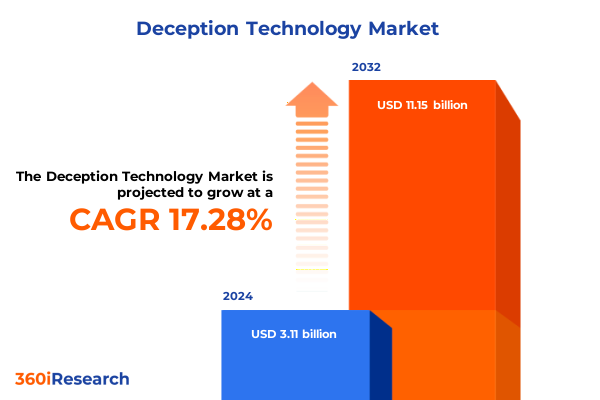
The Deception Technology Market size was estimated at USD 3.62 billion in 2025 and expected to reach USD 4.21 billion in 2026, at a CAGR of 17.43% to reach USD 11.15 billion by 2032.
How Deception Technology Transforms Modern Cybersecurity Posture by Deploying Dynamic Lures and Traps to Counteract Advanced Persistent Threats Inside Networks
Historically, organizations relied on simple honeypots to bait attackers and capture rudimentary intrusion data. These early implementations served as proof-of-concept tools but lacked scalability and context-awareness. Over time, advances in automation, threat intelligence, and synthetic assets enabled the evolution of deception technology into a robust discipline. By embedding dynamic decoys throughout complex IT and OT environments, enterprises have graduated beyond static honeypots to a comprehensive active defense model.
In recent years, organizations have witnessed a paradigm shift in their cybersecurity approach as traditional perimeter defenses struggle to contain increasingly sophisticated threats. The evolution of deception technology has emerged as a game-changing strategy that embeds interactive lures and decoys across the infrastructure to misdirect malicious actors. This proactivity enables security teams to recognize attackers in real time, substantially reducing dwell time and preventing lateral movement. As a result, enterprises can complement their existing defense frameworks with deceptive layers that act as an early warning system, fundamentally altering the detection and response lifecycle.
Moreover, the convergence of automation and intelligence in deception platforms has heightened their efficacy. By simulating realistic assets-ranging from server infrastructures to application environments-these systems engage adversaries with believable bait, gathering contextual threat intelligence. This novel methodology mitigates alert fatigue, as genuine intrusion attempts are clearly distinguished from benign anomalies. Consequently, security operations centers achieve greater operational efficiency, reallocating resources toward strategic initiatives rather than triaging false positives.
Furthermore, regulatory pressures and evolving compliance mandates are accelerating the adoption of deception solutions. Organizations facing stringent data protection requirements recognize the value of preemptive detection and continuous monitoring to demonstrate due diligence. In addition, heightened risk awareness among executive leadership underscores the necessity of integrating multiple defensive layers. Therefore, deception technology’s growing prominence reflects a broader shift toward active defense postures that anticipate adversary behaviors rather than merely reacting to incidents.
Additionally, industry case studies have illustrated that combining deception capabilities with threat intelligence feeds and endpoint detection evolves into a holistic defense ecosystem. When deception tools feed real-time alerts into orchestration platforms, automatic containment actions can isolate compromised assets before adversaries achieve their objectives. This integration empowers security teams to leverage deception signals as actionable input for incident response playbooks and threat hunting operations. In essence, deception technology has transitioned from experimental deployments to a strategic necessity that fortifies modern cyber resilience architectures.
Examining the Transformative Shifts in Enterprise Security Landscape Driven by Integration of AI, Cloud Adoption, and Heightened Regulatory Demands Impacting Deception Strategies
The cybersecurity terrain continues to evolve as enterprises integrate advanced technologies into their defense arsenals. Artificial intelligence and machine learning capabilities now underpin next-generation deception platforms, enabling predictive decoy deployment and anomaly detection with unprecedented accuracy. Automated algorithms analyze network behavior to identify potential attack paths and dynamically generate deception scenarios tailored to the environment. This level of sophistication not only enhances threat visibility but also adapts in real time to shifting attacker tactics, effectively raising the cost of intrusion for adversaries.
