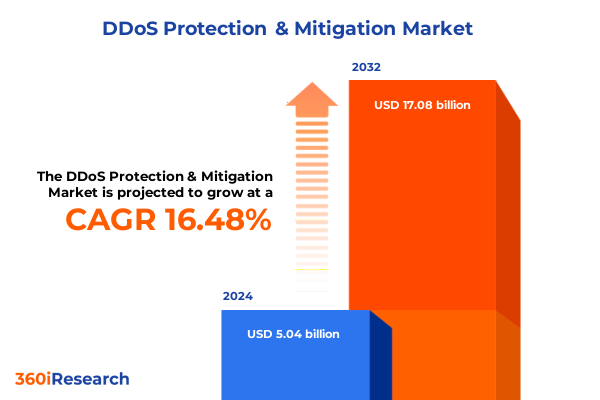
The DDoS Protection & Mitigation Market size was estimated at USD 4.69 billion in 2025 and expected to reach USD 5.29 billion in 2026, at a CAGR of 13.23% to reach USD 11.21 billion by 2032.
Navigating the Complexities of Modern DDoS Threats to Establish a Strong Foundation for Proactive Protection and Organizational Resilience
The digital ecosystem that drives today’s enterprises faces an ever-escalating threat from distributed denial of service attacks that can disrupt operations, erode customer trust, and inflict substantial financial and reputational damage. As organizations expand their footprint across cloud platforms, edge networks, and remote workforce environments, the vectors available to malicious actors have multiplied, demanding a comprehensive reframing of defensive strategies. In this context, an executive summary must not only outline prevailing risk scenarios but also illuminate the technological and organizational imperatives required to stay one step ahead of adversaries.
Against this backdrop, stakeholders ranging from boardroom executives to security operations teams are pressing for clarity on the mechanisms, investments, and processes that underpin effective DDoS protection and mitigation. This overview lays out critical developments in attack landscapes, regulatory considerations such as evolving tariff regimes, segmentation drivers, regional nuances, leading vendor capabilities, and actionable pathways designed to strengthen resilience. By distilling these complex themes into structured insights, this document aims to set the stage for informed decision-making on both tactical implementations and strategic roadmaps tailored to safeguard the continuity of digital services.
Embracing the Evolution of Distributed Denial of Service Attack Vectors and Defensive Technologies in a Rapidly Changing Cybersecurity Landscape
Over the past several years, the distributed denial of service arena has undergone a profound metamorphosis, driven by the convergence of escalating bandwidth capacities and highly automated attack toolkits. Early volumetric floods, once limited to gigabit-scale on-premise assaults, have given way to multi-vector campaigns that blend application-layer disruption, low-and-slow tunneling, and volumetric spikes orchestrated via commoditized botnets. This transition has necessitated the adoption of hybrid defense architectures that can ingest high traffic volumes at the network edge, while simultaneously analyzing granular request patterns to identify stealthy anomalies that presage application-layer breaches.
Concurrently, the rise of cloud-native infrastructures and the migration toward microservices and containerized workloads have introduced additional complexity. It is no longer sufficient to rely on traditional perimeter appliances; instead, security teams must integrate scalable cloud-based scrubbing centers with agile policy orchestration and rapid policy propagation across geographically dispersed points of presence. Crucially, this shift has also stimulated a trend toward centralized threat intelligence sharing, enabling organizations to benefit from collective learning and real-time updates on emerging attack signatures. As defenders recalibrate their tactics in response to these transformative forces, a nuanced understanding of both legacy and emergent vectors will underpin the next generation of DDoS mitigation solutions.
Assessing the Broad Reach of 2025 U.S. Tariff Policies and Their Direct and Indirect Consequences on Technology Procurement and Security Investments
The imposition of new U.S. tariff measures in 2025 has reverberated across technology procurement channels, influencing the cost parameters for key hardware appliances and commercial software modules integral to DDoS mitigation stacks. Organizations heavily reliant on imported network devices and specialized mitigation gear have encountered incremental price pressures, prompting a reevaluation of procurement timelines and vendor diversification strategies. This dynamic has not only affected capital expenditure forecasts but has also reshaped contractual negotiations with multinational suppliers.
Furthermore, the indirect ripple effects of these tariffs have been felt in the software ecosystem, where licensing agreements and subscription models tied to hardware bundling clauses have undergone renegotiation. Some providers have responded by offering alternate deployment configurations that leverage locally manufactured components or containerized virtual appliances, thereby mitigating the impact of elevated customs duties. In parallel, budgetary realignments have driven heightened interest in managed DDoS services, as organizations seek capex-to-opex shifts to preserve agility. Through these cumulative categorizations of tariff-induced pressures and adaptive vendor responses, the security community continues to navigate a dynamic procurement landscape shaped by regulatory policy shifts.
