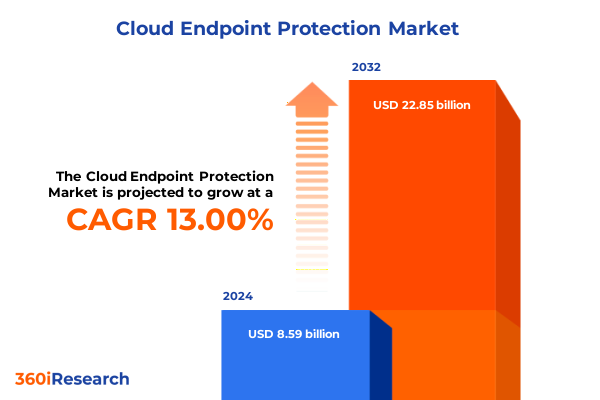
The Cloud Endpoint Protection Market size was estimated at USD 9.65 billion in 2025 and expected to reach USD 10.83 billion in 2026, at a CAGR of 13.10% to reach USD 22.85 billion by 2032.
Revealing the Critical Role of Cloud Endpoint Protection in Securing Digital Assets, Mitigating Risk, and Ensuring Compliance in Dynamic IT Environments
In an era where digital transformation initiatives accelerate at unprecedented speed, cloud endpoint protection emerges as a pivotal defense mechanism against a sophisticated threat landscape. Organizations are no longer constrained by physical perimeters; endpoints ranging from employee laptops to IoT devices extend corporate networks into unpredictable territory. As adversaries deploy stealthy attack techniques and exploit vulnerabilities at scale, decision-makers require assurance that endpoints-once considered the first line of defense-remain fortified with advanced detection, prevention, and remediation capabilities. Introducing robust cloud endpoint protection frameworks not only mitigates risk but also fosters resilience by integrating real-time threat intelligence and centralized policy enforcement. This report’s executive summary serves as a guide to understanding how businesses can navigate the complexities of securing distributed environments, harmonize endpoint security strategies with broader cyber defense architectures, and align investments with both operational priorities and regulatory mandates. Through a deep dive into market dynamics, supply chain pressures, segmentation nuances, and actionable recommendations, readers will gain a holistic perspective on the rapidly evolving cloud endpoint protection domain, equipping them to safeguard critical assets as digital ecosystems continue to expand and diversify.
Understanding How Cloud Endpoint Protection Is Transforming Security Strategies Through AI, Automation, and Zero Trust Frameworks Across Enterprises
Cloud endpoint protection has undergone transformative shifts that redefine how enterprises approach security, moving from reactive threat response to proactive risk management powered by cutting-edge technologies. The incorporation of artificial intelligence and machine learning algorithms now enables predictive detection of anomalous behavior patterns, reducing dwell time and mitigating potential breaches before they escalate. Concurrently, automation pipelines orchestrate incident response playbooks, diminishing manual intervention and accelerating remediation processes. Zero trust frameworks, once a conceptual blueprint, have become central to endpoint strategies, enforcing continuous authentication and strict microsegmentation regardless of device location. Furthermore, the convergence of endpoint protection with secure access service edge architectures allows organizations to enforce unified security policies across network and cloud environments. These shifts reflect a paradigm where agility and innovation drive security outcomes, compelling leaders to reevaluate legacy tools in favor of solutions that can adapt to evolving threats at machine speed. Understanding these transformative dynamics is essential for stakeholders seeking to future-proof their security posture and maintain operational continuity in an increasingly digital-first world.
Examining the Far-Reaching Consequences of 2025 United States Tariffs on Cloud Endpoint Protection Supply Chains, Pricing Models, and Adoption Trends
The implementation of new United States tariffs in 2025 has imparted a cumulative impact across the cloud endpoint protection ecosystem, influencing supply chain economics, vendor pricing structures, and adoption trajectories. As duties on imported hardware and software components rose, vendors have revisited procurement strategies, shifting towards domestic or nearshore suppliers to contain costs and maintain service-level commitments. These adjustments have, in turn, cascaded to end users, where total cost of ownership calculations now account for augmented import expenses and potential pass-through charges, prompting some buyers to renegotiate contracts or delay large-scale rollouts. Simultaneously, vendors have explored alternative commercialization models, including usage-based pricing and subscription bundling, to provide flexibility amidst cost pressures. The tariff-induced disruption has also spurred increased collaboration between government agencies and industry consortia to ensure compliance and streamline licensing complexities. Ultimately, while tariffs have introduced short-term headwinds, they have catalyzed innovation in sourcing, pricing, and partnership strategies, underscoring the importance of supply chain resilience in sustaining robust endpoint protection deployments.
