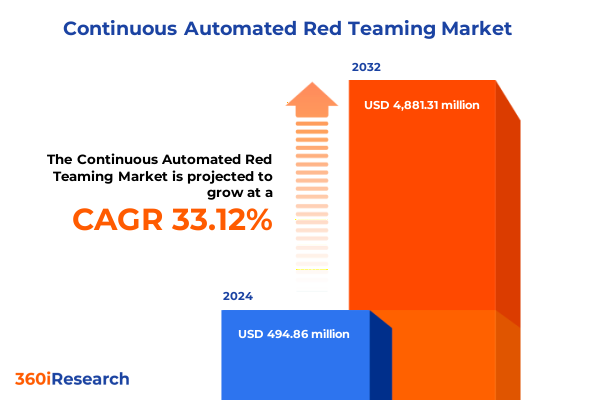
The Continuous Automated Red Teaming Market size was estimated at USD 646.63 million in 2025 and expected to reach USD 850.58 million in 2026, at a CAGR of 33.47% to reach USD 4,881.31 million by 2032.
Discovering How Continuous Automated Red Teaming Transforms Cybersecurity Postures to Prevent Emerging Threats and Ensure Real-Time Resilience Across Enterprises
As cyber threats escalate in complexity and frequency, organizations are confronted with an imperative to shift from episodic vulnerability assessments toward perpetual security validation. Nation-state actors and sophisticated criminal syndicates relentlessly probe digital infrastructures, exploiting gaps in traditional defensive measures. Recent analyses warn that state-sponsored campaigns targeting critical infrastructure have intensified amid geopolitical tensions, underscoring the insufficiency of point-in-time penetration tests against an adaptive adversary landscape.
Continuous automated red teaming emerges as a strategic paradigm that embeds adversary emulation into daily operations. By harnessing machine learning-driven simulations and AI-based reconnaissance, security teams can execute realistic attack scenarios at machine speed, uncovering latent vulnerabilities across networks, endpoints, cloud environments, and applications. This ongoing cycle of attack simulation and control validation transforms abstract risk assessments into actionable, data-driven insights that drive prioritization and remediation at scale.
In an era defined by DevSecOps and agile development methodologies, embedding continuous automated red teaming into CI/CD pipelines ensures that every software update, configuration change, and infrastructure deployment undergoes adversarial scrutiny before reaching production. This shift accelerates time-to-remediation, reduces dwell time, and fosters a proactive security culture where defensive controls evolve alongside the threat landscape. As enterprises grapple with increasing compliance demands and stakeholder expectations, continuous automated red teaming offers a robust framework to demonstrate demonstrable, ongoing resilience against emerging cyber threats.
Unveiling the Most Influential Technological and Operational Shifts Redefining Continuous Automated Red Teaming Practices in 2025
The landscape of continuous automated red teaming is undergoing transformative shifts fueled by advancements in artificial intelligence, automation frameworks, and collaborative defense architectures. Cutting-edge research has introduced multi-agent red teaming frameworks that dynamically integrate emerging attack vectors, enabling automated systems to discover novel tactics, techniques, and procedures in real time. For example, AutoRedTeamer leverages a dual-agent architecture with memory-guided attack selection to achieve significantly higher success rates against large language model targets while reducing computational overhead by nearly half.
Integration with the MITRE ATT&CK framework has become a cornerstone of advanced red teaming strategies. Organizations increasingly embed ATT&CK-based adversary emulation into automated platforms, using tools such as CALDERA and Atomic Red Team to replicate realistic threat behaviors and validate detection and response processes at scale. This alignment not only standardizes attack modeling but also enhances communication between red, blue, and DevSecOps teams through a common taxonomy of adversary tactics and mitigations.
Security orchestration and automation platforms now seamlessly ingest ATT&CK-mapped findings from continuous red teaming exercises, triggering tailored playbooks that orchestrate investigation workflows and remediation actions without manual intervention. This consolidation of threat emulation, detection engineering, and response orchestration marks a departure from siloed operations toward unified, intelligence-driven defense ecosystems.
Simultaneously, the shift toward cloud-native and software-defined architectures has spurred the development of lightweight, containerized emulation engines that reduce dependency on specialized hardware. By decoupling red teaming capabilities from proprietary appliances, vendors and enterprises harness scalable virtualized environments to execute high-fidelity attack simulations across hybrid infrastructures, accelerating adoption and lowering barriers to entry.
