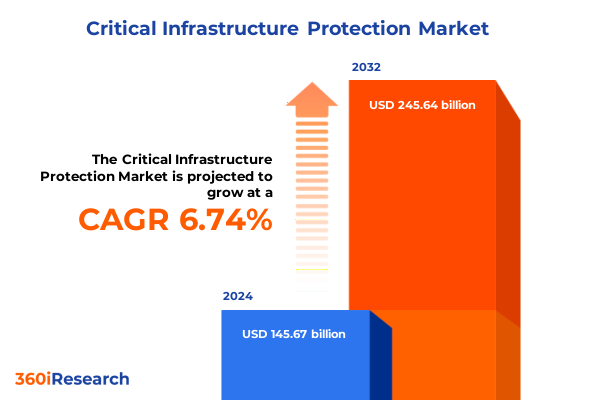
The Critical Infrastructure Protection Market size was estimated at USD 154.67 billion in 2025 and expected to reach USD 164.23 billion in 2026, at a CAGR of 6.83% to reach USD 245.64 billion by 2032.
Navigating the Complex Terrain of Critical Infrastructure Protection in an Era of Rapid Digital Transformation and Escalating Cyber-Physical Threats
As the global landscape of critical infrastructure continues to evolve, organizations are confronted with a complex interplay of physical and cyber threats that demand an integrated, forward-looking approach. Critical infrastructure protection no longer operates within isolated silos of physical security, cybersecurity, or operational technology; instead, it requires harmonized strategies that traverse each domain. This introduction establishes the context for the ensuing analysis, underscoring how rapid digitalization, growing geopolitical tensions, and intensifying climate-driven disruptions have reshaped the imperatives for resilience. By framing the key challenges-ranging from ransomware targeting electric grids to supply chain vulnerabilities in water treatment facilities-this section lays the groundwork for understanding the urgency of a robust protection posture.
In this volatile ecosystem, stakeholders must navigate regulatory complexities, technological adoption cycles, and evolving threat actor capabilities. The emergence of regulatory frameworks such as updated cybersecurity directives, infrastructure modernization grants, and public–private partnership initiatives highlights the intersection of policy and practice. Moreover, the blending of cloud-native services with legacy operational technology architectures has created new attack surfaces, demanding innovative risk management approaches. Transitioning from ad hoc measures to a cohesive security architecture is critical for maintaining service continuity and safeguarding public welfare.
This executive summary synthesizes transformative shifts in the protection landscape, evaluates the cumulative impact of recent tariffs on supply chains, unpacks segmentation and regional insights, highlights key companies, and delivers actionable recommendations. The methodological rigor and expert validation underpinning the analysis ensure that decision-makers can confidently translate these insights into strategic decisions that bolster the resilience of critical infrastructure assets.
Embracing Unprecedented Technological Convergence and Threat Evolution Reshaping Critical Infrastructure Protection Strategies Worldwide
The protection of critical infrastructure is undergoing a fundamental metamorphosis driven by the convergence of emerging technologies and the sophistication of threat vectors. Traditional perimeter defenses are being augmented and, in some cases, replaced by adaptive security architectures that leverage artificial intelligence to detect anomalies in real time. As operational technology integrates with cloud platforms and digital twin simulations facilitate predictive maintenance, defenders now harness vast data streams to anticipate disruptions. This shift toward proactive, intelligence-driven security represents a departure from reactive incident response models, enabling organizations to address vulnerabilities before they metastasize into full-scale outages or breaches.
Concurrently, the proliferation of the Internet of Things across energy, transportation, and healthcare sectors has extended the attack surface exponentially. Each connected sensor or controller has the potential to introduce a weak link, intensifying the need for unified endpoint management and identity-based access controls. At the same time, advances in quantum-safe encryption and zero-trust frameworks are poised to redefine best practices for securing the most sensitive assets. The strategic imperative for operators lies in adopting modular, interoperable solutions that can evolve alongside emerging standards and regulatory mandates.
Ultimately, this landscape demands that security leaders cultivate an ecosystem mindset, forging collaborative partnerships across government, industry consortia, and technology providers. Only through collective intelligence sharing, cross-sector drills, and shared resilience frameworks can the community stay ahead of agile adversaries who exploit both technological and human vulnerabilities.