Uncovering Strategic Opportunities Through In-Depth Segmentation Analysis of Component, Security Type, Deployment, Organization Size, and Industry Dynamics
Insight into market segmentation reveals strategic pathways for vendors and buyers to sharpen their focus and tailor solutions to unique requirements. The component dimension delineates services into managed offerings that deliver proactive monitoring and rapid incident handling, alongside professional services that provide custom integration and expert advisory. In parallel, software splits between integrated platform solutions that unify threat prevention, detection, and response under a single interface and stand-alone options that address specific use cases with focused functionality. When considering security type, stakeholders differentiate between advanced endpoint detection and response platforms designed for deep forensic analysis and real-time alerting, and traditional endpoint protection platforms optimized for signature-based defense and policy enforcement. Deployment preferences further stratify into cloud-based architectures that promise scalability, remote manageability, and reduced local infrastructure overhead, contrasted with on-premises implementations that cater to organizations with stringent data sovereignty or latency constraints. The organizational dimension distinguishes requirements of large enterprises-with sprawling global estates and complex compliance mandates-from small and medium enterprises seeking simplicity, cost-effectiveness, and ease of deployment. Finally, end user industries spanning BFSI, government and defense, healthcare, IT and telecom, manufacturing, and retail each present specialized threat profiles, regulatory pressures, and operational imperatives, demanding tailored endpoint security strategies that align to sector-specific governance frameworks.
This comprehensive research report categorizes the Cloud Endpoint Protection market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Security Type
- Deployment Mode
- End User Industry
Evaluating Regional Variances in Cloud Endpoint Protection Uptake and Innovation Across Americas, Europe Middle East and Africa, and Asia Pacific Markets
Regional variations in cloud endpoint protection adoption underscore how macroeconomic factors, regulatory environments, and threat landscapes shape security investments. In the Americas, early adopters leverage mature cloud infrastructures and broad regulatory standards to deploy advanced threat protection and centralized management capabilities. North American enterprises prioritize integration with existing SIEM and SOAR platforms, while Latin American organizations focus on cost-effective, managed services that address limited in-house cybersecurity talent. Moving to Europe, Middle East, and Africa, evolving data privacy regulations drive a careful balance between cloud innovation and compliance, with many organizations opting for hybrid deployments to maintain data within national boundaries. In the Middle East, rising cyber insurance requirements are accelerating investment in proactive endpoint detection technologies, while African markets emphasize scalable, lightweight solutions that can operate with constrained connectivity. Across Asia-Pacific, high-growth economies in China and India witness increasing demand for integrated platform software capable of mitigating sophisticated regional threats, whereas governments and large enterprises in Australia and Japan invest heavily in endpoint detection and response tools to safeguard critical infrastructure. This regional mosaic highlights the necessity of aligning security strategies to local market conditions, regulatory frameworks, and ecosystem maturity levels.
This comprehensive research report examines key regions that drive the evolution of the Cloud Endpoint Protection market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Leading Cloud Endpoint Protection Providers and Their Differentiation Strategies Through Technology, Services, and Market Positioning
Leading providers of cloud endpoint protection compete through differentiated service portfolios, technological innovation, and strategic partnerships. Established incumbents focus on expanding unified platforms that encompass threat intelligence, device posture management, and cloud workload protection, leveraging deep integration across their broader enterprise security suites. At the same time, specialized pure-play vendors emphasize modular architectures that allow rapid adoption of emerging capabilities such as behavior-based anomaly detection, sandbox analysis, and real-time forensics. Collaboration with cloud service providers and managed security service partners enhances deployment flexibility and support coverage, enabling tailored solutions for both global enterprises and mid-market clients. Investment in open APIs and developer ecosystems further accelerates integration with SIEM, XDR, and identity management platforms, fostering a more holistic view of risk across the attack surface. Competitive differentiation also arises from the ability to deliver advanced automation, low-latency detection, and high-fidelity threat scoring, empowering security operations teams to focus efforts on critical incidents. Taken together, these approaches underline the importance of agility and innovation in maintaining leadership positions within a rapidly evolving cloud endpoint protection landscape.
This comprehensive research report delivers an in-depth overview of the principal market players in the Cloud Endpoint Protection market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Bitdefender
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- CrowdStrike Holdings, Inc.
- McAfee Corp.
- Microsoft Corporation
- Palo Alto Networks, Inc.
- SentinelOne, Inc.
- Sophos Ltd.
