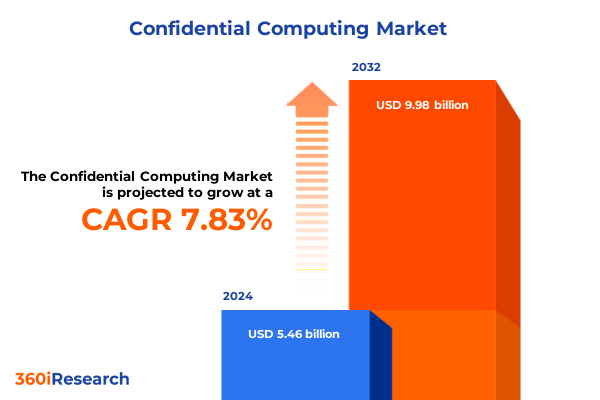
The Confidential Computing Market size was estimated at USD 5.59 billion in 2025 and expected to reach USD 6.48 billion in 2026, at a CAGR of 16.29% to reach USD 16.09 billion by 2032.
Introduction to the Rising Importance of Confidential Computing Shaping the Future of Data Assurance and Next-Generation Security Architectures
The proliferation of sensitive data across cloud, edge, and on-premises environments has elevated the strategic imperative of protecting information not only at rest and in transit, but critically, in use. Confidential computing represents the next frontier of data assurance, leveraging hardware-based isolation to create trusted execution environments that shield workloads from unauthorized access even when they are actively processed. As organizations grapple with expanding digital footprints, the capacity to compute on encrypted data without exposing it in plaintext has emerged as a foundational capability for securing AI-driven analytics, multi-party collaborations, and regulated data operations.
This introduction frames confidential computing as a cornerstone of modern security architectures. It underscores how the convergence of advanced encryption methodologies and silicon-level innovations is redefining trust boundaries within cloud and edge infrastructures. By establishing a hardware-protected enclave around code and data, confidential computing addresses the inherent vulnerabilities of traditional virtualization models. Consequently, enterprises can architect solutions that preserve data sovereignty, meet stringent compliance mandates, and build resilient pipelines for emerging workloads such as generative AI and federated learning.
Unveiling the Transformative Shifts Reshaping Confidential Computing Driven by AI, Cloud Evolution, Edge Proliferation, and Regulatory Imperatives
Confidential computing is undergoing transformative shifts catalyzed by the rapid adoption of AI workloads, the maturation of cloud-native services, and the explosive growth of edge deployments. AI-driven organizations now demand privacy-preserving environments where models can train and infer on proprietary data without risking leakage or exposure. In response, leading cloud providers have embedded trusted execution environments directly into their virtual machine offerings, enabling seamless migration of sensitive workloads into fortified enclaves without significant refactoring.
Simultaneously, the edge computing landscape is integrating confidential computing to secure latency-sensitive applications and distributed analytics. From telecommunications base stations to manufacturing control systems, hardware-based enclaves are being embedded into edge nodes to ensure that real-time data streams remain protected against both insider threats and supply chain attacks. Regulatory momentum is also reshaping the industry, with governments introducing frameworks that explicitly reference confidentiality in compute as a compliance requirement. As this shift gains traction, organizations are moving beyond experimental pilots to full-scale deployments, fundamentally altering how security teams architect and enforce data protection policies across hybrid environments.
Assessing the Cumulative Impact of United States Tariffs in 2025 on Confidential Computing Hardware Supply Chains and Global Security Ecosystems
In 2025, newly enacted United States tariffs on semiconductor components have introduced a complex layer of economic influence over the confidential computing ecosystem. Hardware security modules, extensions for trusted execution environments, and virtualization security modules are all subject to increased import duties, elevating the cost base for third-party manufacturers and cloud operators alike. This cost pressure has prompted organizations to reevaluate procurement strategies, with many seeking to balance the need for advanced enclave capabilities against evolving budgetary constraints.
