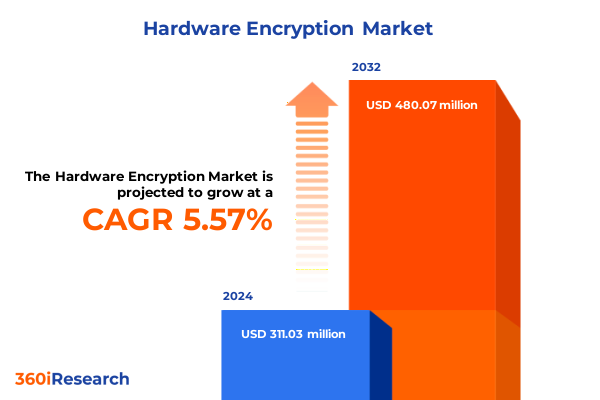
The Hardware Encryption Market size was estimated at USD 328.08 million in 2025 and expected to reach USD 344.65 million in 2026, at a CAGR of 5.58% to reach USD 480.07 million by 2032.
Understanding How Hardware Encryption Is Revolutionizing Data Security Strategies to Counter Sophisticated Threats and Address Expanding Compliance Requirements
As organizations grapple with increasingly sophisticated cyber threats and stringent regulatory frameworks, hardware encryption has emerged as a cornerstone technology for safeguarding sensitive information. Unlike software-only approaches that can be vulnerable to compromise at the operating system level or to side-channel attacks, hardware encryption embeds cryptographic capabilities directly into processors, storage devices, or dedicated modules. This approach delivers tamper-resistant protection and significantly reduces the attack surface, ensuring that data remains encrypted at rest, in transit, and across device lifecycles. In recent years, the proliferation of cloud computing, edge devices, and data-intensive applications has elevated the importance of seamless, high-performance encryption solutions as a fundamental pillar of corporate security strategies.
Moreover, as enterprises undergo digital transformation initiatives that rely on massive data flows and complex network architectures, the benefits of hardware-accelerated encryption become increasingly evident. By offloading cryptographic workloads from general-purpose CPUs to dedicated hardware, organizations can achieve higher throughput and lower latency without compromising on security. This shift not only enhances system performance but also simplifies compliance with evolving data-protection mandates, reducing the complexity associated with managing encryption keys and enforcing uniform policies.
This executive summary outlines the critical developments reshaping the hardware encryption landscape, examines the cumulative impact of recent policy changes, and offers segmented insights to inform strategic decision-making. By exploring key market segments, regional dynamics, and leading innovators, this report equips decision-makers with a holistic understanding of how hardware encryption solutions can drive resilience, operational efficiency, and regulatory adherence in today’s volatile threat environment.
Identifying the Key Technological and Regulatory Shifts Redefining Hardware Encryption Solutions for Modern Infrastructure and Emerging Security Paradigms
The trajectory of hardware encryption has been profoundly influenced by a confluence of technological breakthroughs and evolving regulatory pressures. One notable shift is the integration of encryption engines into standard system-on-chip designs, blurring the lines between discrete cryptographic modules and general-purpose processors. This convergence enables more efficient power management, tighter hardware-software integration, and streamlined deployment across a wide spectrum of platforms, from data centers to Internet-of-Things endpoints.
Concurrently, the emergence of edge-computing paradigms and the relentless growth of distributed applications have driven demand for decentralized encryption models. Organizations are investing in trusted execution environments and secure enclaves that facilitate data protection at the network edge, mitigating risks associated with data aggregation and transit. This movement toward localized cryptographic processing underscores a broader trend: security must be architected in tandem with compute and storage, not tacked on as an afterthought.
On the regulatory front, governments around the world have introduced more stringent data-sovereignty and encryption export controls. These measures are compelling vendors to develop solutions that not only meet global performance benchmarks but also adhere to diverse jurisdictional requirements. As such, multinational enterprises are seeking hardware encryption technologies that offer flexibility in key-management policies and support regional compliance mandates. Taken together, these trends are transforming hardware encryption from a specialized niche into a strategic imperative for any organization striving to maintain data integrity and confidentiality in an increasingly interconnected ecosystem.
