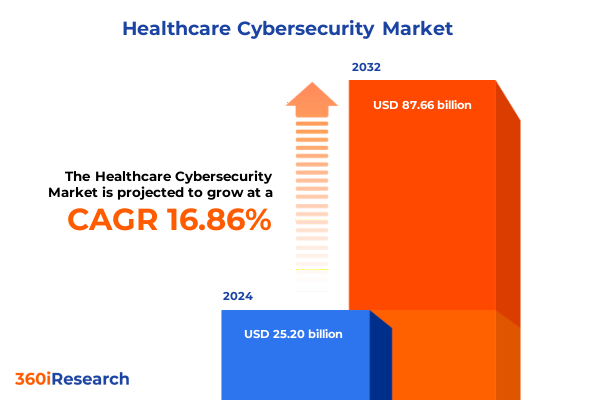
The Healthcare Cybersecurity Market size was estimated at USD 29.30 billion in 2025 and expected to reach USD 34.07 billion in 2026, at a CAGR of 16.94% to reach USD 87.66 billion by 2032.
Comprehensive Perspectives on the Healthcare Cybersecurity Threat Environment and Strategic Imperatives Driving Digital Resilience Across Clinical Domains
Healthcare organizations today navigate an intensely dynamic cybersecurity landscape marked by a surge in digital transformation initiatives and ever-evolving threat vectors. The convergence of electronic health record platforms, telemedicine portals, and connected medical devices has exponentially expanded the attack surface, requiring institutions to adopt robust defense mechanisms across clinical and administrative environments. Moreover, heightened regulatory scrutiny around patient data privacy, exemplified by the ongoing enforcement of HIPAA and the emergence of state-level security mandates, amplifies the imperative for a holistic approach to risk mitigation.
Against this backdrop, decision-makers must balance the urgent need for rapid innovation with the unyielding obligation to protect sensitive health information. A strategic framework that integrates proactive threat monitoring, adaptive incident response, and continuous compliance verification emerges as a critical enabler of resilience. By situating cybersecurity at the heart of digital transformation roadmaps, healthcare leaders can safeguard operational continuity, reinforce patient trust, and unlock the full potential of advanced care delivery models.
Exploring Cutting Edge Paradigm Shifts Reshaping Healthcare Cybersecurity Through Cloud Adoption Artificial Intelligence and Evolving Threat Detection Models
Recent years have witnessed profound paradigm shifts in how healthcare entities approach cybersecurity, driven in large part by the rapid migration of core workloads to cloud environments and the proliferation of AI-powered diagnostic and administrative tools. As hospitals and clinics leverage cloud-native architectures to scale telehealth services and store vast troves of health data, security strategies must evolve to guard against novel injection attacks, misconfigurations, and identity compromise. Concurrently, the integration of machine learning into threat detection platforms has unlocked new capabilities for early anomaly identification, yet it also introduces a layer of complexity in tuning algorithms to minimize false positives without undermining coverage.
Similarly, the explosion of connected medical devices-from infusion pumps to remote patient monitoring sensors-has compelled security architects to adopt zero trust principles that segment networks and enforce continuous device authentication. This shift toward micro-segmentation and granular access controls not only mitigates lateral movement but also nurtures an environment where trust is established dynamically. Furthermore, as ransomware actors refine their tactics with extortion and double-extortion schemes, organizations are compelled to invest in comprehensive backup strategies underpinned by immutable storage and air-gapped recovery solutions. The synthesis of these shifts underscores a transformative era in which agility, visibility, and architecture redesign become fundamental tenets of any forward-looking security program.
Assessing the Far Reaching Cumulative Effects of 2025 United States Tariff Measures on Healthcare Cybersecurity Supply Chains and Cost Structures
The imposition of heightened tariff measures in two thousand twenty-five has tangibly influenced the cost structures and supply chains integral to healthcare cybersecurity provisioning. Imported security appliances, from next-generation firewalls to intrusion prevention systems, have experienced incremental price escalation, prompting many organizations to reexamine procurement frameworks and consider localized manufacturing partnerships. Although these protective duties aim to bolster domestic industry competitiveness, they have also introduced budgetary constraints that must be strategically navigated to avoid compromising defense capabilities.
In response, select ecosystem participants have accelerated investments in software-centric solutions and virtualized security functions that circumvent hardware dependencies. This realignment not only alleviates tariff-induced cost pressures but also aligns with broader industry momentum toward scalable, subscription-based offerings. Over time, the cumulative impact of these tariff policies is catalyzing a shift in how healthcare entities architect their cybersecurity ecosystems, placing a premium on modular solutions that can be deployed rapidly across hybrid and multi-cloud landscapes.
