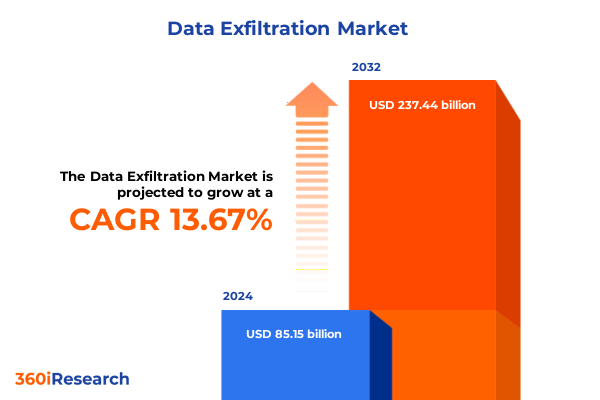
The Data Exfiltration Market size was estimated at USD 95.66 billion in 2025 and expected to reach USD 107.47 billion in 2026, at a CAGR of 13.86% to reach USD 237.44 billion by 2032.
Exploring the Evolving Threat Landscape of Data Exfiltration and Why It Demands Strategic Attention from Organizational Leadership
Data exfiltration continues to rank among the foremost cybersecurity threats confronting organizations in 2025. As attackers refine their tactics-leveraging compromised credentials, sophisticated malware, and living-off-the-land techniques-sensitive information is siphoned from corporate networks at unprecedented scale. This growing peril transcends industry verticals, striking financial services, healthcare, government agencies, and technology firms alike. Elevated by rapid cloud adoption and remote work models, the potential for unauthorized data transfers demands both strategic visibility and rigorous defense postures.
In the face of escalating breaches, executives are compelled to reevaluate legacy controls and embrace a proactive security frame. The imperative to detect anomalies in real time, limit exposure of critical assets, and integrate policy enforcement across endpoints and cloud boundaries underscores a pivotal inflection point. With regulators intensifying penalties and customers increasing scrutiny of data stewardship, leadership teams must recognize data exfiltration not as an IT challenge alone but as a core business risk requiring coordinated resource allocation and governance oversight.
Analyzing Transformative Shifts in Data Security Architectures and Tactics That Are Redefining How Organizations Prevent Exfiltration
Recent years have witnessed seismic shifts in how enterprises approach data security, catalyzed by emerging architectures and threat dynamics. Zero Trust frameworks have gained traction, eschewing perimeter-centric models in favor of continuous authentication and microsegmentation. By verifying every access request-regardless of network origin-organizations are reducing attack surfaces and limiting lateral movement. Concurrently, convergence of security tools into Extended Detection and Response platforms allows for unified telemetry analysis across endpoint, network, and cloud domains, streamlining incident response.
Artificial intelligence and machine learning are also pivotal, augmenting human analysts with behavioral modeling to discern subtle exfiltration indicators. These capabilities empower security teams to flag irregular data flows, unauthorized privilege escalations, and anomalous lateral hops before adversaries complete their objectives. Furthermore, next-generation cloud workload protection services are enforcing runtime policies to safeguard ephemeral assets, demonstrating a move toward adaptive, context-aware defenses. As these transformations take hold, they lay the groundwork for more resilient counterexfiltration postures.
Evaluating the Cumulative Impact of Recent United States Tariffs on Data Security Technology Supply Chains and Operational Costs
In 2025, the imposition of additional United States tariffs on imported security appliances and semiconductor components has underscored vulnerabilities within global procurement channels. Hardware manufacturers faced elevated input costs, translating into longer lead times and heightened pricing for next-generation security appliances. As organizations contended with these constraints, budget pressures prompted reassessments of deployment roadmaps and accelerated adoption of software-defined alternatives, including virtualized firewalls and cloud-native encryption services.
Beyond procurement, these tariff-induced dynamics sparked broader supply chain realignments. Vendors began diversifying component sources and expanding regional manufacturing footprints to mitigate duties and logistical bottlenecks. Such strategic shifts required security teams to adapt integration plans, validate interoperability of alternate hardware revisions, and recalibrate total cost models. By encouraging dialogue between procurement, legal, and security functions, organizations navigated the evolving trade landscape while sustaining progress toward robust exfiltration controls.