Assessing the Complex Impacts of 2025 US Tariffs on Hardware Encryption Supply Chains, Cost Structures, and International Partner Dynamics
The implementation of revised United States tariffs in early 2025 has introduced new complexities for hardware encryption vendors and end users. Tariff adjustments, particularly those targeting semiconductor components and cryptographic modules, have exerted upward pressure on production costs across multiple stages of the supply chain. Manufacturers that previously sourced chips and modules from low-cost regions have been compelled to reevaluate their procurement strategies or absorb additional expenses, directly affecting the total cost of ownership for advanced encryption hardware.
Moreover, changes to import duties have disrupted established partner relationships, as vendors navigate customs reclassifications and shifting geographic sourcing considerations. Organizations dependent on international collaboration for hardware security module (HSM) provision or custom encryption ASIC design now face longer lead times and increased logistical overhead. These constraints are prompting some firms to diversify their supplier bases or invest in near-shoring critical production processes to minimize tariff exposure and maintain agile response capabilities.
Yet, amid these challenges, the industry has demonstrated resilience by innovating around cost structures. Vendors have consolidated functionally overlapping modules and optimized hardware designs to reduce component counts without sacrificing cryptographic strength. Additionally, some solution providers have embraced flexible deployment models, offering both on-premises and managed service options that enable end users to shift capital expenditures to operational budgets. These adaptive strategies underscore the market’s ability to uphold security imperatives while adjusting to an evolving tariff landscape and preserving competitive positioning.
Unveiling Market Segmentation Insights Illuminating How End Users, Encryption Types, Deployment Models, and Applications Drive Hardware Encryption Adoption
The hardware encryption market can be segmented by end-use sectors, revealing distinct adoption patterns and priority use cases. Financial services and banking institutions often seek ultra-low-latency encryption capabilities to secure high-velocity trading platforms, whereas energy and utilities companies prioritize hardware modules capable of withstanding harsh environmental conditions while ensuring the integrity of critical infrastructure. Government and defense agencies demand the highest assurance levels, including physical tamper resistance and rigorous certification standards, while healthcare providers focus on safeguarding patient records and complying with health-data privacy regulations. The IT and telecom sector requires scalable encryption solutions that can be embedded across network equipment, and retail organizations emphasize point-of-sale encryption to protect transaction data and customer information.
Examining encryption types, CPU-based solutions incorporating AES-NI and Trusted Memory Encryption have gained traction for their seamless integration with existing data-center architectures, while hardware security modules in the form of network-attached devices, PCIe cards, and USB tokens offer specialized key-management and cryptographic acceleration. Self-encrypting drives available in NVMe, SAS, and SATA form factors deliver transparent at-rest encryption, and software-based implementations-whether API-centric or integrated within applications-extend protection into environments where dedicated hardware may not be feasible. Deployment models vary from cloud-native encryption services to hybrid architectures that blend managed key-holding with on-premises control and fully localized security appliances.
Within application domains, data-at-rest encryption remains the foundation for secure storage, data-in-transit solutions protect information flows across networks, and device security capabilities are being embedded at the hardware level to ensure endpoint trust. Together, these segmentation insights illustrate how diverse industry requirements and technical preferences drive the evolution and adoption of hardware encryption technologies.
This comprehensive research report categorizes the Hardware Encryption market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- End User
- Encryption Type
- Deployment Model
- Application
Exploring Regional Dynamics and Adoption Patterns Highlighting How Americas, EMEA, and Asia-Pacific Shape the Global Hardware Encryption Ecosystem
Analysis of regional dynamics highlights divergent trajectories across the Americas, EMEA, and Asia-Pacific markets, driven by distinct regulatory, economic, and technological factors. In the Americas, regulatory emphasis on consumer data protection and the rapid adoption of cloud-based services have fueled demand for hardware encryption solutions that can seamlessly integrate with hyperscale platforms. North American organizations are at the forefront of deploying edge-based encryption within IoT ecosystems, leveraging hardware accelerators to secure data collected from distributed sensors and devices.
Meanwhile, Europe, the Middle East, and Africa are characterized by complex cross-border data-privacy regulations and a growing emphasis on sovereign encryption frameworks. GDPR compliance remains a driving force in Europe, and governments across the region are investing in domestic encryption capabilities to reduce reliance on foreign-controlled key-management systems. In EMEA, the interplay between multinational compliance burdens and emerging cybersecurity directives has catalyzed collaborations between regional security vendors and global hardware manufacturers.
