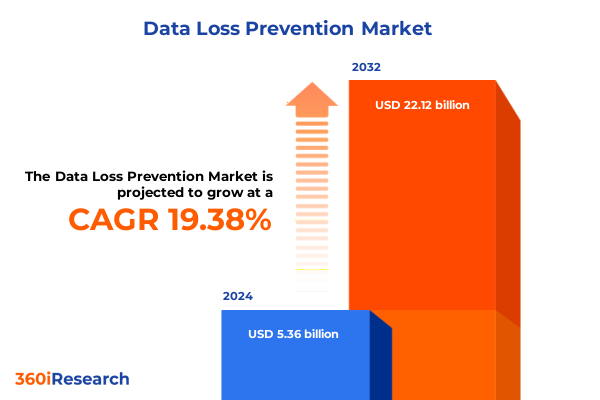
The Data Loss Prevention Market size was estimated at USD 6.39 billion in 2025 and expected to reach USD 7.58 billion in 2026, at a CAGR of 19.40% to reach USD 22.12 billion by 2032.
Charting the Crucial Imperative of Data Loss Prevention Strategies to Safeguard Corporate Assets Against Evolving Cyber Threat Landscapes
The digital era has ushered in unprecedented volumes of sensitive information across industries, making data integrity a cornerstone of corporate resilience. As enterprises navigate an increasingly complex threat environment, the potential for inadvertent or malicious data exfiltration has grown exponentially. No longer can organizations rely solely on traditional perimeter defenses; they must adopt a comprehensive approach to monitor, detect, and prevent unauthorized data movements.
Data loss prevention solutions have emerged as the linchpin of modern security architectures, offering visibility into data flows both within and beyond organizational boundaries. By combining content inspection, contextual analysis, and policy enforcement, these platforms empower stakeholders to maintain compliance with evolving regulations while preserving operational agility. The ensuing analysis delves into the critical trends shaping the data loss prevention domain, unpacks the implications of fiscal policies, and provides actionable insights to guide strategic decision making.
This executive summary synthesizes key findings across technological evolutions, market segmentation, regional dynamics, and competitive landscapes. It distills essential learnings to equip decision-makers with the foresight necessary to mitigate data exfiltration risks, optimize security investments, and foster a culture of proactive data stewardship across diverse operational contexts.
In light of accelerating digital transformation initiatives and a shift to hybrid cloud environments, understanding the interplay between emerging threats and protective strategies has never been more vital. Therefore, this executive summary sets the stage for a deeper exploration of transformative shifts in threat vectors, regulatory catalysts, and the evolving toolkit of prevention mechanisms available to today’s enterprises.
Illuminating the Transformative Shifts Redefining the Data Loss Prevention Landscape Across Technology Evolution and Regulatory Pressures
Organizations today are witnessing a paradigm shift in how data is created, consumed, and protected. The migration towards cloud-native applications and the ubiquity of remote workforces have transformed the perimeter, rendering legacy security controls insufficient. In response, data loss prevention platforms have evolved to integrate seamlessly with cloud access security brokers (CASBs) and secure web gateways. This convergence ensures that content inspection and policy enforcement persist regardless of whether data resides on-premises, in private clouds, or within public cloud instances.
Simultaneously, advancements in machine learning and behavioral analytics have empowered these systems to distinguish between legitimate user actions and anomalous exfiltration attempts. Predictive models now analyze file attributes, user roles, and contextual metadata to preemptively flag risks, reducing reliance on static rule sets. As institutions contend with exponential data volumes, the ability to scale detection capabilities without overwhelming security teams has become a decisive differentiator among solution providers.
Regulatory landscapes are also driving innovation at an accelerated pace. Heightened scrutiny under federal statutes and evolving state privacy laws mandate granular control over personally identifiable information. This has spurred the adoption of real-time policy orchestration and automated remediation workflows to ensure compliance without impeding business continuity. Moreover, collaborative initiatives between industry consortiums and standards bodies have begun to harmonize data protection frameworks, further underscoring the need for flexible, extensible platforms.
Finally, the integration of zero trust principles with data loss prevention architectures has emerged as a transformative shift. By enforcing least-privilege access and continuously validating user and device trustworthiness, organizations can create multi-layered defense ecosystems. This holistic approach aligns prevention tools with broader security strategies, enabling a resilient posture against increasingly sophisticated threat actors.
