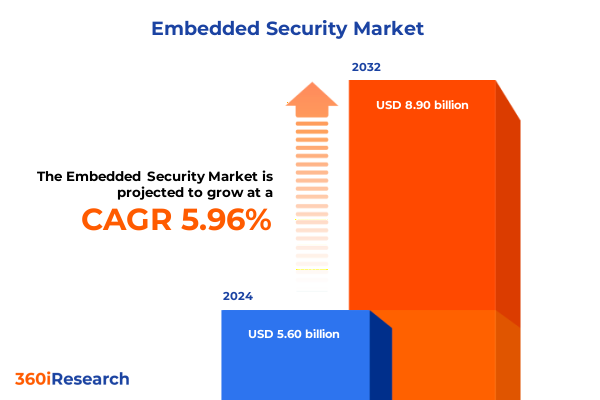
The Embedded Security Market size was estimated at USD 5.94 billion in 2025 and expected to reach USD 6.26 billion in 2026, at a CAGR of 5.94% to reach USD 8.90 billion by 2032.
Unveiling the Critical Role of Embedded Security Solutions in Safeguarding Complex Connected Systems Amid Rapid Technological Evolution
Embedded security has transitioned from a specialized niche to an indispensable foundation for modern technology architectures. As connected devices proliferate across industrial, consumer, and mission-critical environments, the imperative for robust on-board security measures has never been greater. Today’s embedded systems must address an expanding threat landscape that includes sophisticated cyberattacks targeting firmware, secure element exploitation, and supply chain manipulations. In this context, stakeholders across industries are racing to implement multi-layered security architectures that start at the hardware root-of-trust and extend through secure processors, integration devices, and software elements.
With the convergence of Internet of Things, edge computing, and 5G communications, embedded security solutions are undergoing rapid evolution. Innovations in hardware security modules and secure enclave technologies are converging with advanced encryption protocols, multi-factor authentication, and machine learning-driven anomaly detection. This fusion creates a cohesive ecosystem in which hardware, hybrid integration, and software layers collaborate seamlessly to protect sensitive data and prevent unauthorized access. As organizations pursue digital transformation, a nuanced understanding of these developments is crucial for designing resilient, future-proof systems.
Exploring the Transformative Shifts Driving Embedded Security Innovation Including AI Integration and Converging Hardware-Software Ecosystems
The embedded security landscape is witnessing transformative shifts driven by advancements in artificial intelligence, the democratization of secure element integration, and the blurring of traditional hardware-software boundaries. AI and machine learning have moved from peripheral add-ons to integral components of threat detection frameworks, empowering devices to adaptively respond to novel attack vectors in real time. Simultaneously, secure processors that combine cryptographic acceleration with tamper-resistant packaging are unlocking new performance thresholds while reducing integration complexity.
Moreover, the proliferation of hybrid solutions that marry hardware security modules with software-based policy engines is redefining how security is architected at the edge. Integration devices now incorporate programmable secure enclaves, enabling secure boot, firmware attestation, and runtime integrity verification without compromising system performance. As a result, vendors are collaborating with open-source communities to standardize security protocols and accelerate time-to-market, fostering a more cohesive and interoperable ecosystem. These shifts underscore a broader trend: security is no longer an afterthought but a core design principle woven into every layer of embedded computing.
Assessing How the 2025 United States Tariffs Are Reshaping Embedded Security Supply Chains Manufacturing Costs and Strategic Partnerships
The implementation of additional tariffs on imported semiconductors and security modules into the United States in early 2025 has introduced new complexities across global supply chains. Components historically sourced from leading manufacturers in Asia have experienced pronounced cost escalations, prompting original equipment manufacturers to reassess supplier portfolios and explore domestic production incentives. This realignment has accelerated investments in North American and European fabrication facilities that prioritize security-certified processes, albeit with longer lead times and higher capital expenditure.
Furthermore, the tariff landscape has catalyzed strategic partnerships between chip suppliers, systems integrators, and contract manufacturers aimed at mitigating the financial impact through shared engineering resources and volume commitments. These collaborations are fostering the development of modular security subsystems that can be assembled locally, reducing dependency on cross-border logistics while preserving stringent compliance with government regulations. Consequently, organizations are revisiting their risk management frameworks to incorporate tariff volatility scenarios, ensuring that project budgets and delivery timelines remain resilient in the face of evolving trade policies.
Deriving Key Insights from Multi-Level Segmentation of Embedded Security Markets Spanning Hardware Hybrid and Software Domains
A nuanced analysis of the embedded security market reveals distinct trends across security type, device architecture, and application domain. When examining security type, hardware-centric solutions encompass specialized modules, secure elements, and trusted platform modules that anchor a device’s trustchain. These components are complemented by hybrid offerings, which integrate secure processors and connectivity hubs to enable dynamic policy enforcement. On the software front, advanced encryption libraries, authentication frameworks, firewalls, and antivirus engines deliver adaptable layers of defense that can be updated in the field to counter emerging threats.