Analyzing How Recent United States Tariff Policies Have Reshaped the Cost Structures and Deployment Strategies of Cybersecurity Operations
Over the past year, unpredictable tariff policies have reverberated throughout cybersecurity supply chains, prompting organizations to recalibrate deployment strategies and total cost of ownership analyses. At high-profile industry conferences, defense and technology executives expressed anxiety over tariff-induced economic volatility, warning that escalating import duties risk undermining modernized security postures and injecting uncertainty into procurement roadmaps.
Hardware-dependent cybersecurity appliances have felt the immediate impact, with network security and threat detection appliances experiencing component cost increases of up to 18 percent. In response, many enterprises have deferred hardware refresh cycles, extending lifecycles by an average of 1.5 to 2 years while seeking lifecycle extension services to maximize existing investments.
Contrary to initial concerns, tariff pressures have also accelerated the shift toward cloud-based and SaaS-delivered security services. While on-premises systems faced steep cost hikes, hyperscale cloud providers have largely insulated customers from immediate price changes, positioning cloud-native red teaming platforms as a cost-effective alternative. Industry experts anticipate that rising infrastructure costs will eventually trickle through to subscription fees, but early adopters of cloud-focused solutions currently benefit from vendor-absorbed margin adjustments and extended pause periods on component levies.
Leading cybersecurity vendors are responding by innovating their product roadmaps to emphasize software-defined emulation tools that de-emphasize specialized hardware dependencies. This strategic pivot underscores a broader trend toward agile, portable architectures capable of delivering continuous automated red teaming capabilities across on-premise, cloud, and edge environments without the same tariff exposure.
Illuminating Critical Market Segmentation Drivers That Shape Continuous Automated Red Teaming Adoption Across Technologies, Components, and End Users
Market segmentation reveals critical nuances that guide continuous automated red teaming adoption patterns across enterprise landscapes. When examining component categories, organizations evaluate integrated platform and software offerings alongside professional and managed services-each presenting distinct value propositions. While platforms and software deliver turnkey emulation engines and analytics dashboards, professional services provide custom scenario development and expert-driven campaign orchestration, and managed services offer turnkey operations with end-to-end accountability for continuous testing cycles.
From a technology perspective, the convergence of AI and machine learning with structured frameworks such as MITRE ATT&CK forms the backbone of most advanced red teaming solutions. AI-driven tools leverage dynamic attack generation and real-time adaptation, whereas ATT&CK framework integration ensures that every scenario aligns with up-to-date adversary tactics, enabling organizations to measure their defenses against standardized benchmarks and emerging threat intelligence inputs.
Deployment models further diversify market opportunities, as enterprises weigh the flexibility of cloud-based implementations against the control afforded by on-premise architectures. Cloud deployments excel in scalability and rapid provisioning, while on-premise solutions appeal to highly regulated industries with stringent data residency and sovereignty requirements. Alongside deployment considerations, organizations tailor their investments based on size, with large enterprises commanding broad-scale platform rollouts and small to medium enterprises favoring modular service offerings that deliver immediate, high-impact insights without extensive infrastructure commitments.
Continuous automated red teaming extends across a spectrum of end-user use cases and verticals. Attack path discovery and security control validation anchor baseline testing scenarios, while more specialized capabilities-such as insider threat simulation, phishing and social engineering emulation, and zero trust architecture validation-address sector-specific risk profiles. Vertically, financial services, healthcare, retail, manufacturing, and government sectors lead consumption, driven by compliance mandates and the imperative to safeguard critical customer and operational data.
This comprehensive research report categorizes the Continuous Automated Red Teaming market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Technology
- Deployment Type
- Organization Size
- End
- Vertical
Mapping the Distinct Regional Dynamics and Growth Catalysts Driving Adoption of Continuous Automated Red Teaming Across Global Markets
In the Americas, robust digital transformation initiatives and rigorous regulatory regimes underpin high-velocity adoption of continuous automated red teaming. North American financial institutions and technology enterprises lead demand, embedding adversarial testing into DevSecOps pipelines to maintain compliance with evolving data protection directives. Public sector agencies, responding to disclosures of state-sponsored cyber campaigns, are also increasing investments in perpetual validation programs. Meanwhile, Latin American firms are beginning to follow suit, buoyed by partnerships with global managed service providers that facilitate turnkey red teaming operations.
Europe, Middle East & Africa present a mosaic of cybersecurity maturity levels influenced by landmark regulations such as the EU’s NIS2 Directive and the Digital Operational Resilience Act. Western European organizations prioritize demonstrable, continuous security validation to meet stringent compliance requirements, while the Middle East accelerates adoption amid national cybersecurity strategies tied to critical infrastructure modernization. African markets are at an earlier stage of adoption but are experiencing steady growth fueled by public-private collaborations aimed at reinforcing national cyber resilience and supporting digital economy imperatives.
