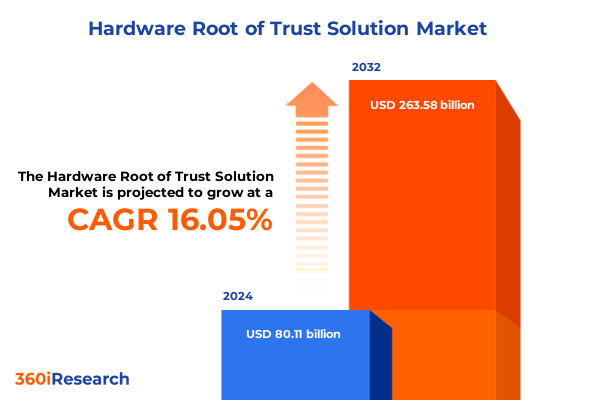
The Hardware Root of Trust Solution Market size was estimated at USD 304.36 million in 2025 and expected to reach USD 325.27 million in 2026, at a CAGR of 8.30% to reach USD 531.95 million by 2032.
Pioneering a New Era of Trust Through Resilient Hardware Security Foundations for Mission-Critical Digital Operations and Data Integrity Assurance
In an era defined by relentless cyber adversaries and escalating data integrity concerns, establishing a hardware root of trust has become foundational to secure digital ecosystems. This core security concept anchors critical operations in an immutable hardware-based trust anchor that validates firmware, software, and system integrity prior to execution. As attack surfaces proliferate across cloud, edge, and IoT environments, this hardware-enforced trust boundary serves as an impenetrable checkpoint, ensuring that every layer of the digital stack commences from a verifiable and uncompromised state.
Drawing on decades of embedded security innovation, hardware root of trust solutions now enable enterprises to embed cryptographic identity, secure key management, and system attestation directly at the silicon level. By shifting the security paradigm from reactive defenses to proactive trust establishment, organizations can mitigate risks from supply chain tampering, firmware exploits, and unauthorized access. This introduction highlights the transformative role of hardware roots of trust in shaping resilient architectures, safeguarding critical infrastructure, and empowering decision-makers to drive digital transformation with uncompromising confidence.
Navigating Disruptive Technological Shifts Reshaping Hardware Root of Trust Solutions Across Evolving Cybersecurity and Compliance Demands
The cybersecurity landscape is undergoing seismic shifts as the boundaries between cloud, edge, and on-premise deployments blur under the weight of converged IT and OT environments. Hardware root of trust solutions have evolved to address the demands of zero-trust architectures, providing immutable verification at every node-from data centers to microcontrollers embedded in connected appliances. This transition towards distributed trust models is propelled by the rise of remote work, the integration of AI-driven threat detection, and the urgent need for supply chain transparency in semiconductor fabrication.
Regulatory frameworks and industry standards are also redefining the requirements for secure systems. Governments and global bodies are mandating certified hardware security modules and cryptographic compliance, pressuring vendors to align product roadmaps with evolving assurance levels. Simultaneously, open standards initiatives are fostering interoperability between proprietary silicon modules and cross-vendor security ecosystems. This confluence of regulatory pressures, technological convergence, and collaborative innovation is driving a new paradigm for hardware root of trust solutions-one where agility and assurance coalesce to meet the demands of next-generation digital infrastructures.
Assessing the Ripple Effects of Enacted United States Tariffs in 2025 on Hardware Root of Trust Supply Chains and Strategic Sourcing Models
With the United States maintaining and recalibrating its tariff regime in 2025, hardware root of trust solution providers and end users have had to reassess supply chain strategies to mitigate escalating component costs. Levies on imported silicon wafers, module assemblies, and specialized chips have introduced variable cost pressures. In response, leading semiconductor vendors and system integrators are exploring dual-sourcing arrangements, onshoring critical manufacturing processes, and leveraging tariff exemptions for research and development activities to maintain competitive pricing and supply continuity.
These policy-driven cost shifts are also reshaping pricing models for security modules and trusted execution environments. Organizations are balancing the immediate impact of higher landed costs against the long-term benefits of localized production, which can reduce lead times and strengthen quality assurance. Moreover, the current tariff landscape has accelerated investment in purpose-built secure compute platforms within allied jurisdictions, fostering new regional partnerships and innovation hubs focused on hardware-based trust anchors.
As the broader geopolitical environment continues to influence trade flows, security architects are prioritizing transparency in component provenance. The push for onshore and nearshore manufacturing not only addresses cost volatility but also enhances supply chain resilience against systemic disruptions. Ultimately, the cumulative effect of 2025 tariffs underscores the strategic imperative for organizations to diversify sourcing strategies and embed hardware root of trust capabilities into roadmap planning to uphold security postures and operational agility.
Unveiling Critical Segmentation Perspectives Across Components Types Applications Enterprise Sizes and Deployment Modes Driving Adoption Patterns
An in-depth examination of the market through a component lens reveals that Hardware Security Modules have long dominated high-assurance use cases, yet emerging demands are propelling runtime memory solutions and secure CPU implementations to the forefront, while security perimeter devices carve out specialized niches for network-level root of trust verification. Simultaneously, analysis based on solution type indicates that platform-based silicon continues to gain traction among OEMs seeking integrated security, with fixed function architectures catering to streamlined workloads and programmable variants offering the flexibility required for evolving cryptographic standards; concurrently, standalone Trusted Platform Modules retain their relevance for legacy integration and standardized attestation profiles.
