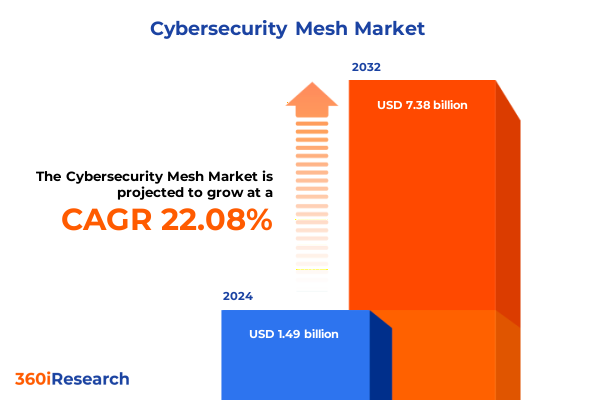
The Cybersecurity Mesh Market size was estimated at USD 1.83 billion in 2025 and expected to reach USD 2.17 billion in 2026, at a CAGR of 22.01% to reach USD 7.38 billion by 2032.
Unveiling Cybersecurity Mesh Architecture as a Foundational Framework for Securing Distributed Digital Assets in Hybrid and Multicloud Environments
The executive summary introduces cybersecurity mesh architecture as a revolutionary approach to securing distributed digital assets across modern enterprises. It highlights the necessity of moving beyond traditional perimeter-focused defenses to a decentralized, identity-centric security framework that adapts to hybrid and multicloud environments. By weaving together disparate security capabilities into an interoperable fabric, organizations can achieve continuous, context-aware protection, minimize security gaps, and enhance visibility across all touchpoints. This paradigm shift responds to the evolving threat landscape, where sophisticated attackers exploit silos and blind spots in legacy security models.
By framing cybersecurity mesh architecture as a foundational framework, the introduction sets the stage for an in-depth exploration of its transformative potential, the impact of external factors such as trade policies, and critical market segmentation insights. It underscores the imperative for executives and security leaders to understand emerging dynamics, evaluate vendor ecosystems, and align technology investments with long-term resilience objectives. This section establishes the context for the detailed analysis that follows, emphasizing the role of mesh architecture in shaping the future of enterprise cybersecurity.
Examining the Transformative Shifts Driving the Adoption of Cybersecurity Mesh Through Identity-First, Composable, and AI-Driven Security Models
The shift toward cybersecurity mesh architecture marks a fundamental transformation in how organizations defend their digital estates. Traditional perimeter models, anchored on network borders and static controls, are increasingly inadequate in an era of remote work, cloud services, and proliferating IoT devices. Cybersecurity mesh introduces a composable security fabric that places identity at its core, ensuring that every user, device, and application must authenticate and be continuously validated before accessing resources. This identity-first approach delivers a flexible security posture that adapts to changing risk profiles and dynamic IT topologies, reducing reliance on fixed trust boundaries and mitigating lateral movement of threats.
Simultaneously, modular and composable design principles drive mesh adoption by enabling best-of-breed components to interoperate within a unified architecture. Security functions such as access control, threat detection, and encryption operate as discrete services that can be assembled, extended, or replaced without disrupting the overall fabric. Organizations can therefore tailor implementations to unique needs, scale seamlessly with business growth, and accelerate deployment cycles. The integration of real-time threat intelligence and analytics across the mesh boosts responsiveness and automates policy enforcement, trimming incident response times by up to 85 percent in mesh-enabled environments.
Lastly, the advent of AI-driven and orchestrated response mechanisms has elevated mesh architectures to new heights of agility. Security Orchestration, Automation, and Response (SOAR) workflows embedded within the mesh fabric can isolate compromised nodes, revoke access tokens, or trigger forensics processes in seconds. This level of cross-domain orchestration breaks down silos between identity, network, and endpoint controls, providing cohesive incident management across hybrid and multicloud landscapes. By decentralizing decision-making yet maintaining centralized oversight, organizations “centralize to decentralize” risk management and empower resource owners to act swiftly while adhering to enterprise-wide policies.
Analyzing the Cumulative Impact of 2025 United States Tariff Policies on Cybersecurity Mesh Supply Chains, Costs, and Resilience Strategies
The introduction of reciprocal U.S. tariffs in early 2025 significantly disrupted the cybersecurity mesh supply chain, driving up hardware and component costs by double-digit percentages. Providers of firewalls, routers, and SD-WAN appliances faced 25 percent surcharges on Canadian imports, while tariffs on goods assembled or partially sourced in China reached 34 percent. As a result, manufacturing expenses for network security appliances surged, prompting many vendors to consider reshoring production or extending hardware refresh cycles from three to five years to offset increased outlays.