Moreover, the tariffs have catalyzed a strategic pivot toward domestic production and innovation. Under the CHIPS and Science Act, incentives have been realigned to accelerate onshore fabrication of CPUs and dedicated security co-processors. As a result, leading semiconductor vendors are ramping up localized manufacturing capacity and prioritizing the integration of confidential computing features into next-generation silicon. While the short-term effect has included supply chain realignments and vendor diversification, the long-term consequence may be a more resilient, sovereign supply chain that underpins secure compute for both public and private sectors.
Revealing Key Market Segmentation Insights Highlighting the Diverse Offerings, Technologies, Applications, Industries, Deployment Models, and Organization Sizes
Dissecting the landscape of confidential computing reveals nuanced insights across multiple dimensions of market segmentation. When evaluated through the lens of offering, hardware extensions and security modules remain the foundational building blocks, whereas managed services and professional services are gaining momentum as organizations seek expert guidance for deployment and ongoing operations. Within solutions, components such as secure elements, trusted execution environments, and virtualization security modules are converging to form integrated stacks that streamline policy enforcement and workload portability.
By technology, homomorphic encryption is advancing toward practical implementations in niche analytics use cases, and multi-party computation is emerging as a vital enabler for cross-organization collaboration without data leakage. Secure enclaves and trusted execution environments continue to serve as the workhorses of real-time protection, with new silicon releases enhancing isolation guarantees and performance. Across applications, protecting AI workloads, ensuring cloud data confidentiality, governing identity and access management, and securing transaction flows are the primary focus areas where confidential computing provides tangible risk reduction.
End user industries exhibit divergent maturity curves. Banking, financial services, and insurance sectors were among the earliest adopters, driven by stringent regulatory mandates and the high value of financial data. Governments have followed closely, deploying enclaves for citizen data services and secure digital identities. Healthcare providers are exploring secure enclaves to process patient records and genomic data. In IT and telecommunication, confidential computing is being embedded into next-generation network functions and virtualized infrastructure. Manufacturing and retail enterprises are piloting edge deployments to protect industrial IoT streams and customer payment transactions.
Deployments often hinge on model preferences. Cloud-based implementations offer scalability and integration with managed platforms, attracting organizations with limited in-house security expertise. Conversely, on-premises deployments appeal to entities with strict data residency requirements or specialized performance needs. Organization size also influences adoption strategies: large enterprises typically pursue a multi-pronged approach combining on-premises enclaves with hybrid cloud, while SMEs gravitate toward cloud-based managed services to minimize upfront capital outlay and operational overhead.
This comprehensive research report categorizes the Confidential Computing market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Offering
- Technology
- Application
- End User Industry
- Deployment Model
- Organization Size
Mapping Regional Dynamics with Key Insights into the Americas, Europe Middle East Africa, and Asia-Pacific Confidential Computing Landscapes Evidencing Unique Drivers
Regional dynamics are defining the trajectory of confidential computing in distinct ways across the globe. In the Americas, rapid cloud adoption, mature hyperscale infrastructure, and a robust startup ecosystem have accelerated integration of enclave technologies. Financial institutions in North America are standardizing confidential compute into their risk management playbooks, while technology providers in Silicon Valley and Canada are pioneering new developer frameworks.
Europe, the Middle East, and Africa present a tapestry of regulatory drivers and data sovereignty initiatives. The General Data Protection Regulation has informed national guidelines that incorporate protections for data in use, prompting public and private sector organizations to explore enclave architectures. Across the Middle East, government-led digital transformation programs are embedding confidential computing into smart city deployments. In Africa, partnerships between telecommunication operators and cloud vendors are enabling secure data processing in emerging markets.
The Asia-Pacific region is characterized by aggressive government support, domestic chipset ventures, and rapid scale of digital services. China’s emphasis on self-reliance has spurred investments in homegrown enclave-capable processors, while India’s digital identity and payments ecosystems are integrating confidential frameworks to safeguard citizen data. Japan and Australia are focusing on low-latency, edge-based enclaves for industrial automation, reflecting a broader emphasis on operational resilience. As each region navigates unique regulatory, economic, and technological factors, vendors and end users alike are crafting differentiated strategies that align with regional priorities and capabilities.
