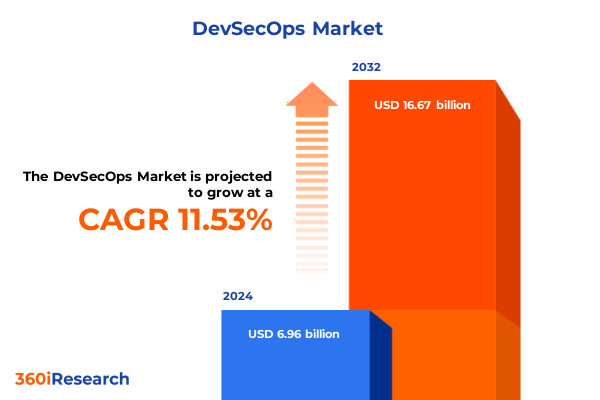
The DevSecOps Market size was estimated at USD 7.72 billion in 2025 and expected to reach USD 8.58 billion in 2026, at a CAGR of 11.61% to reach USD 16.67 billion by 2032.
Embedding Security by Design into Rapid DevOps Pipelines to Elevate Software Resilience and Accelerate Secure Development in Today’s Digital Age
DevSecOps has emerged as a critical discipline that embeds security controls and practices into every phase of the software development lifecycle, ensuring applications are resilient from the earliest code commits through deployment to production. By shifting security left and integrating policy-as-code approaches, development teams can identify vulnerabilities during the initial stages of coding rather than reacting to threats post-release, ultimately reducing risk and accelerating delivery cycles.
Contemporary DevSecOps strategies harness the power of artificial intelligence and machine learning to automate threat detection, prioritize remediation, and continuously adapt defenses to evolving attack patterns. Organizations leveraging AI-driven orchestration tools can flag misconfigurations and anomalous behaviors in real time, while emerging co-pilot models guide developers to remediate vulnerabilities with minimal manual intervention, streamlining workflows and boosting overall security posture.
Harnessing AI, Cloud-Native Architectures, and Automated Compliance to Transform DevSecOps Capabilities for Agile and Secure Software Delivery
As businesses contend with increasingly complex software supply chains and sophisticated cyber threats, DevSecOps has undergone transformative shifts driven by automation, cloud-native architectures, and centralized platforms. Advanced shift-left strategies now incorporate static application security testing, dynamic tests, and infrastructure-as-code scanning directly into CI/CD pipelines, enabling teams to detect and remediate issues early without slowing release velocity.
Concurrent with these automation advances, the industry is witnessing the rise of AI-driven security and compliance solutions that embed policies as code, enforce continuous drift detection, and apply remediation autonomously. As organizations codify security standards such as CIS Benchmarks, NIST frameworks, and GDPR requirements, automated configuration management ensures consistent governance across hybrid and multi-cloud environments.
Furthermore, centralized DevSecOps platforms are reshaping how teams secure modern software supply chains by unifying SBOM management, vulnerability analysis, and threat intelligence under a single pane of glass. This consolidation fosters closer collaboration between development and security teams, provides real-time visibility into application risk, and accelerates the adoption of application detection and response solutions as integral components of extended detection and response ecosystems.
Navigating the Cumulative Impacts of 2025 U.S. Tariff Policies on Global Supply Chains, Compliance Costs, and Technology Industry Dynamics
The culmination of multiple U.S. tariff actions in 2025 has intensified compliance complexities and driven material cost pressures across global technology supply chains. Section 232 levies on steel, aluminum, passenger vehicles, key auto parts, and copper scrap were enacted between March and August 2025, with rates ranging from 25 percent to 50 percent, prompting technology vendors to reevaluate sourcing strategies and inventory buffers to mitigate margin erosion.
Meanwhile, Section 301 tariffs on Chinese imports remain in effect through October 2025, with exclusions for certain solar manufacturing equipment and specific product lists extended by the USTR through August 2025. These rolling exclusions require organizations to track frequent policy updates and classify goods accurately to preserve preferential duty treatment, elevating the need for robust tariff engineering and classification processes.
Consequently, technology firms face rising indirect costs as extended compliance teams sustain additional headcount, external legal support, and tariff mitigation solutions. Supply chain leaders are pivoting to nearshoring and regional diversification to reduce exposure to high-tariff routes, while logistics partners redesign distribution networks to leverage trade agreements such as USMCA and U.S.-Japan frameworks for tariff relief.
Ultimately, U.S. trade interventions have not only elevated component and raw material costs but have also reshaped long-term supply chain resilience planning. Companies that proactively invest in scenario planning, data analytics for duty forecasting, and agile procurement strategies are better positioned to contain costs and maintain continuity despite ongoing policy uncertainty.