Simultaneously, the widespread migration to cloud architectures has introduced new complexities in deception strategy design. Cloud-native workloads and serverless functions require flexible decoy mechanisms that operate seamlessly across hybrid environments. As organizations distribute assets among public, private, and multi-cloud infrastructures, deceptive lures must maintain consistency in appearance and functionality to remain credible to attackers. Consequently, vendors are innovating with containerized decoys and microservice-level traps to align with elastic workloads and automation pipelines. These advancements reinforce defense-in-depth models by extending deception coverage beyond traditional data centers.
In parallel, regulatory landscapes have intensified, compelling organizations to demonstrate robust cybersecurity controls and incident management processes. Compliance frameworks such as GDPR, CCPA, and emerging federal directives emphasize continuous monitoring and rapid breach detection. These requirements have elevated deception technology from a supplemental feature to a fundamental component of security roadmaps. In addition, collaboration between security operations and legal teams ensures that deception deployments adhere to privacy and operational standards. Ultimately, these transformative shifts converge to drive broader adoption of deception technology as businesses strive to remain resilient amid a dynamic threat ecosystem.
Looking ahead, the convergence of 5G connectivity, edge computing, and Internet of Things deployments will further influence deception strategy evolution. As network perimeters become increasingly diffuse, decoy placement must adapt to transient edge nodes and interconnected device ecosystems. Vendors and security teams will need to design lightweight, automated deception elements that can be rapidly instantiated across mobile and remote environments. This forward-looking perspective underscores the importance of flexibility and innovation in achieving sustained security effectiveness in an ever-shifting technological landscape.
Analyzing the Cumulative Impact of 2025 United States Tariffs on Cybersecurity Supply Chains and Technology Procurement for Deception Solutions Across Global Operations
The introduction of targeted tariffs by the United States in early 2025 has created significant ripple effects across the cybersecurity supply chain, particularly for deception technology providers that rely on specialized hardware components. Devices such as programmable network switches, customized firmware modules, and sensor arrays have faced increased import duties, resulting in elevated procurement costs for both vendors and end users. As a consequence, some defense organizations have encountered budgetary constraints when updating or scaling deception deployments, prompting a reevaluation of hardware-intensive solutions in favor of software-heavy approaches.
Furthermore, service-oriented segments have experienced indirect cost pressures due to shifts in labor and travel expenses. Managed deception services, which historically included on-site setup and periodic maintenance, now contend with rising operational overheads influenced by trade policy-induced inflation. Professional service engagements for deployment and threat intelligence analysis have similarly been affected, leading providers to streamline engagement models and emphasize remote delivery. This transition has accelerated the adoption of self-service deception platforms and cloud-based management consoles, enabling clients to maintain robust deception strategies while mitigating tariff-driven cost increases.
Moreover, the software component landscape has adapted through strategic pivoting toward domestic development and alternative supply sources. Developers of application deception, host-based decoy systems, and network traps have intensified collaborations with local partners to circumvent import barriers. Simultaneously, organizations have expanded open-source integrations and community-driven deception frameworks to reduce dependency on proprietary modules. In addition, industry consortia are engaging policymakers to advocate for exemptions on critical cybersecurity imports, emphasizing the national importance of threat detection and incident response capabilities.
In response to these challenges, procurement teams across leading enterprises have diversified their supply chains and strengthened vendor risk assessments. By qualifying multiple suppliers and negotiating long-term agreements, organizations aim to secure consistent access to essential hardware and software components. Some entities are also exploring onshore manufacturing partnerships to localize production and shield critical capabilities from future tariff fluctuations. These strategic sourcing measures highlight the imperative of supply chain resilience and cost predictability in sustaining deception technology investments amid shifting trade policies.