This comprehensive research report examines key regions that drive the evolution of the Confidential Computing market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Examining Influential Players in Confidential Computing and Their Strategic Approaches to Partnerships, Product Innovation, and Market Leadership Trajectories
Leading technology vendors are solidifying their positions through a combination of product innovation, strategic partnerships, and ecosystem development. In the processor domain, Intel’s Software Guard Extensions and forthcoming Trust Domain Extensions continue to set performance and security benchmarks for confidential workloads. AMD’s Secure Encrypted Virtualization has gained traction in cloud environments, while cloud-native solutions such as AWS Nitro Enclaves and Azure Confidential VMs provide integrated managed experience for customers.
Beyond hyperscale offerings, specialist firms are enhancing platform capabilities. IBM’s Cloud Hyper Protect service leverages custom co-processors to deliver robust enclaves for mission-critical workloads. Open-source initiatives like Open Enclave SDK and Microsoft’s Confidential Consortium Framework are enabling interoperability and cross-platform development. Startups are also shaping the space; emerging players are focusing on homomorphic encryption libraries, multi-party computation orchestrators, and turnkey enclave management platforms. Partnerships between chipmakers, cloud providers, and security software vendors are becoming the norm, reflecting a collective drive to reduce integration friction and accelerate time to value.
Innovation pipelines further extend into adjacent ecosystems, with hardware acceleration firms collaborating with AI and analytics vendors to integrate enclave compatibility into popular frameworks. Telecommunication operators are forging alliances with cloud and semiconductor partners to embed confidential computing directly into network infrastructure. This broad array of strategic initiatives underscores a convergence of capabilities and an industry-wide commitment to operationalizing data protection at the hardware level.
This comprehensive research report delivers an in-depth overview of the principal market players in the Confidential Computing market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Intel Corporation
- International Business Machines Corporation
- Advanced Micro Devices, Inc.
- Amazon Web Services, Inc.
- Microsoft Corporation
- Oracle Corporation
- Google LLC by Alphabet Inc.
- Cisco Systems, Inc.
- Vmware, Inc. by Broadcom Inc.
- Anjuna Security, Inc.
- Arm Limited by SoftBank Group Corp.
- Capgemini SE
- Cysec SA
- Duality Technologies Inc.
- Edgeless Systems GmbH
- Fortanix Inc.
- HUB Security Ltd.
- OPAQUE Systems Inc.
- OVH SAS
- phoenixNAP LLC
- Profian
- Secretarium Ltd.
- Swisscom AG
- Telefónica, S.A.
- Thales Group
- Wipro Limited
Actionable Recommendations for Industry Leaders to Accelerate Confidential Computing Adoption Through Strategic Collaboration, Governance, and Technology Integration
Industry leaders seeking to harness the power of confidential computing must begin by aligning business objectives with technical use cases, selecting pilot projects that balance risk reduction with demonstrable return on investment. Organizations should develop a clear governance framework that delineates roles, responsibilities, and policies for managing hardware enclaves, ensuring consistency across cloud and edge environments. Cross-functional collaboration between security, IT, and application development teams is critical for embedding enclave integration into DevOps pipelines and release processes.
It is equally important to cultivate strategic partnerships. Engaging with hyperscale cloud providers and silicon vendors can unlock tailored service offerings and early access to hardware roadmaps. Collaborations with specialist security consultancies and academic institutions can provide the methodological rigor required for complex deployments involving multi-party computation or homomorphic encryption. Leaders must also invest in training programs to build internal expertise, equipping security operations centers with the skills to monitor and remediate enclave-related vulnerabilities.
Adopting a phased approach allows organizations to optimize resource allocation and measure success at each milestone. By piloting confidential computing within non-production environments, teams can refine deployment templates and governance practices before scaling. Finally, participating in industry consortia and contributing to open standards helps shape the evolution of interoperability frameworks, ensuring that future vendor releases align with organizational requirements and regulatory expectations.