Unraveling the Multifaceted Client and Technology Segmentation Models Driving Targeted DDoS Protection Strategies Across Diverse Industry Use Cases
Delving into the market through a component lens reveals dual pillars of service and solution. On the service side, organizations must weigh the benefits of fully managed DDoS oversight against the flexibility of professional consultancy engagements. While managed offerings deliver continuous monitoring, automated remediation, and SLAs that transfer certain operational risks to the provider, professional services often focus on threat-scoping assessments, custom rule creation, and incident response drills, empowering internal security teams to hone their own capabilities. Within the solution category, the hardware dimension encompasses dedicated scrubbing appliances and inline network devices that offer deterministic throughput guarantees, whereas software solutions deliver flexible, policy-driven defenses that can be deployed across virtualized or cloud-native environments.
Transitioning to deployment preferences, the narrative diverges between cloud environments and on-premise installations. Within cloud deployments, organizations are increasingly embracing hybrid models that marry the elasticity of public clouds with the control of private infrastructures. Public cloud deployments facilitate instantaneous scale-up when under attack, and private cloud settings permit tighter data governance, while hybrid architectures strike a balance by orchestrating traffic diversions based on dynamic threat intelligence. On-premise implementations, by contrast, remain vital for entities with constrained connectivity or stringent compliance requirements, ensuring local scrubbing capacity remains proximal to enterprise assets.
When considering organization size, large enterprises typically orchestrate multi-layered defenses with centralized consoles and regional scrubbing nodes to safeguard global operations. Small and medium enterprises, subdivided into medium and small cohorts, often face resource constraints that make turnkey cloud-centric services more appealing, yet some mid-tier companies opt for locally managed hardware-software bundles to retain hands-on control. In security typology, application-layer protections guard against HTTP floods, protocol exploits, and API misuse, whereas network-layer defenses address volumetric saturation, SYN flood techniques, and UDP amplification, necessitating specialized tuning across both dimensions.
The end-user segmentation spans financial institutions, energy and utilities providers, government and defense agencies, healthcare networks, retail chains, and telecommunication or IT service firms. Each vertical brings unique traffic patterns, risk appetites, and regulatory landscapes, shaping how mitigation policies are crafted, from latency-sensitive financial platforms to high-availability carrier networks. By contextualizing these segmentation vectors, stakeholders can align their DDoS protection strategies to operational priorities, risk thresholds, and compliance obligations.
This comprehensive research report categorizes the DDoS Protection & Mitigation market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Offering
- Attack Vector Type
- Deployment Mode
- Organization Size
- End User
Deciphering Regional Variations in DDoS Mitigation Adoption Patterns Across the Americas, EMEA, and Asia-Pacific to Inform Strategic Deployment Decisions
Within the Americas, a robust combination of regulatory mandates, extensive cloud adoption, and mature threat intelligence ecosystems has propelled organizations to integrate multi-layered DDoS defenses as part of standard security frameworks. High-speed connectivity and a competitive service provider landscape have fostered advanced mitigation capabilities, yet compliance directives such as data localization laws in certain jurisdictions introduce nuanced deployment considerations. Meanwhile, regional carrier outage patterns and cross-border traffic flows highlight the importance of geographically distributed scrubbing centers and network peering agreements.
In Europe, the Middle East, and Africa, divergent regulatory regimes and infrastructure disparities punctuate the DDoS protection narrative. Financial capitals in Western Europe often lead in mandating rigorous uptime and resilience standards, driving enterprises to partner with cross-regional mitigation providers. Conversely, in emerging markets across EMEA, connectivity constraints and cost sensitivities can delay adoption of fully distributed defense architectures, steering some organizations toward managed cloud services hosted in proximal data centers. Data privacy regulations such as GDPR intersect with DDoS controls, as packet inspection and traffic routing decisions must adhere to strict data handling policies.
Across the Asia-Pacific region, expansive digital transformation initiatives have accelerated cloud migrations, IoT rollouts, and remote access frameworks. Rapidly developing economies have emerged as fertile ground for DDoS campaigns exploiting under-protected networks, while advanced service providers in mature markets offer integrated threat-intelligence-driven platforms. Strategic deployments in APAC often emphasize hybrid cloud scrubbing capabilities, accommodating regional latency requirements and diverse connectivity profiles. Through these regional lenses, organizations can identify tailored mitigation pathways aligned with localized threat dynamics, regulatory frameworks, and infrastructure realities.
