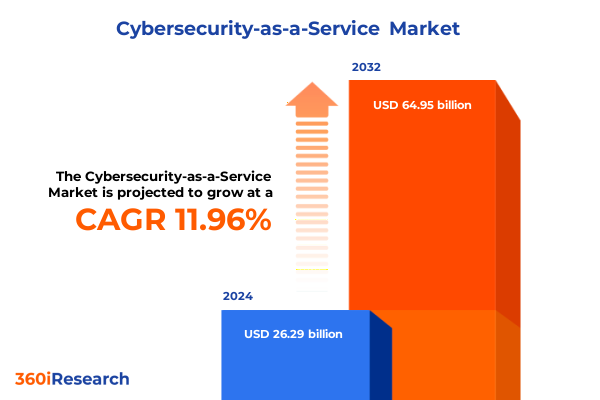
The Cybersecurity-as-a-Service Market size was estimated at USD 29.48 billion in 2025 and expected to reach USD 32.74 billion in 2026, at a CAGR of 11.94% to reach USD 64.95 billion by 2032.
Navigating the Evolving Security Terrain as Enterprises Pivot to Cybersecurity-as-a-Service in an Era of Heightened Digital Threats
In an era marked by escalating threats and accelerating digital transformation, organizations of all sizes are recognizing the limitations of traditional perimeter-based security models. The convergence of cloud computing, remote workforces, and an expanding threat landscape has made it imperative for enterprises to seek flexible, scalable, and cost-effective cybersecurity solutions. Cybersecurity-as-a-Service has emerged as a pivotal framework, enabling businesses to outsource critical security functions while benefiting from specialized expertise and advanced technologies.
This model transcends the constraints of standalone hardware appliances and siloed software deployments by offering continuous monitoring, real-time threat intelligence, and on-demand access to best-in-class security capabilities. As enterprises strive to maintain agility in their operations, they demand security solutions that align with dynamic infrastructure needs and evolving business priorities. Consequently, the adoption of subscription-based security services is reshaping how organizations allocate resources, manage risk, and orchestrate cybersecurity strategies.
As this report will demonstrate, the shift toward a service-centric security paradigm is not merely a response to immediate threats but a strategic initiative that underpins digital resilience. It empowers organizations to focus on their core competencies while leveraging a broad ecosystem of specialized security providers. This introductory analysis sets the stage for understanding the transformative drivers, segmentation nuances, regional variations, and strategic imperatives that define today’s cybersecurity-as-a-service landscape.
Identifying the Fundamental Transformations Redefining Cybersecurity Delivery Models and Strategies Across Global Enterprises
The cybersecurity paradigm is undergoing profound transformation as organizations grapple with increasingly sophisticated attack vectors and regulatory complexities. Cloud-native architectures have become the backbone of modern IT environments, compelling service providers to integrate security directly into infrastructure and application layers. This has given rise to holistic frameworks that merge network security controls with identity governance, threat intelligence, and proactive vulnerability assessment.
At the same time, the zero-trust model has gained rapid traction, shifting the focus from perimeter defense to continuous verification of user identities, device integrity, and contextual risk factors. Machine learning and artificial intelligence are now foundational elements in automated threat detection and response workflows, enabling security operations centers to triage alerts with greater precision and speed. These capabilities, once reserved for large enterprises, are increasingly accessible through managed platforms and co-managed service offerings.
Moreover, the convergence of extended detection and response with strategic threat intelligence has fostered a collaborative ecosystem among vendors, service partners, and government agencies. This collaboration ensures that emerging threat patterns are identified and mitigated at scale, while also informing policy development and compliance frameworks. As a result, cybersecurity-as-a-service providers are positioning themselves not just as vendors, but as strategic allies in digital transformation journeys, reshaping the competitive landscape and redefining the nature of security engagement.
