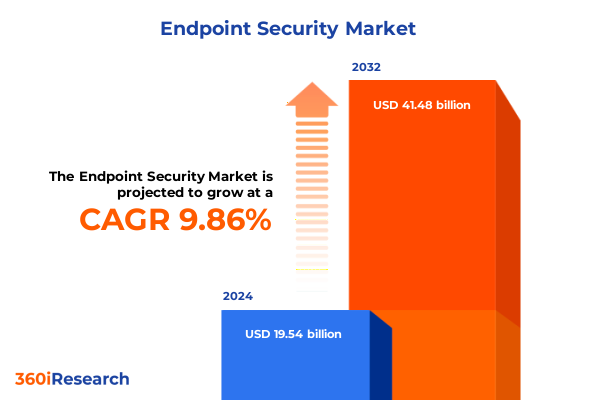
The Endpoint Security Market size was estimated at USD 21.32 billion in 2025 and expected to reach USD 23.31 billion in 2026, at a CAGR of 9.97% to reach USD 41.48 billion by 2032.
Exploring the Critical Role of Endpoint Security in Safeguarding Modern Enterprises Against Complex Threats and Emerging Cyber Challenges
Endpoint security has become the cornerstone of modern enterprise defense, evolving from simple antivirus solutions into a multifaceted shield against an ever-expanding array of cyber threats. As organizations confront sophisticated malware, zero-day exploits, and targeted ransomware campaigns, they must integrate a comprehensive set of services and software capabilities to protect each device operating within their network. Consequently, leaders must consider everything from consulting and implementation services to training and support, alongside advanced software tools encompassing antivirus and antimalware engines, encryption protocols, firewalls, and intrusion detection systems.
Moreover, the proliferation of diverse operating systems-most notably Android, iOS, and Windows-has introduced additional layers of complexity, demanding solutions that seamlessly adapt to mobile devices, desktops, and remote endpoints. At the same time, endpoint security no longer exists in isolation; it forms a critical component of broader risk management strategies that span endpoint device management across desktops, mobiles, and remote units, as well as network security disciplines addressing email defense, network access controls, and web protection. This convergence underscores the criticality of a unified approach that aligns tactical defenses with strategic resilience.
By acknowledging the imperative for a holistic stance on endpoint security, stakeholders can anticipate how evolving threat vectors will shape future investments. This introduction sets the stage for an in-depth exploration of transformative shifts, tariff impacts, segmentation dynamics, regional insights, competitive landscapes, and data-driven recommendations-offering a roadmap to navigate the endpoint security domain with authority and confidence.
Uncovering the Transformative Shifts Rapidly Redefining the Endpoint Security Landscape Through Technological Innovation, Strategic Adoption, and Collaboration
The endpoint security landscape has undergone a remarkable transformation, propelled by rapid technological advances in artificial intelligence, machine learning, and behavioral analytics. Simultaneously, organizations have shifted from traditional reactive defenses to proactive threat hunting and real-time response frameworks, embedding security deeply into application workflows and device management protocols. This transformative journey has not only accelerated detection and response efficiency but has also fostered tighter collaboration between security operations teams and broader IT functions.
In parallel, the rise of software-driven architectures has propelled the adoption of cloud-native security services alongside on-premises deployments, granting enterprises the flexibility to scale protections dynamically according to workload demands and compliance imperatives. As a result, vendors have diversified their portfolios to include consulting expertise, system integration, and continuous training, ensuring that technical capabilities translate effectively into operational resilience. Consequently, forward-looking organizations are now focusing on predictive analytics and threat intelligence sharing, creating a unified front against emerging cyber adversaries.
This section unpacks how these transformative shifts are reshaping the endpoint security ecosystem. It examines the integration of advanced prevention techniques, collaborative frameworks, and emerging deployment models, revealing how businesses are recalibrating their security postures to stay ahead of threats. By understanding these critical inflection points, decision-makers can prioritize strategic investments that bolster defenses and cultivate long-term agility.