In Asia-Pacific, rapid digitalization initiatives and large-scale smart infrastructure projects are scaling the market for hardware encryption at pace. National data-protection laws in multiple APAC countries have begun to mandate hardware-based key protection, encouraging domestic enterprises to adopt self-encrypting storage and HSMs for critical applications. Furthermore, the Asia-Pacific region is seeing a surge in local semiconductor manufacturing, which is shifting the balance of innovation and supply towards in-region production. Taken together, these regional insights underscore the necessity for vendors to tailor their strategies to highly varied regulatory and operational environments.
This comprehensive research report examines key regions that drive the evolution of the Hardware Encryption market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Leading Hardware Encryption Solution Providers and Their Innovations Driving Competitive Differentiation in Performance, Security, and Integration
Examining the competitive landscape reveals a diverse set of established players and innovative challengers driving differentiation through performance enhancements, integration capabilities, and security assurances. Thales has focused on expanding its hardware security module portfolio with next-generation cryptographic accelerators and modular key-management services, while Microchip Technology has leveraged its microcontroller expertise to introduce low-power encryption engines optimized for embedded applications. Broadcom has innovated by integrating secure enclaves within its network processors, enabling line-rate packet encryption for high-throughput telecom environments.
Samsung Electronics has invested heavily in self-encrypting drive technologies, offering NVMe SSDs with built-in encryption controllers that deliver enterprise-grade performance alongside streamlined key-management APIs. Infineon Technologies continues to be a leading supplier of discrete cryptographic chips and secure microcontroller platforms, catering to defense, automotive, and industrial IoT segments. Meanwhile, emerging providers have differentiated by offering cloud-native HSM services that seamlessly integrate with hyperscaler environments, enabling customers to manage keys in a hybrid fashion without compromising on hardware roots of trust.
Across the board, vendors are forming strategic partnerships to embed encryption capabilities into a broader ecosystem of hardware, software, and managed services. This collaborative approach addresses rising complexity in key lifecycle management and helps end users deploy end-to-end protection frameworks. As competition intensifies, the ability to combine robust security features with flexible deployment options will determine which companies capture the largest share of future growth opportunities.
This comprehensive research report delivers an in-depth overview of the principal market players in the Hardware Encryption market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Broadcom Inc.
- Cisco
- Giesecke+Devrient
- IBM Corporation
- IDEMIA
- Infineon Technologies AG
- Intel Corporation
- Kanguru Solutions
- Kingston Technology
- KIOXIA Holdings
- McAfee, LLC
- Micron Technology
- NetApp
- NXP Semiconductors N.V.
- Samsung Electronics
- Seagate Technology
- Thales Group
- Utimaco
- Western Digital Technologies
- WinMagic Inc.
Proactive Recommendations Empowering Industry Leaders to Optimize Hardware Encryption Strategies, Enhance Security Posture, and Accelerate Deployment Success
To capitalize on the evolving landscape, industry leaders should embark on a multi-pronged strategy that reinforces both technological resilience and operational agility. First, organizations must prioritize the adoption of unified encryption management platforms that can harmonize key-management workflows across CPU-based engines, self-encrypting drives, and hardware security modules. Integrating disparate encryption components within a single management console reduces complexity, streamlines audit processes, and ensures consistent policy enforcement.
Second, enterprises should explore strategic partnerships with cloud providers and hardware vendors to co-develop bespoke encryption solutions tailored to specific use cases. By collaborating early during product development cycles, companies can influence feature roadmaps and ensure that critical requirements-such as FIPS certification or custom tamper-evident designs-are built into solutions from the outset. Such alliances also facilitate smoother integration into hybrid infrastructures, enabling workloads to move securely between on-premises and cloud environments.
Finally, organizations must invest in continuous security validation and staff training focused on hardware encryption best practices. Simulated exercises, red-teaming, and regular configuration reviews help unearth potential misconfigurations and strengthen incident response capabilities. By embedding encryption expertise within operational teams, organizations can avoid common pitfalls, maintain compliance with evolving regulations, and accelerate deployment timelines. Collectively, these actionable recommendations empower decision-makers to leverage hardware encryption not only as a defensive measure but also as a driving force for innovation and competitive differentiation.