Device type segmentation highlights an equally complex tapestry of requirements. Field-programmable gate arrays, whether large, medium, or small in scale, afford designers flexibility in customizing security logic, while microcontrollers across 8-, 16-, and 32-bit architectures balance cost and performance for targeted applications. Secure elements, available in both contact and contactless form factors, serve niche use cases ranging from secure payment terminals to identity verification badges. At the other end of the spectrum, systems on chip that house application processors and microprocessors integrate comprehensive security suites directly within high-performance computing platforms, catering to advanced industrial IoT and telecommunications deployments.
Application segmentation underscores the breadth of embedded security adoption. In aerospace and defense, avionics navigation and surveillance systems demand ironclad integrity and low latency. The automotive realm is split between electric vehicles optimizing battery management security and traditional vehicles securing telematics. Consumer electronics range from home appliances with embedded trust anchors to smartphones and wearables that require continuous secure authentication. Healthcare applications extend from medical devices under stringent regulatory oversight to telemedicine platforms safeguarding patient data. Industrial IoT installations in manufacturing execution systems, robotics, and SCADA prioritize real-time monitoring, while retail ecosystems secure point-of-sale and supply chain management. Smart home environments blend energy management, security systems, and lighting automation under unified control, and telecom networks transition from 4G/3G frameworks to burgeoning 5G architectures that embed native security protocols.
This comprehensive research report categorizes the Embedded Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Security Type
- Device Type
- Application
Analyzing Regional Dynamics in the Embedded Security Market Across Americas EMEA and Asia-Pacific to Uncover Growth and Adoption Patterns
Regional dynamics in the embedded security market are characterized by distinct growth drivers, regulatory environments, and ecosystem maturity. In the Americas, government initiatives to bolster cybersecurity resilience are complemented by robust research collaborations between academic institutions and technology vendors. The United States leads in developing security standards for emerging applications such as connected vehicles and critical infrastructure, while Latin American markets show increasing adoption of secure payment terminals and IoT solutions in agriculture.
Across Europe, Middle East & Africa, a diverse regulatory mosaic shapes market behavior. The European Union’s stringent data protection and cryptographic requirements have spurred widespread integration of advanced encryption modules in consumer and industrial devices. In parallel, Middle Eastern nations are investing heavily in smart city frameworks, integrating security at the edge to protect critical public services. African markets, though nascent, are witnessing rapid uptake of contactless secure elements in finance and telecommunications, driven by the expansion of mobile money platforms.
Asia-Pacific continues to be the largest and most dynamic market, propelled by domestic chipset development in China, Japan’s leadership in secure semiconductor process technologies, and South Korea’s drive toward secure 5G rollout. Southeast Asian nations are emerging as key manufacturing hubs for secure modules, while Australia and New Zealand emphasize cyber resilience in regional defense initiatives. Each sub-region presents unique opportunities for security solution providers to tailor offerings that align with local regulatory frameworks and supply chain infrastructures.
This comprehensive research report examines key regions that drive the evolution of the Embedded Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Leading Embedded Security Innovators and Strategic Collaborations That Are Shaping Competitive Dynamics and Technology Roadmaps
Leading players in the embedded security domain are distinguished by their innovation pipelines, strategic alliances, and commitment to open standards. Major semiconductor manufacturers are expanding their portfolios to include integrated secure enclaves and cryptographic accelerators, while startups are differentiating through specialized firmware attestation and tamper-detection solutions. Partnerships between device OEMs and cloud service providers are becoming more prevalent, resulting in cohesive end-to-end security stacks that span from edge hardware to centralized analytics.
Moreover, collaborative engagement with industry consortia and standards bodies is driving consensus on secure boot protocols, trusted execution environments, and post-quantum cryptography readiness. This alignment accelerates interoperability across vendor ecosystems and reduces integration friction for system builders. Companies are also investing in localized engineering centers to navigate regional compliance landscapes more effectively, ensuring that their products meet continent-specific requirements without extensive requalification efforts.
This comprehensive research report delivers an in-depth overview of the principal market players in the Embedded Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Advantech Co. Ltd.
- BAE Systems Plc
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems Inc.
- IBM Corporation
- IDEMIA
- Infineon Technologies AG
- Karamba Security Ltd.
- Lattice Semiconductor Corporation
- Microchip Technology Inc.
- Microsoft Corporation
- NXP Semiconductors
- Palo Alto Networks Inc.