Analyzing the Cumulative Impact of 2025 United States Tariffs on Data Loss Prevention Infrastructure and Operational Costs
In 2025, the imposition of tariffs on imported hardware components and software licenses by the United States government has generated ripple effects across the data loss prevention ecosystem. Devices such as encryption appliances and network sensors have experienced cost escalations, prompting organizations to reevaluate their capital expenditure allocations. As a result, some enterprises have deferred hardware refresh cycles, shifting their reliance towards virtualized or cloud-based alternatives to mitigate upfront investments.
Concurrently, tariff-driven constraints on semiconductor imports have indirectly affected the availability of specialized chips used in high-throughput data inspection modules. Vendors have responded by optimizing software algorithms for lower-specification hardware, thereby balancing performance with cost containment. These developments have underscored the strategic importance of deployment agility, empowering security teams to select configurations that align with both regulatory objectives and budgetary realities.
The tariff landscape has also influenced contractual negotiations between service providers and enterprise clients. Cloud-native DLP solutions, which depend on underlying infrastructure markets, are increasingly structured to include pass-through cost adjustments and flexible term lengths. This shift elevates the importance of transparent pricing models as organizations analyze total cost of ownership over multi-year horizons. Simultaneously, sellers are enhancing modular licensing to accommodate incremental capacity upgrades without punitive surcharges.
Ultimately, the cumulative impact of 2025 tariffs has accelerated the migration toward subscription-based, software-centric approaches. By decoupling protection capabilities from tariff-exposed hardware and leveraging global delivery networks, enterprises can maintain consistent policy enforcement while insulating themselves from volatile import costs. This dynamic has reinforced the broader industry trend toward hybrid deployments and subscription economics.
Unveiling Critical Segmentation Insights Across Components Deployment Models Organizational Scales and Industry Verticals Driving DLP Adoption
Component analysis reveals that software-only solutions continue to gain traction due to their rapid deployment cycles and lower capital intensity, while service-oriented offerings appeal to organizations seeking managed oversight and domain expertise. The services segment, encompassing continual monitoring, policy creation, and incident response consultancy, addresses the complexity of integrating DLP into extended enterprise architectures. Conversely, software-centric products emphasize extensibility and ecosystem integration, enabling custom workflows and API-driven automation within existing technology stacks.
When examining deployment models, organizations are recognizing the value of cloud-hosted DLP platforms for their on-demand scalability and reduced infrastructure overhead. Hybrid architectures, combining on-premises sensors with cloud policy engines, bridge the gap between legacy investments and new operational paradigms. Meanwhile, traditional on-premise implementations persist in highly regulated environments that require full data sovereignty and offline processing capabilities, illustrating the enduring importance of flexible deployment options.
Organizational size further nuances adoption patterns. Large enterprises often centralize DLP governance within dedicated security operations centers, leveraging extensive customization and integration with identity management systems. In contrast, small and medium-sized enterprises prioritize turnkey solutions that minimize administrative complexity and deliver rapid time-to-value. This divergence highlights the need for vendor roadmaps that accommodate both deep configurability and simplified deployment experiences.
Industry verticals demonstrate differentiated needs based on data sensitivity and regulatory regimes. Financial institutions, spanning banking, insurance, and securities markets, demand robust encryption controls and transaction-level inspection. Government clients at both federal and state tiers focus on classified data segregation and compliance with stringent mandates. Healthcare organizations, including hospitals, clinics, and pharmaceutical entities, emphasize patient privacy and intellectual property protection, whereas IT service providers and telecom operators balance data security with service availability. Retail merchants, whether brick-and-mortar or purely online, align loss prevention measures with customer loyalty programs, payment card industry standards, and supply chain visibility.
This comprehensive research report categorizes the Data Loss Prevention market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Deployment Model
- Organization Size
- Industry Vertical
Exploring Key Regional Insights That Highlight Divergent Adoption Patterns and Challenges in Americas Europe Middle East Africa and Asia Pacific Markets
In the Americas region, a blend of mature enterprise deployments and progressive regulatory frameworks has fueled robust DLP adoption. North American organizations benefit from established cybersecurity infrastructures, supplemented by emerging state privacy statutes that mirror or exceed federal requirements. This convergence of compliance pressure and digital acceleration has positioned the Americas as a bellwether for cloud-centric prevention strategies and advanced threat analytics.
Across Europe, the Middle East, and Africa, heterogeneous regulatory landscapes and varying levels of digital maturity have shaped DLP priorities. European Union member states strive to harmonize directives under the GDPR umbrella, driving demand for centralized policy management and cross-border data flow controls. Meanwhile, Middle Eastern markets are investing in national cybersecurity frameworks that include DLP as a core element of critical infrastructure protection. In Africa, a growing emphasis on financial inclusion is accompanied by investments in secure digital services, catalyzing adoption in banking and telecom sectors.