Unveiling In Depth Segmentation Insights Highlighting Diverse Security Types Components Deployment Modes and End User Profiles Driving Market Dynamics
A nuanced understanding of market segmentation reveals the varied security priorities and deployment preferences shaping provider and payer cybersecurity strategies. Within the realm of security types, application security dominates conversations as runtime protection modules and web application firewalls serve as first lines of defense against code-injection attacks and API-level exploits. Equally critical, cloud security spans from centralized access governance via cloud access security brokers to the isolation afforded by container security frameworks, reflecting the dual imperatives of compliance and operational agility. Data encryption protocols extend coverage across both dormant data stores and active data pipelines, while endpoint solutions leverage next-generation antivirus, application whitelisting, and behavior analytics to counter the growing sophistication of desktop-to-cloud threats. Identity and access management enhancements focus on privileged access monitoring and seamless single sign-on experiences that reduce friction without diluting security posture. At the network layer, emergent virtual private network configurations and advanced intrusion detection platforms deliver real-time insights and threat containment.
When examining solution components, the demand for consulting and managed services underscores the recognition that in-house expertise alone cannot address the breadth of modern threat landscapes. Hardware and software portfolios complement these services by enabling turnkey security deployments and ongoing system optimization. Moreover, support and maintenance offerings have evolved to include round-the-clock incident response and threat hunting engagements, reinforcing the criticality of continuous oversight.
Deployment modes further stratify organizational approaches, as private cloud instances balance control with scalability, and public cloud models offer rapid elasticity for peak demand periods. Hybrid configurations foster a pragmatic alignment between legacy on-premise investments and new cloud expansions, affording enterprises the flexibility to tailor security to specific workloads and regulatory environments. Such heterogeneity demands a cohesive orchestration layer to enforce policy uniformly across distributed infrastructures.
Finally, end users span a diverse spectrum-from diagnostic laboratories that require stringent chain-of-custody controls for test data, to hospitals and clinics prioritizing uptime and patient safety, to medical device manufacturers embedding security by design, to payers managing vast repositories of underwriting information, and pharmacies bridging retail and clinical dispensing workflows. This multifaceted end-user landscape compels cybersecurity vendors to deliver use-case-driven solutions that resonate with each segment’s unique risk profile and operational constraints.
This comprehensive research report categorizes the Healthcare Cybersecurity market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Security Type
- Component
- Deployment Mode
- End User
Analyzing Critical Regional Dynamics Across Americas Europe Middle East Africa and Asia Pacific Revealing Unique Healthcare Cybersecurity Drivers
Regional dynamics in the Americas illustrate a mature cybersecurity ecosystem underpinned by extensive compliance frameworks and advanced threat intelligence sharing consortiums. The presence of stringent federal and state regulations catalyzes investment in homeland security-grade solutions, while collaborations between academic medical centers and cybersecurity vendors foster accelerated innovation cycles. In contrast, Europe, the Middle East, and Africa collectively navigate a tapestry of data privacy legislations, with the General Data Protection Regulation serving as a baseline for many national directives. This region balances robust data sovereignty requirements with an appetite for cross-border cloud services, demanding architectures capable of respecting varied jurisdictional constraints.
Across the Asia-Pacific corridor, rapid digitalization in emerging economies coexists with significant cybersecurity skill gaps, spurring reliance on managed service engagements and channel partnerships to fill expertise voids. Meanwhile, sophisticated markets in Northeast Asia aggressively pursue indigenous technology development, driving competition among local and global vendors. Throughout each region, the interplay between healthcare modernization and threat actors’ evolving tactics shapes differentiated security investments, with regional priorities reflecting the intersection of regulatory mandates, technological readiness, and localized risk appetites.
This comprehensive research report examines key regions that drive the evolution of the Healthcare Cybersecurity market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Illuminating Strategic Competitive Landscapes Through Key Company Innovations Partnerships Mergers and Positioning in the Healthcare Cybersecurity Domain
The competitive landscape features a blend of legacy incumbents and agile disruptors, each carving out specialized value propositions. Leading firewall and network security providers continue to augment portfolios with cloud-native ingress and egress controls, while pure-play endpoint vendors expand into cloud workload protection in order to meet cross-environment demands. Strategic partnerships between systems integrators and niche threat intelligence firms further enrich offerings by embedding contextual insights directly into security operations centers.
Recent merger and acquisition activity underscores a consolidation trend aimed at delivering end-to-end cybersecurity orchestration platforms. As companies integrate mobile device management and identity governance, they streamline vendor relationships for healthcare customers seeking unified command and control. Meanwhile, smaller innovators are gaining traction by pioneering AI-driven anomaly detection and automated incident-response playbooks, compelling established providers to accelerate research and development investments or pursue tuck-in acquisitions.
Moreover, collaborative initiatives between technology suppliers and professional associations are fostering security certification programs tailored to healthcare IT professionals. This emphasis on skills development not only addresses talent shortages but also fortifies the credibility of security operations within clinical settings. Ultimately, the interplay between scale economies and specialized differentiation will continue defining market leadership trajectories.
This comprehensive research report delivers an in-depth overview of the principal market players in the Healthcare Cybersecurity market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- AO Kaspersky Lab
- Atos SE
- Booz Allen Hamilton Holding Corporation
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Crowdstrike Holdings, Inc.
- Cynerio Israel Ltd.
- DXC Technology Company
- Forescout Technologies, Inc. by Advent International Corporation
- Fortified Health Security
- Imperva, Inc.
