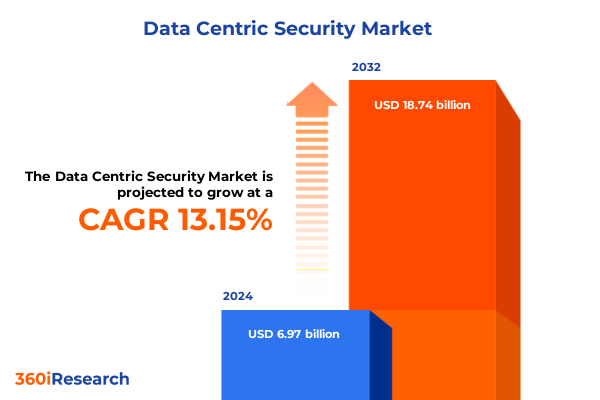
The Data Centric Security Market size was estimated at USD 7.78 billion in 2025 and expected to reach USD 8.70 billion in 2026, at a CAGR of 13.36% to reach USD 18.74 billion by 2032.
Positioning Data Centric Security as the Strategic Backbone of Trust, Resilience, and Compliance in a Hyperconnected Economy
Data is now at the heart of competitive advantage, and it has simultaneously become a primary target for increasingly sophisticated adversaries. Over the past two years, data breaches and ransomware campaigns have escalated in both frequency and impact, with global studies showing that breach-related disruption and recovery costs have climbed to record levels as attackers exfiltrate larger volumes of sensitive information and exploit complex hybrid environments. At the same time, regulatory regimes worldwide continue to tighten expectations around privacy, reporting timelines, and demonstrable controls over personal, financial, and health data.
In this context, data centric security has moved from a specialist concern to a board-level imperative. Rather than focusing solely on defending networks or endpoints, data centric strategies prioritize the protection of information itself-wherever it resides and however it moves. This approach spans technologies such as strong encryption, tokenization, data masking, data loss prevention, and continuous monitoring of database and application activity. It also requires mature governance, including clear data classification, policies for access and retention, and robust key management.
Organizations across banking and financial services, healthcare, government, manufacturing, technology, and retail are therefore reassessing how they architect security. Many are discovering that legacy perimeter-centric controls cannot adequately manage risks associated with cloud adoption, software-as-a-service, and the rapid use of generative AI models trained on large volumes of sensitive content. Data centric security provides a unifying framework for addressing these challenges by aligning protection mechanisms with the value and sensitivity of data, rather than with the boundaries of individual systems.
This executive summary synthesizes key findings on transformative shifts in the landscape, the implications of the 2025 United States tariff environment, critical segmentation dynamics, regional patterns, and the strategies of leading providers. It is designed to equip executives and security leaders with a concise yet nuanced understanding of where the market is heading and what actions are most likely to strengthen resilience, support compliance, and preserve trust in the years ahead.
Capturing the Paradigm Shift from Perimeter Defenses to Intelligent, Data Aware Controls Across Hybrid, Multi Cloud, and AI Driven Environments
The most profound change reshaping security is the shift from perimeter and device-centric defenses to architectures that assume compromise and focus on securing data in every state-at rest, in motion, and in use. Zero trust principles are increasingly being operationalized at the data layer, with organizations enforcing least-privilege access based on granular attributes such as user role, device posture, and data classification, rather than relying solely on network location. This evolution is a direct response to an environment where ransomware, extortion, and data theft campaigns now routinely bypass traditional controls, and where a significant share of incidents involve data spread across multiple clouds and on-premises environments.
Alongside this architectural shift, automation and artificial intelligence have become central to effective data centric security. Recent breach analyses show that organizations extensively deploying AI-driven security and automation identify and contain incidents materially faster and at lower cost than those that do not. In practice, this means using machine learning to automatically discover and classify sensitive records, detect anomalous access patterns in real time, and adapt data protection policies based on observed behavior. These capabilities are particularly valuable for reducing so‑called “shadow data,” where sensitive information appears in ungoverned data stores, collaboration tools, and AI training sets.