Examining the Far-Reaching Consequences of 2025 United States Tariffs on Critical Infrastructure Supply Chains and Operational Resilience
The imposition of new United States tariffs in 2025 has exerted significant pressure on the cost structures and supply chain strategies underpinning critical infrastructure projects. Tariffs on electronic components and specialized hardware have driven procurement teams to reassess their sourcing strategies, prioritizing regional partners and domestic manufacturers to mitigate exposure to escalating duties. As a result, project timelines have been extended to accommodate alternative suppliers, while capital expenditures have been reallocated to balance tariff-related price increases without compromising resilience objectives.
In parallel, the increased cost of imported cybersecurity solutions has prompted many operators to explore open-source and locally developed platforms. While this shift can foster innovation within domestic ecosystems, it also carries potential drawbacks in terms of interoperability with established vendor portfolios. Consequently, many organizations are investing in integration services to harmonize disparate tools, ensuring cohesive monitoring and incident response capabilities. These integration efforts often demand additional consulting and maintenance services, altering the revenue mix for solution vendors and service providers alike.
Moreover, the tariff-induced reorientation toward nearshore or onshore manufacturing has underscored the importance of dual-sourcing strategies and inventory optimization. Operators are now combining just-in-time delivery models with strategic stockpiles for critical spares, reducing the risk of operational disruptions due to supply chain bottlenecks. This recalibration of inventory policies has led to increased collaboration between procurement, operations, and security teams, ensuring that resilience remains a paramount consideration throughout the asset lifecycle.
Unlocking Strategic Advantage through In-Depth Component, Technology, Deployment, Lifecycle Phase, and End User Segmentation Analysis for Critical Infrastructure Protection
A nuanced understanding of market segmentation reveals the diverse factors shaping the critical infrastructure protection ecosystem. When examining components, it becomes clear that hardware-including controllers, IoT devices, and sensors-serves as the foundational layer upon which services and software operate. Consulting, integration, and maintenance services drive value by ensuring that these physical assets are configured, deployed, and managed effectively, while analytical tools, management platforms, and comprehensive platform solutions enable end-to-end visibility and control.
Technology segmentation further illuminates how cybersecurity software, identity and access management, network security, physical security systems, and surveillance systems each contribute unique capabilities. Within cybersecurity software, antivirus solutions, encryption tools, firewalls, and intrusion detection systems safeguard digital assets, whereas multi-factor authentication, privileged access management, and single sign-on reinforce identity-based controls. Network security encompasses firewalls, intrusion prevention systems, and virtual private networks, while physical security systems and surveillance solutions-access control, perimeter defenses, CCTV cameras, and video analytics-provide critical oversight of operational environments.
Deployment modes have evolved to encompass cloud, hybrid, and on-premise architectures, with private and public cloud options unlocking scalability and flexibility for remote monitoring, data analysis, and incident response. Lifecycle phase segmentation highlights the progression from detection-anomaly detection, incident detection, and threat monitoring-to prevention strategies such as risk assessments, security training, and vulnerability management. Recovery capabilities focus on data backup, recovery, and system restoration, while response functions, including disaster recovery and incident response services, ensure that organizations can rebound swiftly from disruptive events. Finally, end users spanning energy and utilities, government, healthcare, IT and telecom, and transportation sectors each exhibit unique resilience requirements that shape solution adoption and deployment strategies.
This comprehensive research report categorizes the Critical Infrastructure Protection market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Technology
- Deployment Mode
- Lifecycle Phase
- End User
Exploring Regional Dynamics Shaping Critical Infrastructure Protection Priorities Across Americas, Europe Middle East & Africa, and Asia-Pacific Markets
The regional dynamics influencing critical infrastructure protection priorities vary significantly across the Americas, Europe Middle East & Africa, and Asia-Pacific domains. In the Americas, emphasis on modernizing aging grid infrastructure and expanding renewable energy integration has driven rapid adoption of advanced analytics and cloud-based security platforms. Regulatory momentum, particularly around critical infrastructure cybersecurity standards, has incentivized utilities and transportation operators to accelerate digital transformation initiatives while aligning with federal and state mandates.