- Trend Micro Incorporated
- VMware
Delivering Practical Strategic Guidance for Industry Leaders to Enhance Cloud Endpoint Protection Maturity, Improve ROI, and Future-Proof Security Architectures
Industry leaders must adopt a multifaceted approach that balances strategic vision with tactical execution to strengthen their cloud endpoint protection posture. First, embedding artificial intelligence and machine learning into detection workflows will reduce mean time to detect and enable predictive threat hunting. Organizations should also formalize zero trust principles by enforcing continuous verification and least-privilege access across all endpoints. Establishing a unified security operations center that integrates endpoint telemetry with network and cloud logs can expedite incident response and offer a comprehensive risk view. Investing in skill development and continuous training will ensure teams remain sharp on emerging threats and best practices. To optimize costs, executives may consider consolidating point products into integrated platforms, negotiating flexible subscription terms, and evaluating managed service models to offload routine monitoring tasks. Cross-functional collaboration between IT, security, and business units will drive alignment between security outcomes and organizational objectives, enhancing buy-in and resource allocation. Finally, regular tabletop exercises and crisis simulations will validate resilience plans and foster a culture of continuous improvement. By taking these steps, security executives can bridge the gap between policy and practice, ensuring that cloud endpoint protection capabilities deliver tangible business value.
Detailing the Comprehensive Research Approach Combining Qualitative Interviews, Quantitative Surveys, and Secondary Data to Ensure Validity and Reliability
The research underpinning this report employed a rigorous methodology designed to capture both breadth and depth of market insights. Qualitative interviews were conducted with senior security and IT decision-makers across diverse industries to understand drivers, challenges, and deployment experiences in real-world environments. A quantitative survey of over two hundred organizations further quantified adoption rates, spending priorities, and satisfaction metrics, enabling statistical validation of hypotheses. Additionally, a thorough review of secondary data sources-including regulatory filings, policy announcements, and public financial disclosures-provided context on tariff impacts, vendor partnerships, and technology roadmaps. Data triangulation techniques ensured that findings were cross-validated across primary and secondary inputs, while an expert advisory panel reviewed interim analyses to refine interpretations and mitigate bias. The synthesis of these approaches produced a comprehensive and reliable view of the global cloud endpoint protection landscape, balancing empirical rigor with actionable insights relevant to practitioners and executives alike.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Cloud Endpoint Protection market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Cloud Endpoint Protection Market, by Component
- Cloud Endpoint Protection Market, by Security Type
- Cloud Endpoint Protection Market, by Deployment Mode
- Cloud Endpoint Protection Market, by End User Industry
- Cloud Endpoint Protection Market, by Region
- Cloud Endpoint Protection Market, by Group
- Cloud Endpoint Protection Market, by Country
- United States Cloud Endpoint Protection Market
- China Cloud Endpoint Protection Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 1113 ]
Summarizing Key Findings and Emphasizing the Imperative of Investing in Advanced Cloud Endpoint Protection Capabilities to Navigate Emerging Threats
Drawing together the key threads of this report, it is clear that cloud endpoint protection sits at the intersection of technological innovation, supply chain dynamics, and evolving threat landscapes. The integration of AI-driven detection, automation, and zero trust architectures has transformed endpoint security from perimeter-based defense to a contextual, risk-centric paradigm. At the same time, 2025 tariffs have reshaped vendor strategies and procurement models, prompting shifts toward localized sourcing and alternate pricing frameworks. Segmentation analysis underscores the need for tailored approaches based on service versus software preferences, security type capabilities, deployment models, organizational scale, and industry-specific imperatives. Regional insights reveal that what drives adoption in the Americas may differ significantly from motivators in EMEA or Asia-Pacific markets. Leading vendors continue to differentiate through platform integration, modular capabilities, and ecosystem partnerships, while security executives are urged to adopt strategic recommendations that bridge policy and practice. As enterprises confront a continuously evolving cyber threat landscape, investing in advanced endpoint protection capabilities will be indispensable to safeguard critical assets, maintain regulatory compliance, and preserve stakeholder trust.
Engage with Our Associate Director, Sales and Marketing, to Secure Exclusive Access to the Full Cloud Endpoint Protection Market Research Report and Drive Your Security Strategy
Engaging directly with Ketan Rohom, Associate Director of Sales & Marketing, unlocks the opportunity to acquire a comprehensive market research report that will empower security architects and business leaders to make informed decisions supported by rigorous analysis and actionable insights. By initiating a conversation, organizations stand to gain exclusive access to in-depth data, expert commentary, and strategic frameworks tailored to optimize endpoint protection investments and accelerate time to value. Connecting will pave the way for personalized demonstrations of key findings, flexible licensing options, and premium support services designed to drive adoption and cultivate competitive advantage. Secure your organization’s future posture by partnering with a seasoned advisor who understands both the technical nuances and commercial imperatives of cloud endpoint protection, ensuring that your security strategy is aligned with the latest threat landscapes and regulatory requirements. Reach out today to schedule a bespoke consultation, benefit from early-bird discounts, and leverage a research asset that will guide your security roadmap through 2025 and beyond

- How big is the Cloud Endpoint Protection Market?
- What is the Cloud Endpoint Protection Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