Another transformative trend is the convergence of data centric security with data governance, privacy, and analytics platforms. Organizations are increasingly embedding encryption, tokenization, and masking directly into data pipelines and analytics workflows so that sensitive attributes are protected without undermining the business value of large-scale data processing. Vendors are responding by delivering integrated platforms that combine data discovery, classification, encryption, masking, and access governance, often delivered as cloud-native services that can span multi-cloud and hybrid estates.
Finally, the rise of generative AI has sharpened focus on securing data used to train and prompt large models. Enterprises are scrutinizing how personal and proprietary information flows into AI workloads, applying stricter controls on what can be ingested, and relying more heavily on techniques such as masking and pseudonymization to protect privacy while still enabling innovation. Regulators and industry bodies are beginning to issue guidance for responsible AI, and data centric security is emerging as the primary mechanism for aligning AI adoption with legal and ethical expectations.
Assessing How the 2025 United States Tariff Environment Reshapes Supply Chains, Costs, and Strategic Investment in Data Centric Security
The tariff landscape confronting technology buyers and suppliers in 2025 is the product of overlapping policy decisions across successive United States administrations. Targeted measures introduced under Section 301 have raised duties on a range of Chinese imports in strategic sectors, including semiconductors, batteries, steel, aluminum, and selected clean energy technologies. These actions are explicitly framed as responses to unfair trade practices and as tools to reduce dependence on concentrated foreign supply in critical digital and industrial value chains.
More recently, broader tariff proposals and measures have added further uncertainty. A universal surcharge on imports, coupled with continued or revised duties on Chinese goods, has stoked concern among technology firms and investors that the cost of building and operating advanced digital infrastructure in the United States could rise significantly. Coverage of the AI infrastructure boom has already highlighted how new tariffs and trade frictions risk increasing the expense of data center construction and extending procurement timelines for generators, transformers, and other core components. In parallel, draft and proposed regulations that seek to restrict software and connected-vehicle technologies sourced from certain jurisdictions underscore how trade policy is now deeply intertwined with national security and data protection objectives.
For data centric security, the cumulative effect of these tariffs manifests in several ways. First, higher duties on semiconductors and related hardware can translate into increased capital costs for on-premises security appliances, storage systems, and specialized cryptographic modules. While hyperscale cloud providers can amortize such increases across global footprints, smaller providers and enterprises may face tougher trade-offs when refreshing infrastructure or expanding capacity. Second, projected increases in data center construction and energy costs driven partly by tariff-induced supply constraints can push organizations to prioritize security solutions that are software-defined, cloud-delivered, and more efficient in their use of compute and storage resources.
Third, tariffs are accelerating a strategic realignment of supply chains. Vendors of data centric security solutions and underlying hardware are actively diversifying their manufacturing and component sourcing toward North America, Europe, and trusted partners in Asia-Pacific to mitigate future trade shocks. This trend supports broader initiatives around “friendshoring” and regional resilience, but it also requires buyers to scrutinize their suppliers’ transparency on component provenance, firmware security, and lifecycle management. As supply chains fragment, the ability to attest to the integrity of hardware security modules, secure enclaves, and cryptographic accelerators becomes a differentiating factor in vendor selection.
For executive decision-makers, the implication is clear: trade policy must now be treated as a structural element of security strategy rather than as a macroeconomic backdrop. Scenario planning for the next three to five years should assess how alternative tariff regimes could affect the economics of on-premises versus cloud deployments, the feasibility of multi-region redundancy, and the availability of specialized skills and components. Organizations that weave these considerations into their data centric security roadmaps will be better positioned to sustain investment momentum, avoid lock-in to fragile supply chains, and preserve the flexibility to adapt as the geopolitical environment evolves.
Uncovering Strategic Insights from Component, Deployment, Organization Size, and Industry Segmentation in Data Centric Security Adoption
The structure of demand for data centric security is best understood through the lens of several interlocking segmentation dimensions, starting with the distinction between services and solutions. Solutions such as data encryption, data loss prevention, data masking, and database activity monitoring currently represent the core of most deployments, as organizations seek tangible controls they can integrate into applications, data platforms, and analytics environments. At the same time, services encompassing consulting and integration, together with ongoing support and maintenance, have become critical for helping enterprises rationalize overlapping tools, adapt architectures to hybrid and multi-cloud realities, and keep pace with evolving regulatory obligations.