Across Europe Middle East & Africa, diverse regulatory landscapes coexist with unique threat profiles. European nations continue to refine cross-border collaborative mechanisms and adopt stringent cyber resilience directives. In the Middle East, strategic infrastructure projects, such as large-scale smart city developments, demand integrated security architectures that can handle both high volumes of data and critical operational continuity requirements. Meanwhile, Africa’s evolving network of telecom and public services presents opportunities for leapfrogging legacy systems with cloud-native solutions, though challenges remain around infrastructure investment and skills development.
In the Asia-Pacific region, robust growth in manufacturing and logistics has catalyzed significant investments in industrial cybersecurity and physical security convergence. Countries are increasingly mandating global cybersecurity frameworks, prompting organizations to bolster identity management, network monitoring, and real-time threat intelligence capabilities. Simultaneously, regional supply chain complexities and geopolitical considerations are driving a pivot toward supplier diversification and strategic partnerships to ensure uninterrupted operations.
This comprehensive research report examines key regions that drive the evolution of the Critical Infrastructure Protection market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Leading Innovators and Market Trailblazers Driving Resilience and Innovation in Critical Infrastructure Protection Ecosystems Globally
Leading innovators and established market players are driving the evolution of critical infrastructure protection through targeted investments and strategic partnerships. Global automation and engineering conglomerates have expanded their portfolios to include advanced cybersecurity services, integrating AI-driven threat detection with established OT control systems to deliver unified solutions. Meanwhile, technology titans renowned for network security have deepened their engagements with energy and utilities customers, customizing firewalls, intrusion prevention, and secure remote access platforms to address sector-specific compliance and operational challenges.
Concurrently, nimble specialists offering identity and access management have gained traction by developing modular, cloud-native authentication solutions optimized for hybrid deployments. Their ability to integrate with both legacy infrastructure and new digital services has made them key partners for transportation and telecom operators seeking to modernize access controls without disrupting critical operations. Surveillance and physical security vendors are likewise collaborating with software analytics firms to embed real-time video intelligence into broader security operations centers, creating holistic command-and-control capabilities.
In the services domain, consulting and system integration firms have aligned teams of domain experts, cybersecurity analysts, and field engineers to deliver tailored resilience assessments, incident response exercises, and maintenance programs. Through these multifaceted engagements, they help organizations validate risk models, test recovery workflows, and ensure that protective measures remain effective as threats and technologies continue to evolve.
This comprehensive research report delivers an in-depth overview of the principal market players in the Critical Infrastructure Protection market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- ABB Ltd.
- Cisco Systems, Inc.
- Emerson Electric Co.
- General Electric Company
- Honeywell International Inc.
- IBM Corporation
- Johnson Controls International plc
- Rockwell Automation, Inc.
- Schneider Electric SE
- Siemens Aktiengesellschaft
- Thales Group
Strategic Roadmap and Tactical Playbook for Industry Leaders to Strengthen Critical Infrastructure Protection Posture and Enhance Operational Resilience
To strengthen critical infrastructure protection and maintain operational resilience, industry leaders must adopt a strategic roadmap that balances technological innovation with pragmatic risk mitigation. The first step involves conducting continuous threat intelligence gathering and scenario planning, ensuring that both cyber and physical threat vectors are tracked in real time. From there, organizations should prioritize the deployment of adaptive architectures that support zero-trust principles, leveraging identity-based access controls and microsegmentation to contain potential breaches before they propagate.
In parallel, executives should champion investments in workforce development and cross-functional training programs that bridge the gap between IT, OT, and physical security teams. Fostering a culture of collaboration and shared accountability is crucial for sustaining effective incident response and recovery operations. Leaders are also encouraged to review and optimize their supply chain resilience by integrating dual sourcing, inventory buffering, and nearshoring strategies to minimize exposure to tariff fluctuations and global disruptions.
Finally, decision-makers should establish performance metrics that align with organizational resilience objectives, tracking key indicators such as mean time to detect, mean time to recover, and the percentage of assets covered under unified security frameworks. By embedding these metrics into executive dashboards and board-level reporting, leaders can maintain visibility into resilience posture and drive continuous improvement in the face of evolving threats.
