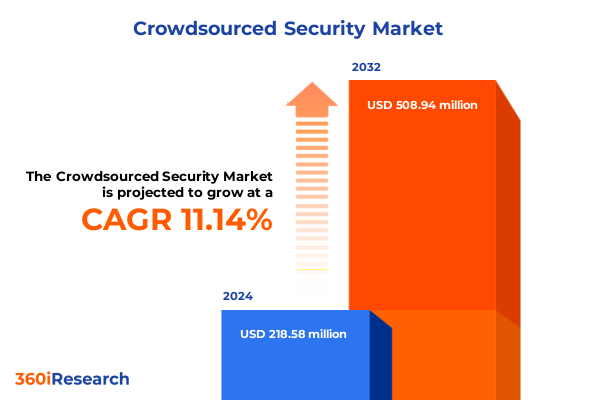
The Crowdsourced Security Market size was estimated at USD 242.52 million in 2025 and expected to reach USD 274.18 million in 2026, at a CAGR of 11.16% to reach USD 508.94 million by 2032.
Exploring the Critical Importance of Collaborative Crowdsourced Security in Safeguarding Complex Digital Infrastructures at Scale Amid Evolving Threats
The proliferation of sophisticated cyber threats has fundamentally reshaped the imperatives of modern organizations, elevating collaborative defense models from optional tools to strategic necessities. As technological ecosystems expand in size and complexity, the traditional perimeter-focused approach proves insufficient to detect and neutralize novel attack vectors. The growing digital attack surface demands innovative security solutions that leverage the collective intelligence of ethical hackers, security researchers, and organizational stakeholders.
Crowdsourced security has emerged as a critical component in this evolving landscape, harnessing the diverse skills of global talent pools to identify vulnerabilities that might otherwise go unnoticed. Beyond point-in-time assessments, continuous vulnerability discovery powered by coordinated incentives ensures rapid detection and remediation. Moreover, advances in platform capabilities enable seamless integration with existing security operations, fostering a dynamic feedback loop between defenders and external contributors.
Recognizing the strategic value of this model, decision-makers are increasingly prioritizing crowdsourced initiatives alongside traditional security investments. Early adopters report enhanced visibility into system weaknesses, improved organizational resilience, and a culture of proactive risk management. In this context, the following sections will delve into the key shifts driving adoption, the impact of macroeconomic factors, insights across segmentation and geographies, and recommended actions for leaders seeking to optimize their security posture.
Understanding Revolutionary Trends Redefining Crowdsourced Security Models and Driving Evolution Across Enterprise Risk Postures with Emerging Technologies
The crowdsourced security ecosystem is undergoing transformative shifts, propelled by exponential growth in attack sophistication and the convergence of emerging technologies. Machine learning and automation are enabling platforms to triage incoming vulnerability reports more efficiently, allowing human researchers to dedicate time to sophisticated exploit development. This synergy not only accelerates the identification of critical flaws but also enhances the quality of insights delivered to organizations.
Simultaneously, organizations are shifting from reactive to proactive security mindsets, embedding crowdsourced testing into the software development lifecycle. Continuous integration pipelines now incorporate dynamic and static analysis tools complemented by live bug bounty engagements, ensuring vulnerabilities are caught earlier and fixed before reaching production. As a result, the traditional boundaries between development, operations, and security teams are dissolving in favor of a DevSecOps approach that embraces external collaboration.
Regulatory landscapes are also evolving, with compliance frameworks increasingly recognizing and rewarding transparent vulnerability disclosure practices. Companies operating in highly regulated sectors are adopting crowdsourced models to satisfy stringent reporting requirements, while establishing clear policies that protect both organizations and ethical hackers. These combined forces are fundamentally redefining the role of crowdsourced security, positioning it as a cornerstone of modern risk management strategies.
Analyzing Revolutionary Trends Redefining Crowdsourced Security Models and Driving Evolution Across Enterprise Risk Postures with Emerging Technologies and Supply Chain Resilience Implications
The introduction of new tariffs by the United States in 2025 has ripple effects on global cybersecurity initiatives, specifically influencing the cost dynamics of crowdsourced security engagements. Increased duties on specialized hardware components and onshore professional services have prompted organizations to explore more cost-effective, remote testing models. Ethical hackers distributed worldwide are stepping in to fill geographic gaps, mitigating the impact of supply chain constraints and local service premiums.
Organizations subject to higher operational costs are reallocating budgets toward platforms that facilitate remote collaboration, enabling them to maintain or even expand their vulnerability research programs despite tighter margins. This shift encourages greater reliance on platform-based economies of scale, where subscription models and outcome-based pricing offer predictable budgeting and align costs with results. Providers that can demonstrate efficient global talent sourcing and rapid issue resolution gain a competitive edge in this tariff-inflated environment.
Moreover, the broader implications of these trade measures have made security leaders more vigilant about supply chain transparency and third-party risk. By diversifying their crowdsourced rosters across multiple regions, they can ensure continuous coverage even when local factors disrupt traditional service delivery. Ultimately, the 2025 tariff adjustments have underscored the strategic value of flexible, resilient security testing models that transcend geographic and economic barriers.