Within the solutions landscape, adoption patterns reflect differing maturity levels across use cases. Encryption and data loss prevention are now well-established in sectors such as banking, financial services, insurance, and healthcare, where regulatory scrutiny and the high value of personal and financial data have normalized the use of strong cryptography, policy-driven access controls, and outbound content inspection. Data masking is gaining particular traction in organizations that rely heavily on analytics and software testing, because it enables teams to work with realistic datasets while reducing exposure of actual customer identifiers and sensitive attributes. Database activity monitoring, meanwhile, is rising in importance as attackers target backend repositories directly and as auditors demand greater transparency into who accessed which records and when.
Deployment mode constitutes a second key axis. Cloud-based data centric security has moved to the foreground as enterprises accelerate migrations to software-as-a-service and platform-as-a-service offerings and embrace cloud-native data warehouses and data lakes. Industry analysis of adjacent markets such as big data security shows that tokenization, encryption, and masking capabilities delivered as cloud software are now central to protecting data both at rest and in transit in distributed architectures. Nevertheless, on-premises deployments remain essential in organizations that handle state secrets, defense information, or highly sensitive financial and health records, and hybrid models have become common as firms balance control, latency, and regulatory requirements.
Organization size creates further differentiation. Large enterprises were early adopters of data centric security and continue to drive sophisticated, multi-domain programs that span structured and unstructured data, global user bases, and complex partner ecosystems. They often invest in bespoke integration projects, custom policies, and federation of controls across multiple business units. Smaller and medium-sized enterprises, however, are no longer on the sidelines. Today’s ransomware and extortion campaigns increasingly target mid-market organizations, and surveys indicate that smaller firms now represent a substantial share of breach victims, prompting them to adopt cloud-delivered encryption, simplified key management, and managed data protection services that avoid large upfront investments.
End-user industry segmentation adds another layer of nuance. Banking, financial services, and insurance continue to lead in adoption, driven by stringent supervisory expectations, well-defined data classifications, and a long history of investment in cryptography and transaction monitoring. Government agencies increasingly prioritize data centric security to protect citizen identities, critical infrastructure data, and sensitive intelligence, particularly as digital government initiatives expand. Healthcare organizations, under pressure from both regulators and relentless ransomware activity, are ramping up the use of encryption, tokenization, and masking to shield electronic health records and medical images. In manufacturing, the convergence of operational technology and IT, coupled with the targeting of industrial firms by criminal groups, has raised the stakes for protecting design files, process data, and telemetry. Retail and e-commerce players, whose business models depend on trust in digital customer experiences, are using data centric controls to secure payment data, behavioral analytics, and loyalty information.
Taken together, these segmentation patterns underline that there is no single archetypal buyer or deployment model. Instead, adoption reflects a spectrum of maturity, risk appetite, and regulatory exposure, with each segment gravitating toward a blend of services and solutions, deployment modes, and industry-specific controls that align with its unique threat landscape and operational realities.
This comprehensive research report categorizes the Data Centric Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Deployment Mode
- Organization Size
- End User Industry
Decoding Regional Dynamics in the Americas, Europe, Middle East and Africa, and Asia Pacific for Data Centric Security Strategies
Regional dynamics exert a powerful influence on how data centric security is prioritized, funded, and implemented. In the Americas, and particularly in the United States, organizations operate under intense pressure from both attackers and regulators. The United States consistently records some of the highest breach costs globally, reflecting the scale of digital operations, the value of intellectual property, and the rigor of legal and compliance frameworks. The region’s technology and financial sectors are at the forefront of adopting advanced encryption, tokenization, and AI-driven monitoring, encouraged by a dense ecosystem of cybersecurity vendors, hyperscale cloud providers, and specialized service firms. At the same time, the tariff environment and the explosion of AI data center projects have made infrastructure decisions more complex, reinforcing the importance of software-defined and cloud-native data protection strategies that can flex around shifting cost structures.