Comprehensive Research Framework Integrating Multi-Tier Data Collection, Rigorous Analytical Techniques, and Expert Validation for Reliable Insights
The research methodology underpinning this analysis combines a multi-tiered approach to data collection, rigorous analytical techniques, and expert validation to ensure robust and reliable insights. Primary research included in-depth interviews with senior security executives, operational technology managers, and regulatory authorities, capturing firsthand perspectives on emerging threats, adoption challenges, and strategic priorities. These qualitative inputs were supplemented by detailed surveys targeting technology providers, integration partners, and end users across diverse sectors to quantify deployment patterns, maturity levels, and service preferences.
Secondary research involved a systematic review of publicly available regulatory documents, industry white papers, technical standards, and peer-reviewed publications. This desk research facilitated trend triangulation and supported the contextualization of primary findings within the broader policy and technological landscape. Advanced analytics techniques-including cluster analysis, use-case mapping, and scenario simulation-were applied to dissect the interdependencies among components, deployment modes, and lifecycle phases, revealing nuanced segmentation insights.
To validate the results, the findings were presented to an advisory panel composed of former utility CISOs, critical infrastructure policy experts, and cybersecurity researchers. Their feedback refined the analysis, addressed potential blind spots, and ensured that the recommendations align with real-world operational constraints. This comprehensive framework underpins the strategic relevance and actionable nature of the conclusions.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Critical Infrastructure Protection market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Critical Infrastructure Protection Market, by Component
- Critical Infrastructure Protection Market, by Technology
- Critical Infrastructure Protection Market, by Deployment Mode
- Critical Infrastructure Protection Market, by Lifecycle Phase
- Critical Infrastructure Protection Market, by End User
- Critical Infrastructure Protection Market, by Region
- Critical Infrastructure Protection Market, by Group
- Critical Infrastructure Protection Market, by Country
- United States Critical Infrastructure Protection Market
- China Critical Infrastructure Protection Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 3021 ]
Solidifying Forward-Looking Strategies through Integrated Insights to Elevate Critical Infrastructure Protection in an Ever-Evolving Threat Environment
In synthesizing the diverse insights presented, it becomes evident that securing critical infrastructure demands a holistic, forward-looking strategy that unifies physical, cyber, and operational technology domains. The transformative shifts identified-ranging from AI-driven detection capabilities to the convergence of cloud and edge deployments-underscore the necessity of adaptive architectures that can scale with evolving threats. At the same time, the cumulative impacts of tariffs have illustrated the interconnected nature of supply chain resilience and protection strategies, reaffirming the importance of diversified sourcing and inventory optimization.
By leveraging segmentation insights across components, technologies, deployment modes, lifecycle phases, and end-user requirements, organizations can more precisely align investments with their unique operational contexts. Regional nuances further influence these priorities, as regulatory regimes and infrastructure modernization agendas shape market dynamics in the Americas, Europe Middle East & Africa, and Asia-Pacific. Leading companies are already modeling best practices by integrating identity management, network security, physical surveillance, and advanced analytics into unified solutions, supported by agile service offerings that deliver continuous monitoring and rapid incident response.
Ultimately, the path forward hinges on a commitment to cross-sector collaboration, continuous learning, and metrics-driven governance. By embracing the strategic recommendations and research-backed frameworks outlined in this summary, decision-makers can solidify their resilience posture and ensure that critical infrastructure remains robust in the face of ever-shifting threat landscapes.
Empower Organizations with Expert Critical Infrastructure Protection Intelligence and Connect with Ketan Rohom to Access the Full Market Research Report Today
For organizations seeking to transform their approach to critical infrastructure protection, expert insights and comprehensive intelligence are essential. Engage directly with Ketan Rohom, Associate Director of Sales & Marketing, to obtain the full market research report that will equip your teams with strategic foresight, tactical guidance, and in-depth analysis. By partnering with a seasoned industry professional, you will gain exclusive access to the latest data, nuanced market perspectives, and actionable frameworks tailored to fortify operational resilience. Don’t miss this opportunity to empower your organization with the definitive resource on safeguarding vital infrastructure in an increasingly complex threat environment

- How big is the Critical Infrastructure Protection Market?
- What is the Critical Infrastructure Protection Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




