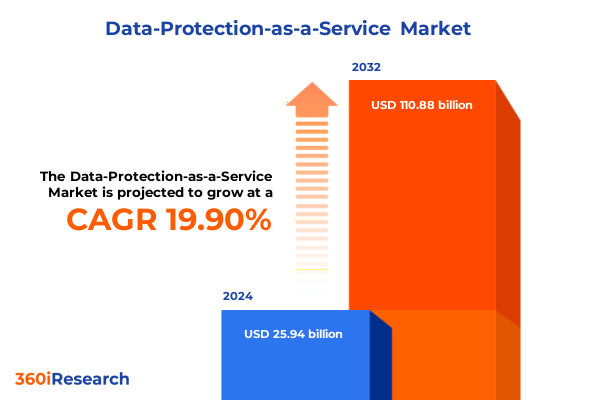
The Data-Protection-as-a-Service Market size was estimated at USD 30.87 billion in 2025 and expected to reach USD 36.80 billion in 2026, at a CAGR of 20.03% to reach USD 110.88 billion by 2032.
Enterprises Confronting Escalating Data Threats Turn to Data-Protection-as-a-Service as a Core Pillar of Strategic Resilience and Growth
Enterprises face an unprecedented confluence of challenges as digital transformation accelerates across industries. The proliferation of cloud infrastructures, hybrid environments, and remote work models has dramatically expanded the attack surface for malicious actors. Simultaneously, evolving regulatory mandates and heightened compliance requirements demand robust data protection strategies that can adapt in real time. In this context, Data-Protection-as-a-Service has emerged as a critical framework for organizations seeking to safeguard sensitive information while driving scalability and operational efficiency.
By decoupling data protection from rigid on-premises architectures, this service model enables dynamic alignment with fluctuating workloads and threat landscapes. Enterprises can now seamlessly extend backup, encryption, and recovery capabilities across cloud, on-premises, and edge environments without the capital expenditure burdens traditionally associated with infrastructure deployments. Moreover, the subscription-based structure facilitates predictable cost management, enhancing budgetary alignment and reducing total cost of ownership. As digital assets continue to proliferate in volume and complexity, Data-Protection-as-a-Service stands out as the strategic imperative for organizations determined to protect, comply, and thrive.
Emerging Technologies and Regulatory Dynamics Are Catalyzing a Paradigm Shift in Data Protection Services Landscape
The data protection landscape is undergoing profound shifts driven by technological innovation and intensifying threat vectors. Artificial intelligence and automation have fueled an unprecedented surge in malicious activity, with global automated scanning rising by 16.7 percent year-over-year to reach approximately 36,000 scans per second. Adversaries exploit AI to craft highly targeted phishing campaigns and accelerate credential-based attacks, forcing organizations to embrace advanced defense mechanisms in response.
Simultaneously, ransomware has evolved into a commoditized offering, with Ransomware-as-a-Service operations lowering barriers for threat actors and catalyzing a 500 percent increase in logs from compromised systems, resulting in more than 1.7 billion stolen credentials circulating on the dark web. As affiliates collaborate with advanced groups, organizations face both encryption and extortion threats, necessitating integrated backup and recovery solutions that can counter double extortion tactics and dynamic extortionware demands.
In parallel, regulatory momentum and post-quantum cryptography discussions are reshaping compliance landscapes. Major events spotlight the imperative of zero trust, with over 81 percent of organizations adopting zero-trust architectures to fortify perimeters and mitigate lateral movement. As enterprises integrate real-time threat intelligence and AI-driven anomaly detection, the service model continues to transform into a resilient, policy-driven ecosystem capable of responding to the most sophisticated attacks.
Escalating U.S. Tariff Policies in 2025 Have Cascading Effects on Data Protection Service Economics and Infrastructure Strategies
The cumulative impact of escalating U.S. tariffs in 2025 has reverberated through the data protection ecosystem, notably affecting hardware-dependent service delivery models. Major hyperscale and cloud providers are encountering a substantial increase in hardware costs as import duties on servers, storage arrays, and networking components surge by up to 25 percent. This has placed intense pressure on capital expenditures, compelling organizations to evaluate cost-recovery strategies or absorb higher expenses in cloud and colocation contracts.
Moreover, supply chain disruptions have intensified lead-time variability and introduced delays of 20 to 30 percent in infrastructure deployments, threatening project timelines and service level agreements. In response, many providers are diversifying sourcing into regions such as Vietnam, Mexico, and Taiwan to circumvent tariff liabilities, albeit at the cost of onboarding and quality assurance overheads.
In the healthcare sector, elevated import duties on data-center equipment have prompted institutions to postpone on-premises upgrades and pivot toward cloud-native solutions to mitigate tariff-induced budget constraints. This transition underscores a broader shift toward software-defined architectures and service-based consumption models that can adapt to dynamic trade policies while preserving data protection objectives.
