Methods and Enterprise Cloud Security Imperatives in an Era of Heightened Regulatory and Threat Pressures
In today’s digital economy, organizations are navigating an unprecedented surge in data generation and storage demands, driven by rapid cloud adoption and the proliferation of remote work models. This paradigm shift has elevated the importance of robust data protection strategies, positioning encryption services as a cornerstone of enterprise security architectures. As organizations accelerate their migration to public, private, and hybrid cloud environments, the imperative to maintain data confidentiality, integrity, and availability has never been more acute.
Against this backdrop, cloud encryption services have evolved from optional add-ons into essential components of modern IT infrastructures. By providing seamless integration with storage, computing, and networking layers, these solutions safeguard sensitive information at each stage of its lifecycle. Moreover, advanced key management frameworks and policy-driven controls are empowering security teams to enforce granular access restrictions without compromising operational agility. As the surface area for cyber threats expands, encryption mechanisms now play a critical role in mitigating risks posed by both external attackers and potential insiders.
This executive summary distills crucial insights from the current landscape of cloud encryption services, highlighting transformative shifts, regulatory influences, and emerging best practices. Subsequent sections will examine the cumulative impact of United States tariffs in 2025, uncover segmentation and regional perspectives, spotlight leading providers, and deliver strategic recommendations. By weaving together market intelligence and expert analysis, this summary offers a cohesive foundation for decision-makers seeking to strengthen their data protection postures in an era defined by persistent threat activity and evolving compliance requirements.
Unveiling the Pivotal Shifts Redefining Cloud Encryption Services Including Quantum-Resistant Algorithms Zero Trust Adoption and Hybrid Deployment Models
The past two years have witnessed a profound transformation in how organizations approach cloud encryption, spurred by escalating threat sophistication and regulatory intensification. Advanced persistent threats have increasingly leveraged automation and artificial intelligence to identify vulnerabilities, prompting security teams to adopt zero trust architectures that treat every access request as untrusted by default. This shift has elevated the role of encryption as an active defense mechanism, integrated into identity and access management workflows and continuous monitoring solutions.
Simultaneously, the growing discourse around quantum computing has accelerated investments in quantum-resistant encryption algorithms. While commercial quantum systems remain nascent, forward-looking enterprises are proactively piloting lattice-based and code-based cryptographic methods to future-proof their data assets. At the same time, multi-party computation and homomorphic encryption are emerging as innovative techniques that enable secure data processing in encrypted form, opening new avenues for collaborative analytics without exposing raw datasets.
Moreover, the convergence of cloud-native key management platforms with container orchestration frameworks is streamlining encryption deployment across dynamic microservices environments. Policy-as-code paradigms now facilitate automated key rotation, revocation workflows, and compliance attestation, reducing manual overhead and human error. From a regulatory standpoint, global mandates such as GDPR, CCPA, and evolving data residency requirements are compelling organizations to deploy context-aware encryption policies that align with jurisdictional stipulations. These cumulative shifts underscore a rapidly maturing cloud encryption ecosystem in which agility, innovation, and compliance coalesce.
Assessing the Far-Reaching Effects of 2025 United States Technology Tariffs on Cloud Encryption Service Adoption and Supply Chain Dynamics
In 2025, the United States implemented a sweeping tariff regime targeting imported semiconductor components and specialized hardware modules critical to cloud encryption services. This policy aimed to bolster domestic manufacturing and secure supply chains against geopolitical disruptions but has introduced new cost and procurement complexities for service providers and end-users alike. Hardware security modules, network encryption appliances, and high-performance cryptographic accelerators have seen input cost increases of up to 20 percent, leading to downstream effects on service pricing models.
As a result, many cloud service providers have accelerated their shift toward software-defined encryption solutions that leverage general-purpose compute instances and native cloud key vaults, reducing reliance on specialized hardware. Meanwhile, organizations constrained by budgetary pressures have reevaluated on-premise encryption gateways, often deferring hardware refresh cycles in favor of virtualized alternatives. Although this transition bolsters deployment flexibility, it also demands heightened attention to instance isolation and performance tuning to preserve throughput and latency targets.
The tariff impact has also catalyzed collaborative purchasing agreements among consortiums of large enterprises and public sector entities, pooling procurement volumes to negotiate more favorable pricing and lead times. These alliances underscore the strategic importance of supplier diversification and long-term contract negotiations in mitigating the effects of trade policy volatility. Looking ahead, encryption service roadmaps increasingly emphasize software portability and cloud neutrality, ensuring that organizations can dynamically redirect workloads across regions and vendors without incurring prohibitive hardware dependencies.
Deriving Actionable Insights from Deployment Type Encryption Variants Organizational Scale and Industry-Specific Cloud Encryption Trends
Disaggregating the cloud encryption market by deployment environment reveals divergent adoption patterns between fully managed public cloud offerings and self-hosted on-premise solutions. Large enterprises often opt for hybrid deployments that combine a centralized cloud key management platform with localized hardware security modules deployed in data centers, balancing control and scalability. By contrast, smaller organizations tend to prioritize turnkey cloud-native encryption services that abstract key management complexities and reduce capital expenditures on specialized hardware.
