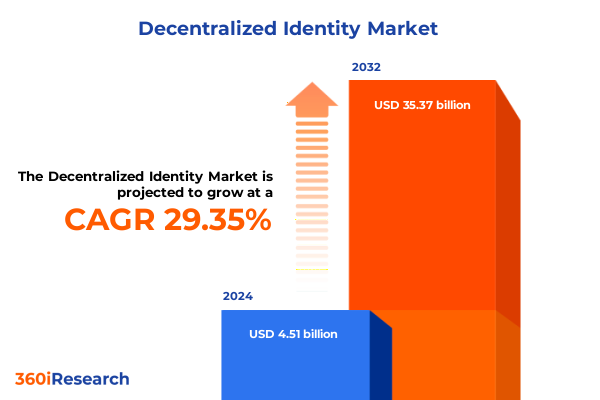
The Decentralized Identity Market size was estimated at USD 5.72 billion in 2025 and expected to reach USD 7.27 billion in 2026, at a CAGR of 29.70% to reach USD 35.37 billion by 2032.
Setting the Stage for a Decentralized Identity Revolution That Elevates Security, Privacy, and User Control Across Digital Ecosystems
As organizations navigate an increasingly digital world, the limitations of traditional identity systems have become starkly apparent. Centralized directories and siloed credentials expose enterprises to breaches, regulatory scrutiny, and user frustration. At the same time, individuals face password fatigue, data privacy concerns, and limited control over their personal information. In this context, decentralized identity emerges as a compelling alternative, offering a paradigm that balances robust security with a user-centric approach to data sovereignty.
Decentralized identity leverages distributed ledger technologies and cryptographic proof models to enable direct relationships between identity holders and service providers. By eliminating intermediaries and enabling verifiable credentials, it promises to reduce fraud, streamline compliance, and restore trust in digital interactions. Furthermore, its modular architecture allows seamless integration with emerging technologies-such as zero trust frameworks and mobile wallets-facilitating both incremental adoption within existing infrastructures and green-field implementations.
This executive summary sets the stage for a deep dive into the transformative landscape of decentralized identity. It highlights pivotal industry shifts, examines the impact of trade policies, delves into key segmentation and regional dynamics, profiles leading innovators, and offers actionable recommendations. Additionally, it outlines the rigorous research methodology behind the report and concludes with a forward-looking perspective, culminating in a clear invitation to engage with Ketan Rohom to access the full breadth of insights.
Uncovering the Pivotal Shifts Redefining Identity Management Through Blockchain, Zero Trust Principles, and Enhanced User Empowerment Models
The identity management landscape has entered a period of profound transformation, driven by the convergence of blockchain innovations, evolving data privacy regulations, and a growing emphasis on user empowerment. Traditional perimeter-based security is giving way to zero trust models that require continuous verification, while enterprise adoption of distributed ledger technologies enables immutable audit trails and tamper-resistant credential exchanges. Simultaneously, new standards-such as decentralized identifiers and verifiable credential specifications-are maturing, creating the technical foundation for interoperable solutions across public and private sectors.
Moreover, regulatory frameworks like GDPR and the proposed revisions to data protection laws in key markets are reinforcing the need for privacy-preserving architectures. Organizations are now compelled to give individuals greater control over how their personal data is stored, shared, and revoked. In tandem, the proliferation of mobile devices and digital wallets is reshaping user expectations, making seamless credential exchange and offline functionality vital components of any identity strategy.
Taken together, these disruptive forces are not only redefining security and compliance but also unlocking new business models. Enterprises across industries can leverage decentralized identity to streamline customer onboarding, enhance fraud detection, and enable frictionless cross-border services. As a result, market participants must adapt to these transformative shifts or risk falling behind in a rapidly evolving ecosystem.