- Qualcomm Technologies Inc.
- Rambus Incorporated
- Renesas Electronics Corporation
- RunSafe Security Inc.
- Samsung Electronics Co.
- Secure-IC S.A.S.
- STMicroelectronics N.V.
- Synopsys Inc.
- Texas Instruments Incorporated
- Thales Group
- Utimaco
Strategic Roadmap of Actionable Recommendations for Industry Leaders to Enhance Security Posture and Capitalize on Emerging Embedded Security Trends
Industry leaders must adopt a proactive stance to navigate the rapidly evolving embedded security landscape. Executives should prioritize the establishment of a unified security framework that integrates hardware, hybrid, and software layers from the earliest design phases. By conducting regular threat modeling exercises and red team assessments, organizations can identify potential vulnerabilities before deployment and streamline mitigations through firmware updates or component revisions.
In parallel, cultivating strategic relationships with trusted suppliers and integration partners will help balance cost pressures from tariffs and supply chain disruptions. Leaders should explore co-development agreements that incentivize volume commitments and joint innovation roadmaps. Investing in workforce capabilities is equally critical: cross-functional training programs that bridge hardware design, cryptography, and secure software development will foster a culture of security-first thinking across the product lifecycle.
Finally, maintaining active participation in industry alliances and contributing to open-source security projects will accelerate standardization and interoperability. By championing common security protocols and aligning with emerging regulatory frameworks, organizations can reduce time-to-market, simplify certification processes, and enhance consumer confidence.
Comprehensive Research Methodology Employing Qualitative Stakeholder Interviews Quantitative Data Analysis and Rigorous Validation Processes
This research employs a multi-pronged methodology that combines primary and secondary data sources, expert interviews, and rigorous validation techniques. Quantitative data was collected through surveys and market analytics platforms to map out device shipments, technology adoption rates, and supply chain footprints. Concurrently, qualitative insights were gathered from in-depth interviews with security architects, systems integrators, and regulatory authorities to contextualize market drivers and pain points.
To ensure robustness, all insights were cross-referenced against publicly available technical white papers, patent filings, and government policy documents. Statistical analysis, including trend extrapolation and variance testing, was applied to identify significant patterns across security type, device architecture, and application verticals. Finally, a validation workshop with cross-industry stakeholders was conducted to stress-test preliminary findings and refine strategic imperatives, ensuring that the final deliverables embody both analytical rigor and real-world applicability.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Embedded Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Embedded Security Market, by Security Type
- Embedded Security Market, by Device Type
- Embedded Security Market, by Application
- Embedded Security Market, by Region
- Embedded Security Market, by Group
- Embedded Security Market, by Country
- United States Embedded Security Market
- China Embedded Security Market
- Competitive Landscape
- List of Figures [Total: 15]
- List of Tables [Total: 3021 ]
Concluding Perspectives on the Evolution of Embedded Security Solutions and Strategic Imperatives for Stakeholders to Navigate Future Challenges
As embedded security solutions become the cornerstone of reliable and resilient connected systems, stakeholders must remain vigilant in adapting to emerging threats and technological advances. The integration of hardware root-of-trust mechanisms with agile software defenses is poised to deliver unprecedented levels of assurance, while tariff-driven supply chain realignments underscore the need for diversified sourcing strategies.
Looking ahead, the convergence of AI-powered anomaly detection, secure edge computing, and post-quantum cryptography will set new benchmarks for security performance and interoperability. By leveraging the insights and recommendations outlined in this executive summary, decision-makers can devise strategic roadmaps that balance innovation with compliance, cost efficiency with robust defense, and regional market demands with global scalability. The imperative is clear: security must be a fundamental design principle, not an afterthought, in every embedded system moving forward.
Take the Next Step: Engage with Ketan Rohom to Unlock Critical Embedded Security Market Insights Through a Comprehensive Research Report
For decision-makers seeking to deepen their understanding of embedded security market dynamics and capitalize on emerging opportunities, Ketan Rohom, Associate Director, Sales & Marketing, stands ready to provide personalized guidance. Engaging with Ketan Rohom will grant access to an in-depth research report that delves into critical market trends, competitive benchmarking, and strategic imperatives. The report offers comprehensive analysis across security types, device categories, application verticals, and regional nuances, underpinned by a rigorous methodology and expert interviews. By connecting with Ketan Rohom, organizations can align their product roadmaps with evolving regulatory landscapes, anticipate the impact of supply chain disruptions, and identify ideal partners for innovation. Reach out to schedule a customized briefing or request a detailed proposal that will equip your executive team with actionable intelligence, empowering your organization to stay ahead in the rapidly evolving embedded security arena.

- How big is the Embedded Security Market?
- What is the Embedded Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