Unlocking Key Segmentation Insights to Illuminate Demand Dynamics Across Component Categories Deployment Models Organizational Sizes and End User Verticals in Deception Technology
Analysis of the component dimension reveals divergent growth trajectories for hardware, services, and software offerings within the deception ecosystem. Hardware solutions continue to provide foundational support through physical decoys and specialized devices, yet their growth pace is moderated by escalating procurement expenses. In contrast, services have gained momentum as organizations seek expertise in deploying and managing complex deception environments. Managed offerings deliver continual monitoring and maintenance, while professional engagements facilitate tailored strategy design and incident response readiness. Software modules-spanning application deception, host-level decoys, and network traps-demonstrate the strongest adoption as enterprises prioritize flexibility and rapid scalability.
Transitioning to deployment preferences, cloud-based deception platforms are increasingly favored for their ease of integration with modern infrastructure and elastic resource allocation. The scalability of cloud deployments enables security teams to deploy decoys across distributed network segments without extensive on-premises investment. Nevertheless, on-premises solutions retain appeal for organizations with stringent data residency and compliance mandates. Simultaneously, organizational size influences adoption patterns; large enterprises leverage extensive security budgets and centralized teams to implement multi-faceted deception initiatives, while small and medium enterprises often gravitate toward turnkey, SaaS-based deception tools that minimize complexity and overhead.
When considering end user vertical dynamics, financial institutions and healthcare providers lead implementation efforts due to their high-value data and regulatory oversight, necessitating proactive threat detection capabilities. Energy and utilities sectors also prioritize deception to protect critical infrastructure from nation-state actors, whereas government entities deploy decoys to safeguard sensitive information and fortify public services. Meanwhile, the IT and telecom industry utilizes deception techniques to secure expansive network infrastructures and mitigate the risk of advanced persistent threats, and retail organizations explore targeted lures to defend against point-of-sale intrusions and credential theft. These segmentation insights collectively shape market strategies and drive technology innovation across the deception landscape.
This comprehensive research report categorizes the Deception Technology market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Deployment Mode
- Organization Size
- End User
Navigating Regional Trends and Adoption Patterns Across Americas Europe Middle East Africa and Asia Pacific to Uncover Strategic Opportunities in Deception Technology Deployment
In the Americas, the United States continues to dominate adoption of deception technology, driven by sophisticated threat environments and proactive regulatory frameworks. Canadian enterprises also demonstrate growing interest, particularly in sectors such as financial services and critical infrastructure, spurred by national cybersecurity strategies. Latin American markets are gradually embracing deception solutions as digital transformation accelerates and external partnerships expand. In addition, cross-border collaboration with North American security vendors enhances access to managed services and specialized decoy deployments, reinforcing the region’s leadership in innovative defense postures.
Across Europe, the Middle East, and Africa, varying regulatory landscapes and threat profiles influence deployment patterns. Western European nations lead in maturity of security programs, integrating deception tools within established cybersecurity operations and compliance regimes. Meanwhile, Middle Eastern countries are investing heavily in securing oil, gas, and energy infrastructures by integrating decoy strategies that address advanced persistent threats. African markets, while still emerging, show promising growth as digital initiatives scale and regional collaborations develop. Furthermore, data protection regulations in Europe and emerging privacy laws in other jurisdictions have propelled interest in deception as a proactive control measure.
Asia Pacific presents a diverse landscape of adoption, marked by rapid digitalization and heightened incident awareness. In East Asia, advanced research institutions and major enterprises deploy sophisticated deception frameworks to counter state-sponsored threats. Southeast Asian countries are progressively embracing cloud-based deception services to protect evolving e-commerce ecosystems, whereas Australia and New Zealand maintain robust security programs combining on-premises and hybrid deployments. As intra-regional partnerships strengthen and local vendor ecosystems mature, the Asia Pacific region is poised for accelerated growth in deception technology utilization.