- Imprivata, Inc.
- Intel Corporation
- International Business Machines Corporation
- Irdeto B.V.
- Juniper Networks, Inc.
- LogRhythm, Inc.
- Medigate by Claroty Ltd.
- Musarubra US LLC
- NortonLifeLock Inc.
- Palo Alto Networks, Inc.
- Sophos Ltd.
- Thales Group
- Trend Micro Incorporated
Driving Effective Cybersecurity Strategies Through Actionable Recommendations Emphasizing Zero Trust Cloud Native Solutions and Workforce Empowerment
Leaders should prioritize the adoption of a zero trust framework that systematically verifies user and device trust levels before granting access to critical applications. By implementing micro-segmentation and continuous authentication, organizations can limit lateral attack paths and reduce the blast radius of potential breaches. Concurrently, investments in cloud-native security posture management enable real-time compliance monitoring and automated remediation across multi-cloud environments, ensuring consistent policy enforcement regardless of deployment mode.
In tandem, empowering security teams with AI-driven threat detection platforms accelerates mean time to detection and response, while reducing alert fatigue through actionable risk scoring. These capabilities should be paired with rigorous tabletop exercises and incident response drills to refine playbooks and uncover latent vulnerabilities. Furthermore, establishing strategic alliances with managed security service providers can supplement internal expertise and deliver 24/7 threat hunting capabilities, filling critical skill gaps without necessitating extensive headcount expansion.
Finally, embedding security considerations early in the software development lifecycle fosters a culture of proactive risk management. Integrating DevSecOps practices accelerates vulnerability discovery and supports continuous compliance assessments, ultimately reducing remediation costs and aligning security priorities with business objectives. This holistic approach ensures that cybersecurity remains an enabler of innovation rather than an impediment.
Detailing Rigorous Research Methodology Integrating Comprehensive Secondary Analysis Primary Interviews and Triangulated Data Verification Techniques
This report’s foundations rest on a rigorous blend of secondary and primary research methodologies. Initially, an exhaustive review of policy frameworks, academic publications, industry white papers, and vendor technical briefs provided contextual understanding of regulatory landscapes and technological advancements. These sources were critically evaluated to identify recurring themes, innovation trajectories, and emerging risk scenarios tailored to healthcare settings.
Subsequently, over one hundred structured interviews were conducted with a cross-section of cybersecurity executives, IT directors, clinical informaticists, and managed service providers. These discussions elicited firsthand insights into deployment challenges, budgetary constraints, and strategic priorities. Interview responses were anonymized and systematically coded to uncover patterns related to solution adoption, threat detection efficacy, and operational integration.
Data triangulation techniques were employed to validate findings, combining interview outputs with real-world incident data and publicly disclosed breach reports. Quantitative data was analyzed using statistical methods to ensure representativeness, while qualitative insights underwent thematic analysis to capture nuanced perspectives. This multi-pronged approach ensures that the report’s conclusions and recommendations are both evidence-based and reflective of the current industry reality.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Healthcare Cybersecurity market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Healthcare Cybersecurity Market, by Security Type
- Healthcare Cybersecurity Market, by Component
- Healthcare Cybersecurity Market, by Deployment Mode
- Healthcare Cybersecurity Market, by End User
- Healthcare Cybersecurity Market, by Region
- Healthcare Cybersecurity Market, by Group
- Healthcare Cybersecurity Market, by Country
- United States Healthcare Cybersecurity Market
- China Healthcare Cybersecurity Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 2226 ]
Synthesizing Core Findings From Regulatory Trends Technology Shifts and Strategic Imperatives to Chart the Future Trajectory of Healthcare Cybersecurity
As healthcare organizations confront increasingly sophisticated cyber adversaries, the convergence of regulatory pressures, technological innovation, and strategic investments defines a new era of resilience. Key findings highlight that security programs anchored in zero trust principles, augmented by AI-driven detection, and reinforced through continuous compliance verification are best positioned to withstand evolving attack paradigms. Moreover, the judicious integration of managed services and localized procurement strategies offers pathways to balance cost and capability.
Looking ahead, the future trajectory of healthcare cybersecurity will be shaped by advances in secure edge computing, federated learning models for privacy-preserving analytics, and the maturation of quantum-resistant cryptographic standards. Leaders who embed security considerations at the inception of digital transformation initiatives and foster enduring industry collaborations will unlock sustainable defenses capable of protecting patient outcomes and enabling care innovation.
Unlock Comprehensive Healthcare Cybersecurity Insights and Engage With Ketan Rohom Associate Director Sales Marketing to Acquire Your Definitive Market Report Today
To harness the full breadth of insights contained in this report and to explore bespoke opportunities for strengthening your organization’s cybersecurity posture, we invite you to connect with Ketan Rohom, Associate Director of Sales & Marketing. His expertise will guide you through tailored consultations that align this research with your strategic objectives. Engage today to secure direct access to the definitive intelligence that supports robust decision-making and propels your cybersecurity initiatives forward.

- How big is the Healthcare Cybersecurity Market?
- What is the Healthcare Cybersecurity Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