When considering application-driven segmentation, authentication and access control remain foundational drivers of early adoption, though cryptographic operations and data encryption functions are scaling rapidly to meet sophisticated privacy mandates and multi-tenant environments. Storage protection features are increasingly sought after in industries reliant on transaction integrity and intellectual property safeguarding. From an end-user industry perspective, banking, financial services, and insurance sectors continue to invest heavily in hardware-enforced trust anchors to comply with regulatory audits, while energy and utilities providers emphasize grid resilience. Government and defense agencies demand the highest assurance levels, healthcare entities focus on safeguarding patient data, and IT and telecom operators integrate roots of trust into network infrastructure. Manufacturing players, spanning automotive to consumer electronics, are embedding hardware trust primitives along production lines, and retailers are enhancing point-of-sale security through tamper-resistant modules.
Insights into enterprise size reveal that large enterprises leverage bespoke deployments with extensive customization, whereas small and medium enterprises increasingly opt for modular, off-the-shelf root of trust solutions that balance cost and capability. Analysis of deployment modes shows that cloud-based implementations are accelerating adoption among service providers, while on-premise configurations remain indispensable for organizations with stringent data sovereignty and latency requirements.
This comprehensive research report categorizes the Hardware Root of Trust Solution market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Type
- Application
- End-User Industry
- Enterprise Size
- Deployment Mode
Decoding Regional Dynamics in Hardware Root of Trust Implementation Trends Across Americas EMEA and Asia-Pacific Market Ecosystems
In the Americas, hardware root of trust adoption is propelled by a robust ecosystem of semiconductor innovation in North America and extensive deployment among financial institutions in Latin America. Pioneering research at technology hubs in the United States fuels advanced secure compute platforms, and regional policy incentives for chip fabrication bolster localized manufacturing. This confluence has positioned the Americas as both a leading innovation source and a major consumer of secure hardware solutions.
Across Europe, the Middle East, and Africa, stringent data protection regulations and critical infrastructure mandates have intensified demand for high-assurance hardware security modules. GDPR compliance, defense modernization efforts, and renewable energy grid protection programs are driving investments in root of trust capabilities. Collaboration across EU member states and Gulf Cooperation Council initiatives is fostering standardized certification pathways, enhancing cross-border interoperability and elevating regional security postures.
Asia-Pacific markets are characterized by dynamic growth fueled by large-scale manufacturing in China, semiconductor R&D in Japan and South Korea, and burgeoning demand in India’s digital transformation agenda. Regional supply chain diversification strategies are emerging in response to trade tensions, with ASEAN economies positioning themselves as key alternatives for secure component production. This geographic diversity, coupled with aggressive cloud adoption in Australia and New Zealand, underscores the Asia-Pacific region as a critical driver of next-generation hardware root of trust solutions.
This comprehensive research report examines key regions that drive the evolution of the Hardware Root of Trust Solution market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Leading Vendor Innovations Strategic Alliances and Competitive Differentiators Shaping the Hardware Root of Trust Landscape
Leading technology vendors are aggressively refining their hardware root of trust portfolios through strategic partnerships, product roadmaps, and acquisitions. Infineon has introduced next-generation secure elements that integrate advanced cryptographic accelerators, while NXP has expanded its secure MCU lineup with enhanced key storage and lifecycle management features. STMicroelectronics continues to leverage its global foundry footprint to deliver cost-optimized security modules, and Microchip’s enhanced secure authenticator families underscore a focus on embedded IoT use cases. Intel and AMD are embedding root of trust capabilities directly into platform chipsets, enabling silicon-to-cloud security models for enterprise and hyperscale deployments.
Simultaneously, specialized players such as Microsemi, Rambus, and Texas Instruments are forging alliances with leading foundries and software providers to bolster security-by-design frameworks. Cloud hyperscalers and platform providers are also entering the arena: Google’s Titan series and Apple’s T2 security chip demonstrate the competitive convergence between consumer electronics and enterprise-grade security features. These vendor strategies underscore an industry-wide shift toward integrated hardware security tailored to diverse application demands, reflecting a marketplace where innovation velocity and strategic positioning will determine long-term leadership in the hardware root of trust domain.
This comprehensive research report delivers an in-depth overview of the principal market players in the Hardware Root of Trust Solution market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Advanced Micro Devices, Inc.
- Apple Inc.
- Arm Limited
- Broadcom Inc.
- Cadence Design Systems Inc.
- Cisco Systems, Inc.
- Giesecke+Devrient GmbH
- Infineon Technologies AG
- Intel Corporation
- Lattice Semiconductor Corporation
- Marvell Technology Group Ltd.
- Microchip Technology Inc.
- Micron Technology, Inc.
- Nuvoton Technology Corporation
- NXP Semiconductors N.V.