Uncovering In-Depth Insights Across Diverse Security Testing Types Deployment Models Organizational Scales and Industry Verticals for Tailored Risk Mitigation and Strategic Planning
Crowdsourced security adoption is nuanced across various testing methodologies, deployment frameworks, organizational scales, and industry verticals, revealing a tapestry of distinct use cases and value drivers. When viewed through the prism of security testing type, the most mature programs gravitate toward bug bounty initiatives and web application penetration testing, while emerging practices like threat hunting and red teaming gain traction in sectors requiring persistent adversary simulations. Simultaneously, mobile application pentesting and network infrastructure assessments remain essential for organizations prioritizing user-facing services and critical communications.
Deployment models influence the balance between control and scalability. On premises implementations appeal to highly regulated entities seeking granular data sovereignty, whereas public cloud offerings accelerate program launch and facilitate dynamic scaling. Private cloud solutions strike a balance, providing dedicated resources within a managed environment. This flexibility allows organizations to tailor their engagement model according to compliance demands and operational preferences.
Examining adoption through organizational size highlights divergent priorities. Large enterprises leverage extensive vulnerability assessment programs and code review services to manage vast codebases, while small and medium enterprises focus on targeted security audits complemented by focused penetration testing to optimize limited budgets. Within this spectrum, medium enterprises invest in comprehensive assessments across multiple layers, whereas small enterprises often start with web application and basic infrastructure testing.
Industry vertical distinctions further enrich this landscape. Banking, financial services, and insurance firms prioritize code review and vulnerability assessments to uphold transactional integrity, while government entities emphasize red teaming and threat hunting to safeguard critical national assets. Healthcare providers combine medical device pentesting with security audits to ensure patient safety, and IT and telecommunications companies adopt network infrastructure and penetration testing to protect service continuity. Retail and e-commerce organizations employ web and mobile application testing to secure customer interactions and maintain trust.
This comprehensive research report categorizes the Crowdsourced Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Security Testing Type
- Deployment Model
- Organization Size
- Industry Vertical
Examining Regional Variations and Emerging Patterns in Crowdsourced Security Adoption Across the Americas Europe Middle East Africa and Asia Pacific
Regional adoption patterns for crowdsourced security illustrate how local market dynamics and regulatory frameworks shape program evolution. In the Americas, maturity levels are highest in North America, where well-established platforms integrate seamlessly with enterprise-scale DevSecOps pipelines and compliance requirements such as those in the financial and healthcare sectors. Emerging economies in Central and South America are accelerating adoption, driven by growing digital transformation initiatives and public-private partnerships aimed at strengthening national cybersecurity postures.
In Europe, Middle East, and Africa, regulatory harmonization through frameworks like GDPR and upcoming directives incentivizes transparent vulnerability disclosure. Public sector agencies at federal and state levels collaborate with private sector organizations to launch regional bug bounty programs, fostering community engagement and risk awareness. Nations with advanced telecommunications infrastructures see robust growth in network and mobile application testing programs as digital services proliferate.
In the Asia-Pacific region, rapid digitalization and mobile-first economies fuel demand for crowdsourced assessments, especially in e-commerce hubs and fintech markets. Organizations leverage both global and local talent pools to address high-volume transaction systems and protect sensitive consumer data. The coexistence of public and private cloud deployment preferences reflects a balance between regulatory scrutiny and the need for agile scalability, shaping a dynamic and competitive landscape.
This comprehensive research report examines key regions that drive the evolution of the Crowdsourced Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Identifying Market Leaders Innovators and Emerging Players Shaping the Future of Crowdsourced Security Services Worldwide through Strategic Collaborations and Technological Breakthroughs
The competitive landscape of crowdsourced security is defined by a blend of established platforms, specialized service providers, and innovative startups. Leading global platforms have built extensive communities of ethical hackers, offering a broad range of testing types from penetration testing and code review to threat hunting and red teaming. These organizations typically differentiate themselves through advanced automation, integration capabilities, and robust compliance support tailored to critical sectors.
Meanwhile, specialized firms focus exclusively on high-value engagement types such as mobile application pentesting and medical device vulnerability assessments, capitalizing on deep vertical expertise. Their nimble structures enable rapid program customization and personalized customer support, appealing to emerging enterprises and sector-specific clients in government and healthcare. At the same time, rising startups leverage AI-driven vulnerability triage and predictive analytics to reduce noise in vulnerability feeds and accelerate remediation workflows.
Across this spectrum, providers compete on community quality, platform robustness, and outcome-based pricing models that align incentives between organizations and security researchers. The convergence of comprehensive service portfolios with flexible engagement options has become a critical success factor in retaining large enterprise clients and fostering long-term partnerships.
This comprehensive research report delivers an in-depth overview of the principal market players in the Crowdsourced Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Aqua Security Software Ltd.
- Bugcrowd, Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Cloudflare, Inc.
- Cobalt Security, Inc.
- CrowdStrike Holdings, Inc.
- Detectify AB
- Fortinet, Inc.
- Hacken OÜ
- HackerOne, Inc.