This comprehensive research report examines key regions that drive the evolution of the Deception Technology market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Leading Companies Shaping the Deception Technology Market Through Innovative Portfolios Strategic Partnerships and Expanding Global Footprints to Enhance Cyber Resilience
Attivo Networks, a pioneer in deception technology, continues to expand its portfolio with advanced endpoint detection and response integrations, coupling host-based deception modules with comprehensive threat intelligence feeds. The company’s global expansion has been bolstered by strategic alliances with major managed security service providers, enabling delivery of comprehensive deception-as-a-service offerings. Meanwhile, TrapX Security has differentiated itself through specialized network deception appliances and proactive threat disruption capabilities. By emphasizing real-time detection and automated response workflows, TrapX addresses complex attack vectors while reducing manual intervention requirements and enhancing operational efficiency.
Illusive Networks has positioned itself at the forefront of contextual deception strategies by integrating adaptive deception controls and identity-driven decoys. Its solutions capitalize on behavioral analytics to identify lateral movement and insider threats before data exfiltration occurs. Through partnerships with cloud service providers, Illusive has augmented its platform to support multi-cloud deployments, thereby meeting the requirements of highly distributed enterprise environments. In addition, Fidelis Cybersecurity has extended its detection portfolio by incorporating deception sensors into its unified visibility and response platform, delivering a cohesive ecosystem for threat hunting and incident management.
Cymmetria has gained recognition for its modular deception architecture, allowing organizations to tailor decoy deployment at the network, application, and host levels with minimal overhead. Similarly, Acalvio Technologies emphasizes autonomous deception operations powered by self-learning AI algorithms that optimize decoy placement over time. Smokescreen Technologies also innovates in threat research by simulating adversary tactics within controlled environments, generating actionable intelligence that continually refines deception strategies. Collectively, these vendors are fostering a rich ecosystem of alliances, mergers, and collaborative initiatives that drive continuous innovation and reinforce deception technology’s position as an indispensable cyber defense layer.
This comprehensive research report delivers an in-depth overview of the principal market players in the Deception Technology market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Acalvio Technologies, Inc.
- Akamai Technologies, Inc.
- Allure Security Technology, Inc.
- Broadcom Inc.
- CounterCraft, S.L.
- CyberTrap, Inc.
- Fidelis Cybersecurity, Inc.
- Fortinet, Inc.
- Illusive Networks Ltd.
- LogRhythm, Inc.
- Microsoft Corporation
- Morphisec Ltd.
- Palo Alto Networks, Inc.
- Rapid7, Inc.
- SentinelOne, Inc.
- Smokescreen Technologies, Inc.
- TrapX Security, Inc.
- Trellix, Inc.
- Zscaler, Inc.
Actionable Recommendations for Industry Leaders to Maximize Deception Technology Effectiveness Through Strategic Integration Operational Alignment and Continuous Threat Intelligence Acceleration
To fully leverage deception technology as a proactive defense mechanism, organizations should integrate decoy deployment into their existing security orchestration and response workflows. By funneling deception alerts into centralized incident management systems, security teams can automate containment actions and accelerate remediation, reducing the manual effort required for investigation. Furthermore, aligning deception initiatives with threat modeling exercises ensures that decoys are strategically placed along critical attack paths, maximizing the chance of early detection.
In addition, operational alignment between security, network, and compliance teams is essential to maintain both effectiveness and governance. Regular cross-functional workshops and tabletop exercises will foster shared understanding of deception tactics and ensure that decoy deployments adhere to organizational policies and regulatory requirements. These sessions also offer opportunities to refine incident response playbooks, incorporate legal and privacy considerations, and cultivate a culture of collaborative defense.
Finally, continuous threat intelligence acceleration should guide deception strategy refinement. Organizations are encouraged to establish feedback loops whereby insights gleaned from deception engagements-such as attacker behaviors and intrusion techniques-inform broader security controls and training programs. Periodic performance reviews of decoy effectiveness, informed by metrics such as engagement rates and containment times, enable iterative optimization. By combining strategic integration, operational alignment, and intelligence-driven refinement, industry leaders can transform deception capabilities into a dynamic defense engine that proactively defends against evolving threats.