Assessing the Multifaceted Consequences of Newly Imposed United States Tariffs on Cybersecurity Service Delivery and Infrastructure Costs
In 2025, a series of tariff adjustments introduced by the United States government has exerted notable pressure on the global cybersecurity market, particularly affecting hardware-dependent solutions and supply chains. By imposing additional duties on imported appliances and security devices, these measures have elevated procurement costs for organizations that rely on physical firewalls, intrusion detection systems, and on-premises security operations centers. As a result, many enterprises have accelerated their migration toward cloud-based and hybrid deployment models to mitigate capital expenditure risks.
Vendors have responded by optimizing their service portfolios to emphasize software-defined solutions and subscription-based licensing, thereby reducing reliance on hardware sales. This strategic pivot has enabled providers to preserve margins while offering price-stable service tiers that absorb tariff-related cost fluctuations. Customers benefit from the predictability of operational expenditures and the flexibility to scale services in response to evolving threat landscapes.
While the increased cost of hardware has driven some slowdown in on-premises deployments, it has simultaneously spurred innovation in virtualized security functions and cloud-native managed detection and response platforms. These shifts underscore a broader industry trend toward decoupling security capabilities from physical infrastructure and emphasize the value of elasticity, resilience, and global threat intelligence networks in maintaining robust cybersecurity postures.
Uncovering Critical Insights from Service Type Deployment Model Organizational Size and Industry Vertical Breakdown in Cybersecurity-as-a-Service
The cybersecurity-as-a-service market can be dissected through multiple analytical lenses, revealing nuanced demand patterns and adoption behaviors. An examination of service type highlights that offerings such as Firewall as a Service, which encompasses next-generation and web application firewalls, remain foundational security controls. At the same time, the growing need for identity governance has propelled demand for identity and access management as a service, particularly in multi-factor authentication, privileged access management, and single sign-on solutions. In parallel, managed detection and response services-whether delivered through cloud-based platforms, endpoint-centric solutions, or network-based architectures-are gaining traction as organizations seek continuous vigilance against advanced threats.
Deployment model segmentation underscores that pure cloud implementations have surged, driven by the agility they offer, while hybrid frameworks remain popular among enterprises balancing legacy investments with modern security demands. On-premises deployments, although experiencing relative contraction, continue to serve highly regulated industries requiring localized control.
From the standpoint of organizational size, large enterprises leverage comprehensive service bundles to integrate threat intelligence-as-a-service with security operations center-as-a-service functions, whether through co-managed arrangements or fully managed service models. Meanwhile, small and medium enterprises often prioritize streamlined vulnerability management as a service, focusing on penetration testing and vulnerability assessment to address critical exposure points.
Industry-specific perspectives reveal that sectors such as banking, where traditional financial institutions and capital markets coexist with insurance entities, emphasize strategic intelligence feeds. Government agencies and defense organizations require tactical and operational intelligence layers, whereas healthcare and life sciences entities balance regulatory compliance with protective measures across biotechnology, clinical, and pharmaceutical environments. Similarly, IT and telecom providers, from cloud service operators to telecom carriers, integrate threat intelligence into service level agreements, and manufacturers across automotive, electronics, and heavy equipment sectors seek tailored security frameworks to safeguard industrial control systems.
This comprehensive research report categorizes the Cybersecurity-as-a-Service market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Service Type
- End User Industry
- Deployment Model
- Organization Size
Unearthing Regional Variations in Adoption and Priorities across Americas Europe Middle East & Africa and Asia-Pacific Markets for Cybersecurity-as-a-Service
Regional dynamics play a critical role in shaping adoption curves and strategic priorities for cybersecurity-as-a-service offerings. In the Americas, enterprises are rapidly embracing managed detection and response and security operations center-as-a-service engagements, fueled by substantial investments in cloud transformation and a proactive regulatory environment that mandates breach reporting. The North American market is characterized by early stage diffusion of zero-trust frameworks and a strong affinity for integrated threat intelligence subscriptions that augment existing security portfolios.
Across Europe, the Middle East, and Africa, compliance imperatives such as GDPR have driven significant uptake of identity and access management services, particularly in multi-factor authentication and privileged access management implementations. Meanwhile, the Gulf Cooperation Council and African markets are witnessing a surge in demand for vulnerability management services, as regional policymakers intensify data protection mandates. Service providers in these territories are customizing their portfolios to align with varying maturity levels, ranging from civil government agencies to defense organizations where fully managed security operations remain a priority.