Analyzing the Far-Reaching Cumulative Impact of 2025 United States Tariffs on Endpoint Security Supply Chains, Costs, and Strategic Resilience
The imposition of new United States tariffs in 2025 has exerted a cumulative impact on the endpoint security market, particularly affecting hardware-dependent solutions and cross-border service delivery costs. As customs duties on imported components increased, enterprises faced higher expenses for specialized security appliances, encrypted storage modules, and intrusion detection hardware. Consequently, procurement strategies have pivoted toward optimized sourcing, favoring domestic manufacturing where feasible and renegotiating vendor contracts to mitigate tariff-driven price escalations.
In addition, service providers have adapted their offerings by bundling remote training and support services with core consulting and implementation packages, delivering greater value that offsets equipment cost pressures. This strategic rebalancing has simultaneously spurred innovation in lightweight, software-centric solutions that reduce reliance on tariff-impacted physical devices. Furthermore, organizations have intensified their focus on cloud-based deployments to sidestep import barriers, leveraging elastic infrastructure to maintain robust security postures without bearing excessive upfront capital expenditures.
Hence, understanding the ripple effects of 2025 tariffs on endpoint security demands a nuanced perspective that accounts for supply chain adjustments, pricing recalibrations, and evolving deployment preferences. By dissecting these dynamics, stakeholders can craft resilient procurement frameworks and anticipate vendor strategies poised to navigate the altered economic landscape.
Delivering Key Segmentation Insights to Navigate the Endpoint Security Market Across Offerings, Operating Systems, Applications, End Users, Deployment, and Organization Sizes
Insightful market segmentation reveals how enterprises tailor endpoint security solutions according to specific requirements and organizational contexts. From a offerings standpoint, the landscape bifurcates into a comprehensive suite of services-spanning expert consulting engagements, system implementation projects, and ongoing training and support-and a versatile array of software solutions that include core antivirus and antimalware engines, robust encryption tools, next-generation firewalls, and intrusion detection systems designed for real-time threat identification.
Turning to operating system considerations, the market must address the unique security paradigms of Android’s open ecosystem, iOS’s controlled architecture, and Windows’ enterprise-centric feature set, each demanding bespoke policy frameworks and threat modeling approaches. At the application layer, endpoint security intersecting with device management functions-encompassing desktop administration, mobile device oversight, and remote device orchestration-interlocks with network security measures focused on email protection, network access governance, and web traffic inspection.
End-user classifications further nuance deployment strategies, as sectors such as banking, financial services and insurance, education, energy, government and defense, healthcare and life sciences, telecommunications, manufacturing, and retail each present distinct regulatory and threat profiles. Deployment preferences bifurcate between cloud-based flexibilities and on-premises control, while organization size delineates the contrast in resource availability and risk tolerance between large enterprises and small-to-medium enterprises. Together, these segmentation dimensions provide a granular blueprint for crafting tailored security architectures and go-to-market approaches.
This comprehensive research report categorizes the Endpoint Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Offerings
- Operating System
- Application
- End User
- Deployment
- Organization Size
Illuminating Comprehensive Regional Insights into Endpoint Security Trends, Challenges, and Opportunities Across Americas, Europe, Middle East & Africa, and Asia-Pacific
Regional dynamics exert a profound influence on endpoint security adoption and vendor strategies across the globe. In the Americas, regulatory initiatives and high-profile data breaches have accelerated demand for integrated solutions that combine preventative and detective capabilities. Organizations in this region increasingly favor cloud-based models for rapid deployment, augmented by localized support networks that ensure compliance with stringent privacy frameworks.
Meanwhile, Europe, the Middle East, and Africa present a diverse tapestry of market maturity levels, with Western Europe emphasizing stringent GDPR-aligned encryption standards and real-time monitoring, while emerging economies throughout the Middle East and Africa seek cost-effective, managed service offerings to address resource constraints and evolving threat landscapes. This heterogeneous environment has prompted vendors to tailor modular solutions that adapt to varying regulatory regimes and infrastructure readiness.