Unveiling Critical Market Segmentation Insights Shaping DevSecOps Adoption Across Offerings, Implementation Models, Organizational Scales, and Industry Verticals
The DevSecOps market can be viewed through its spectrum of offerings and solutions, where managed services and professional services support the deployment and operationalization of core security tools such as application security testing, cloud security and compliance, container and microservices security, identity and access management, incident detection and response, and secure software development. This duality ensures organizations can select both advisory expertise and turnkey solutions that align with their risk profiles and technical architectures.
Further segmentation by type reveals that compliance as code, infrastructure as code, policy as code, and security as code are distinct modalities through which organizations automate governance, enforce configuration standards, define security policies, and embed security checks directly into software artefacts. By translating abstract compliance requirements into executable code, teams achieve consistent enforcement and continuous validation without manual audits.
Deployment mode segmentation highlights the divergent needs of cloud and on-premises implementations. Cloud environments demand scalability and integration with native service-provider security tools, whereas on-premises deployments emphasize legacy compatibility, network isolation, and tailored configuration management. Organizations often adopt hybrid models that balance agility and control in complex enterprise estates.
Organization size segmentation differentiates between large enterprises-requiring multi-jurisdictional compliance, centralized governance, and high transaction throughput-and small and medium-sized enterprises, which prioritize rapid time-to-value, cost efficiency, and accessible managed services. Tailored offerings address the unique resource constraints and risk appetites of each cohort.
Industry vertical segmentation underscores the heterogeneity of security demands across banking, financial services, insurance, education, energy and utilities, government and public sector, healthcare and life sciences, IT and telecom, manufacturing, media and entertainment, and retail and e-commerce. Each vertical imposes specialized compliance frameworks and threat vectors, from HIPAA and NERC CIP to PCI DSS and intellectual property protections, shaping the selection and customization of DevSecOps capabilities.
This comprehensive research report categorizes the DevSecOps market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Offering
- Type
- Deployment Mode
- Organization Size
- Industry Vertical
Analyzing Regional Dynamics and Security Drivers Across the Americas, Europe Middle East Africa, and Asia-Pacific DevSecOps Ecosystems
In the Americas, maturity in cloud adoption and established federal cybersecurity mandates drive widespread integration of security into DevOps lifecycles. Organizations benefit from comprehensive zero trust frameworks, supplier consolidation, and alignment with procurement policies that reward security-by-design. The region’s robust venture capital ecosystem also fuels innovation in automated compliance and AI-powered threat detection.
In Europe, the Middle East, and Africa, regulatory catalysts such as GDPR enforcement, the EU Cyber Resilience Act, and the NIS2 Directive have elevated the imperative for continuous compliance and security posture monitoring. Fragmented regulatory environments across EMEA create both complexity and opportunity, leading enterprises to adopt unified platforms that deliver end-to-end visibility and accommodate diverse data sovereignty and localization requirements.
Across Asia-Pacific, rapid digital transformation initiatives, government programs for cloud infrastructure security, and domestic sovereignty policies are accelerating DevSecOps uptake. Markets like Singapore, Australia, and Japan report strong adoption among financial services and technology sectors, while emerging economies leverage cloud-native security to leapfrog legacy architectures. The region’s emphasis on near-real-time compliance with evolving cybersecurity standards positions APAC as a fertile ground for AI-driven and agentic security solutions.
This comprehensive research report examines key regions that drive the evolution of the DevSecOps market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Leading DevSecOps Innovators Driving Integration of AI, Automation, and Secure Software Tools to Strengthen Software Supply Chain Defenses
Leading DevSecOps innovators are enhancing platform intelligence and developer productivity through seamless integrations, intelligent automation, and AI-native architectures. GitLab’s Duo Vulnerability Resolution and Secret Push Protection automate remediation by generating merge requests and blocking inadvertent credential exposure, thereby reducing manual effort and accelerating secure code delivery.
Similarly, Snyk’s AI Trust Platform embeds agentic AI workflows that discover assets, prioritize vulnerabilities with contextual analysis, and autonomously generate fixes within the developer’s IDE. By unifying visibility, policy enforcement, and remediation, the platform fosters secure collaboration between developers and security engineers at scale.
Palo Alto Networks and Okta’s expanded partnership exemplifies the fusion of identity and network security with AI-driven threat detection. Their integrations between Okta Workforce Identity, Prisma Access Browser, and Cortex XSIAM facilitate context-aware access controls and automated response actions, reinforcing zero trust postures for hybrid work environments.
Contrast Security is pioneering the integration of Application Detection and Response into the extended detection and response ecosystem, filling critical gaps at the application layer. Its ADR solutions correlate runtime telemetry with threat intelligence to detect and remediate vulnerabilities in production, ensuring comprehensive protection across both build-time and run-time phases.
This comprehensive research report delivers an in-depth overview of the principal market players in the DevSecOps market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- 4ARMED Limited
- Amazon Web Services, Inc.
- Aqua Security Software Ltd
- Broadcom Inc.
