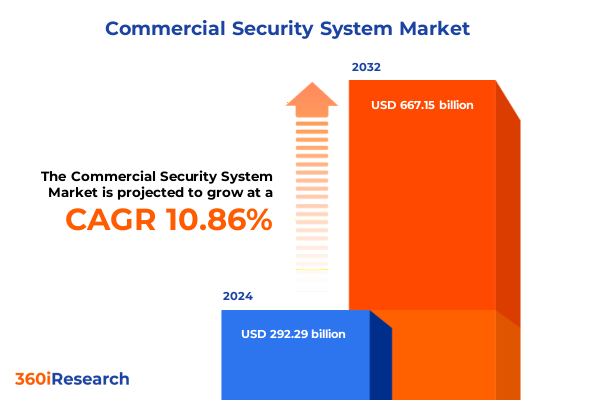
The Commercial Security System Market size was estimated at USD 321.61 billion in 2025 and expected to reach USD 355.00 billion in 2026, at a CAGR of 10.98% to reach USD 667.15 billion by 2032.
Unveiling the Critical Role of Next-Generation Commercial Security Architectures That Fortify Modern Business Ecosystems Against Emerging Threats
Commercial security systems have become indispensable for organizations seeking to safeguard people, assets, and data from an increasingly complex array of threats. The rapid proliferation of digital transformation initiatives has deepened the reliance on connected devices at every level of commercial infrastructure, creating new risk vectors while simultaneously elevating the strategic value of robust security frameworks. As threat actors evolve their tactics, blending physical intrusion with sophisticated cyber exploits, enterprises must adopt agile solutions that integrate hardware, services, and software into cohesive architectures. This executive summary introduces the fundamental dynamics shaping commercial security today, setting the stage for an in-depth exploration of transformative trends, regulatory challenges, and actionable insights.
Drawing upon primary interviews with industry leaders, extensive supply chain analysis, and rigorous secondary research, this report synthesizes key observations across global markets without disclosing proprietary forecast data. Stakeholders are guided through a layered examination of technological advancements, policy shifts, and market segmentation, revealing how evolving deployment models and end-user demands are driving strategic decision making. With an emphasis on evidence-based recommendations, the following sections traverse the latest developments-from artificial intelligence–enabled video analytics to the broader implications of recent tariff policies-equipping decision-makers with the context needed to elevate security postures, optimize investment strategies, and navigate the next chapter of commercial security innovation.
Transitionally, this document highlights the interplay between cost considerations and strategic imperatives, emphasizing the cumulative impact of trade policies, regulatory landscapes, and regional variances. By framing each analysis within the broader context of operational resilience and compliance requirements, the reader gains a holistic perspective on both immediate priorities and longer-term initiatives. The ultimate goal of this introduction is to orient executives toward the critical themes that underpin robust security architectures, providing a compelling narrative that drives the imperative for proactive adaptation in an era defined by rapid technological disruption and geopolitical volatility.
Exploring the Convergence of Artificial Intelligence Connectivity and Cloud Innovations Reshaping Commercial Security Frameworks for Enhanced Resilience
The commercial security landscape is being reshaped by an unprecedented convergence of artificial intelligence, edge-to-cloud connectivity, and advanced analytics. AI-powered video analytics have moved beyond basic object detection to offer real-time behavioral analytics that can differentiate between benign activities and potential threats. In parallel, the proliferation of edge devices equipped with machine learning capabilities has enabled preliminary processing at the source, reducing latency and preserving critical bandwidth. These capabilities are further enhanced by seamless cloud integration, which allows centralized management and orchestration of security data across distributed facilities. Consequently, organizations can achieve heightened situational awareness while optimizing deployment costs and operational efficiency.
Moreover, the rise of Internet of Things connectivity has accelerated the adoption of unified security platforms that bridge traditional silos of access control, intrusion detection, and video surveillance. By leveraging open frameworks and standardized communication protocols, these platforms facilitate cross-functional data sharing and workflow automation. Internal zones now benefit from predictive maintenance alerts, while perimeter security layers leverage geospatial analytics and drone integration for proactive threat detection. The maturity of wireless systems has enabled installers to reduce deployment complexity, yet demands the implementation of robust encryption standards and network segmentation to mitigate cybersecurity vulnerabilities inherent in pervasive connectivity.