Detailed Research Methodology Unveiling the Systematic Approaches and Rigorous Processes Underpinning the Integrity of Hardware Encryption Market Analysis
The research methodology underpinning this analysis combines rigorous primary and secondary approaches to ensure robust insights and high confidence in findings. Primary research consisted of in-depth interviews with key stakeholders, including CISOs, IT architects, product managers, and regulatory compliance officers, providing qualitative perspectives on adoption drivers, challenges, and future requirements. Secondary research involved a comprehensive review of technical specifications, whitepapers, standard-setting body publications, and regulatory documents to establish an accurate baseline of encryption technologies and policy frameworks.
Quantitative data were triangulated using both bottom-up and top-down modeling techniques. The bottom-up approach aggregated individual use-case requirements, hardware configurations, and pricing structures to capture granular cost and performance metrics. In parallel, a top-down analysis evaluated broader industry reports, procurement data, and macroeconomic indicators to contextualize growth drivers and market dynamics. Cross-validation exercises ensured alignment between both perspectives and identified any discrepancies for further investigation.
Quality assurance processes incorporated multiple rounds of internal reviews, peer feedback sessions, and verification against publicly available benchmarks. Additionally, findings were validated through expert panel discussions, bringing together industry veterans and academic researchers to challenge assumptions and refine conclusions. This comprehensive research framework guarantees that the insights presented are both actionable and reflective of the real-world hardware encryption landscape.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Hardware Encryption market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Hardware Encryption Market, by End User
- Hardware Encryption Market, by Encryption Type
- Hardware Encryption Market, by Deployment Model
- Hardware Encryption Market, by Application
- Hardware Encryption Market, by Region
- Hardware Encryption Market, by Group
- Hardware Encryption Market, by Country
- United States Hardware Encryption Market
- China Hardware Encryption Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 795 ]
Concluding Insights Reinforcing the Strategic Imperative of Embracing Hardware Encryption to Safeguard Digital Assets and Maintain Competitive Advantage
The analysis affirms that hardware encryption is no longer a peripheral security enhancement but a central pillar of enterprise and government data-protection strategies. As cyber threats evolve in sophistication, embedding encryption capabilities at the silicon level provides unparalleled assurance that sensitive information remains secure, regardless of system vulnerabilities or software-level exploits. Moreover, as regulatory regimes grow more stringent and data demands intensify, organizations are compelled to adopt robust, hardware-based encryption solutions to maintain compliance and operational continuity.
Regional and segment-level insights reveal nuanced adoption patterns, underscoring the importance of tailored approaches that address industry-specific requirements and local regulatory nuances. Leading vendors that combine performance optimization with flexible deployment models are poised to capture significant opportunities, especially when they align product roadmaps with end-user priorities and evolving tariff landscapes. Meanwhile, strategic collaborations between hardware providers and cloud platforms will continue to redefine how encryption services are consumed and managed, driving both innovation and greater market accessibility.
Ultimately, hardware encryption represents a strategic imperative for any organization seeking to protect digital assets, minimize risk, and maintain competitive advantage. By leveraging the insights presented-ranging from segmentation nuances to region-specific dynamics and actionable recommendations-decision-makers can chart a clear path forward, ensuring their encryption strategies are both future-proof and aligned with overarching business objectives.
Engage with Ketan Rohom to Unlock In-Depth Insights and Secure Your Hardware Encryption Market Research Report for Strategic Decision-Making
To seize a decisive edge in the competitive landscape of hardware encryption solutions, reach out to Ketan Rohom today to explore comprehensive market intelligence tailored to your strategic objectives. Ketan brings deep expertise in security technologies and possesses a nuanced understanding of emerging encryption trends, enabling him to guide you through a detailed walk-through of key findings, segmentation analyses, and regional dynamics that shape the market. Engaging with Ketan will allow you to gain personalized insights on how best to align your technology roadmaps with evolving regulatory frameworks, optimize your partner ecosystems, and accelerate your product roadmap. Don’t miss the opportunity to leverage actionable data that empowers your organization to make informed investment choices, enhance your security posture, and capitalize on growth opportunities in hardware encryption. Contact Ketan Rohom, Associate Director of Sales & Marketing, to arrange a customized briefing or to secure your access to the full, in-depth market research report. Empower your team with the critical information needed to drive innovation, mitigate risk, and stay ahead of cyber adversaries in an increasingly complex digital environment.

- How big is the Hardware Encryption Market?
- What is the Hardware Encryption Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