- Checkmarx Ltd.
- Contrast Security, Inc.
- Copado, Inc
- CYBERARK SOFTWARE LTD
- Entersoft Information Systems Pvt Ltd.
- Gitlab Inc.
- Google by Alphabet Inc.
- International Business Machines Corporation
- Microsoft Corporation
- OpenText Corporation
- Palo Alto Networks, Inc.
- Progress Software Corporation
- Qualys, Inc.
- Rapid7, Inc.
- Snyk Limited
- Sonatype Inc.
- Synopsys, Inc.
- Tenable, Inc.
- Trend Micro Incorporated
Actionable Strategies for Technology Leaders to Optimize DevSecOps Practices, Enhance Security Posture, and Foster Collaborative Risk Management Cultures
Technology leaders should cultivate an AI-first security mindset by investing in automation tools that elevate shift-left practices, enforce policy as code, and enable autonomous remediation workflows. This approach empowers developers to address vulnerabilities within their natural workflows, freeing security teams to focus on orchestrating risk management strategies rather than manual testing.
Organizations must also prioritize centralized DevSecOps platforms that deliver unified visibility into software supply chains, integrate SBOM and threat intelligence, and harmonize compliance across hybrid estates. By adopting a single pane of glass for security operations, teams can reduce tool sprawl, streamline incident response, and foster cross-functional collaboration.
To mitigate ongoing trade policy uncertainties and tariff impacts, supply chain executives should implement flexible sourcing strategies, diversify vendor portfolios, and embed tariff engineering capabilities into procurement processes. Scenario planning and data analytics will be instrumental in anticipating cost fluctuations and ensuring resilience in critical component supply chains.
Finally, embedding a culture of continuous learning through developer security training, cross-team workshops, and threat-driven simulations will accelerate DevSecOps maturity. Empowered by metrics-driven insights and executive sponsorship, organizations can align business objectives with security imperatives, transforming security from a gatekeeper into a strategic enabler.
Overview of Research Methodology Employing Expert Interviews, Secondary Analysis, and Data Triangulation for Comprehensive DevSecOps Market Insights
The research underpinning this report combines extensive secondary analysis of industry white papers, vendor briefings, technical blogs, and regulatory publications with primary interviews of C-level executives, DevSecOps practitioners, and supply chain specialists. This dual approach ensured a holistic understanding of both strategic drivers and operational realities.
Data triangulation was employed to validate findings against multiple sources, including trade policy announcements, technology vendor roadmaps, and threat intelligence reports. Segmentation frameworks were iteratively refined through expert workshops, ensuring that the dimensions of offering type, deployment mode, organization size, and industry vertical accurately reflect market needs and adoption patterns.
Quantitative insights were augmented by real-world case studies illustrating best practices in AI-driven remediation, cloud-native security deployments, and tariff-mitigation strategies. Each case study was peer-reviewed by independent subject matter experts to confirm technical viability and business impact.
The final analysis was subjected to an internal quality assurance process that included methodological audits, data integrity checks, and consistency reviews across chapters. This rigorous approach guarantees that the report’s conclusions are grounded in verifiable evidence and industry expertise.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our DevSecOps market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- DevSecOps Market, by Offering
- DevSecOps Market, by Type
- DevSecOps Market, by Deployment Mode
- DevSecOps Market, by Organization Size
- DevSecOps Market, by Industry Vertical
- DevSecOps Market, by Region
- DevSecOps Market, by Group
- DevSecOps Market, by Country
- United States DevSecOps Market
- China DevSecOps Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1272 ]
Concluding Perspectives on the DevSecOps Evolution and Strategic Imperatives to Secure Software Development in a Rapidly Changing Threat Landscape
The evolution of DevSecOps continues to redefine software delivery by embedding security as a fundamental component of agile development. As AI automation, cloud-native architectures, and centralized platforms converge, organizations have unprecedented opportunities to accelerate time-to-market while maintaining robust security postures.
By proactively navigating the cumulative impacts of U.S. tariffs, leveraging nuanced segmentation strategies, and adopting region-specific approaches, enterprises can build resilient supply chains and secure their digital transformation journeys. The convergence of innovative technology vendors and actionable leadership recommendations provides a clear blueprint for embedding security deep into every aspect of the software lifecycle.
Connect with Associate Director Ketan Rohom to Access Comprehensive DevSecOps Market Research and Empower Your Organization with Strategic Insights
Engaging with this report will equip your organization with the actionable intelligence needed to strengthen software security, streamline DevSecOps processes, and make informed strategic investments. To acquire the full DevSecOps market research report and discuss tailored solutions, please reach out to Ketan Rohom, Associate Director, Sales & Marketing, who will guide you through the insights and help you align these findings with your business objectives.

- How big is the DevSecOps Market?
- What is the DevSecOps Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