In addition, cognitive security architectures are fostering the intertwining of physical and cybersecurity strategies. Organizations are embedding intrusion detection software within central station software suites, enabling a unified view of incidents that span digital and physical domains. This shift transcends traditional service delivery models by offering professional and managed services that integrate continuous threat hunting, incident response, and regulatory compliance workflows. The resulting transformation is a more adaptive, intelligence-driven security posture that empowers stakeholders to anticipate emerging risks and maintain resilience against evolving threat modalities.
Assessing the Ramifications of 2025 United States Tariff Measures on Supply Chains Manufacturing and Cost Structures within Commercial Security Markets
In 2025, a series of tariff measures instituted by the United States government introduced significant complexities for commercial security manufacturers and suppliers. Heightened duties on electronic components and optical sensors have driven an increase in upstream costs, compelling original equipment manufacturers to reassess sourcing strategies and negotiate new supplier agreements. These policy actions, initially aimed at balancing trade deficits and promoting domestic production, have tangibly influenced the pricing of video surveillance cameras, intrusion detection sensors, and biometric access control modules. As a result, end customers are encountering elevated procurement budgets, while vendors are exploring alternative design specifications and material substitutions to manage cost pressures.
Simultaneously, the imposition of tariffs on steel and aluminum has reverberated through the hardware supply chain, affecting the fabrication of housings, mounts, and structural enclosures. Fabricators are facing margin compression and longer lead times as domestic capacity struggles to absorb redirected demand. In response, several manufacturers have initiated nearshoring initiatives, relocating assembly lines closer to end markets to alleviate cross-border logistics challenges. While this transition promises improved responsiveness, it also necessitates capital investments in automated assembly technologies and workforce training programs. These strategic realignments are redefining the competitive dynamics among global players, encouraging collaboration between hardware producers and system integrators.
Additionally, the cumulative impact of tariffs has underscored the importance of software-centric revenue streams and managed service agreements. With hardware cost volatility persisting, many organizations are pivoting toward subscription-based software licenses for central station monitoring and intrusion detection services. This shift not only cushions the effect of one-time capital expenditures but also fosters recurring revenue paradigms that underpin longer-term customer relationships. Consequently, the interplay between trade policy and revenue model innovation is driving strategic portfolio diversification, ensuring that suppliers remain agile in navigating policy headwinds and evolving client expectations.
Decoding the Strategic Implications of Differentiated Hardware Service and Software Offerings Alongside Deployment Model Evolution and End-User Dynamics
A nuanced understanding of market segmentation is essential for stakeholders seeking targeted growth opportunities and resource optimization. Based on offerings, the landscape encompasses hardware, services, and software. Hardware spans multiple domains such as access control systems with biometric and card-based mechanisms, fire protection systems featuring alarms, smoke detection, and sprinkler solutions, intrusion detection systems including glass break and motion sensors, and video surveillance systems offering both CCTV and thermal imaging cameras. Service models bifurcate into managed service engagements and professional service contracts, while software offerings include central station platforms and specialized intrusion detection applications. Each segment presents distinct adoption drivers and technology requirements, guiding product roadmaps and channel strategies.
Simultaneously, infrastructure level analysis categorizes security deployments across entry point security, internal zones, and perimeter defenses. Entry point solutions prioritize high-throughput, low-latency credential verification systems, whereas internal zone implementations emphasize asset monitoring, environmental detection, and workflow integration. Perimeter security continues to evolve with geofencing, analytics-driven video wall management, and unmanned aerial surveillance integration. Layering this lens with communication technology segmentation, wired systems leveraging coaxial, Ethernet, and fiber optics remain foundational, while wireless technologies such as Bluetooth, Wi-Fi, and Zigbee facilitate scalable, agile installations. The trade-off between wired reliability and wireless flexibility is a key design consideration.
