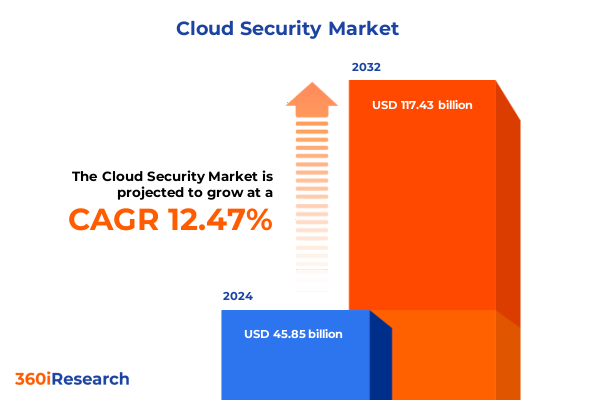
The Cloud Security Market size was estimated at USD 51.30 billion in 2025 and expected to reach USD 57.47 billion in 2026, at a CAGR of 12.55% to reach USD 117.43 billion by 2032.
Surveying the Evolving Trajectory of Cloud Security to Frame Strategic Priorities Amid Intensifying Threat Landscapes and Rapid Digital Advancement
The velocity of digital transformation has propelled cloud security from a niche concern into the cornerstone of enterprise risk management. As organizations accelerate migration efforts to harness flexibility, cost efficiencies, and global reach, the potential for misconfigurations, sophisticated breaches, and compliance gaps has amplified concurrently. This dynamic environment demands a concise yet comprehensive overview of critical influences, shaping the strategic priorities of security teams, technology vendors, and decision-makers alike.
This executive summary synthesizes key findings across multiple dimensions: technological innovations, regulatory drivers, and external economic pressures. It frames the context for actionable recommendations by tracing emerging shifts in threat landscapes, examining the ripple effects of recent tariff policies, offering deep segmentation insights, and highlighting regional variances. The result is an integrated view designed to inform security investments, strategic planning, and vendor partnerships as enterprises strive to build resilient, scalable, and future-ready architectures.
Navigating the Profound Transformations Reshaping Cloud Security Through Emerging Technologies Heightened Regulations and Evolving Threat Actor Strategies
Cloud security is undergoing a period of profound transformation driven by the convergence of innovative architectures, advanced analytics, and evolving regulations. Zero trust principles have surged to the forefront, shifting the focus from perimeter defense to continuous verification of every transaction. This approach, once confined to early adopters, is maturing into a mainstream strategy as organizations seek to mitigate lateral movement by threat actors within distributed environments. Simultaneously, the integration of artificial intelligence into detection and response platforms is redefining incident management, enabling real-time anomaly detection and automated remediation workflows that drastically reduce dwell time.
Beyond technological catalysts, regulatory frameworks continue to exert significant influence. Data privacy mandates such as recent updates to federal protections and cross-border data transfer standards have heightened the imperative for visibility and control over cloud-resident information. These mandates intersect with emerging cybersecurity directives aimed at critical infrastructure sectors, compelling service providers to bake compliance into platform design and delivery. At the same time, threat actors are evolving their tactics, leveraging supply chain compromises and living-off-the-land techniques to evade traditional controls. This multifaceted shift demands a coordinated response across tool vendors, managed service providers, and internal security operations teams, fostering tighter integration of orchestration, threat intelligence, and unified governance.
Assessing the Comprehensive Implications of 2025 United States Tariff Measures on Cloud Security Supply Chains Operational Budgets and Innovation Strategies
The tariff measures introduced by the United States in early 2025 have exerted a tangible impact on the procurement and deployment of cloud security infrastructure. By increasing duties on imported hardware components, security appliance prices have risen, prompting organizations to reassess sourcing strategies and total cost of ownership. Many enterprises are now evaluating alternative suppliers, accelerating the shift toward software-centric controls and cloud-native services that mitigate exposure to hardware inflation. This recalibration underscores a broader trend toward consumption-based security models that align costs with usage and reduce capital expenditure burdens.
In parallel, tariffs have influenced investment in domestic data center expansions as vendors seek to localize manufacturing and assembly to bypass import levies. This trend has spurred greater collaboration between cloud providers and regional service integrators, fostering localized technology ecosystems. While short-term budgetary pressures have challenged some projects, the tariff-induced ripple effects have ultimately catalyzed innovation in cloud security service delivery. Organizations with the agility to adapt procurement, embrace managed security offerings, and optimize licensing structures have been best positioned to navigate this evolving cost landscape.
Uncovering Strategic Depth Through Comprehensive Cloud Security Segmentation Across Offerings Service Models Deployment Modes and Industry Verticals
A nuanced understanding of the market emerges when examined through the prism of diverse segmentation dimensions, each shedding light on distinct value drivers. Based on offerings, service providers and technology vendors have reinforced their portfolios across managed services and professional services, recognizing that continuous monitoring and expert consultation are indispensable for organizations facing an expanding threat surface. Within solutions, the rise of cloud access security brokers has addressed the need for granular control of user interactions, while advanced detection and response platforms have scaled to handle the velocity of cloud-native workloads. Infrastructure entitlement management tools have grown in importance, enforcing least-privilege access across sprawling identities, and cloud security posture management solutions now automate compliance validation at unprecedented scope. Complementing these, workload protection platforms guard compute environments against misconfigurations and runtime exploits.