Across Europe, the Middle East, and Africa, regulatory drivers and threat profiles vary but converge on an elevated focus on data protection. In Europe, the General Data Protection Regulation and a growing body of sector-specific rules have made demonstrable control over personal data a foundational requirement for operating in many industries. This has encouraged adoption of strong encryption, privacy-enhancing technologies, and mature data governance programs that treat security and compliance as two sides of the same coin. In the Middle East and North Africa, rapid digital transformation and ambitious national visions have spurred significant increases in information security investment, with data privacy and cloud security among the fastest-growing areas of spend. Governments and large enterprises in the region are elevating data protection as a board-level priority, motivated by concerns over hack-and-leak operations, ransomware, and the reputational damage associated with high-profile breaches.
Asia-Pacific presents a different but equally dynamic picture. The region combines some of the world’s most advanced digital economies with large emerging markets that are moving rapidly to cloud and mobile-first models. Data localization requirements, sectoral privacy laws, and regional cybersecurity regulations are proliferating, prompting organizations to adopt standardized encryption, tokenization, and masking practices that can be applied consistently across jurisdictions. Studies of adjacent markets, such as data masking and data tokenization for cloud applications, highlight Asia-Pacific as a particularly fast-growing arena for solutions that enable secure analytics, testing, and customer experience personalization. This growth is underpinned by the expansion of e-commerce, digital banking, and super-app ecosystems that process vast quantities of personal and transactional data.
Across all three broad regions, one theme is constant: data centric security is no longer a niche capability but a foundational building block of digital trust. What differs is the mix of drivers-regulatory harmonization in Europe, rapid digital nation-building in the Middle East and many African markets, and accelerating cloud-native innovation in Asia-Pacific and the Americas. Executives crafting global strategies must therefore balance a common architectural vision with sensitivity to local laws, cultural expectations around privacy, and the maturity of regional vendor and services ecosystems.
This comprehensive research report examines key regions that drive the evolution of the Data Centric Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Evaluating Leading Data Centric Security Providers as They Converge Platforms, Embrace AI, and Expand Service Led Value Propositions
The competitive landscape for data centric security is characterized by a blend of established cybersecurity and enterprise software providers, cloud hyperscalers, and specialized innovators. Large, diversified security vendors and infrastructure providers have expanded their portfolios to include integrated suites spanning data discovery, classification, encryption, tokenization, masking, and access governance. By consolidating these functions on shared platforms, they appeal to organizations seeking to reduce the complexity of point solutions and to enforce consistent policies across databases, file systems, SaaS applications, and cloud services.
Cloud providers, meanwhile, are deepening their native data protection offerings, embedding key management, transparent encryption, tokenization, and data security posture management into their core platforms. They are also investing heavily in confidential computing, hardware-backed enclaves, and customer-controlled keys to address concerns about sovereignty and lawful access. For many enterprises, this creates an attractive path to rapidly improving data protection by leveraging capabilities already available in their cloud environments, though it also raises strategic questions about dependence on a single provider and the portability of controls across clouds.
Specialist vendors continue to play an outsized role in advancing the state of the art. Innovators have brought to market data masking and tokenization services delivered as software-as-a-service, enabling organizations to anonymize sensitive attributes across multi-cloud and hybrid estates with minimal integration friction. One prominent example is the emergence of masking and tokenization platforms built on confidential computing foundations, which are seeing uptake among Global 2000 firms that need to protect sensitive data while enabling agile analytics and development. In parallel, newer entrants are focusing on securing data used by AI models and autonomous AI agents, reflecting growing concern about prompt injection, data poisoning, and model exfiltration risks.
Service providers-consultancies, systems integrators, and managed security services firms-are increasingly central to how data centric security is implemented and operated. They help clients build comprehensive data inventories, design classification schemes, and integrate security tooling with data lakes, customer data platforms, and AI pipelines. Many now offer managed data protection services that combine technology deployment with continuous monitoring and policy tuning, targeted at organizations that lack in-house expertise or that prefer to focus internal resources on business-facing security initiatives.
Overall, the competitive environment is moving toward greater consolidation of capabilities into platforms, deeper integration with cloud ecosystems, and heightened emphasis on protecting data in AI-intensive use cases. For buyers, this means prioritizing vendors that demonstrate interoperability, transparent roadmaps for supporting new data environments, and a strong record of aligning product design with emerging regulatory and privacy expectations.
This comprehensive research report delivers an in-depth overview of the principal market players in the Data Centric Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Broadcom Inc.
- Check Point Software Technologies Ltd
- CyberArk Software Ltd.