Analyzing the Comprehensive Effects of 2025 United States Tariffs on the Decentralized Identity Market and Global Supply Chain Dynamics
In 2025, the United States implemented a series of targeted tariffs on imported hardware and technology components used in digital identity solutions. These measures were designed to bolster domestic manufacturing of biometric sensors, secure elements for decentralized identity wallets, and specialized chips for cryptographic operations. As a consequence, vendors relying on offshore production found themselves facing increased costs and supply chain bottlenecks, prompting them to explore nearshoring and alternative sourcing strategies to maintain project timelines and cost targets.
At the same time, this policy shift has accelerated interest in localizing critical infrastructure components, such as secure hardware modules and identity-proofing devices. Enterprises have responded by forging partnerships with domestic manufacturers and consortiums to develop home-grown alternatives, thereby reducing exposure to tariffs. While this transition entails upfront investment in capacity building and certification processes, it presents an opportunity to strengthen national supply chains and foster innovation in specialized security hardware.
Furthermore, the tariff environment has underscored the importance of software-centric identity architectures that decouple verification logic from hardware dependencies. Organizations are increasingly prioritizing browser-based or mobile SDK-driven verifiable credential issuance and verification flows to mitigate the impact of hardware cost fluctuations. By leveraging software wallets and leveraging cloud-hosted cryptographic services, enterprises can maintain resilience in the face of geopolitical shifts, ensuring uninterrupted identity validation across global operations.
Illuminating Critical Segmentation Insights Across Authentication Types, Core Components, Diverse Participants, and Varied End Users and Applications
A nuanced understanding of the decentralized identity market emerges through a detailed examination of multiple segmentation dimensions. From an authentication perspective, solutions span biometric authentication, document authentication, and knowledge-based systems. Biometric authentication, for instance, encompasses facial recognition, fingerprint scanning, and voice recognition technologies. Document authentication relies on government-issued identity cards or utility bills as proof of identity, while knowledge-based methods leverage password and PIN code systems alongside security questions to verify users.
Shifting focus to core components, the ecosystem comprises decentralized identifiers, secure identity wallets, and verifiable credentials. Decentralized identifiers serve as the foundational anchor, enabling entities to reference digital identities without centralized registries. Identity wallets act as personal vaults for storing and presenting credentials, while verifiable credentials encapsulate claims that can be cryptographically verified by validators.
Beyond technology, participants in the ecosystem include identity consumers, such as service providers and enterprises; identity providers that issue credentials; and identity validators responsible for authentication and compliance checks. The market finds practical application across a wide spectrum of sectors, including banking, financial services and insurance, government services, healthcare, retail environments, and telecommunications networks.
Finally, end users range from developers who integrate decentralized identity frameworks into applications, to enterprises-both large corporations and small and medium-sized businesses-that deploy solutions at scale, and individuals who ultimately hold and manage their personal credentials. By weaving these segmentation strands together, stakeholders can identify tailored strategies for product development, partnership formation, and targeted go-to-market initiatives.
This comprehensive research report categorizes the Decentralized Identity market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Type
- Component
- Participants
- Application
- End-User
Exploring Regional Divergences and Growth Drivers in the Americas, Europe Middle East Africa, and Asia Pacific Decentralized Identity Adoption
Decentralized identity adoption varies significantly across the Americas, Europe Middle East Africa (EMEA), and Asia Pacific regions, shaped by regulatory environments, infrastructure maturity, and industry priorities. In the Americas, early movers in the United States and Canada have embraced digital driver’s licenses and mobile wallet prototypes, while leading financial institutions explore interoperable credential exchanges. Meanwhile, Latin American governments are partnering with regional consortia to pilot cross-border identity corridors, leveraging mobile-first strategies to extend inclusion to underserved communities.
Within EMEA, the eIDAS regulation and GDPR enforcement have catalyzed government digital identity programs in countries such as Estonia and Germany. Public-private collaborations are advancing digital health credentials, and telecom operators are integrating verifiable credential frameworks to streamline customer onboarding processes. Furthermore, pan-European initiatives aim to harmonize trust frameworks, laying the groundwork for seamless credential portability across member states.