Asia-Pacific leads global expansion trajectories, driven by rapid digitalization across banking, manufacturing, and telecommunications sectors. Countries with advanced regulatory frameworks-such as Singapore’s Cybersecurity Act-provide robust local points of presence for continuous testing platforms, enabling organizations to meet regional compliance mandates and reduce data latency. In parallel, emerging markets within APAC leverage cloud-first strategies to secure industrial control systems, supply chains, and smart city deployments. This convergence of regulatory encouragement and technological innovation reinforces APAC’s position as the fastest-growing region for continuous automated red teaming deployments.
This comprehensive research report examines key regions that drive the evolution of the Continuous Automated Red Teaming market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Leading Innovators and Strategic Collaborators Fueling Growth and Differentiation in the Continuous Automated Red Teaming Landscape
Leading vendors in the continuous automated red teaming landscape distinguish themselves through differentiated platform capabilities, strategic partnerships, and deep alignment with standardized frameworks. Commercial frontrunners such as Cymulate, SafeBreach, and AttackIQ have set de facto standards for automated adversary emulation, enabling security teams to map defenses to the MITRE ATT&CK framework and derive prioritized risk insights. AttackIQ’s commitment to extensible threat libraries and high-fidelity orchestration integrates seamlessly with SIEM and SOAR systems, elevating control validation to an automated discipline.
Randori’s autonomous reconnaissance showcases another innovation frontier, delivering continuously updated attack paths that expose hidden blind spots in large-scale deployments. Horizon3.ai’s NodeZero platform specializes in autonomous penetration testing with built-in zero trust architecture validations, appealing to organizations embarking on complex digital transformation journeys. Meanwhile, emerging players such as Expel and Bishop Fox extend their managed MDR offerings to encompass continuous red teaming as a service, blending human expertise with AI-driven tooling to deliver turnkey operational models.
Established technology champions and cloud hyperscalers have also entered the fray through partnerships and advisory collaborations. CrowdStrike’s collaboration with the MITRE Engenuity Center for Threat-Informed Defense underscores the importance of threat intelligence–driven emulation, while professional services firms such as Deloitte, EY, and Accenture leverage strategic alliances with automation platforms to embed continuous red teaming into large-scale digital resilience programs. The evolving competitive landscape rewards innovators who can blend advanced automation frameworks with expert-led services to accelerate adoption and drive measurable security outcomes.
This comprehensive research report delivers an in-depth overview of the principal market players in the Continuous Automated Red Teaming market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- AttackIQ, Inc.
- Bishop Fox, Inc.
- Bugcrowd, Inc
- Conviso Security, Inc.
- CrowdStrike Holdings, Inc
- Cymulate Ltd.
- Ethiack, Inc.
- FireCompass Technologies Private Limited
- Fortinet, Inc.
- Fourcore Labs Private Limited
- Google Inc
- HackerOne, Inc.
- Offensive Security LLC
- Palo Alto Networks
- Patrowl SAS
- Pentera Ltd.
- Picus Security Ltd.
- Praetorian Security, Inc
- Randori Inc.
- Rapid7, Inc.
- SafeBreach Ltd.
- Scythe Labs, Inc.
- Shadowmap Technologies GmbH
- Trustwave Holdings, Inc
- XM Cyber Ltd.
Actionable Strategies and Best Practices for Industry Leaders to Leverage Continuous Automated Red Teaming for Enhanced Security Posture
To fully leverage continuous automated red teaming, industry leaders should integrate adversary emulation into development and operations workflows, ensuring that every release and configuration update undergoes rigorous, automated validation. Embedding continuous testing within CI/CD pipelines not only accelerates remediation but also institutionalizes security as a core DevSecOps principle.
Organizations must align red teaming outputs with standardized frameworks such as MITRE ATT&CK and D3FEND, enabling cross-functional teams to translate emulation findings into prioritized, context-rich action plans. By operationalizing ATT&CK-mapped playbooks in SOAR platforms, security leaders can orchestrate automated response actions that close validation loops and reduce manual overhead.
A hybrid deployment strategy-combining cloud-native emulation tools with on-premise controls-mitigates tariff-driven cost pressures and optimizes latency for sensitive workloads. Partnering with managed security service providers and leveraging professional services ensures access to specialized expertise and custom scenario development, accelerating time-to-value and overcoming internal resource constraints.
Finally, cultivating a security culture through continuous training and knowledge sharing ensures that insights derived from automated red teaming drive lasting improvements. Cross-functional collaboration between security, development, and executive teams fosters accountability, transforms adversarial testing into a strategic advantage, and strengthens organizational resilience against evolving cyber threats.