- Digital Guardian, Inc.
- Forcepoint LLC
- IBM Corporation
- Informatica LLC
- McAfee LLC
- Okta, Inc.
- PKWARE, Inc.
- SentinelOne, Inc.
- Trend Micro Inc.
- Varonis Systems, Inc.
Translating Executive Insight into Actionable Priorities for Leaders Seeking to Operationalize Robust Data Centric Security Programs
For industry leaders, the strategic question is not whether to pursue data centric security, but how to sequence and operationalize it effectively. The first priority is to establish an authoritative understanding of where critical data resides, how it flows, and who can access it. This requires building or refining a unified data inventory and classification scheme that spans structured and unstructured repositories, cloud and on-premises systems, and third-party platforms. Once this foundation is in place, executives can align protection levels with data sensitivity, avoiding both over-engineering and under-protection.
The next imperative is to embed data centric controls directly into the architectures underpinning cloud migration and digital transformation programs. Rather than treating encryption, masking, tokenization, and data loss prevention as afterthoughts, organizations should define them as non-negotiable requirements for new applications, data lakes, and analytics initiatives. This includes adopting cloud-native key management and data protection services where appropriate, while ensuring that policies and keys remain under the organization’s governance and that controls are portable across cloud providers to reduce lock-in.
Given the growing role of AI in both attacks and defenses, leaders should prioritize investments in automation that can discover, classify, and protect data at scale. Recent evidence indicates that organizations using AI and automation extensively in security operations reduce breach impact and accelerate containment materially compared with those relying on manual processes. Executives should therefore integrate machine learning-based data discovery and anomaly detection into their data centric security programs, while simultaneously establishing clear guardrails for the use of sensitive data in model training and prompting.
In parallel, governance and culture must keep pace. Boards and senior leadership teams should explicitly recognize data centric security as a strategic enabler of digital trust, not merely as an operational cost. This means defining cross-functional ownership that brings together security, privacy, legal, data management, and business stakeholders, and aligning incentives so that product and analytics teams see robust data protection as a foundation for innovation rather than as a constraint. Regular exercises-such as simulations of data theft and extortion scenarios-can help executives understand where controls may be insufficient and where communication, regulatory reporting, or customer remediation plans require strengthening.
Finally, leaders must factor geopolitical and trade risks into their roadmaps. The evolving tariff environment and regulatory scrutiny of foreign-sourced hardware and software make it essential to scrutinize suppliers’ security practices, transparency, and geographic footprints. Procurement criteria should include not only technical capabilities but also resilience of supply, clarity around data residency and lawful access, and alignment with the organization’s risk tolerance. By approaching data centric security as an integrated program-combining technology modernization, governance, talent development, and external risk management-executives can build durable resilience and safeguard the trust on which digital business depends.
Explaining the Rigorous Mixed Methodology Behind This Data Centric Security Assessment to Support Confident Executive Decision Making
The insights synthesized in this executive summary rest on a rigorous mixed methodology designed to balance breadth of coverage with depth of understanding. At its core is a structured program of secondary research that draws on recent empirical studies of cyber incidents, data breach costs, ransomware trends, and information security investment patterns across major regions and industries. Key inputs include global and regional analyses of breach disruption, reports on ransomware and data theft targeting sectors such as healthcare, manufacturing, and government, and studies examining the impact of AI and automation on detection and response.
Complementing this secondary foundation is a detailed examination of technology and service offerings across the data centric security ecosystem. This encompasses solution categories such as encryption, tokenization, data masking, data loss prevention, database activity monitoring, and data security posture management, as well as the consulting, integration, and managed services that support them. Vendor strategies were assessed using publicly available information on product roadmaps, architectural patterns, and reference deployments, with particular attention paid to innovations in cloud-native delivery, confidential computing, and protection of data used in AI workloads.
The research also incorporates current regulatory and policy developments that materially influence data centric security decisions. These include privacy and data protection regulations in key jurisdictions, emerging guidance on AI governance, and trade and tariff measures affecting the cost and availability of critical hardware and software components. Where possible, cross-referencing across independent sources was used to validate interpretations and to distinguish short-lived headlines from structural trends that are likely to shape organizational strategies over the medium term.