When assessed by service model, infrastructure-as-a-service remains the backbone for customizable deployments, though platform-as-a-service offerings have attracted security investments aimed at securing containerized and serverless functions. Software-as-a-service applications continue to drive demand for embedded security controls and seamless identity federation. From the perspective of security type, application security frameworks have incorporated shift-left testing methodologies to catch vulnerabilities early, data security services have expanded encryption and tokenization capabilities, identity and access security platforms have introduced adaptive authentication, and network security solutions have integrated microsegmentation to contain lateral threats.
Organizational dimensions further illuminate adoption patterns. Large enterprises have leveraged scale to unify security operations across cloud meshes, while small and midsize enterprises prioritize turnkey solutions that deliver robust protections with minimal operational overhead. In deployment modes, private cloud implementations appeal to highly regulated industries seeking dedicated environments, whereas public cloud platforms attract entities that value rapid provisioning and elastic scaling. Finally, industry vertical dynamics reveal that financial institutions emphasize resilient access controls, energy and utilities entities focus on safeguarding operational technology, healthcare organizations drive data-centric security, and technology and telecom firms lead in securing platform innovations. Retailers, hospitality operators, and academic institutions each tailor solutions to their unique risk and compliance profiles, underscoring the criticality of verticalized approaches in addressing specialized threat vectors.
This comprehensive research report categorizes the Cloud Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Offerings
- Service Model
- Security Type
- Organization Size
- Deployment Mode
- Industry Vertical
Revealing Critical Regional Dynamics Shaping Cloud Security Adoption and Innovation Trends Across the Americas Europe Middle East Africa and Asia Pacific Markets
Regional dynamics exert a compelling influence on cloud security strategies, as geographic variances in regulatory requirements, threat landscapes, and cloud adoption rates shape vendor offerings and customer priorities. In the Americas, robust investment in next-generation security controls is driven by stringent data privacy standards and high-profile breach disclosures. North American enterprises are pioneering unified security stacks, integrating native cloud controls with third-party threat intelligence feeds, while Latin American organizations balance evolving regulatory maturity with centralized managed services to bolster limited in-house security expertise.
Turning to Europe, the Middle East, and Africa, data sovereignty remains a central concern, driving demand for localized infrastructure and hybrid cloud configurations. Regulatory regimes spanning the General Data Protection Regulation to emerging cybersecurity directives compel providers to demonstrate compliance through transparent reporting and automated audit capabilities. In contrast, Middle East and African markets display a mix of emerging cloud adoption accompanied by a pressing need for awareness campaigns and professional services that address talent gaps and bridge cultural expectations around data protection.
Across Asia-Pacific, rapid digitalization and government-led initiatives have accelerated cloud migration, prompting organizations in China, Japan, India, and Southeast Asia to prioritize vendor partnerships that deliver deep integration with local compliance frameworks. High-growth sectors such as telecommunications and public sector services lean on managed offerings to offset skills shortages, while tech hubs are driving demand for advanced analytics and AI-driven security controls. Across all regions, the imperative to harmonize global security standards with local mandates remains the cornerstone of any successful multiregional deployment strategy.
This comprehensive research report examines key regions that drive the evolution of the Cloud Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting the Strategic Initiatives Competitive Positioning and Collaborative Innovations Driving Leadership Among Premier Cloud Security Vendors Worldwide
Leading cloud security providers are distinguishing themselves through a combination of platform extensibility, strategic alliances, and continuous innovation. Major hyperscale vendors have embedded security capabilities directly into cloud service portfolios, offering customers a unified console for threat monitoring, configuration management, and automated remediation. These vendors have also opened marketplaces for partner-developed security solutions, enabling third-party specialists to extend core offerings with verticalized modules and specialized threat intelligence feeds.
At the same time, established network security and endpoint protection firms have expanded their reach into cloud-native territories by acquiring or internally developing solutions for posture management, identity governance, and container security. Collaborative ventures between cloud providers and traditional cybersecurity leaders have birthed joint go-to-market initiatives and co-engineered integrations, accelerating time-to-value for enterprise customers. New market entrants, leveraging microservices architectures, are focusing on singular domains such as cloud infrastructure entitlement management and cloud detection and response, pressuring incumbents to sharpen their focus on platform convergence and seamless user experience.
Across the competitive landscape, differentiators include the breadth of compliance templates, depth of API integrations, robustness of machine learning engines, and quality of managed service delivery. Organizations are placing a premium on vendors that demonstrate a clear product roadmap aligned to emerging technologies such as confidential computing and secure access service edge, as well as those that maintain transparent communication channels around threat trends and security advisories.
This comprehensive research report delivers an in-depth overview of the principal market players in the Cloud Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Amazon Web Services, Inc.
- AO Kaspersky Lab
- Box, Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- CrowdStrike Inc.