Diverse Service Solution Size Security and Vertical Segmentation Sheds Light on Tailored Data Protection-as-a-Service Adoption Drivers
Service segmentation underscores a clear trajectory toward scalable and integrated platforms as organizations increasingly demand comprehensive capabilities spanning Backup as a Service, Disaster Recovery as a Service, and Storage as a Service alongside advanced Email/Data Encryption offerings. Cloud-native approaches are gaining a foothold as businesses seek elastic protection models that can dynamically adapt to shifting workloads and compliance imperatives, bolstered by an IDC report projecting 50 percent cloud-native backup adoption by 2025.
When examining solution offerings, enterprises emphasize unified frameworks that integrate Data Loss Prevention, Identity and Access Management, and Unified Threat Management to create cohesive security postures. The growing preference for identity-centric controls and real-time analytics reflects the imperative to preemptively identify anomalies and enforce policy-based safeguards across hybrid estates.
Analysis by Expert Insights reveals that large enterprises dominate the adoption landscape, leveraging their scale to drive hybrid strategies, while small and medium enterprises increasingly embrace managed services to offset limited IT resources. Furthermore, heightened concern over cybersecurity threats, data breaches, and sophisticated malware has elevated demand for advanced endpoint protection and immutable storage solutions.
Industry vertical dynamics remain critical, with Banking, Financial Services, and Insurance continuing to prioritize robust data resilience frameworks given stringent regulatory mandates, while sectors such as Healthcare and Government & Defense demand rigorous encryption and recovery protocols to safeguard mission-critical information.
This comprehensive research report categorizes the Data-Protection-as-a-Service market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Services
- Solution Offerings
- Organization Size
- Security Concerns
- Industry Vertical
Distinct Regional Dynamics Across the Americas EMEA and Asia-Pacific Are Shaping the Trajectory of Data Protection Services Adoption
Regional dynamics reveal distinct drivers that shape Data-Protection-as-a-Service trajectories across geographies. In the Americas, enterprises capitalize on mature cloud ecosystems and robust digital infrastructure to integrate comprehensive backup, encryption, and disaster recovery services, fueling a high penetration of advanced service offerings that address an evolving threat landscape.
Across Europe, the Middle East, and Africa, stringent data sovereignty regulations and the EU-US Data Privacy Framework elevate the importance of localized deployments and privacy-enhancing technologies. Organizations in this region navigate a complex regulatory matrix, balancing cross-border data flows with compliance requirements to ensure resilient data protection architectures.
In Asia-Pacific, rapid digitalization and accelerated public sector modernization drive significant investments in scalable protection services. Countries such as Singapore, Australia, and Japan are leading the charge, integrating AI-driven anomaly detection and multi-cloud backup strategies to mitigate rising cyber risks. A PeerSpot ranking indicates that North America holds approximately 45 percent market mind share, with Europe at 25 percent and Asia-Pacific at 18 percent, highlighting the growing regional equilibrium in service adoption.
This comprehensive research report examines key regions that drive the evolution of the Data-Protection-as-a-Service market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Key Industry Players Are Advancing Data Protection Offerings Through Strategic Partnerships Technological Innovation and Ecosystem Expansion
Leading vendors continue to innovate across the data protection spectrum, forging partnerships and enhancing platforms to meet the demands of a complex ecosystem. Rubrik has distinguished itself with its zero-trust design and AI-driven cyber recovery capabilities, recognized by peer reviews for rapid anomaly detection and prioritized identity recovery processes. Meanwhile, Commvault’s transition to a subscription model and strategic acquisitions has propelled significant revenue growth, affirming its strength in enterprise-scale hybrid deployments.
Veeam remains a top choice for its comprehensive ransomware defense, leveraging immutable storage and proactive IOC detection across hybrid environments. Gartner notes that Veeam’s platform supports a wide array of workloads, combining ease of management with robust threat-scanning functionality. Cohesity’s integration with Veritas Data Protection has created a unified portfolio that encompasses physical, virtual, and cloud environments, bolstering AI-powered anomaly detection and rapid orchestrated recovery for large-scale enterprise customers. Zerto’s continuous data protection capabilities deliver sub-minute recovery objectives, driven by its journal-based architecture and multi-cloud orchestration features that cater to mission-critical applications across industries.
This comprehensive research report delivers an in-depth overview of the principal market players in the Data-Protection-as-a-Service market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Acronis International GmbH
- Amazon Web Services, Inc.
- Arcserve, LLC
- Asigra Inc.
- Cisco Systems, Inc.
- Clarip Inc.
- Code42 Software, Inc.
- Cognizant Technology Solutions Corporation
- Commvault Systems, Inc.
- Dell Inc.
- Druva Inc.
- Hewlett Packard Enterprise Development LP
- Hitachi Vantara Corporation
- HYCU, Inc.
- Imperva, Inc.
- Infrascale Inc.
- International Business Machines Corporation
- Kyndryl Holdings, Inc.
- McAfee, LLC
- Microsoft Corporation
- NetApp, Inc.