This comprehensive research report examines key regions that drive the evolution of the DDoS Protection & Mitigation market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Spotlighting Leading Innovators and Strategic Collaborators Reshaping the DDoS Protection Ecosystem Through Cutting-Edge Solutions and Alliances
Innovation within the DDoS protection space continues to accelerate, driven by a spectrum of established cybersecurity vendors, cloud hyperscalers, and niche specialists. Leading network security companies have integrated advanced anomaly detection engines with high-capacity scrubbing fabrics, charging forward with automated playbooks that dynamically quarantine malicious flows. Cloud platform providers have bolstered native shields by embedding volumetric filtering into edge delivery networks, granting seamless scale without the need for separate scrubbing contracts. Meanwhile, pure-play security service organizations and managed detection and response providers have augmented their portfolios with DDoS-specific monitoring and incident support, complementing broader security operations capabilities.
Strategic alliances and acquisitions have also reshaped the competitive landscape. Networking equipment manufacturers have partnered with cloud service orchestration platforms to ensure consistent policy propagation across hybrid environments, and managed security providers have acquired expert consulting firms to deepen vertical-specific DDoS expertise. Open source initiatives have contributed advanced mitigation rule sets and community-driven threat intelligence feeds, enabling organizations to tap into collective defense insights at minimal cost. As a result, the ecosystem has matured into a collaborative marketplace where interoperability, API-driven controls, and shared intelligence become key differentiators in vendor capabilities.
Looking forward, integration of artificial intelligence and machine learning models with threat-intelligence repositories promises to accelerate detection and response cycles. Vendors that successfully blend predictive analytics with automated enforcement will continue to lead, while those focusing on specialized application-layer defenses or network-layer orchestration will carve out critical niches. In this dynamic environment, partnerships remain essential: security vendors that align their roadmaps with cloud providers, networking infrastructure firms, and managed service integrators can deliver end-to-end DDoS resilience.
This comprehensive research report delivers an in-depth overview of the principal market players in the DDoS Protection & Mitigation market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- A10 Networks, Inc.
- Akamai Technologies, Inc.
- Alibaba Group Holding Limited
- Amazon Web Services, Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Cloudflare, Inc.
- Corero Network Security plc
- DDoS‑Guard Ltd.
- F5, Inc.
- Fastly, Inc.
- Fortinet, Inc.
- Google LLC by Alphabet Inc.
- Hewlett Packard Enterprise Company
- Huawei Technologies Co., Ltd.
- Imperva, Inc. by Thales Group
- Link11 GmbH
- Microsoft Corporation
- NetScout Systems, Inc.
- Neustar, Inc.
- Nexusguard Limited
- NSFOCUS, Inc.
- Palo Alto Networks, Inc.
- Radware Ltd.
- Trend Micro Incorporated
- Verisign, Inc.
Implementing Data-Driven and Future-Proof DDoS Defense Frameworks with Actionable Steps to Fortify Infrastructure and Enhance Incident Response Posture
To effectively guard against the ever-evolving spectrum of DDoS threats, organizations should first construct a comprehensive defense architecture that integrates both cloud-native and on-premise mitigation layers. By embedding scrubbing nodes at critical network egress points and configuring policy orchestration systems to adapt in real time, teams can ensure that volumetric surges are absorbed without impacting service availability. Equally important is the deployment of advanced behavioral analytics that discern anomalous traffic patterns at the application layer, triggering automated countermeasures that block or throttle malicious flows before they disrupt user experiences.
Next, security leaders should prioritize the establishment of formalized threat intelligence sharing agreements with industry peers and service providers. These collaboration frameworks enable the rapid exchange of indicators of compromise, emerging attack signatures, and post-incident forensics, reducing the window of exposure. Simultaneously, organizations ought to formalize robust incident response protocols that delineate clear escalation paths, communication templates for stakeholders, and playbooks for tabletop exercises. Consistent drills that simulate high-volume DDoS events will refine cross-functional coordination between network operations, security operations, and business continuity teams.
On the procurement front, executives should adopt a dual-vendor strategy to mitigate single-supplier dependencies, leveraging complementary strengths to maintain continuity in the event of service disruptions. Contract negotiations must address critical metrics such as time-to-mitigate, service level agreements for traffic cleansing capacities, and flexibility clauses that accommodate shifting traffic patterns and emerging attack methodologies. Beyond contractual safeguards, decision-makers should champion investment in staff training programs focused on DDoS detection and response, ensuring that security operations personnel remain adept at fine-tuning defenses as new vectors materialize.