In Asia-Pacific, a confluence of digital initiatives and heightened awareness of state-sponsored threats has elevated the importance of threat intelligence as a service, spanning operational, strategic, and tactical intelligence layers. Cloud service providers across the region are embedding web application firewall capabilities into their PaaS offerings, while emerging economies drive growth in single sign-on and endpoint-focused managed detection and response solutions. Collectively, these regional distinctions inform product roadmaps and strategic investments for vendors seeking to optimize global delivery networks.
This comprehensive research report examines key regions that drive the evolution of the Cybersecurity-as-a-Service market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Strategic Positioning and Offerings of Leading Cybersecurity-as-a-Service Providers Shaping the Evolving Competitive Landscape
The competitive landscape of cybersecurity-as-a-service is defined by a mix of legacy technology titans and agile pure-play specialists. Network security stalwarts continue to bolster their cloud-based firewall and threat intelligence portfolios through strategic acquisitions of emerging analytics firms. Meanwhile, endpoint protection innovators are enhancing their managed detection and response offerings with advanced machine learning capabilities and extended detection and response integrations.
Key global players distinguish themselves through differentiated service models: some offer co-managed security operations centers that complement in-house teams, while others emphasize fully managed platforms with continuous threat hunting and incident response guarantees. Providers of identity and access management-as-a-service are forging alliances with major cloud hyperscalers to embed authentication and authorization controls directly into PaaS environments, thereby streamlining integration and enhancing end-user experiences.
In the vulnerability management sector, specialized firms are integrating automated penetration testing frameworks with real-time risk scoring, enabling rapid vulnerability prioritization. The ongoing consolidation among mid-tier managed security service providers aims to deliver end-to-end security operations under a unified service umbrella, catering to both large enterprises and resource-constrained small and medium enterprises. These strategic moves underscore the importance of both scale and specialization as defining factors in a market that values agility, innovation, and deep domain expertise.
This comprehensive research report delivers an in-depth overview of the principal market players in the Cybersecurity-as-a-Service market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Accenture PLC
- Amazon Web Services Inc.
- Arctic Wolf Networks Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems Inc.
- CrowdStrike Holdings Inc.
- Cynet Security Ltd.
- eSentire Inc.
- F-Secure Corporation
- FireEye Inc.
- Fortinet Inc.
- Google LLC
- IBM Security
- Kaspersky Lab
- McAfee Corp.
- Microsoft Corporation
- Palo Alto Networks Inc.
- Qualys Inc.
- Rapid7 Inc.
- Red Canary Inc.
- Secureworks Corp.
- Sophos Ltd.
- Symantec Corporation
- Trend Micro Incorporated
- Trustwave Holdings Inc.
Delivering Pragmatic Strategic and Operational Recommendations to Maximize Organizational Resilience and Value from Cybersecurity-as-a-Service Investments
As organizations prepare to navigate the complexities of the cybersecurity-as-a-service ecosystem, several actionable steps can enhance strategic outcomes. Leaders should first evaluate their existing security investments and identify areas where managed services can complement or replace legacy solutions, thereby optimizing total cost of ownership and improving time-to-detect metrics. Embracing a phased approach to zero-trust migration will reduce operational disruption while establishing a scalable foundation for continuous verification and micro-segmentation.
Next, enterprises should prioritize partnerships with providers that offer modular service portfolios, allowing for incremental adoption of capabilities such as vulnerability management, threat intelligence, and security operations center functions. This modularity empowers organizations to align security tangibly with business objectives and regulatory requirements across industries.
Furthermore, integrating advanced analytics and automation into incident response workflows can accelerate containment efforts and reduce alert fatigue. Investing in skills development and change management will maximize the value derived from managed service engagements and foster a security-aware culture. Finally, establishing clear service level agreements with measurable performance indicators ensures accountability and drives continuous improvement. By adhering to these strategic recommendations, industry leaders can transform managed cybersecurity services from cost centers into catalysts for business resilience and innovation.