Moreover, deployment model segmentation differentiates on-premise architectures from cloud-hosted environments. On-premise solutions are favored in highly regulated industries requiring stringent data sovereignty controls, while on-cloud offerings deliver rapid scalability and centralized oversight for distributed enterprise footprints. End-user segmentation highlights diverse adoption patterns across banking, financial services & insurance, corporate offices, educational institutions, government and public sector facilities, healthcare environments including clinics, diagnostic labs, and hospitals, hospitality venues such as hotels, resorts, and restaurants, retail environments, and transportation and logistics nodes comprising airports, rail and bus terminals, and seaports. Distribution channel strategies reflect market maturation, with traditional offline integrators maintaining deep local relationships while online platforms leverage digital marketing and remote support models to penetrate new segments. The interplay between these channels is shaping competitive pricing and service bundling approaches.
This comprehensive research report categorizes the Commercial Security System market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Offerings
- Infrastructure Level
- Communication Technology
- Deployment Model
- End-User
- Distribution Channel
Comparative Analysis of Commercial Security Adoption Trends Across the Americas Europe Middle East Africa and Asia-Pacific Regions
Regional dynamics reveal distinct trajectories in commercial security adoption influenced by regulatory frameworks, economic development levels, and technology infrastructure. In the Americas, robust investment in infrastructure modernization and cybersecurity compliance drives the integration of AI-enabled analytics with legacy video surveillance. North American organizations often leverage professional services to ensure adherence to data privacy mandates, while Latin American markets show growing appetite for hybrid deployment models that balance cost efficiency with risk mitigation. The diversity of end-user requirements, ranging from corporate campuses to manufacturing facilities, has accelerated interest in subscription-based monitoring and rapid scalability.
In Europe, Middle East, and Africa, regulatory rigor and geopolitical considerations significantly shape security strategies. European enterprises are guided by stringent GDPR compliance, leading to increased deployment of on-premise analytics combined with federated cloud models. In the Middle East, government-led smart city initiatives catalyze large-scale perimeter security projects that integrate drone surveillance and advanced radar systems. African markets, while at an earlier stage of digital transformation, are witnessing rapid uptake of wireless systems in urban centers and critical infrastructure. Cross-border partnerships and public-private collaborations are fundamental to driving standardization and knowledge transfer across EMEA.
Meanwhile, the Asia-Pacific region exhibits a dual pattern of mature markets such as Japan and Australia, where innovation in thermal imaging and mobile access control is prevalent, and emerging economies in Southeast Asia and South Asia, where cost-effective wireless solutions dominate. APAC’s high-density urban environments and complex regulatory mosaics necessitate scalable, interoperable platforms that can seamlessly integrate with existing building management systems. Additionally, local manufacturing incentives and import substitution policies are broadening the availability of regionally sourced hardware, reducing dependency on traditional supply chains and accelerating market responsiveness across this dynamic geography.
Transitioning from regulatory influence to economic incentives, government funding for critical infrastructure modernization is accelerating procurement cycles in both public and private sectors. As organizations face budgetary constraints and security imperatives, the decision between cloud-based and on-premise deployments often hinges on long-term total cost of ownership assessments and data sovereignty considerations.
This comprehensive research report examines key regions that drive the evolution of the Commercial Security System market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Evaluating Competitive Strategic Positioning Technological Innovation and Collaborative Partnerships of Leading Global Players in Commercial Security Solutions
The competitive landscape in commercial security is characterized by a blend of legacy conglomerates and agile newcomers, each leveraging unique strengths to capture market share. Established industrial players have deep vertical integration capabilities, offering end-to-end solutions that span sensor manufacturing, professional installation, and long-term managed services. Their extensive research and development investments are fostering next-generation sensor suites, edge computing devices, and unified management consoles. At the same time, technology-focused vendors excel in rapid feature development, cloud-native architectures, and seamless API ecosystems that enable best-of-breed integrations. This dichotomy underscores the importance of strategic partnerships and ecosystem alliances.
