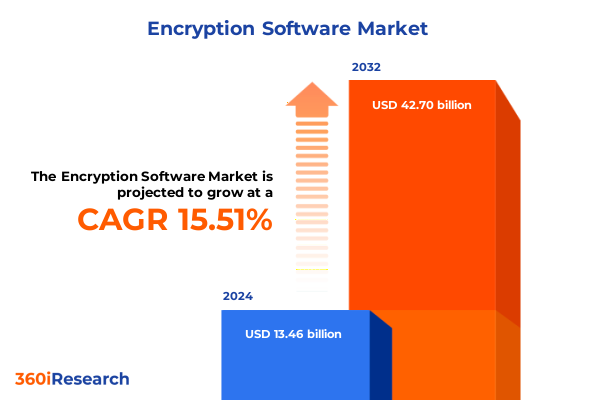
The Encryption Software Market size was estimated at USD 15.43 billion in 2025 and expected to reach USD 17.69 billion in 2026, at a CAGR of 15.64% to reach USD 42.70 billion by 2032.
Unveiling the Pivotal Role of Encryption Software in Safeguarding Data Integrity, Enhancing Regulatory Compliance, and Driving Trust in Complex Digital Ecosystems
In an era defined by exponential data growth and increasingly sophisticated cyber threats, encryption software has emerged as a foundational pillar for safeguarding digital assets. Organizations of every scale and sector are confronting relentless attacks that exploit vulnerabilities in data storage, transmission, and processing. Against this backdrop, encryption solutions-ranging from established symmetric algorithms to advanced asymmetric key management-have become indispensable tools for protecting confidentiality, ensuring integrity, and bolstering overall cybersecurity posture.
As regulatory frameworks continue to evolve, compliance requirements such as the General Data Protection Regulation, the California Consumer Privacy Act, and industry-specific mandates underscore the necessity of robust encryption measures. At the same time, rapid technological advancements-encompassing cloud computing architectures, the proliferation of Internet of Things devices, and emerging quantum computing capabilities-are reshaping the parameters of data protection. Consequently, leaders are seeking encryption platforms that seamlessly integrate with complex IT environments while delivering both performance and future resilience. This executive summary provides a strategic overview of the forces driving market developments, highlights critical shifts in the competitive landscape, and offers refined insights to support informed decision-making in the encryption software domain.
Exploring the Dramatic Technological and Regulatory Transformations Redefining the Encryption Software Ecosystem Across Industry Verticals and Infrastructure
Over the past few years, the encryption software market has undergone transformative shifts driven by advances in algorithmic capabilities, heightened regulatory scrutiny, and the urgent demand for zero-trust architectures. Organizations are moving away from traditional perimeter-centric defenses toward data-centric security models, embedding encryption at every stage of data lifecycle-from creation and storage to processing and sharing. This pivot is underscored by the adoption of homomorphic encryption techniques that enable analytics on encrypted datasets, as well as the rising prominence of quantum-resistant cryptographic algorithms designed to future-proof sensitive information against next-generation threats.
Simultaneously, emerging regulatory initiatives are recalibrating the encryption landscape. Standardization bodies are issuing updated cryptographic recommendations, while regional legislation is mandating stronger data handling protocols. Enterprises are responding by integrating advanced key management systems with artificial intelligence-powered anomaly detection to automate policy enforcement and rapidly identify potential breaches. Moreover, collaborative efforts between technology vendors and regulatory authorities have spurred the development of interoperability frameworks, ensuring encryption solutions can traverse diverse IT infrastructures with minimal friction. Together, these technological and regulatory forces are reshaping market dynamics and redefining competitive differentiation within the encryption software sector.
Assessing How United States Tariff Measures Announced in 2025 Are Reshaping Costs, Supply Chains, and Strategic Priorities within the Encryption Software Sector
In 2025, United States tariff policies have exerted a cumulative influence on the encryption software value chain, particularly affecting hardware security modules, integrated encryption appliances, and ancillary components. Tariffs imposed on imported security-certified processors have increased the landed cost of hardware accelerated encryption platforms, compelling solution providers to reevaluate their supply chain strategies. These measures have translated into higher unit costs for on-premises deployments and have prompted some vendors to accelerate partnerships with domestic manufacturers to mitigate rate hikes.