- International Business Machines Corporation
- Intigriti BV
- Palo Alto Networks, Inc.
- Qualys, Inc.
- SentinelOne, Inc.
- Synack, Inc.
- Tenable Holdings, Inc.
- Wiz, Ltd.
- YesWeHack SAS
- Yogosha SAS
- Zerocopter NV
- Zscaler, Inc.
Delivering Practical Strategic Recommendations for Executives to Elevate Security Posture and Maximize Value from Crowdsourced Security Programs
To derive maximum value from crowdsourced security, organizations should begin by embedding external testing into their development and operations workflows, establishing clear communication channels and defined response protocols. Prioritizing program objectives based on critical asset inventories ensures that vulnerability research is aligned with business risk tolerances and compliance obligations. Leaders must also invest in training internal teams to manage external engagement, fostering a culture that views ethical hackers as allies rather than adversaries.
Next, security and engineering teams should leverage continuous integration tools to automate vulnerability scans and vulnerability report ingestion, creating a seamless feedback loop that accelerates remediation. Developing robust metrics around time to triage, fix rate, and vulnerability severity trends will enable data-driven decision-making and resource allocation. Organizations should also evaluate pricing models that reward performance and outcomes, aligning external researcher incentives with internal objectives.
Finally, executive leadership must stay apprised of emerging threat landscapes and regulatory shifts, adapting program scopes to include specialized assessment types such as red teaming, threat hunting, and medical device testing. By fostering strategic partnerships with platforms that offer both depth in niche areas and breadth across testing methodologies, organizations can build resilient security postures that pivot quickly in response to evolving risks.
Explaining Comprehensive Research Approach Methodologies and Analytical Frameworks Underpinning the Crowdsourced Security Market Report to Ensure Rigor and Actionable Insights
This report is underpinned by a rigorous research framework that combines extensive primary and secondary investigation with expert validation. Primary research involved in-depth interviews with security leaders across multiple industries, capturing first-hand insights into program deployment, effectiveness, and emerging requirements. These qualitative findings were complemented by surveys of ethical hackers, providing perspective on platform usability, engagement incentives, and collaboration dynamics.
Secondary research synthesized publicly available information from regulatory guidelines, industry white papers, technical blogs, and peer-reviewed publications. Data on technology adoption, threat trends, and compliance developments were triangulated to identify prevailing patterns and future directions. A thorough analysis of case studies and program reports added further context, highlighting best practices and lessons learned from diverse organizational scenarios.
The analytical methodology employed a multi-layered approach, combining thematic coding for qualitative data, comparative benchmarking across deployment models and verticals, and scenario-based assessments to project the impact of macroeconomic factors such as tariffs. Throughout the process, findings were reviewed and validated by an advisory panel of security architects and compliance experts, ensuring accuracy, relevance, and actionable clarity.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Crowdsourced Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Crowdsourced Security Market, by Security Testing Type
- Crowdsourced Security Market, by Deployment Model
- Crowdsourced Security Market, by Organization Size
- Crowdsourced Security Market, by Industry Vertical
- Crowdsourced Security Market, by Region
- Crowdsourced Security Market, by Group
- Crowdsourced Security Market, by Country
- United States Crowdsourced Security Market
- China Crowdsourced Security Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 1908 ]
Drawing Conclusive Reflections on the Evolution Impact and Strategic Significance of Crowdsourced Security in Today’s Digital Risk Environment
As digital ecosystems continue to evolve, crowdsourced security stands out as a dynamic and resilient approach to vulnerability management, offering organizations unparalleled visibility and flexibility. The collaborative model harnesses the creativity and expertise of global researchers, ensuring that potential gaps are identified and addressed before they can be exploited. This proactive stance not only strengthens technical defenses but also fosters a culture of shared responsibility.
Across testing methodologies, deployment models, organizational scales, and industry verticals, the patterns of adoption reveal a maturing market that values agility, customization, and strategic alignment. Regulatory environments and macroeconomic variables further shape program structures, underscoring the importance of adaptable engagement frameworks that can pivot quickly in response to changing requirements.
Looking ahead, the integration of automation, machine learning, and continuous testing will propel crowdsourced security into new realms of efficiency and depth. Organizations that embrace this evolution, while adhering to robust program governance and performance measurement, will be best positioned to manage risk in an increasingly complex threat landscape. The insights and recommendations presented herein serve as a roadmap for navigating this journey and harnessing the full potential of crowdsourced security.
Encouraging Engagement with Industry Thought Leaders to Acquire In-Depth Crowdsourced Security Market Report Through Personalized Advisory Sessions
For a tailored discussion on how crowdsourced security insights can be integrated into your organization’s strategic roadmap and to gain exclusive access to comprehensive research findings, please reach out to Ketan Rohom, Associate Director, Sales & Marketing. Ketan is available to guide you through the report’s detailed analyses, address any unique business challenges, and offer customized advisory sessions to help translate insights into actionable strategies. Engaging directly will ensure that you extract maximum value from the study and stay ahead of emerging security threats.

- How big is the Crowdsourced Security Market?
- What is the Crowdsourced Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