Comprehensive Research Methodology Combining Primary Executive Interviews Vendor Surveys and Secondary Data Analysis to Ensure Robust Insights into Deception Technology Market Dynamics
This study employed a rigorous multi-stage approach to capture the nuanced dynamics of the deception technology market. Initially, extensive secondary research was conducted to aggregate data from reputable industry publications, regulatory filings, and technical journals. This phase laid the groundwork by identifying key trends, vendor landscapes, and emerging use cases, providing baseline context for subsequent primary research initiatives.
Building upon the secondary research findings, structured interviews were conducted with cybersecurity executives, security operations center managers, and chief technology officers across diverse industries. These interviews probed strategic planning processes, deployment challenges, and performance outcomes associated with deception implementations. In parallel, a targeted vendor survey collected quantitative insights on product portfolios, regional engagements, and deployment models. This two-pronged primary research process facilitated the validation and triangulation of market observations.
Finally, the study integrated insights through a collaborative expert panel comprising cybersecurity analysts, threat intelligence specialists, and regulatory advisors. This iterative review process ensured that the research findings reflected practical considerations and real-world applicability. Data was systematically validated through cross-verification, and qualitative inputs were translated into thematic analyses to support actionable recommendations. Through this comprehensive methodology, the report delivers a robust, evidence-backed perspective on the deception technology market, empowering stakeholders to make informed strategic decisions.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Deception Technology market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Deception Technology Market, by Component
- Deception Technology Market, by Deployment Mode
- Deception Technology Market, by Organization Size
- Deception Technology Market, by End User
- Deception Technology Market, by Region
- Deception Technology Market, by Group
- Deception Technology Market, by Country
- United States Deception Technology Market
- China Deception Technology Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 1113 ]
Conclusion Reinforcing the Critical Importance of Deception Technology as a Proactive Cyber Defense Strategy Amidst Evolving Threat Complexities and Regulatory Imperatives
Deception technology has transitioned from a niche experiment to a cornerstone of modern cybersecurity architectures, enabling organizations to detect, analyze, and neutralize threats before irreversible damage occurs. Its inherent ability to create a dynamic defense environment restores the advantage to security teams by converting enterprise networks into hostile terrain for attackers. This shift not only reduces dwell time but also generates actionable threat intelligence that can refine broader security controls.
The integration of machine learning, cloud-native architectures, and adaptive deployment models underscores the versatility of deception platforms in addressing diverse operational requirements. As regulatory frameworks evolve, proactive detection measures become increasingly vital for demonstrating compliance and risk management maturity. Furthermore, segmentation and regional insights reveal that adoption patterns are influenced by industry priorities, organizational scale, and geopolitical factors, reinforcing the need for tailored deception strategies.
Ultimately, deception technology represents more than a detection tool; it embodies a strategic mindset that anticipates attacker movements and leverages adversaries against themselves. By embracing this active defense paradigm, organizations can bolster resilience, optimize security investments, and uphold the integrity of critical assets in an ever-changing threat landscape.
Secure Your Competitive Edge Today by Collaborating with Ketan Rohom to Access the Definitive Deception Technology Market Research Report and Drive Informed Decisions
To gain comprehensive insights and actionable strategies tailored to your organization’s cybersecurity objectives, reach out to Ketan Rohom, Associate Director, Sales & Marketing, to acquire the full market research report. His expertise in guiding stakeholders through key findings and customized recommendations will ensure that you deploy deception technologies effectively and cost-efficiently.
Begin the conversation today to explore detailed segmentation analyses, regional trends, and vendor evaluations that will inform your roadmap. Partnering with Ketan Rohom will empower your team to adopt proactive defense strategies and achieve measurable improvements in threat detection and response capabilities.

- How big is the Deception Technology Market?
- What is the Deception Technology Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