- NxtGen Datacenter & Cloud Technologies Private Limited
- Open Text Corporation
- Oracle Corporation
- Palo Alto Networks, Inc.
- Privaon Oy
- Protegrity Corporation by Xcelera Inc.
- Quantum Corporation
- Quest Software Inc.
- SentinelOne, Inc.
- T-Systems International GmbH
- Veritas Storage (Ireland) Limited
- VMware, Inc.
Strategic Imperatives for Leaders Emphasize Integrated Cloud Security Proactive Policy Engagement and Adaptive Service Models to Stay Ahead
Industry leaders must adopt a multifaceted strategy to remain competitive and resilient. First, integrating zero-trust architectures with AI-powered threat analytics will fortify defenses against evolving attack vectors, a practice embraced by over 81 percent of organizations according to Zscaler research. By embedding real-time anomaly detection and policy-based controls within backup and recovery platforms, enterprises can reduce dwell time and limit exposure to ransomware and extortionware.
Second, diversifying hardware sourcing and forging strategic alliances with domestic manufacturers will mitigate tariff-related supply chain risks. Analysis indicates that migrating key infrastructure components to alternative regions such as Southeast Asia and Mexico can avert extended lead times and cost escalations triggered by U.S. import duties. Simultaneously, investing in lifecycle extension programs for existing assets through firmware upgrades and preventive maintenance will optimize capital utilization.
Finally, cultivating a culture of continuous compliance through privacy-enhancing technologies and post-quantum encryption readiness will ensure alignment with geopolitical and regulatory shifts. By fostering cross-functional collaboration between security, IT operations, and legal teams, organizations can develop cohesive policies that balance data protection, privacy, and business continuity imperatives.
Robust Research Methodology Integrates Multi-Source Data Collection Expert Validation and Rigorous Triangulation to Ensure Comprehensive Market Insights
This research applies a structured methodology combining secondary and primary data sources to deliver robust market insights. Secondary research encompassed a comprehensive review of industry reports, regulatory frameworks, and company disclosures to establish foundational context. Key documents included vendor whitepapers, standardization bodies’ publications, and cybersecurity threat assessments.
Primary research incorporated in-depth interviews with senior stakeholders across cloud service providers, enterprises, and channel partners. These discussions validated quantitative findings and enriched understanding of deployment challenges, service preferences, and emerging use cases. Data triangulation techniques ensured consistency and accuracy by cross-referencing interview inputs with publicly available information.
Subsequently, the study employed top-down and bottom-up analytical models to delineate segmentation trends, identifying critical drivers across service types, solution offerings, organization sizes, security concerns, industry verticals, and regions. A rigorous validation process further refined insights through iterative feedback loops with domain experts, ensuring that conclusions reflect the latest market dynamics.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Data-Protection-as-a-Service market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Data-Protection-as-a-Service Market, by Services
- Data-Protection-as-a-Service Market, by Solution Offerings
- Data-Protection-as-a-Service Market, by Organization Size
- Data-Protection-as-a-Service Market, by Security Concerns
- Data-Protection-as-a-Service Market, by Industry Vertical
- Data-Protection-as-a-Service Market, by Region
- Data-Protection-as-a-Service Market, by Group
- Data-Protection-as-a-Service Market, by Country
- United States Data-Protection-as-a-Service Market
- China Data-Protection-as-a-Service Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 954 ]
Synthesizing Insights Highlights the Vital Role of Data-Protection-as-a-Service in Fortifying Enterprise Security Posture Amid Evolving Threats
The insights presented underscore the strategic prominence of Data-Protection-as-a-Service as enterprises confront a rapidly evolving threat landscape and complex regulatory environment. As AI and automation intensify cyber risks, and trade policies introduce economic uncertainties, the demand for agile, scalable, and resilient protection services has never been greater. Leading providers continue to differentiate through technological innovation, ecosystem partnerships, and a commitment to seamless multi-cloud integration.
Enterprises that embrace zero-trust frameworks, diversify supply chains, and invest in post-quantum ready encryption will position themselves for sustained resilience. By aligning data protection strategies with broader digital transformation initiatives, organizations can transform security from a cost center into a competitive advantage. Ultimately, the convergence of advanced analytics, policy-driven automation, and service-based consumption models will define the next chapter of secure, compliant, and efficient data management.
Connect with Ketan Rohom to Unlock Comprehensive Data-Protection-as-a-Service Market Research and Drive Strategic Decision-Making
Elevate your strategic planning by securing the comprehensive Data-Protection-as-a-Service market research report. Reach out to Ketan Rohom, Associate Director of Sales & Marketing, to gain exclusive access to in-depth analysis, actionable insights, and tailored intelligence that empower your organization to navigate evolving digital threats with confidence and precision. Contact today to unlock the data-driven guidance needed to drive resilient growth and maintain a competitive edge in a rapidly transforming landscape.

- How big is the Data-Protection-as-a-Service Market?
- What is the Data-Protection-as-a-Service Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