Notably, leading hardware manufacturers are expanding their service portfolios through acquisitions of professional services firms and investments in centralized monitoring facilities. Concurrently, pure-play software developers are forging alliances with telecommunications providers to facilitate secure, high-bandwidth video streaming and remote device management. Collaborative frameworks between manufacturers, software vendors, and channel partners are facilitating innovative deployment models that blend capital expenditure with subscription-based pricing structures. As a result, market incumbents are differentiating on criteria beyond product functionality, including speed of deployment, integration ease, and holistic lifecycle support.
Recent mergers and acquisitions have further consolidated capabilities, enabling companies to offer holistic solutions that blend physical security sensors with advanced analytics services. This trend underscores the strategic importance of scalable platforms that can adapt to rapid technological shifts and changing client expectations without compromising integration depth. Regional champions and specialized integrators are emerging as pivotal players in localized markets by tailoring solutions to specific regulatory contexts and cultural expectations. By designing modular architectures that accommodate phased rollouts, these organizations are meeting the unique demands of sectors such as critical infrastructure, healthcare, and transportation.
This comprehensive research report delivers an in-depth overview of the principal market players in the Commercial Security System market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Abus August Bremicker Sohne KG
- ADT Inc.
- Allegion PLC
- Assa Abloy AB
- Atlas Ontario LP
- Axis Communications AB
- Carrier Global Corporation
- dormakaba International Holding AG
- Genetec Inc.
- Godrej & Boyce Manufacturing Company Limited
- Halma PLC
- Hangzhou Hikvision Digital Technology Co., Ltd.
- Hanwha Group
- Hochiki Corporation
- Honeywell International Inc.
- IDEMIA Identity & Security USA LLC
- IDIS Inc.
- Johnson Controls International PLC
- LG Electronics Inc.
- Lorex Corporation
- Napco Security Technologies, Inc.
- NewVision Security
- Optex Co., Ltd.
- Panasonic Corporation
- Paxton Access Ltd.
- Phillips Pro Systems, LLC
- Robert Bosch GmbH
- SAMSUNG ELECTRONICS CO., LTD.
- Sanyo Denki Group
- Schneider Electric SE
- SDG Security & Fire
- Secom Co., Ltd.
- Securitas AB
- Siemens AG
- SimpliSafe, Inc.
- Sony Group Corporation
- Swann Communications Ltd.
- Tattletale
- Teledyne Technologies Inc.
- Vector Security
- Vivint, Inc.
- VIVOTEK Inc.
- Zhejiang Dahua Technology Co., Ltd.
Formulating Proactive Strategic Directions for Industry Stakeholders to Navigate Disruption Capitalize on Emerging Opportunities and Strengthen Security Postures
Industry leaders must prioritize a cohesive strategy that aligns technological innovation with evolving risk landscapes. Embracing open standards and interoperability frameworks can mitigate vendor lock-in while fostering ecosystems that accelerate solution deployment. By investing in edge-to-cloud infrastructures, organizations can balance real-time analytics with centralized oversight, thereby optimizing both responsiveness and scalability. Simultaneously, embedding advanced encryption protocols and continuous penetration testing into product lifecycles will ensure that wireless and cloud-based architectures remain resilient against sophisticated cyber threats.
To navigate supply chain volatility, stakeholders should diversify sourcing across domestic and nearshore partners, while leveraging predictive procurement analytics to anticipate cost fluctuations. Cultivating collaborative relationships with key component manufacturers and logistics providers can enhance visibility and agility in the face of geopolitical uncertainties. Additionally, transitioning from purely capital expenditure models to hybrid financial structures-combining upfront device investments with managed service subscriptions-can decouple revenue streams from hardware cost variability, ensuring more predictable long-term relationships and cash flow management.
Moreover, companies should cultivate talent strategies that blend traditional security engineering expertise with data science and software development skills. Establishing centers of excellence for artificial intelligence and cybersecurity will accelerate the integration of intelligent automation capabilities across physical security domains. Engaging in joint research initiatives with academic institutions and industry consortia can further spur innovation and standardization. By adopting these actionable recommendations, business leaders can not only fortify their risk posture but also unlock new pathways for revenue diversification and competitive differentiation.