Comprehensive Research Methodology Combining Quantitative Analysis, Expert Interviews, and Rigorous Data Validation Protocols
This research synthesizes insights from primary interviews with cybersecurity leaders, security operations center directors, and DevSecOps practitioners, complemented by secondary data from reputable news outlets, industry blogs, and academic publications. A rigorous data triangulation process validated qualitative inputs against observable market signals, ensuring the robustness of the analysis.
Quantitative surveys of end users across geographies provided empirical evidence on adoption patterns, technology preferences, and deployment models. These findings were further enriched by expert panel workshops that evaluated emerging technologies, vendor roadmaps, and regulatory influences.
The report’s analytical framework centers on a five-step validation protocol: taxonomy definition, data collection, marketplace verification, scenario testing, and peer review. Taxonomies were anchored in overarching segmentation dimensions-component, technology, deployment, organization size, end use case, and vertical-to ensure comprehensive market coverage.
Quality assurance mechanisms included continuous calibration of key assumptions, iterative feedback loops with subject-matter experts, and alignment with publicly available intelligence from trusted news sources and industry standards organizations. This methodology underpins the report’s objective to deliver fact-based, actionable insights that equip decision-makers to navigate the complex continuous automated red teaming market.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Continuous Automated Red Teaming market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Continuous Automated Red Teaming Market, by Component
- Continuous Automated Red Teaming Market, by Technology
- Continuous Automated Red Teaming Market, by Deployment Type
- Continuous Automated Red Teaming Market, by Organization Size
- Continuous Automated Red Teaming Market, by End
- Continuous Automated Red Teaming Market, by Vertical
- Continuous Automated Red Teaming Market, by Region
- Continuous Automated Red Teaming Market, by Group
- Continuous Automated Red Teaming Market, by Country
- United States Continuous Automated Red Teaming Market
- China Continuous Automated Red Teaming Market
- Competitive Landscape
- List of Figures [Total: 18]
- List of Tables [Total: 1272 ]
Concluding Perspectives on the Evolutionary Trajectory of Continuous Automated Red Teaming and Its Ongoing Implications for Enterprise Security
Continuous automated red teaming represents a pivotal evolution in cybersecurity strategy, transitioning from periodic assessments to perpetual adversarial validation. By harnessing AI-driven emulation, integrated frameworks, and cloud-native architectures, organizations gain real-time visibility into their security posture, enabling proactive risk management and accelerated remediation.
As tariff dynamics and regulatory mandates reshape procurement and compliance landscapes, the adoption of flexible deployment models and software-defined emulation frameworks becomes increasingly critical. Regional variations in maturity and regulatory requirements underscore the importance of tailored strategies that align continuous automated red teaming initiatives with local imperatives and sector-specific risk profiles.
Leading vendors and emerging innovators alike drive a competitive market that rewards integration, automation, and expert services. Organizations that embrace a hybrid approach-blending cloud and on-premise capabilities, embedding red teaming into DevSecOps workflows, and operationalizing ATT&CK-aligned playbooks-will achieve sustained resilience against evolving threat actors.
In the face of an accelerating threat environment, the insights distilled in this report offer a clear roadmap for security leaders to harness continuous automated red teaming as a strategic enabler of robust, adaptive, and cost-efficient defense postures.
Empower Your Organization with In-Depth Insights—Connect with Ketan Rohom to Acquire Your Continuous Automated Red Teaming Market Research Report Today
To secure comprehensive insights into the continuously evolving continuous automated red teaming landscape, connect with Ketan Rohom, Associate Director of Sales & Marketing, to gain immediate access to the full market research report. Ketan’s expertise in cybersecurity market dynamics ensures you will receive tailored guidance on how to leverage the report’s findings to drive strategic decisions, optimize security investments, and stay ahead of adversaries.
By partnering with Ketan, you can explore customized briefing sessions, detailed data extracts, and exclusive advisory calls designed to address your organization’s unique challenges. Whether you need deeper analysis of emerging technological integrations or nuanced understanding of regional deployment patterns, Ketan will facilitate seamless access to the intelligence you require to strengthen your continuous automated red teaming initiatives.
Don’t miss the opportunity to transform your security posture with actionable market intelligence. Reach out to Ketan Rohom today to acquire your copy of the comprehensive market research report and embark on a path toward resilient, future-ready defense strategies that keep pace with the most sophisticated adversaries.

- How big is the Continuous Automated Red Teaming Market?
- What is the Continuous Automated Red Teaming Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