In Asia Pacific, national identity schemes in India and Australia, coupled with large-scale implementations in East Asian markets, demonstrate strong governmental commitment to digital identity transformation. Mobile wallet penetration remains high, and messaging platforms are increasingly embedding verifiable credential interfaces to facilitate peer-to-peer trust exchanges. Across the region, strategic investments in edge computing and local data centers are accelerating adoption, while industry consortia align on standards to ensure interoperability and regulatory compliance.
This comprehensive research report examines key regions that drive the evolution of the Decentralized Identity market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Leading Innovators and Strategic Collaborators Driving Technological Advancements and Partnerships in the Decentralized Identity Ecosystem
Companies leading the charge in decentralized identity vary in their focus areas yet share a common vision of secure, user-centric solutions. Some innovators specialize in distributed ledger platforms that enable scalable decentralized identifier registries, while others provide modular software kits for credential issuance and wallet orchestration. Additionally, hardware vendors are developing secure elements optimized for mobile devices, ensuring that private keys remain protected even on consumer-grade smartphones.
Strategic collaborations have emerged as a cornerstone of industry progress, uniting technology providers, financial institutions, and regulatory bodies under consortia that drive interoperability and governance frameworks. Open source foundations play a critical role in defining standards and fostering community-driven enhancements, while commercial vendors differentiate through value-added services such as integration toolkits, analytics dashboards, and compliance modules.
Leading enterprises are also forging alliances with system integrators and consulting firms to de-risk deployments. By leveraging partner networks, organizations can accelerate time to market and tailor solutions to industry-specific requirements, from KYC compliance in financial services to patient data privacy in healthcare. This collaborative ecosystem not only accelerates technical innovation but also ensures that decentralized identity solutions achieve real-world scalability and regulatory alignment.
This comprehensive research report delivers an in-depth overview of the principal market players in the Decentralized Identity market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- 1Kosmos Inc.
- Accenture PLC
- Blockpass UK Limited
- Circle Internet Financial, LLC
- Civic Technologies, Inc.
- Dai Nippon Printing Co., Ltd.
- Datarella GmbH
- Dragonchain
- DXC Technology Company
- Evernym
- Finema Co., Ltd.
- Gataca Labs S.L.U.
- GSMA Ltd.
- Hu-manity Rights, Inc.
- IDEMIA Group
- International Business Machines Corporation
- Jolocom GmbH
- Microsoft Corporation
- Nuggets Ltd.
- NuID, Inc.
- Persistent Systems Ltd
- SecureKey Technologies Inc. by Avast Limited
- Validated ID S.L.
- Wipro Limited
- Workday, Inc.
Strategic Roadmaps and Recommendations to Empower Industry Leaders in Accelerating Secure, Interoperable, and User-Centric Decentralized Identity
Industry leaders can accelerate decentralized identity adoption by establishing clear governance structures that align technical standards with organizational priorities. First, creating a cross-functional steering committee ensures executive support and fosters collaboration between IT, legal, and business units. Next, adopting open standards-such as decentralized identifiers and verifiable credentials-lays the groundwork for interoperability and reduces vendor lock-in. By participating in industry consortia and contribution to reference implementations, organizations can influence standards evolution and benefit from shared best practices.
Simultaneously, investing in developer enablement is crucial. Providing comprehensive SDKs, sandbox environments, and certification programs empowers engineering teams to integrate decentralized identity capabilities with confidence. To address user experience, conducting iterative usability testing and prioritizing intuitive wallet interfaces will drive consumer and enterprise adoption.
Finally, piloting real-world use cases-such as customer onboarding in financial services or employee credentialing in corporate environments-enables organizations to validate performance, measure operational impact, and refine deployment strategies. By combining strategic governance, technical investment, and user-centric design, industry leaders can unlock secure, privacy-preserving identity solutions that drive competitive differentiation.