Beyond hardware, the tariffs exerted pressure on customer budgets as organizations grappled with economic uncertainty and tariff-induced price increases. Cybersecurity teams reported budgetary cutbacks of up to 15 percent as companies reprioritized spending to manage supply chain costs. This fiscal strain has slowed procurement of new security deployments and delayed major product launches, particularly in small and medium-sized enterprises that operate on tighter financial margins. Analysts warn that decreased near-term demand and lengthened procurement cycles could erode recurring revenue streams for vendors and contract manufacturers alike.
Moreover, the trade tensions have amplified supply chain cyber risks by introducing less-secure tier-two vendors into critical workflows. In efforts to meet production targets amid tariff deadlines, some organizations onboarded new suppliers without comprehensive security vetting, thereby expanding their attack surface. Threat actors have exploited these weak links, targeting less mature partners to infiltrate larger enterprises. This convergence of trade disruptions and cyber vulnerabilities underscores the importance of embedding mesh-based controls at every node of the supply chain, reinforcing resilience against both economic and security shocks.
Deriving Actionable Market Segmentation Insights Across Components, Deployment Modes, Organization Sizes, and Industry Verticals Within Cybersecurity Mesh
The cybersecurity mesh landscape is nuanced across multiple dimensions, beginning with components that span access control, data security, endpoint security, identity security, and network security. Within these domains, subsegments such as Privileged Access Management, Data Loss Prevention, and Endpoint Detection and Response reveal specialized areas of investment where enterprises seek tailored protection aligned to unique risk profiles. Deployment modes further refine these choices, as organizations balance the agility of cloud-native mesh services against the control of on-premises solutions and the flexibility of hybrid architectures. This triad informs strategic roadmaps and operational priorities.
Organizational size dictates differential adoption patterns, with large enterprises often pioneering mesh proofs-of-concept across global estates, while small and medium-sized enterprises favor managed services and subscription-based offerings to minimize upfront commitments. Industry verticals introduce additional complexity: the financial services sector demands rigorous identity and access management controls to meet regulatory mandates, healthcare prioritizes data encryption and loss prevention to protect patient records, and manufacturing emphasizes network segmentation to safeguard operational technology environments. Across each segment, the mesh model enables granular policy enforcement at the asset level, ensuring that security investments align precisely with stakeholder requirements and risk appetites.
This comprehensive research report categorizes the Cybersecurity Mesh market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Deployment Mode
- Organization Size
- End User Industry
Uncovering Key Regional Dynamics Shaping Cybersecurity Mesh Adoption Trends Across the Americas, Europe Middle East & Africa, and Asia-Pacific Markets
Regional dynamics significantly influence the pace and focus of mesh adoption. In the Americas, North American enterprises lead investments in mesh architectures, driven by stringent privacy regulations like the California Consumer Privacy Act and robust venture capital activity fueling next-generation identity fabrics. Public and private sectors alike are forging partnerships with managed security service providers to integrate mesh solutions into national critical infrastructure, positioning the region at the forefront of identity-centric security innovation.
In Europe, Middle East & Africa, data sovereignty initiatives and the General Data Protection Regulation have catalyzed demand for data-centric mesh controls. Established enterprises in Western Europe collaborate with emerging digital economies in the Middle East and Africa, leveraging open-source security platforms and regional incident response coalitions. This cross-border cooperation strengthens resilience across essential services, from energy and utilities to government functions. Meanwhile, Asia-Pacific markets exhibit rapid adoption curves, as mandates on data localization and cybersecurity standards in China, India, and Australia accelerate mesh deployments in finance, healthcare, and telecommunications. Partnerships between local vendors and global technology leaders create tailored solutions that address unique compliance and threat landscapes.
This comprehensive research report examines key regions that drive the evolution of the Cybersecurity Mesh market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Strategic Movements of Leading Cybersecurity Mesh Vendors and Emerging Innovators Shaping the Competitive Landscape
Leading cybersecurity vendors are aggressively evolving their portfolios to seize mesh market opportunities. Legacy network security incumbents such as Cisco Systems have integrated mesh principles by embedding zero-trust firewalls and identity-driven access controls directly into networking infrastructure. Their Hybrid Mesh Firewall offerings and Universal Zero Trust Network Access solutions fuse security and network operations, enabling seamless policy management across on-premises, cloud, and AI-driven environments.