When evaluating encryption modalities, the choice between protecting data at rest, securing information in transit, or ensuring end-to-end encryption typically aligns with specific use cases. Data at rest encryption remains foundational for regulatory compliance and storage security, whereas in-transit encryption through TLS and VPN channels addresses network interception threats. End-to-end encryption solutions are gaining traction among industries that demand absolute data confidentiality, enabling secure collaboration across untrusted networks without exposing plaintext to intermediary services.
The segmentation by organization size highlights that large enterprises allocate substantial resources toward bespoke encryption frameworks, often integrated into mature governance processes and risk management programs. In contrast, small and medium enterprises lean toward subscription-based models that deliver pre-configured keys and policy templates, enabling rapid time to value. Across industry verticals, financial services firms mandate rigorous encryption controls to satisfy banking regulations, government agencies enforce stringent protocols for sensitive citizen data, healthcare providers prioritize HIPAA-aligned at rest encryption for patient records, and technology and telecommunications companies leverage a balanced mix of encryption types to secure distributed workloads and customer communications.
This comprehensive research report categorizes the Cloud Encryption Service market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Encryption Type
- Organization Size
- Industry Vertical
Revealing Regional Dynamics Shaping Cloud Encryption Services Across Americas Europe Middle East Africa and Asia-Pacific Markets
Examining regional dynamics paints a multifaceted picture of cloud encryption adoption shaped by local regulatory regimes, technological infrastructures, and market maturity. In the Americas, the United States and Canada lead in implementing zero trust frameworks and containerized encryption services, while Latin American enterprises are rapidly modernizing legacy on-premise guardrails by integrating cloud key management into hybrid architectures. Cross-border data flow considerations in this region drive investments in centralized key vaults with geo-fencing capabilities.
Across Europe, the Middle East, and Africa, stringent data protection laws such as the EU’s General Data Protection Regulation have elevated data sovereignty as a key driver for encryption deployments. Enterprises in Western Europe are increasingly leveraging regional cloud providers to align with compliance mandates, while emerging markets in the Middle East and Africa are investing in secure data center expansions. This regional patchwork of regulations and infrastructure readiness requires service providers to offer adaptable encryption configurations and localized key management solutions.
In the Asia-Pacific region, the market exhibits considerable heterogeneity. Advanced economies like Japan and Australia demonstrate robust uptake of end-to-end encryption services integrated with advanced analytics, whereas Southeast Asian nations balance rapid digital transformation initiatives with nascent privacy frameworks. China’s indigenous cloud ecosystems emphasize sovereign encryption standards, prompting global service providers to forge partnerships with domestic players. As Asia-Pacific continues its digital acceleration, encryption services that offer seamless cross-border compliance and low-latency key exchange protocols will gain significant traction.
This comprehensive research report examines key regions that drive the evolution of the Cloud Encryption Service market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Innovations and Strategic Movements by Leading Cloud Encryption Service Providers Driving Market Leadership and Technological Advancements
Within the competitive landscape, leading technology firms have charted distinct innovation paths in cloud encryption services. Amazon Web Services expanded its Key Management Service to include multi-region replication and custom key store integrations, enabling enterprises to maintain sovereign control over cryptographic keys. Similarly, Microsoft introduced next-generation confidential computing instances that leverage hardware-based enclaves to protect data during processing, complementing its existing key vault offerings with attestation services and advanced policy controls.
Google Cloud advanced its envelope encryption capabilities by integrating open-source Key Transparency frameworks, allowing organizations to audit key usage and detect unauthorized modifications. Meanwhile, IBM continued to leverage its hardware security pedigree with the Hyper Protect Crypto Services portfolio, offering client-side encryption endpoints and FIPS 140-2 Level 4 certified key management appliances. Oracle’s Cloud Infrastructure responded by bundling encryption and key management into unified security zones, simplifying access governance for inter-cloud workloads.
Beyond hyperscale providers, specialized startups and managed security service providers have introduced niche encryption platforms that focus on use-case specific innovations. These include solutions for secure multi-party computation, homomorphic processing of encrypted data, and cloud-agnostic key synchronization across public, private, and edge environments. As competition intensifies, strategic partnerships, open-source contributions, and acquisitions are likely to further differentiate service portfolios and drive accelerated feature delivery.
This comprehensive research report delivers an in-depth overview of the principal market players in the Cloud Encryption Service market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Akeyless Cyber Ltd.
- Amazon Web Services, Inc.
- Box, Inc.
- CipherCloud, Inc.
- CyberArk Software Ltd.
- DigiCert, Inc.
- Egnyte, Inc.
- Entrust Corporation
- Fortanix, Inc.
- Google LLC
- HashiCorp, Inc.
- IBM Corporation
- Keyfactor, Inc.
- Microsoft Corporation
- Netskope, Inc.
- PKWARE, Inc.
- Thales S.A.
- Unbound Tech Ltd.
- Virtru Corporation
- Zscaler, Inc.