- Forcepoint LLC
- Fortinet, Inc.
- Google LLC by Alphabet Inc.
- International Business Machines Corporation
- McAfee, LLC
- Microsoft Corporation
- Musarubra US LLC
- Netskope, Inc
- Oracle Corporation
- Palo Alto Networks, Inc.
- Qualys, Inc.
- Rapid7, Inc.
- Salesforce, Inc.
- SentinelOne, Inc.
- Sophos Ltd.
- Trellix LLC
- Trend Micro Incorporated
- Varonis Systems, Inc.
- Zscaler, Inc.
Empowering Industry Leaders With Tactical Strategies for Enhancing Cloud Security Postures Strengthening Resilience and Maximizing Operational Agility
Industry leaders should adopt a zero trust framework as a foundational strategy, extending beyond network boundaries to enforce least-privilege access across workloads, identities, and data flows. By integrating identity-aware proxies and continuous adaptive policy evaluation, organizations can reduce their attack surface and respond swiftly to anomalous behaviors. Concurrently, embedding security into the DevOps lifecycle through automated testing, infrastructure as code validation, and continuous integration pipelines ensures that security controls evolve in lockstep with application changes.
Strengthening resilience requires orchestrated incident response capabilities that span endpoint, network, and cloud environments. Security operations teams must harness unified dashboards and playbooks that facilitate cross-domain visibility, enabling faster root-cause analysis and remediation. Budgetary allocations should prioritize scalable managed detection and response services, thereby augmenting in-house expertise and reducing time to detect and respond.
Leaders must also cultivate a culture of continuous learning by investing in training programs that bridge the skill gap between cloud architecture, security engineering, and governance functions. Collaboration with strategic partners and participation in industry threat-sharing consortiums will further enhance situational awareness. Finally, as regulatory landscapes tighten, proactive engagement with policymakers and transparency around compliance postures will position organizations as trusted custodians of customer data and critical infrastructure.
Detailing a Research Methodology Combining Quantitative Analysis Expert Interviews and Triangulation Techniques to Deliver Actionable Cloud Security Insights
The research methodology underpinning this analysis integrates both quantitative and qualitative techniques to ensure a holistic perspective. Primary data was gathered through structured interviews with CISOs, security architects, and cloud service executives, capturing firsthand accounts of deployment challenges, investment priorities, and innovation roadmaps. Concurrently, extensive secondary research surveyed vendor white papers, open-source threat intelligence feeds, regulatory publications, and technology community forums to contextualize broader market dynamics.
Quantitative analysis involved aggregating anonymized usage metrics from leading cloud platforms, comparing adoption patterns across service models and deployment modes. This dataset was normalized and subjected to triangulation techniques, cross-referencing independent sources to validate observed trends. Expert panel workshops were convened to test preliminary findings, challenge assumptions, and refine thematic insights. The rigorous combination of data-driven evidence and expert validation has yielded a robust, actionable framework for understanding the cloud security landscape.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Cloud Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Cloud Security Market, by Offerings
- Cloud Security Market, by Service Model
- Cloud Security Market, by Security Type
- Cloud Security Market, by Organization Size
- Cloud Security Market, by Deployment Mode
- Cloud Security Market, by Industry Vertical
- Cloud Security Market, by Region
- Cloud Security Market, by Group
- Cloud Security Market, by Country
- United States Cloud Security Market
- China Cloud Security Market
- Competitive Landscape
- List of Figures [Total: 18]
- List of Tables [Total: 1431 ]
Synthesizing Critical Discoveries to Illuminate the Future of Cloud Security in an Age Defined by Rapid Technological Progress and Heightened Threat Complexity
The synthesis of technological advancements, regulatory shifts, economic pressures, and competitive dynamics paints a clear picture: cloud security is no longer an adjunct concern but a strategic imperative woven into every facet of modern IT transformation. Organizations that embrace a multidimensional approach-integrating zero trust principles, leveraging managed and professional services, and aligning toolsets with specific service models-will stand resilient in the face of evolving threats.
Moreover, the influence of external factors such as tariff policy adjustments underscores the necessity for agile procurement strategies and adaptive supply chain planning. Regional nuances further emphasize the importance of local compliance alignment and culturally attuned delivery models. By internalizing these insights and acting on the recommendations outlined, industry participants can not only protect critical assets but also seize new market opportunities, driving long-term value and sustained growth.
Take the Next Step to Elevate Your Cloud Security Posture by Engaging With Ketan Rohom Associate Director Sales and Marketing for Market Research Solutions
In an environment where digital resilience dictates competitive advantage, engaging with market leaders has never been more critical. Partnering with Ketan Rohom, Associate Director, Sales and Marketing, provides tailored guidance to navigate complex security demands, tailor solutions to organizational objectives, and unlock rich insights that drive informed decision-making. Reach out to begin a strategic dialogue and secure access to comprehensive market research solutions that empower your organization to stay ahead of evolving threats and capitalize on emerging opportunities.

- How big is the Cloud Security Market?
- What is the Cloud Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