In Asia-Pacific, rapid digital transformation across industries such as finance, healthcare, and manufacturing has spurred significant investments in both software-centric security platforms and strategic consulting services. Localized threat intelligence and integration with regional cloud providers have become critical differentiators, enabling organizations to balance centralized management with nuanced cultural and compliance considerations. Hence, regional insights shape both product roadmaps and service delivery models, guiding stakeholders toward contextually relevant solutions.
This comprehensive research report examines key regions that drive the evolution of the Endpoint Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Key Companies Driving Innovation and Competitive Dynamics in Endpoint Security Through Advanced Solutions, Partnerships, and Strategic Investments
The competitive landscape in endpoint security is defined by a confluence of established technology powerhouses and agile specialists, each leveraging unique strengths to capture market relevance. Leading service integrators emphasize end-to-end consultancy, embedding best practices in risk management and compliance frameworks into every engagement, while software innovators distinguish themselves through advanced machine learning algorithms and automated threat hunting capabilities.
Strategic partnerships have emerged as a hallmark of success, with vendors aligning with cloud infrastructure providers, managed security service firms, and academic research institutions to accelerate feature development and threat intelligence sharing. This collaborative ethos drives continuous refinement of endpoint security solutions, ensuring that defensive mechanisms evolve in lockstep with attacker methodologies. Consequently, the most influential companies are those that balance depth of technical innovation with breadth of service delivery, enabling clients to orchestrate cohesive security ecosystems across diverse environments.
Moreover, mergers and acquisitions continue to reshape the industry, as larger entities integrate niche technology providers to fill capability gaps and expand their global footprints. For decision-makers, tracking these corporate developments is crucial to understanding future product roadmaps and potential shifts in support models, equipping stakeholders with the foresight necessary to align investments with credible, future-proof partners.
This comprehensive research report delivers an in-depth overview of the principal market players in the Endpoint Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Accenture PLC
- AO Kaspersky Lab
- BeyondTrust Corporation
- Cisco Systems, Inc.
- CrowdStrike, Inc.
- Cylance, Inc. by BlackBerry Limited
- ESET, spol. s r.o.
- Forcepoint LLC
- Fortinet, Inc
- Gen Digital Inc.
- Intel Corporation
- International Business Machines Corporation
- Ivanti Software, Inc.
- Microsoft Corporation
- Morphisec Ltd.
- Palo Alto Networks, Inc.
- Quest Software Inc.
- S.C. BITDEFENDER S.R.L.
- SentinelOne, Inc.
- Sophos Ltd.
- Trend Micro Incorporated
- Webroot, Inc. by Open Text Corporation
- WithSecure Corporation
- Xcitium, Inc.
- Zoho Corporation Pvt. Ltd.
Providing Actionable Recommendations for Industry Leaders to Enhance Endpoint Security Posture Through Strategic Investments, Collaboration, and Operational Excellence
To fortify endpoint defenses amid evolving threats and economic headwinds, industry leaders must embark on a multifaceted action plan. First, they should allocate resources toward predictive analytics capabilities that harness machine learning to preempt emerging attack vectors, thereby reducing incident response times and minimizing potential business disruption. Alongside this, integrating security training and simulation exercises tailored to diverse user profiles ensures that human risk factors are addressed proactively, reinforcing technical safeguards with informed employee behaviors.
Furthermore, organizations should cultivate strategic alliances with specialized vendors and research consortia, leveraging shared threat intelligence to stay abreast of adversarial tactics. This collaborative network reduces duplication of effort while amplifying collective defense efficacy. At the same time, adopting a hybrid deployment strategy that balances the scalability of cloud-based models with the control of on-premises infrastructures enables enterprises to optimize cost-effectiveness without compromising core security requirements.
Finally, operational excellence demands continuous measurement and refinement of security postures through metrics and audit frameworks aligned with industry standards. By establishing clear governance structures and accountability mechanisms, leaders can ensure sustained alignment between security objectives and broader business goals, driving measurable improvements and reinforcing resilience against future threat landscapes.