Asia-Pacific markets display a spectrum of digital transformation trajectories, with advanced economies embracing AI-powered prevention platforms as part of their Industry 4.0 initiatives. Regional cloud providers are embedding DLP modules into platform portfolios to meet local data residency requirements, while multinational corporations leverage unified policies to maintain consistency across dispersed operations. Rapid growth in Southeast Asia and Oceania underscores the region’s increasing appetite for integrated risk management solutions that accommodate both global standards and localized compliance mandates.
These regional dynamics highlight the importance of tailoring data loss prevention strategies to address jurisdictional nuances and technology ecosystems. Enterprises that align policy frameworks with regional requirements and partner ecosystems can realize both compliance and efficiency gains.
This comprehensive research report examines key regions that drive the evolution of the Data Loss Prevention market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Distilling Key Company Insights Revealing Strategic Priorities and Competitive Dynamics Among Leading Data Loss Prevention Providers
Leading providers in the data loss prevention arena exhibit diverse strategic priorities that reflect varying go-to-market philosophies and technology betas. Some vendors are deepening partnerships with hyperscale cloud platforms to embed prevention controls directly into infrastructure services, thereby shortening deployment cycles and reducing integration friction. Others are expanding into adjacent security domains-such as secure access service edge (SASE) or cloud access security brokers-to offer unified suites that span network, endpoint, and data protection.
Investment in artificial intelligence continues to be a focal point, with companies enhancing behavioral analytics to detect insider threats and sophisticated exfiltration attempts. This emphasis on autonomous detection is complemented by user-centric features, including adaptive risk scoring and contextualized alerts that prioritize high-impact incidents. Vendors that balance automation with human-in-the-loop workflows are positioning themselves to address enterprise demands for both efficiency and oversight.
Mergers and acquisitions remain a prominent theme, as larger incumbents seek to augment their portfolios with niche capabilities-ranging from blockchain-enabled data traceability to homomorphic encryption engines. Meanwhile, emerging startups target specific use cases, such as secure orchestration of data sharing in collaborative research environments or precision monitoring of regulated communication channels. This dynamic competitive landscape underscores the need for enterprises to evaluate vendor roadmaps against both current requirements and future innovation pathways.
Ultimately, the success of these providers will hinge on their ability to offer flexible licensing models, transparent pricing, and responsive professional services. Firms that can demonstrate rapid ROI and seamless integration with existing security fabrics are likely to capture a growing share of the market.
This comprehensive research report delivers an in-depth overview of the principal market players in the Data Loss Prevention market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems Inc.
- Code42 Inc.
- CoSoSys Ltd.
- Forcepoint LLC
- Fortra LLC
- GTB Technologies LLC
- International Business Machines Corporation
- McAfee LLC
- Microsoft Corporation
- Netskope Inc.
- Palo Alto Networks Inc.
- Proofpoint Inc.
- Safetica s.r.o.
- Spirion LLC
- Teramind Inc.
- Trellix Inc.
- Trend Micro Incorporated
- Zscaler Inc.
Formulating Actionable Recommendations Empowering Industry Leaders to Strengthen Data Loss Prevention Posture Through Strategic Initiatives
Industry leaders should prioritize the adoption of integrated prevention ecosystems that unify network, endpoint, and cloud controls under a centralized policy framework. This approach ensures consistent enforcement regardless of user location or data repository, reducing operational complexity and minimizing blind spots. Furthermore, aligning data loss prevention architectures with zero trust principles fosters continuous verification and minimizes trust assumptions across all access attempts.
In tandem, organizations must invest in advanced analytics capabilities that leverage both supervised and unsupervised machine learning to distinguish benign user behaviors from malicious patterns. By refining detection algorithms and incorporating threat intelligence feeds, security teams can reduce false positives and focus resources on critical incidents. It is equally important to establish cross-functional incident response workflows that integrate prevention tools with security orchestration platforms, enabling rapid containment and remediation.
Given the evolving regulatory landscape, industry leaders should also conduct periodic policy reviews to ensure alignment with new privacy statutes and data residency mandates. Automated compliance reporting modules can streamline audit processes and support real-time visibility into policy adherence. Additionally, organizations should foster a culture of data stewardship through ongoing user education programs, reinforcing the shared responsibility model for safeguarding sensitive information.
Finally, enterprises may consider strategic partnerships with specialized managed security service providers or consultancy firms to augment internal capabilities. These collaborations can accelerate implementation timelines, enhance threat hunting proficiency, and provide access to domain experts who can tailor prevention strategies to specific operational contexts.