Detailing the Rigorous Research Methodology and Data Collection Techniques Underpinning the Robust Cybersecurity-as-a-Service Market Intelligence
This analysis is underpinned by a rigorous research methodology that combines primary and secondary data sources to ensure comprehensive market intelligence. Primary research involved structured interviews with senior security executives, technology specialists, and managed service providers spanning multiple industries and geographic regions. These interviews provided qualitative insights into adoption drivers, deployment challenges, and service-level expectations.
Secondary research encompassed a thorough review of regulatory frameworks, industry whitepapers, vendor collateral, and publicly available financial reports. Data triangulation techniques were applied to validate market trends and ensure consistency across diverse information sets. Quantitative analysis leveraged proprietary databases and structured models to map service-type segmentation, deployment preferences, and organization-size distinctions.
In addition, expert validation sessions were conducted with industry analysts and cybersecurity consultants to refine the segmentation framework and verify the relevance of key drivers. Regional market assessments incorporated localized intelligence from governmental publications, trade associations, and regional security centers. The integration of these methodologies ensures that the findings presented herein reflect both depth and breadth, yielding actionable insights that support informed decision making in cybersecurity-as-a-service procurement and strategy.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Cybersecurity-as-a-Service market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Cybersecurity-as-a-Service Market, by Service Type
- Cybersecurity-as-a-Service Market, by End User Industry
- Cybersecurity-as-a-Service Market, by Deployment Model
- Cybersecurity-as-a-Service Market, by Organization Size
- Cybersecurity-as-a-Service Market, by Region
- Cybersecurity-as-a-Service Market, by Group
- Cybersecurity-as-a-Service Market, by Country
- United States Cybersecurity-as-a-Service Market
- China Cybersecurity-as-a-Service Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 2544 ]
Concluding Synthesis Emphasizing Key Strategic Imperatives and Growth Opportunities Emerging from the Cybersecurity-as-a-Service Executive Analysis
In conclusion, the cybersecurity-as-a-service market is at a pivotal juncture where technological innovation, economic pressures, and regulatory mandates converge to redefine how organizations secure digital assets. The migration from hardware-centric defenses to cloud-native, service-driven models signifies a strategic shift towards agility, scalability, and continuous risk management. As tariff-related cost pressures incentivize software-centric solutions, providers are accelerating the development of virtualized security functions that meet stringent performance and compliance requirements.
Segmentation insights reveal differentiated adoption patterns, with large enterprises favoring comprehensive co-managed and fully managed portfolios, while small and medium enterprises selectively deploy targeted vulnerability and identity management services. Regional analyses underscore the nuanced interplay of regulatory regimes, digital maturity, and threat landscapes across the Americas, EMEA, and Asia-Pacific markets.
For organizations charting their cybersecurity roadmaps, the recommendations detailed in this report provide a clear blueprint to harness managed services effectively, optimize resource allocation, and foster resilient security cultures. By leveraging the robust research methodology that supports this analysis, decision makers can confidently select service partners and design security architectures that align with evolving business imperatives. Ultimately, the insights presented here empower stakeholders to transform cybersecurity from a protective necessity into a strategic enabler of digital innovation and sustainable growth.
Engage Today with Ketan Rohom to Obtain Comprehensive Cybersecurity-as-a-Service Market Insights and Empower Your Strategic Decision Making
To deepen your understanding of this market’s evolving dynamics and capitalize on the insights shared throughout this executive summary, you are invited to engage directly with Ketan Rohom, Associate Director of Sales & Marketing. His expertise in cybersecurity-as-a-service market strategy will guide you through the detailed report and help you tailor its findings to your organization’s specific needs. By partnering with him, you will gain access to supplemental data, proprietary analysis, and bespoke advisory support aimed at reinforcing your organization’s security posture and strategic planning. Don’t miss the opportunity to translate these insights into actionable strategies-reach out to Ketan Rohom today and secure the full market research report to drive informed decision making and sustainable competitive advantage.

- How big is the Cybersecurity-as-a-Service Market?
- What is the Cybersecurity-as-a-Service Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