Throughout the analysis, an executive decision-making lens has been applied. Rather than focusing on quantitative projections or detailed vendor rankings, the methodology emphasizes the synthesis of patterns and scenarios that matter most to boards, chief information security officers, chief data officers, and business unit leaders. The result is a holistic view that connects technological evolution, regulatory expectations, geopolitical dynamics, and organizational realities, offering readers a practical foundation for strategic planning without relying on speculative market estimations or forecasts.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Data Centric Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Data Centric Security Market, by Component
- Data Centric Security Market, by Deployment Mode
- Data Centric Security Market, by Organization Size
- Data Centric Security Market, by End User Industry
- Data Centric Security Market, by Region
- Data Centric Security Market, by Group
- Data Centric Security Market, by Country
- United States Data Centric Security Market
- China Data Centric Security Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 1113 ]
Synthesizing Strategic Themes Across Technology, Regulation, and Geopolitics to Clarify the Future of Data Centric Security
Data centric security has emerged as a unifying response to a confluence of forces: relentless escalation in cyber threats, intensifying regulatory demands, rapid cloud and AI adoption, and growing geopolitical complexity. Organizations can no longer depend on perimeter defenses or fragmented tooling to protect the information assets that underwrite their business models. Instead, they must place data-its value, sensitivity, and lifecycle-at the heart of security design, ensuring that controls travel with the data across applications, infrastructures, and jurisdictions.
The broader environment in 2025 adds both urgency and opportunity. Breach and ransomware trends underline that attackers are targeting data directly, often exploiting gaps in visibility across hybrid and multi-cloud environments. At the same time, advances in automation, analytics, and confidential computing are equipping defenders with more powerful tools to discover, classify, and protect information at scale. Regulatory and trade developments-from privacy statutes to tariffs on critical technologies-are reshaping the economic and legal context in which data centric security strategies must operate.
Against this backdrop, the organizations most likely to succeed will be those that treat data centric security as a strategic, cross-functional program rather than as a collection of tactical projects. They will invest in accurate data inventories and governance, embed encryption, masking, tokenization, and monitoring into the fabric of their digital platforms, and ensure that their architectures remain adaptable to shifting regulatory and geopolitical conditions. They will also cultivate cultures in which security, privacy, and innovation reinforce rather than undermine one another.
Ultimately, the destination is a state in which customers, partners, regulators, and employees can trust that sensitive data is handled with diligence, transparency, and resilience-even in the face of continued technological disruption and adversarial pressure. The analysis presented here is intended to support leaders on that journey, providing a structured view of the landscape and actionable guidance for shaping the next phase of their data centric security evolution.
Partner with Ketan Rohom, Associate Director, Sales & Marketing at 360iResearch, to Access the Full Data Centric Security Market Report
In an environment where sensitive data is under relentless assault and regulatory expectations continue to rise, delaying a comprehensive view of the data centric security landscape carries real strategic risk. Executive teams, boards, and security leaders benefit most when they can anchor their decisions in a single, cohesive body of analysis that connects technology choices, regulatory pressures, geopolitical developments, and competitive positioning in a way that is both independent and deeply informed by the reality of front-line practitioners.
To move from interest to impact, engage directly with Ketan Rohom, Associate Director of Sales and Marketing, to discuss how the full report can support your organization’s immediate and long-term priorities. Through this engagement, decision-makers can align the study’s segmentation, regional insights, and vendor landscape with their own transformation roadmap, whether the focus is rationalizing a fragmented security stack, preparing for audits, or de‑risking large-scale cloud and AI initiatives.
By securing licensed access to the complete report, your leadership team gains the ability to brief stakeholders with authoritative narratives, ground strategic planning in robust evidence, and benchmark internal initiatives against peers across industries and geographies. This is particularly valuable for organizations facing near-term investment or compliance milestones, such as negotiating major security contracts, refreshing data protection policies, or responding to board-level inquiries on cyber resilience.
You are encouraged to schedule a focused conversation with Ketan to explore purchasing options, delivery formats, and opportunities to complement the core report with tailored briefings or executive workshops. Taking this step transforms the analysis from a reference document into a practical instrument for steering your organization’s data centric security journey with confidence and clarity.

- How big is the Data Centric Security Market?
- What is the Data Centric Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