Proposing Concrete Strategic and Operational Measures to Enhance Cloud Encryption Adoption Strengthen Compliance and Foster Competitive Differentiation
Industry leaders should adopt a proactive encryption strategy that aligns with overarching zero trust objectives, ensuring that cryptographic controls are embedded at the earliest stages of application development and data lifecycle management. By integrating encryption policies into continuous integration and continuous deployment pipelines, organizations can enforce security gates and automate compliance checks, minimizing manual interventions. Furthermore, enterprises should evaluate the feasibility of hybrid key management architectures that combine the flexibility of cloud-native vaults with the assurance of on-premise hardware security modules to balance agility with control.
To address emerging threats from quantum-capable adversaries, organizations must develop a quantum-readiness roadmap, piloting post-quantum algorithms alongside existing encryption schemes. Engaging with industry consortiums and standards bodies will provide early access to validated implementations and interoperability guidelines. In parallel, building cross-functional collaboration between security, legal, and compliance teams will help align encryption policies with evolving regulatory frameworks and contractual obligations.
Finally, cultivating vendor ecosystems through strategic partnerships and managed services can accelerate the deployment of advanced encryption capabilities. By leveraging external expertise for specialized functions such as key lifecycle management, cryptographic audit logging, and secure enclave orchestration, organizations can optimize resource allocation and accelerate time to value. These actionable measures will not only enhance security postures but also foster differentiation and resilience in an increasingly competitive digital marketplace.
Detailing the Systematic Research Methodology Including Data Collection Analysis and Validation Processes Underpinning the Cloud Encryption Service Study
The research underpinning this cloud encryption service study employed a robust, multi-phase methodology designed to ensure data accuracy, relevance, and comprehensiveness. Initial secondary research involved analyzing publicly available white papers, regulatory guidelines, and technical specifications from standards organizations. This phase laid the groundwork for understanding prevailing encryption frameworks, compliance requirements, and technology roadmaps.
Subsequently, primary research consisted of in-depth interviews with senior executives, security architects, and risk management professionals across diverse industry verticals. These qualitative insights provided context around real-world deployment challenges, feature priorities, and strategic objectives. In parallel, structured surveys captured quantitative data on adoption trends, preferred encryption modalities, and procurement considerations, enabling cross-segment analysis by deployment type, organization size, and industry.
Data triangulation was achieved by cross-referencing primary findings with vendor press releases, published case studies, and neutral third-party benchmarks. An expert advisory panel comprising cryptographers, cloud architects, and compliance specialists reviewed preliminary insights to validate assumptions and refine analytical frameworks. This systematic approach ensured that the study’s conclusions reflect both macro-level trends and nuanced sectoral dynamics.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Cloud Encryption Service market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Cloud Encryption Service Market, by Encryption Type
- Cloud Encryption Service Market, by Organization Size
- Cloud Encryption Service Market, by Industry Vertical
- Cloud Encryption Service Market, by Region
- Cloud Encryption Service Market, by Group
- Cloud Encryption Service Market, by Country
- United States Cloud Encryption Service Market
- China Cloud Encryption Service Market
- Competitive Landscape
- List of Figures [Total: 15]
- List of Tables [Total: 636 ]
Closing Reflections on the Strategic Imperatives and Future Prospects Shaping the Evolution of Cloud Encryption Services in Complex Digital Environments
As organizations navigate the intricate matrix of digital transformation, encryption emerges as a non-negotiable element of data protection strategies. The interplay of regulatory mandates, threat evolution, and technological innovation underscores the necessity for adaptable encryption frameworks that can scale with enterprise demands. By embracing software-defined encryption, zero trust paradigms, and quantum-resistant techniques, security teams can establish resilient defenses that safeguard critical assets across cloud and hybrid environments.
Moreover, understanding the nuanced preferences across deployment types, organization sizes, and industry verticals empowers decision-makers to tailor encryption policies that deliver maximum impact. Regional considerations further highlight the importance of selecting providers and configurations that align with local data sovereignty and compliance landscapes. Strategic partnerships with leading vendors and managed service specialists can streamline implementation, accelerate innovation, and reduce operational complexity.
Ultimately, the continued maturation of cloud encryption services will hinge on a collaborative ecosystem approach, where standardization, open interfaces, and shared best practices drive collective security enhancements. The insights presented in this summary serve as a foundational blueprint for crafting robust, future-ready encryption strategies that not only meet today’s requirements but also anticipate the challenges of tomorrow.
Connect with Associate Director of Sales and Marketing to Secure Comprehensive Cloud Encryption Service Insights Tailored to Your Strategic Priorities
To explore how these insights can directly inform your strategic priorities, reach out to Ketan Rohom, Associate Director of Sales & Marketing, to secure the complete market research report. Ketan brings extensive expertise in aligning cloud encryption service intelligence with organizational objectives and will guide you through a tailored overview of the study’s findings, implications, and complementary deliverables. Engaging with Ketan ensures you gain access to detailed analyses, proprietary data visualizations, and customized advisory that support your decision-making processes. Don’t miss the opportunity to equip your teams with the actionable, in-depth perspectives necessary to elevate your security posture and competitive positioning within the evolving cloud encryption landscape.

- How big is the Cloud Encryption Service Market?
- What is the Cloud Encryption Service Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