Finally, governance structures should incorporate periodic reviews of deployment topologies, tariff impacts, and regional regulatory shifts to maintain alignment with strategic risk tolerances. By establishing a continuous improvement cycle-rooted in insights from real-world incidents, technology roadmaps, and sector-specific threat assessments-organizations can iterate defenses, optimize expenditure, and uphold the highest standards of digital continuity.
Outlining a Rigorous and Transparent Research Approach Integrating Qualitative Insights and Quantitative Analysis to Ensure Credible DDoS Protection Findings
This analysis synthesizes insights derived from a multi-phased research methodology, beginning with comprehensive secondary research of public domain sources, industry guidelines, and regulatory frameworks. Primary data was gathered through in-depth interviews with cybersecurity executives, network engineers, and managed security service providers, yielding qualitative perspectives on deployment challenges, tariff negotiations, and vendor selection criteria. To validate these findings, a series of workshops and peer-review sessions were conducted, engaging subject matter experts in threat intelligence, cloud architecture, and compliance to cross-verify thematic conclusions.
Quantitative rigor was ensured by triangulating telemetry data from anonymized traffic logs provided under nondisclosure agreements, combined with third-party indicators of DDoS incident frequency and scale. Advanced statistical techniques were applied to identify correlations between mitigation approaches and recovery times, informing the assessment of solution efficacy without producing market sizing metrics. Throughout the process, quality assurance protocols maintained data integrity and ethical guidelines governed all stakeholder engagements. The resulting framework delivers a robust, transparent foundation for interpreting evolving DDoS protection imperatives.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our DDoS Protection & Mitigation market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- DDoS Protection & Mitigation Market, by Offering
- DDoS Protection & Mitigation Market, by Attack Vector Type
- DDoS Protection & Mitigation Market, by Deployment Mode
- DDoS Protection & Mitigation Market, by Organization Size
- DDoS Protection & Mitigation Market, by End User
- DDoS Protection & Mitigation Market, by Region
- DDoS Protection & Mitigation Market, by Group
- DDoS Protection & Mitigation Market, by Country
- United States DDoS Protection & Mitigation Market
- China DDoS Protection & Mitigation Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1908 ]
Synthesizing Key Insights from Market, Technology, and Regulatory Analyses to Illuminate Pathways for Robust DDoS Security and Organizational Growth
The escalating sophistication of distributed denial of service attacks necessitates a strategic shift from reactive stand-alone appliances toward cohesive, intelligence-driven defense ecosystems. As attack vectors proliferate across network and application layers, organizations must embrace adaptable architectures that blend on-premise control with cloud scalability. Regulatory and policy dynamics, including evolving tariff regimes and data privacy mandates, further underscore the importance of aligning procurement and deployment strategies with both global standards and localized requirements.
Segmentation analysis reveals that no single model suffices; rather, a calibrated mix of managed services and turnkey solutions, deployed across public, private, and hybrid clouds, affords optimal flexibility. Regional insights highlight that mitigation strategies must be attuned to local connectivity patterns, compliance mandates, and threat actor profiles, while vendor landscapes emphasize the value of partnerships that span hardware manufacturers, cloud hyperscalers, and boutique security specialists.
Through a combination of advanced analytics, collaborative threat sharing, and structured incident response playbooks, organizations can not only mitigate immediate risks but also cultivate a continuous improvement cycle. By synthesizing these multifaceted insights, decision-makers are equipped to chart resilient pathways that safeguard digital continuity, foster stakeholder confidence, and drive sustained organizational performance in the face of persistent DDoS threats.
Elevate Your Cyber Defense Strategy Today by Engaging Directly with the Associate Director of Sales & Marketing for Customized DDoS Protection Insights and Offerings
To unlock the full value of this in-depth analysis and to explore how these strategic insights can be tailored to your organization’s priorities, we invite you to connect directly with Ketan Rohom, Associate Director of Sales & Marketing. Engage in a one-on-one briefing to discuss your unique challenges, gain customized recommendations, and secure the comprehensive executive report that will empower your next steps in reinforcing your defenses against distributed denial of service threats. Reach out today to initiate a collaborative dialogue and transform these findings into actionable outcomes for your security posture.

- How big is the DDoS Protection & Mitigation Market?
- What is the DDoS Protection & Mitigation Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