Detailing the Rigorous Research Methodology Employed to Deliver Comprehensive Endpoint Security Market Analysis Through Systematic Data Collection and Expert Validation
This research synthesizes a rigorous methodological framework designed to deliver comprehensive insights into the endpoint security market. Primary data collection involved in-depth interviews with cybersecurity practitioners, IT decision-makers, and vendor executives, ensuring a balanced perspective across solution providers and end-user organizations. Complementing these qualitative inputs, secondary research encompassed an extensive review of regulatory filings, technical whitepapers, and threat intelligence reports, creating a foundation of credible, up-to-date data.
Quantitative data triangulation further strengthened the analysis, as historical deployment patterns and adoption rates were cross-verified against expert forecasts and industry benchmarks. Throughout the process, a multi-stage validation protocol engaged independent cybersecurity analysts to challenge assumptions, refine categorizations, and affirm interpretive accuracy. This iterative approach facilitated the identification of emergent trends and validated the segmentation schema spanning offerings, operating systems, applications, end users, deployment models, and organization sizes.
By adhering to these meticulous research standards, the study ensures that its findings reflect both current market realities and potential inflection points. The transparency of our methodology empowers stakeholders to reproduce analyses or drill down into specific subsegments, fostering confidence in the robustness of the insights delivered.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Endpoint Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Endpoint Security Market, by Offerings
- Endpoint Security Market, by Operating System
- Endpoint Security Market, by Application
- Endpoint Security Market, by End User
- Endpoint Security Market, by Deployment
- Endpoint Security Market, by Organization Size
- Endpoint Security Market, by Region
- Endpoint Security Market, by Group
- Endpoint Security Market, by Country
- United States Endpoint Security Market
- China Endpoint Security Market
- Competitive Landscape
- List of Figures [Total: 18]
- List of Tables [Total: 1749 ]
Summarizing the Executive Insights and Industry Imperatives in Endpoint Security to Empower Stakeholders with Strategic Direction and Future-Proof Resilience
As this executive summary has demonstrated, endpoint security stands at a pivotal juncture, shaped by technological evolution, economic policies, and shifting operational paradigms. The convergence of advanced software suites, dynamic service models, and strategic collaborations underscores the sector’s maturation into a critical enabler of organizational resilience. Consequently, stakeholders must remain vigilant in adapting to emerging threat environments while leveraging segmentation frameworks to tailor solutions effectively.
Through this exploration of transformative shifts, tariff impacts, granular segmentation, regional dynamics, and competitive landscapes, decision-makers are equipped with a multidimensional understanding of the endpoint security domain. Armed with actionable recommendations and a clear view of market drivers, they can chart a course that balances innovation with pragmatism, ensuring that security investments deliver tangible risk reduction and long-term agility.
Ultimately, the continual refinement of endpoint security strategies will define the next wave of enterprise cyber defense. By integrating the insights and methodologies presented herein, organizations can fortify their defenses, drive strategic alignment across teams, and position themselves to confront future challenges with confidence.
Engaging with Ketan Rohom to Leverage Exclusive Endpoint Security Market Research Insights and Drive Informed Decisions for Robust Cyber Defense Strategies
For industry leaders ready to translate insight into action, a direct conversation with Associate Director, Sales & Marketing Ketan Rohom offers unparalleled access to proprietary endpoint security intelligence. Engage in a strategic dialogue that uncovers tailored solutions aligned with organizational priorities and risk postures, enabling you to harness expert guidance in selecting optimal security architectures and partner ecosystems. By reaching out, you gain an exclusive opportunity to deep dive into scenario-based analyses that address unique deployment challenges and compliance requirements, ensuring your decision-making is both data-driven and future-oriented. Initiate this collaboration today to secure privileged early insights into forthcoming industry developments, operational benchmarks, and vendor landscapes that will shape the next generation of cyber defense strategies. Unlock the full value of your security investments by leveraging a partnership that bridges rigorous market analysis with actionable implementation roadmaps tailored to your enterprise context.

- How big is the Endpoint Security Market?
- What is the Endpoint Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