Pure-play security innovators are also reshaping the competitive landscape. Palo Alto Networks continues to expand its Prismo XSIAM platform with mesh orchestration capabilities, while Fortinet advances its Security Fabric through tighter integration of identity, endpoint, and network modules. Check Point and Trend Micro emphasize AI-enhanced threat detection at mesh enforcement points, and emerging cloud-native specialists such as Zscaler and CrowdStrike deliver lightweight, API-first mesh services that simplify deployments for digital-first enterprises. Across this ecosystem, partnerships and strategic acquisitions underscore the race to offer cohesive, end-to-end mesh architectures that address evolving customer requirements.
This comprehensive research report delivers an in-depth overview of the principal market players in the Cybersecurity Mesh market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Akamai Technologies Inc.
- Appgate Inc.
- Banyan Security Services Inc.
- Cato Networks Ltd.
- Check Point Software Technologies Ltd.
- CrowdStrike Holdings Inc.
- Cybereason Inc.
- Forcepoint LLC
- Fortinet Inc.
- Gurucul Solutions Pvt. Ltd.
- Illumio Inc.
- Palo Alto Networks Inc.
- TrueFort Inc.
- ZeroTier Inc.
- Zscaler Inc.
Formulating Actionable Recommendations for Industry Leaders to Harness Cybersecurity Mesh Architecture and Future-Proof Their Security Posture
To harness the full potential of cybersecurity mesh, industry leaders should initiate cross-functional governance structures that embed mesh principles into enterprise security charters. By empowering resource owners with clear accountability frameworks and decision rights, organizations can “centralize to decentralize” risk management and ensure consistent policy enforcement across diverse business units. Additionally, prioritizing identity first and designing security modules as composable microservices will enable rapid adaptation to shifting threat vectors and technology evolutions.
Leaders must also conduct rigorous supply chain risk assessments that incorporate mesh-based controls at every vendor touchpoint, mitigating exposure to emerging third-party vulnerabilities. Investing in data science capabilities within security teams can further enhance anomaly detection and risk scoring, while aligning mesh deployments with regulatory mandates and digital sovereignty initiatives will optimize compliance and governance. Finally, ongoing performance measurement and scenario-based stress testing will validate mesh designs, ensuring resilience under economic pressures and evolving threat landscapes.
Detailing the Comprehensive Research Methodology Employed to Ensure Robust, Unbiased Analysis of the Cybersecurity Mesh Landscape
This analysis employed a rigorous research methodology combining primary and secondary sources to deliver a comprehensive view of the cybersecurity mesh market. Primary research included in-depth interviews with IT and security executives across industries, structured discussions with vendor product teams, and workshops with cybersecurity consultants. Secondary research drew upon authoritative industry reports, regulatory frameworks, vendor white papers, and peer-reviewed publications to ensure contextual accuracy and conceptual rigor. Insights were validated through cross-referencing multiple data points and scenario modeling to account for economic, technological, and geopolitical variables.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Cybersecurity Mesh market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Cybersecurity Mesh Market, by Component
- Cybersecurity Mesh Market, by Deployment Mode
- Cybersecurity Mesh Market, by Organization Size
- Cybersecurity Mesh Market, by End User Industry
- Cybersecurity Mesh Market, by Region
- Cybersecurity Mesh Market, by Group
- Cybersecurity Mesh Market, by Country
- United States Cybersecurity Mesh Market
- China Cybersecurity Mesh Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 2226 ]
Concluding Insights on the Strategic Imperatives and Long-Term Opportunities Presented by Cybersecurity Mesh Architecture
Cybersecurity mesh architecture represents a strategic inflection point for securing modern enterprises amid escalating threat complexity and supply chain disruptions. By decentralizing control, prioritizing identity, and embracing composable security modules, organizations can achieve adaptive, resilient defenses that bridge existing silos. Coupled with data-driven orchestration and AI-enabled response mechanisms, mesh architectures promise to redefine incident management, bolster compliance, and future-proof digital transformation initiatives. As economic headwinds and regulatory mandates continue to reshape IT priorities, mesh strategies will be instrumental in safeguarding competitive advantage and sustaining long-term organizational resilience.
Take Next Steps Today to Secure Your Competitive Edge by Connecting with Ketan Rohom for the Full Cybersecurity Mesh Market Research Report
To gain a comprehensive view of the cybersecurity mesh market and secure your strategic roadmap, contact Ketan Rohom, Associate Director of Sales & Marketing, to obtain the full market research report and empower your organization with data-driven intelligence.

- How big is the Cybersecurity Mesh Market?
- What is the Cybersecurity Mesh Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