Beyond hardware, certain software licensing classifications have also been subject to revised duties, influencing total cost of ownership calculations for enterprise clients. Providers have adapted by revising pricing structures and offering subscription-based cloud encryption alternatives that shift capital expenses to operational models. As a result, organizations are increasingly considering hybrid architectures to offset tariff-driven cost increases while maintaining compliance and performance standards. Taken together, US tariff adjustments in 2025 have catalyzed a strategic realignment in procurement policies, spurring both innovation in localized manufacturing and a recalibration of deployment preferences among end users.
Unlocking Market Insights Through Detailed Analysis of Encryption Technologies, Enterprise Adoption, and Deployment Models Across Diverse End Users
A granular view of market segmentation reveals critical nuances that shape adoption and investment strategies. When the market is examined based on encryption type, the study differentiates between asymmetric and symmetric solutions, uncovering distinct application patterns across data in transit versus data at rest. Asymmetric key infrastructures are increasingly leveraged for secure communications and identity management, whereas symmetric ciphers remain predominant for bulk data encryption in high-throughput environments.
Furthermore, the landscape diverges significantly when analyzed by organization size. Large enterprise environments often demand on-premises control and extensive customization, whereas Small and Medium Enterprise operations favor turnkey cloud-delivered encryption services to minimize upfront capital expenditure. Deployment mode insights indicate that cloud-native encryption is experiencing robust uptake, complemented by hybrid configurations that balance flexibility and security. Within cloud adoption, public environments are prized for scalability, while private cloud implementations are chosen for enhanced governance. Finally, end user profiles underscore that Banking, Financial Services and Insurance organizations lead in stringent encryption mandates, government entities prioritize national security standards, healthcare providers comply with patient privacy regulations, and Information Technology and Telecom sectors drive innovation in high-performance secure communications.
This comprehensive research report categorizes the Encryption Software market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Encryption Type
- Organization Size
- Deployment Mode
- End User
Comparative Regional Dynamics Highlighting Growth Drivers, Regulatory Environments, and Adoption Patterns of Encryption Software Across Global Markets
Regional dynamics offer a compelling lens on the global encryption software ecosystem. In the Americas, market momentum is fueled by robust hyperscale data center growth, evolving privacy legislation, and a rapid shift toward cloud-centric IT environments. North American organizations are at the forefront of integrating advanced key management practices, while Latin American markets exhibit growing demand for affordable cloud encryption services to comply with localized data sovereignty mandates.
Turning to the Europe, Middle East & Africa domain, heterogeneous regulatory landscapes-from GDPR enhancements in the European Union to digital resilience strategies in Middle Eastern economies-are propelling diverse encryption requirements. Multinational corporations operating across these geographies must navigate cross-border data transfer restrictions and tailor encryption deployments to meet both regional compliance and performance criteria. Meanwhile, the Asia-Pacific region is marked by accelerated digital transformation initiatives, substantial investments in 5G infrastructure, and local encryption standards that vary by country. These factors collectively drive adoption among telecom operators, financial institutions, and government agencies seeking to secure vast data streams in complex, high-growth markets.
This comprehensive research report examines key regions that drive the evolution of the Encryption Software market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Leading Encryption Software Providers to Illuminate Strategic Innovations, Competitive Differentiators, and Partnership Ecosystems Fueling Market Leadership
Industry leadership within the encryption software sector is increasingly defined by the ability to innovate across product portfolios, forge strategic alliances, and deliver seamless integration with broader security ecosystems. Leading providers differentiate through AI-powered key lifecycle automation, which reduces manual oversight and accelerates compliance assurance. Others emphasize quantum-safe research programs, positioning their road maps around future-proof cryptography that addresses potential vulnerabilities posed by quantum computing advances.
Competitive positioning also pivots on ecosystem engagements. Partnerships with hyperscalers and system integrators enable encryption vendors to embed their solutions within public cloud platforms and enterprise service bundles. Simultaneously, targeted acquisitions are consolidating specialized startups in areas such as homomorphic encryption, secure multi-party computation, and zero-trust network access. As a result, emerging challengers are capturing niche opportunities, while established incumbents seek to broaden their footprints through extended platform offerings and global support networks.
This comprehensive research report delivers an in-depth overview of the principal market players in the Encryption Software market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Amazon Web Services, Inc.
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Cryptomathic Ltd.
- CyberArk Software, Inc.
- Dell Technologies Inc.
- ESET spol. s r.o.
- F-Secure Corporation
- Fortinet, Inc.