Outlining the Comprehensive Mixed Method Research Approach Leveraging Primary Insights Secondary Data and Triangulation for Market Intelligence Rigor
This research leverages a multi-faceted methodology designed to deliver robust, actionable insights into the commercial security landscape. Secondary research commenced with an exhaustive review of open source documents including regulatory filings, industry white papers, and publicly available financial statements to establish a foundational understanding of technology trends and policy developments. Concurrently, primary research was conducted through in-depth interviews with senior executives, system integrators, and end users across diverse verticals, capturing frontline perspectives on deployment challenges, innovation priorities, and service model preferences.
The qualitative feedback was systematically triangulated with quantitative data collected from supply chain participants, channel distributors, and software analytics dashboards. Data validation protocols were applied to ensure consistency across sources, with discrepancies addressed through follow-up engagements and cross-referencing against known benchmarks. Market segmentation analyses were formulated using a rigorous classification framework that incorporates offering types, communication technologies, infrastructure levels, deployment models, end-user verticals, and distribution channels. Each segment was evaluated against adoption drivers, technology maturity, and competitive intensity.
Furthermore, regional analyses integrated geopolitical risk assessments, regulatory compliance reviews, and infrastructure readiness checks to contextualize global trends within local market conditions. The research process adhered to established market intelligence best practices, ensuring transparency, reproducibility, and adherence to ethical standards. Collectively, this mixed method approach underpins the credibility of the findings and equips decision-makers with evidence-based insights to inform strategic planning and investment decisions.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Commercial Security System market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Commercial Security System Market, by Offerings
- Commercial Security System Market, by Infrastructure Level
- Commercial Security System Market, by Communication Technology
- Commercial Security System Market, by Deployment Model
- Commercial Security System Market, by End-User
- Commercial Security System Market, by Distribution Channel
- Commercial Security System Market, by Region
- Commercial Security System Market, by Group
- Commercial Security System Market, by Country
- United States Commercial Security System Market
- China Commercial Security System Market
- Competitive Landscape
- List of Figures [Total: 18]
- List of Tables [Total: 3021 ]
Summarizing the Pivotal Insights Driving Commercial Security Evolution and Reinforcing Strategic Imperatives for Business Leadership and Decision Making
The commercial security sector is undergoing a significant evolution driven by convergent technologies, shifting policy landscapes, and dynamic end-user requirements. Key themes that have emerged include the critical importance of artificial intelligence–enabled analytics, the strategic value of cloud and edge integrations, and the growing imperative to mitigate supply chain risks exacerbated by recent tariff measures. Regional variations underscore the need for tailored approaches, with divergent regulatory frameworks and infrastructure capabilities shaping deployment strategies across the Americas, EMEA, and Asia-Pacific regions.
Moreover, segmentation insights reveal that hardware, software, and service portfolios must be intricately aligned to meet the nuanced demands of diverse verticals, from financial services to transportation and logistics. The competitive landscape continues to be redefined by agile innovators and legacy incumbents alike, emphasizing the necessity for ecosystem partnerships and flexible business models. Industry stakeholders are advised to adopt an integrative strategy that harnesses open standards, diversifies sourcing, and balances capex with opex commitments, ensuring both fiscal resilience and strategic agility.
This synthesis reaffirms the critical imperatives for security and risk management leaders: prioritize interoperability, invest in talent and innovation, and leverage data-driven insights to anticipate emergent threats. By embracing these strategic levers, organizations will be better positioned to safeguard assets, optimize operational performance, and capitalize on new growth vectors in the rapidly transforming commercial security arena.
Engage Directly with Our Associate Director of Sales Marketing to Unlock and Purchase Your Comprehensive Commercial Security Market Research Report Today
To explore in-depth analyses, proprietary data, and executive-level recommendations that will shape your strategic roadmap, contact Ketan Rohom, Associate Director, Sales & Marketing. Secure your organization’s competitive advantage by accessing our comprehensive research and actionable insights tailored to the evolving commercial security landscape. Don’t miss this opportunity to empower your decision-makers with the intelligence needed to drive innovation, fortify defenses, and achieve operational excellence.

- How big is the Commercial Security System Market?
- What is the Commercial Security System Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