Uncovering Critical Insights from Solution Deployment Organization Size and Industry-Based Segmentation Trends in Data Exfiltration Defense
When examining prevention strategies across solution categories, cloud security emerges as the fastest-evolving domain, with firms integrating cloud access security brokers alongside cloud workload protection to supervise data flows in multi-cloud environments. Data loss prevention platforms have similarly expanded, offering distinct enforcement modules for endpoint, network, and cloud-native architectures. Encryption solutions have bifurcated into discrete approaches-database-centric controls, full disk encryption at rest, and granular file-level protections-enabling organizations to align security with asset criticality. Endpoint defenses continue to mature, blending antivirus with advanced anti-malware heuristics and endpoint detection and response analytics, while network security platforms now incorporate next-generation firewalls and intrusion prevention tuned to modern threat signatures.
Deployment preference reveals that cloud-based offerings are rapidly outpacing on-premises installations, though hybrid models retain a strategic place in tightly regulated sectors. Large enterprises gravitate toward integrated platforms that unify centralized policy management across geographic footprints, whereas small and medium enterprises often opt for managed services that reduce operational overhead. Across verticals, financial institutions emphasize compliance-driven segmentation and real-time transaction monitoring, government and defense bodies prioritize classified data enclaves and insider threat detection, healthcare providers focus on patient record privacy and HIPAA alignment, IT and telecom companies secure sprawling network infrastructures, and retail players concentrate on safeguarding point-of-sale systems and customer data.
This comprehensive research report categorizes the Data Exfiltration market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Solution
- Deployment Mode
- Organization Size
- Industry Vertical
Mapping Regional Dynamics in the Data Exfiltration Landscape Across the Americas Europe Middle East Africa and Asia Pacific Regions
Regional security postures reflect distinct regulatory, maturity, and threat actor landscapes. In the Americas, stringent data privacy statutes alongside sector-specific frameworks such as CMMC and HIPAA drive robust investments in multi-factor authentication, microsegmentation, and advanced monitoring. Latin American nations, while still ramping up legislative rigor, show increased appetite for managed detection and response services to shore up resource gaps.
Europe, the Middle East, and Africa present a tapestry of requirements under GDPR and evolving NIS2 directives, compelling a harmonized approach to cross-border data flow controls. Localized encryption mandates and breach notification timelines have spurred deployment of unified policy enforcement across cloud service providers. Conversely, Asia-Pacific exhibits a dualistic market: mature economies like Japan and Australia maintain comprehensive data protection regulations and high adoption of endpoint analytics, while emerging markets in Southeast Asia and India emphasize affordable cloud-first solutions and vendor partnerships to bolster cybersecurity resilience.
This comprehensive research report examines key regions that drive the evolution of the Data Exfiltration market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Leading Vendors Innovations and Competitive Strategies Driving the Data Exfiltration Prevention Industry Forward
A competitive blend of established security stalwarts and agile innovators shapes the data exfiltration prevention terrain. Major platform providers have fortified their portfolios through strategic acquisitions, integrating AI-driven analytics and unified policy engines to deliver end-to-end visibility. These incumbents leverage global support networks and extensive research operations to refine threat intelligence feeds and accelerate response playbooks. Meanwhile, specialist vendors-often born in the cloud era-challenge convention with purpose-built host-based sensors, microagent architectures, and SaaS-native policy controls designed for rapid deployment and minimal overhead.
This interplay between broad-spectrum suites and targeted solutions fosters continuous innovation. Incumbent players are embracing open architectures to interoperate with third-party telemetry sources, while start-ups explore decentralized encryption techniques and secure enclave microservices. The result is a dynamic ecosystem that empowers customers to tailor defenses-from holistic frameworks down to pinpointed controls-based on unique risk appetites and operational constraints.
This comprehensive research report delivers an in-depth overview of the principal market players in the Data Exfiltration market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Code42, Inc.
- Digital Guardian, Inc.
- Forcepoint LLC
- Microsoft Corporation
- NVIDIA Corporation
- Palo Alto Networks, Inc.
- Proofpoint, Inc.