- Google LLC
- Hewlett Packard Enterprise Company
- International Business Machines Corporation
- McAfee Corp
- Microsoft Corporation
- Oracle Corporation
- PKWARE, Inc.
- Proofpoint, Inc.
- Thales S.A.
- Trend Micro Incorporated
- Utimaco GmbH
- Venafi, Inc.
- VMware, Inc.
- WinMagic Inc.
Strategic Roadmap for Industry Executives to Capitalize on Emerging Encryption Trends, Mitigate Risks, and Cultivate Sustainable Competitive Advantages
Industry executives should prioritize a multifaceted security strategy that aligns with both current threat landscapes and anticipated technological shifts. Investing in quantum-resistant encryption algorithms today safeguards data against the inevitability of quantum decryption capabilities tomorrow. Concurrently, embedding encryption as a core component of a zero-trust framework ensures that every access request is continually validated and encrypted, minimizing the risk of lateral movement by threat actors.
Leaders must also cultivate interoperable encryption architectures that span cloud, hybrid, and on-premises environments, thereby providing the agility to shift workloads without compromising data protection. Proactively engaging with regulatory bodies and contributing to emerging standards enables organizations to influence policy directions and maintain compliance road maps. Finally, fostering strategic partnerships with hyperscale providers, telecommunications firms, and specialized integrators accelerates time-to-value, enabling enterprises to deploy end-to-end encryption solutions that are both resilient and scalable.
Comprehensive Overview of Rigorous Research Frameworks and Data Collection Methodologies Underpinning the Analysis of the Encryption Software Market
This research leverages a rigorous, dual-phased methodology to ensure comprehensive and balanced market insights. Primary research encompassed structured interviews with key stakeholders across vendor organizations, enterprise end users, and regulatory bodies to capture qualitative perspectives on technology adoption, competitive strategies, and policy impacts. Complementary secondary research included analysis of publicly available financial reports, patent filings, academic publications, and regulatory documentation to validate and enrich primary findings.
Quantitative data was synthesized using a bottom-up approach that reconciles segment-level insights with macroeconomic indicators and industry benchmarks. Data triangulation through multiple sources minimized bias and enhanced the reliability of the conclusions. Additionally, expert review panels were convened to scrutinize intermediate findings, ensuring alignment with real-world market conditions. This methodological rigor underpins the credibility of the analysis and supports the strategic recommendations provided herein.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Encryption Software market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Encryption Software Market, by Encryption Type
- Encryption Software Market, by Organization Size
- Encryption Software Market, by Deployment Mode
- Encryption Software Market, by End User
- Encryption Software Market, by Region
- Encryption Software Market, by Group
- Encryption Software Market, by Country
- United States Encryption Software Market
- China Encryption Software Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 954 ]
Synthesizing Market Trends, Strategic Implications, and Future Trajectories to Provide a Cohesive Perspective on the Encryption Software Landscape
The encryption software ecosystem stands at a critical juncture, shaped by technological breakthroughs, evolving regulatory landscapes, and shifting cost structures influenced by tariff policies. Across encryption types and deployment models, market participants are recalibrating strategies to address the dual imperatives of data security and operational efficiency. As organizations grapple with accelerating digital transformation, encryption has emerged as an essential enabler of trust, compliance, and competitive differentiation.
Looking ahead, the convergence of quantum-resistant technologies, AI-driven key management, and zero-trust principles will define the next phase of innovation. Strategic alliances, standardization efforts, and adaptive policy frameworks will further influence adoption trajectories. In this dynamic environment, decision-makers equipped with a nuanced understanding of market segmentation, regional trends, and supplier capabilities will be best positioned to harness the full potential of encryption software and safeguard their digital assets against present and future threats.
Secure Your Competitive Edge with Expert Insights – Contact Ketan Rohom for Exclusive Access to the Comprehensive Encryption Software Market Research Report
Leverage this comprehensive market research to stay ahead in a rapidly evolving encryption landscape. Engaging directly with an authoritative expert can provide deeper insights, tailored recommendations, and strategic foresight that drive impactful decisions. Ketan Rohom stands ready to guide your organization through the complexities of encryption technologies, regulatory shifts, and competitive dynamics. Connect today to secure your access to the full in-depth report and empower your team with actionable intelligence that shapes tomorrow’s security strategies

- How big is the Encryption Software Market?
- What is the Encryption Software Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