Explaining the Rigorous Research Methodology Underpinning the Confidential Computing Analysis Including Data Collection, Validation, and Analytical Frameworks
The foundation of this analysis is a rigorous research methodology that blends both secondary and primary research approaches. Secondary research included comprehensive reviews of academic journals, white papers, vendor documentation, and publicly available regulatory guidelines to establish a baseline understanding of confidential computing technologies and adoption patterns. This phase also incorporated an examination of patent filings and standards body publications to identify nascent innovations and emerging compliance frameworks.
Primary research was conducted through in-depth interviews with technology executives, security architects, and compliance officers across banking, government, healthcare, telecommunications, manufacturing, and retail sectors. These conversations yielded qualitative insights into real-world deployment challenges, best practices, and success criteria. To complement interviews, structured surveys captured quantitative data on project timelines, technology preferences, and governance maturity across organizations of varying sizes.
Data triangulation was applied to reconcile divergent viewpoints and ensure consistency across multiple sources. Insights were further validated through advisory workshops with subject matter experts, providing a forum for peer review and critique. The methodology also incorporated a rigorous quality assurance process, including fact-checking, editorial review, and compliance with confidentiality protocols for all interview participants. This multi-layered approach underpins the robustness and credibility of the findings presented in this report.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Confidential Computing market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Confidential Computing Market, by Offering
- Confidential Computing Market, by Technology
- Confidential Computing Market, by Application
- Confidential Computing Market, by End User Industry
- Confidential Computing Market, by Deployment Model
- Confidential Computing Market, by Organization Size
- Confidential Computing Market, by Region
- Confidential Computing Market, by Group
- Confidential Computing Market, by Country
- United States Confidential Computing Market
- China Confidential Computing Market
- Competitive Landscape
- List of Figures [Total: 18]
- List of Tables [Total: 1749 ]
Concluding Reflections on the Strategic Imperatives and Future Outlook of Confidential Computing as an Integral Component of Enterprise Cybersecurity Posture
Confidential computing has transitioned from academic concept to operational imperative, redefining how organizations safeguard data during processing. The confluence of AI-driven demands, edge proliferation, and regulatory enhancements has accelerated adoption, while evolving geopolitical dynamics have underscored the strategic importance of resilient supply chains. As enterprises navigate the complexity of hardware enclaves, encryption schemes, and governance structures, they are positioning confidential computing as a key pillar of their cybersecurity posture.
Looking ahead, the industry is poised for continued innovation. Quantum-safe enclave designs, cross-vendor orchestration frameworks, and standardized attestation protocols will further streamline deployment and interoperability. Policy evolution, including new data protection regulations and international trade agreements, will shape investment priorities and vendor roadmaps. Ultimately, organizations that proactively integrate confidential computing into their security architectures will gain a competitive edge by enabling transformative use cases-from secure multi-party consortium analytics to privacy-preserving AI services-while maintaining trust and compliance in an increasingly complex digital ecosystem.
Engaging Call-To-Action to Connect with Ketan Rohom for Exclusive Access to the Confidential Computing Market Research Report and Customized Insights
To unlock unparalleled insights into the rapidly evolving confidential computing landscape, reach out to Ketan Rohom, Associate Director of Sales & Marketing, for immediate access to the comprehensive market research report. Ketan brings deep expertise in bridging advanced security innovations with practical business strategies, ensuring you receive tailored intelligence to drive informed decision-making. Engage directly with Ketan to explore bespoke research deliverables, customized data briefs, and priority briefing sessions that align with your organization’s unique confidentiality and compliance objectives. Connect today to secure your executive overview, detailed analytical chapters, and expert recommendations that will empower your organization to lead in the era of data protection in use. Your next competitive advantage awaits-partner with Ketan to bring this critical strategic resource into your organization.

- How big is the Confidential Computing Market?
- What is the Confidential Computing Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