Outlining a Robust Research Methodology Integrating Primary Interviews Secondary Analysis and Quantitative Techniques to Ensure Data Integrity
The research methodology underpinning this analysis integrates both primary and secondary approaches to ensure comprehensive coverage and data integrity. Primary research included in-depth interviews with over two dozen senior security leaders across industries, capturing firsthand perspectives on deployment challenges, technology preferences, and evolving threat landscapes. These conversations were complemented by structured surveys targeting IT administrators and compliance officers to quantify adoption drivers and inhibitor metrics.
Secondary research efforts encompassed a rigorous review of peer-reviewed journals, white papers from leading security associations, regulatory filings, and technology briefs published by industry consortia. Vendor literature and publicly available financial disclosures provided additional insights into product roadmaps, partnership strategies, and R&D investments. This multi-source data collection enabled triangulation of key findings and validation of emerging trends.
Quantitative analysis techniques were employed to assess the relative prevalence of deployment models, component preferences, and industry vertical usage patterns. Advanced statistical methods, including cluster analysis and regression modeling, were used to identify correlations between organizational attributes and prevention effectiveness. Meanwhile, qualitative thematic analysis distilled common pain points, success factors, and strategic imperatives from interview transcripts.
Rigorous data cleansing and validation protocols were applied throughout the research lifecycle. Findings were peer-reviewed by a cross-functional team of analysts and security practitioners to mitigate bias and ensure practical relevance. This robust methodology provides a solid foundation for the insights and recommendations presented in this executive summary.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Data Loss Prevention market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Data Loss Prevention Market, by Component
- Data Loss Prevention Market, by Deployment Model
- Data Loss Prevention Market, by Organization Size
- Data Loss Prevention Market, by Industry Vertical
- Data Loss Prevention Market, by Region
- Data Loss Prevention Market, by Group
- Data Loss Prevention Market, by Country
- United States Data Loss Prevention Market
- China Data Loss Prevention Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 1590 ]
Summarizing Key Findings and Emphasizing the Strategic Imperative of Data Loss Prevention in Evolving Cybersecurity Ecosystems
This executive summary underscores the critical importance of data loss prevention as a foundational element of contemporary cybersecurity strategies. The confluence of technology advancements, regulatory pressures, and evolving threat landscapes has elevated the need for dynamic, scalable solutions that provide both visibility and control across diverse digital ecosystems. By examining transformative shifts, tariff impacts, segmentation patterns, regional nuances, and vendor strategies, organizations can identify optimal pathways to fortify their data protection posture.
Key insights reveal that flexibility in deployment, integration of AI-driven analytics, and alignment with zero trust frameworks are central to achieving comprehensive coverage while maintaining operational agility. Moreover, tariff-driven cost considerations have accelerated the transition toward subscription-based, software-centric models that decouple protection capabilities from hardware constraints. Segmentation analysis highlights the varied requirements across components, deployment models, organizational scales, and industry verticals, emphasizing the necessity of tailored strategies.
In conclusion, the synthesis of regional and competitive intelligence provides a roadmap for enterprises to navigate the complexities of modern data ecosystems. By leveraging the actionable recommendations and detailed research methodology outlined herein, decision-makers can implement data loss prevention measures that not only mitigate risk but also support strategic growth objectives in an increasingly interconnected world.
Unlock Comprehensive Insights and Accelerate Your Data Loss Prevention Strategy by Engaging with Ketan Rohom for Tailored Research Support
Engaging with Ketan Rohom, Associate Director of Sales & Marketing whose expertise bridges technical rigor and market-driven insights, offers organizations a direct pathway to leverage this comprehensive research for strategic advantage. By partnering with Ketan, decision-makers can arrange personalized briefings that align the detailed findings of the report with their unique technology roadmaps, risk tolerance profiles, and compliance requirements. This engagement is designed to translate high-level market intelligence into pragmatic deployment plans that maximize protection against data exfiltration and regulatory exposure.
Whether the objective is to refine cloud security strategies, assess the impact of evolving tariff regimes on procurement strategies, or benchmark internal operations against industry best practices, Ketan Rohom provides tailored consultation to ensure each stakeholder derives maximum value from the data loss prevention analysis. Prospective clients are encouraged to initiate a conversation to explore bespoke research add-ons, priority deep-dives, or executive workshops that facilitate cross-functional alignment and accelerate secure adoption. Reach out to Ketan to unlock the full potential of these insights and drive your next phase of data protection initiatives.

- How big is the Data Loss Prevention Market?
- What is the Data Loss Prevention Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