- Trellix Holdings LLC
- Trend Micro Incorporated
Implementing Strategic Roadmaps and Best Practices to Strengthen Organizational Defenses Against Evolving Data Exfiltration Threats
Industry leaders should begin by embracing a consolidated security fabric that unites endpoint, network, and cloud policy enforcement under a common control plane. This approach reduces tool fragmentation and streamlines incident orchestration, enabling rapid containment of anomalous data transfers. Complementing this foundation, organizations should adopt continuous behavioral analytics powered by machine learning models trained to detect slight deviations in user and system interactions, thereby catching exfiltration attempts hidden within legitimate traffic.
Strategic investment in Zero Trust principles will ensure that every access request is evaluated dynamically, while microsegmentation isolates critical workloads to thwart lateral movement. To sustain these measures, executives must establish clear data governance policies and cultivate a culture where security hygiene-from privileged account management to encryption key rotation-is deeply ingrained. Finally, forging deeper partnerships with vendors and peer industry groups accelerates knowledge sharing, enabling proactive threat anticipation and collective resilience against emerging exfiltration vectors.
Detailing the Comprehensive Research Framework and Methodological Approach Underpinning the Data Exfiltration Market Analysis
The findings presented in this executive summary are underpinned by a rigorous research framework combining primary and secondary methods. In-depth interviews were conducted with senior security architects, CISOs, and procurement officers across diverse industries to capture firsthand perspectives on threat trends, solution efficacy, and budgeting priorities. These qualitative insights were corroborated with technical briefings from leading vendors and anonymized data from incident response engagements.
Secondary research encompassed an extensive review of policy documents, compliance regulations, vendor whitepapers, and peer-reviewed studies. Quantitative validation was achieved through analysis of anonymized telemetry data and aggregated incident volumes, ensuring that observed patterns corresponded with real-world breach case studies. To guarantee analytical rigor, all inputs underwent cross-verification by a multi-disciplinary panel of cybersecurity experts, and findings were stress-tested against hypothetical scenarios to affirm their resilience under evolving threat conditions.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Data Exfiltration market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Data Exfiltration Market, by Solution
- Data Exfiltration Market, by Deployment Mode
- Data Exfiltration Market, by Organization Size
- Data Exfiltration Market, by Industry Vertical
- Data Exfiltration Market, by Region
- Data Exfiltration Market, by Group
- Data Exfiltration Market, by Country
- United States Data Exfiltration Market
- China Data Exfiltration Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 1590 ]
Synthesizing Core Findings and Strategic Imperatives to Guide Decision Makers in Mitigating Data Exfiltration Risks
This executive summary synthesizes core insights into the escalating complexity of data exfiltration threats, the emergence of integrated prevention technologies, and the strategic implications of recent trade policy shifts. By dissecting segmentation and regional variances, it has illuminated how solution preferences, deployment models, and industry-specific drivers shape security priorities. The competitive landscape reveals a healthy tension between broad platform vendors and focused innovators, fostering continuous improvement in detection, encryption, and response capabilities.
As organizations navigate a risk environment defined by rapid digital transformation and sophisticated adversaries, the recommendations outlined here serve as a foundation for resilient, future-proof strategies. Executives empowered with these insights can champion a unified security vision, optimize resource allocation, and align technology initiatives with broader business objectives to effectively prevent data exfiltration and safeguard enterprise value.
Speak Directly with Associate Director of Sales and Marketing to Unlock Full Insights from the Comprehensive Report and Drive Strategic Advantage
To gain a tailored walkthrough of our comprehensive analysis and unlock exclusive strategic insights, reach out directly to Ketan Rohom, Associate Director of Sales & Marketing. By engaging with Ketan, you can secure prioritized access to the full market research report that dives deep into emerging data exfiltration vectors, evolving vendor landscapes, and actionable defense frameworks. This personalized consultation will enable your organization to refine procurement decisions, accelerate risk mitigation planning, and leverage competitive benchmarking data with confidence. Connect now to discuss customized licensing options and discover how this report can fortify your enterprise against advanced exfiltration threats and drive long-term security ROI.

- How big is the Data Exfiltration Market?
- What is the Data Exfiltration Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