- Oracle Corporation
- Qualcomm Technologies, Inc.
- Rambus Inc.
- Samsung Electronics Co., Ltd.
- SECURE-IC S.A.S
- Silicon Laboratories Inc.
- STMicroelectronics N.V.
- Synopsys Inc.
- Texas Instruments Incorporated
- Thales Group
- Winbond Electronics Corporation
Strategic Action Plans for Industry Stakeholders to Optimize Hardware Root of Trust Deployment and Enhance Security Resilience and Operational Efficiency
Industry leaders should prioritize alignment with semiconductor suppliers and system integrators to co-develop customizable hardware root of trust modules that address specific threat vectors. By investing in early-stage collaboration, enterprises can influence product roadmaps, accelerate time-to-market, and secure preferential access to emerging silicon innovations. Simultaneously, organizations must engage with regulatory bodies and standards organizations to shape certification requirements that balance assurance levels with deployment pragmatism.
To optimize resilience, stakeholders should implement diversified sourcing strategies that mitigate tariff impacts and geopolitical risks. Combining onshore manufacturing with strategic partnerships in allied regions will ensure supply continuity and cost predictability. Furthermore, enterprises are encouraged to integrate hardware root of trust into DevSecOps pipelines, enabling seamless attestation, key management, and firmware verification within continuous integration workflows. Developing internal expertise through targeted training programs and threat modeling exercises will bolster the ability to architect secure systems at scale.
Comprehensive Mixed-Method Research Approach Leveraging Qualitative and Quantitative Techniques to Illuminate Hardware Root of Trust Market Insights
This research employs a mixed-method approach, integrating primary and secondary data sources to deliver comprehensive market insights. Primary research involved in-depth interviews with C-level executives, security architects, and procurement specialists across multiple industries to capture nuanced perspectives on adoption drivers, procurement challenges, and feature priorities. These qualitative insights were complemented by quantitative data points obtained from technical whitepapers, regulatory filings, patent analyses, and publicly available vendor disclosures, ensuring a holistic view of the technology landscape.
Our methodology further incorporated scenario analysis and triangulation techniques to validate findings. Quantitative models extrapolated adoption curves based on historical implementation benchmarks, while qualitative workshops with domain experts explored emerging use cases and threat vectors. Data integrity checks and iterative feedback loops with external consultants were employed to refine assumptions and enhance the accuracy of segment-level insights. This rigorous framework guarantees that the conclusions and recommendations presented herein are both actionable and reflective of real-world market dynamics.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Hardware Root of Trust Solution market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Hardware Root of Trust Solution Market, by Component
- Hardware Root of Trust Solution Market, by Type
- Hardware Root of Trust Solution Market, by Application
- Hardware Root of Trust Solution Market, by End-User Industry
- Hardware Root of Trust Solution Market, by Enterprise Size
- Hardware Root of Trust Solution Market, by Deployment Mode
- Hardware Root of Trust Solution Market, by Region
- Hardware Root of Trust Solution Market, by Group
- Hardware Root of Trust Solution Market, by Country
- United States Hardware Root of Trust Solution Market
- China Hardware Root of Trust Solution Market
- Competitive Landscape
- List of Figures [Total: 18]
- List of Tables [Total: 1431 ]
Drawing Consolidated Insights on Hardware Root of Trust Advancements and Strategic Imperatives for Sustained Security Posture Enhancement
The persistent rise of sophisticated cyber threats and the intensifying complexity of global supply chains have firmly established hardware roots of trust as indispensable components of modern security architectures. By anchoring system integrity at the silicon level and providing immutable verification mechanisms, these solutions form the bedrock upon which resilient digital initiatives are built. As organizations navigate converged IT and OT ecosystems, the adoption of hardware-enforced trust primitives will prove critical to maintaining data sovereignty, regulatory compliance, and operational continuity.
Looking ahead, the convergence of secure AI workloads, edge computing proliferation, and evolving regulatory landscapes will further amplify the importance of hardware roots of trust. Enterprises that proactively integrate these trust anchors into their development lifecycles and diversification strategies will secure competitive advantage and robust defense postures. In this dynamic environment, the imperative is clear: embed hardware-based trust at the core of digital transformation agendas to safeguard innovation and ensure enduring security excellence.
Empowering Strategic Decisions Reach Out to Ketan Rohom Associate Director Sales Marketing to Unlock the Complete Hardware Root of Trust Market Analysis
For organizations poised to fortify their digital environments through robust hardware root of trust implementations, reaching out to Ketan Rohom, Associate Director, Sales & Marketing at 360iResearch, represents the most efficient next step. His deep understanding of security-centric architectures and nuanced market dynamics will ensure you gain tailored guidance on how this research can drive your strategic planning and procurement processes.
Engaging with Ketan will provide clarity on customizable research packages, access to detailed segment analyses, and personalized consultation on leveraging hardware root of trust for maximum resilience. Connect today to secure access to unparalleled insights and position your enterprise at the vanguard of security innovation.

- How big is the Hardware Root of Trust Solution Market?
- What is the Hardware Root of Trust Solution Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