Outlining Rigorous Research Methodology Encompassing Data Collection, Qualitative and Quantitative Analysis, and Validation Techniques for Integrity
The research methodology underpinning this report integrates both qualitative and quantitative approaches to ensure comprehensive coverage and analytical rigor. Primary research comprised interviews with identity architects, security leaders, and solution providers across multiple industries. These conversations deepened understanding of real-world deployment challenges and success factors. In parallel, an extensive secondary research phase reviewed technical specifications, regulatory guidelines, and white papers to map emerging trends and standards.
On the qualitative front, thematic analysis of interview transcripts identified recurring themes such as governance models, interoperability hurdles, and user experience optimization. Quantitative analysis leveraged survey data from enterprise IT decision-makers and developer communities, offering insights into adoption rates, technology preferences, and investment priorities. Data triangulation across multiple sources enhanced validity, while peer reviews from external domain experts provided critical feedback and validation.
To further ensure the integrity of findings, the research incorporated vendor briefings and product demonstrations, allowing for direct comparison of feature sets and roadmap alignment. Finally, a collaborative review process with neutral moderators and governance board members refined the report’s structure and recommendations, ensuring that conclusions reflect a balanced perspective on decentralized identity’s present capabilities and future potential.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Decentralized Identity market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Decentralized Identity Market, by Type
- Decentralized Identity Market, by Component
- Decentralized Identity Market, by Participants
- Decentralized Identity Market, by Application
- Decentralized Identity Market, by End-User
- Decentralized Identity Market, by Region
- Decentralized Identity Market, by Group
- Decentralized Identity Market, by Country
- United States Decentralized Identity Market
- China Decentralized Identity Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1590 ]
Summarizing the Strategic Imperatives and Future Outlook for Decentralized Identity Adoption to Drive Secure and Privacy-Centric Digital Transformation
As decentralized identity moves from pilot projects to mainstream deployments, organizations must embrace strategic imperatives that foster secure, privacy-centric digital transformation. Key among these is the adoption of interoperable standards that enable seamless credential exchanges across diverse platforms and jurisdictions. By prioritizing user empowerment through transparent consent mechanisms and self-sovereign models, enterprises can build trust and differentiate their brand in an increasingly privacy-conscious market.
Looking ahead, the convergence of decentralized identity with emerging technologies-such as edge computing, artificial intelligence, and the Internet of Things-will unlock new use cases that extend beyond traditional web and mobile applications. For example, device-to-device trust in industrial environments or autonomous vehicle identity frameworks will rely on robust, decentralized credentialing mechanisms.
Moreover, regulators and consortiums will play a pivotal role in shaping the evolution of trust frameworks, balancing innovation with consumer protection. Organizations that engage proactively in these dialogues will be best positioned to influence policy trajectories and ensure compliance. Ultimately, embracing decentralized identity not only addresses current security and privacy challenges but also lays the foundation for a more resilient and inclusive digital economy.
Engage With Ketan Rohom to Unlock Comprehensive Decentralized Identity Insights and Secure Your In-Depth Market Research Report Today
To explore the full breadth of insights and strategic analysis on decentralized identity, reach out to Ketan Rohom, Associate Director of Sales & Marketing, for personalized guidance. He can provide a detailed overview of the methodology, segmentation, regional dynamics, and company assessments that shape the transformative potential of identity innovation. Engaging directly with Ketan will give you exclusive access to expert recommendations, actionable roadmaps, and the comprehensive data you need to make confident decisions about technology adoption and partnership strategies.
By connecting with Ketan, you will gain clarity on how decentralized identity can redefine customer interactions, streamline compliance, and secure digital ecosystems across industries. Whether you aim to pilot a proof of concept, integrate a verifiable credential framework, or benchmark your organization against global best practices, Ketan can tailor the insights to your unique business objectives. Don’t miss the opportunity to empower your strategy with our in-depth research and accelerate your journey toward a more secure and user-centric identity paradigm.
Engage with Ketan Rohom today to secure your copy of the market research report and transform the way your organization approaches identity management.

- How big is the Decentralized Identity Market?
- What is the Decentralized Identity Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




