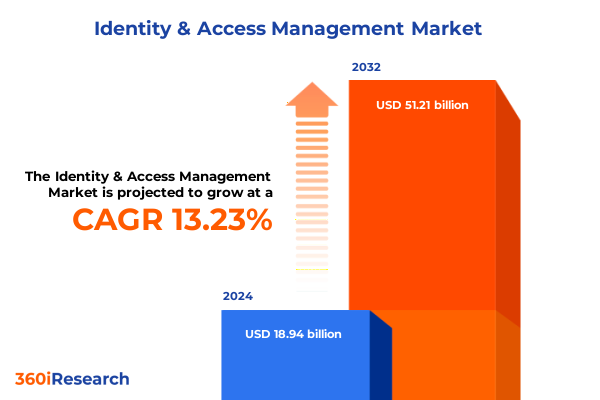
The Identity & Access Management Market size was estimated at USD 21.30 billion in 2025 and expected to reach USD 24.00 billion in 2026, at a CAGR of 13.35% to reach USD 51.21 billion by 2032.
Building the Foundation of Identity and Access Management Excellence with an Engaging Introduction that Frames the Strategic Imperative
Identity and access management has emerged as a foundational pillar of enterprise security and digital trust, establishing a robust framework for verifying user identities, controlling privileged access, and enforcing security policies across complex technology environments. In an era marked by rapid digital transformation and an expanding threat surface, organizations are recalibrating their security architectures to center on identity as the new perimeter. Consequently, enterprises are prioritizing solutions that can deliver seamless yet secure user experiences while addressing evolving regulatory expectations around data privacy and compliance.
This report provides a comprehensive introduction to the key drivers, challenges, and strategic imperatives that define the contemporary identity and access management landscape. It delivers critical context for stakeholders charged with protecting digital assets, enabling secure remote access, and supporting continuous innovation. By framing the strategic importance of identity-centric security, the introduction sets the stage for deeper analysis into market shifts, segmentation dynamics, regional variations, and actionable guidance aimed at elevating an organization’s security posture.
Examining Pivotal Technological and Regulatory Shifts that Are Reshaping the Identity and Access Management Landscape for Enterprise Security
The identity and access management market is being reshaped by a confluence of technological breakthroughs and regulatory pressures that together are redefining how organizations authenticate, authorize, and govern user access. Cloud migration initiatives continue to migrate critical workloads from on premises to public and private clouds, driving demand for identity solutions capable of spanning hybrid environments. Meanwhile, the rise of zero trust architectures is prompting a shift from perimeter-based defenses to continuous verification models that adapt authentication and authorization based on context and user behavior.
Regulatory shifts are intensifying as data privacy frameworks such as GDPR and the California Consumer Privacy Act demand greater transparency and control over personal information. At the same time, global directives around digital identity and Know Your Customer requirements are placing new emphasis on robust identity governance and administration. Furthermore, more sophisticated cyber threats and credential compromise tactics are accelerating adoption of multifactor authentication and biometric technologies. Together, these transformative shifts are forging an environment where agility, visibility, and adaptive controls are nonnegotiable for security leaders.
Assessing the Collective Effects of U.S. Tariff Measures in 2025 on Identity Security Infrastructure and Supply Chain Resilience for IAM Deployments
The cumulative impact of U.S. tariff measures enacted in 2025 has introduced nuanced challenges for organizations procuring identity security hardware and appliances, influencing both cost structures and supply chain strategies. Tariffs imposed under Section 232 on certain electronic components and under Section 301 on products originating from specific regions have elevated the landed cost of hardware authentication tokens, network appliances, and specialized servers. Consequently, procurement teams are reevaluating their vendor partnerships and exploring localized manufacturing options to mitigate exposure to import duties.
Moreover, higher tariffs have accelerated the migration toward software-based authentication solutions and cloud-native identity platforms, as organizations seek to minimize reliance on tariff-impacted physical goods. As a result, software token adoption has outpaced hardware token deployments, and emerging architectures prioritize adaptive contextual control that can be delivered through APIs and cloud services. In addition, compliance teams are adjusting budgetary allocations to accommodate increased operational expenses tied to customs duties and are integrating tariff sensitivity into their vendor selection criteria. Overall, the 2025 tariff landscape is catalyzing a strategic realignment toward cloud-centric identity models and strengthening supply chain resilience within the identity and access management domain.
Deriving Insightful Perspectives from Comprehensive Component Deployment Size and Vertical Segmentation to Illuminate Market Dynamics and Opportunities
Insight into component segmentation highlights that access management continues to command the lion’s share of investment, with adaptive contextual access control, consumer identity systems, and federation technologies forming the core pillars of modern access solutions. Identity governance and administration is rapidly gaining ground as certification, provisioning and deprovisioning, and role management capabilities become essential for meeting stringent compliance demands. In parallel, multifactor authentication is evolving beyond traditional hardware tokens toward biometric-based, software token, and SMS and email modalities, reflecting enterprise priorities around user convenience and security efficacy. Password management remains a critical discipline, driven by vaulting and rotation services that complement self-service password reset tools to reduce helpdesk costs and enhance user autonomy. Privileged access management is also witnessing robust uptake, underpinned by endpoint privilege management and session management controls that safeguard critical assets. Finally, single sign on adoption is bifurcating across desktop and web use cases, enabling seamless experiences whether users operate within local networks or interact with cloud applications.
Deployment mode trends reveal that cloud-delivered identity services are outpacing on-premise implementations, while hybrid configurations persist in heavily regulated sectors where data sovereignty and legacy integration requirements remain paramount. In terms of organizational scale, large enterprises are leading with comprehensive, integrated suites, whereas small and medium enterprises increasingly favor modular, cloud-first solutions that can be rapidly deployed without extensive upfront capital investment. Industry vertical analysis underscores that banking and insurance companies demand rigorous identity governance and robust authentication to meet financial regulations, public sector organizations balance security with citizen service delivery, healthcare providers prioritize patient identity and data privacy, IT and telecom firms focus on scalability and performance, and retail and e-commerce businesses leverage single sign on and seamless access to optimize customer experience across both brick and mortar and online channels.
This comprehensive research report categorizes the Identity & Access Management market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Offering
- Access Type
- Technology
- Deployment Mode
- Authentication Type
- End User
- Organization Size
Unveiling Regional Variations in Adoption Trends and Strategic Priorities across the Americas Europe Middle East Africa and Asia Pacific Markets
Regional analysis reveals significant variation in identity and access management adoption trajectories and strategic emphases across the Americas, Europe Middle East and Africa, and Asia Pacific. In the Americas, especially within North America, organizations lead with cloud-native architectures and advanced analytics capabilities to support zero trust initiatives and real-time threat detection. Regulatory drivers such as stringent privacy laws and sector-specific requirements in finance and healthcare continue to elevate the importance of governance and compliance offerings.
Across Europe, the Middle East, and Africa, GDPR and related data protection frameworks are fundamental drivers shaping identity governance priorities. Hybrid deployment strategies are common as enterprises balance legacy on-premise infrastructure with public cloud services. Government initiatives around digital identity in several EMEA countries are further catalyzing investments in centralized identity platforms and citizen-centric access models.
Asia Pacific markets are characterized by rapid digital transformation and strong growth in mobile and e-commerce channels. Cloud adoption in this region is accelerating, with organizations leveraging identity as a service to secure remote workforces and dispersed partner networks. Moreover, government-led digital identity programs are prompting enterprises to integrate with national identity schemes and adopt scalable identity architectures that support cross-border interoperability.
This comprehensive research report examines key regions that drive the evolution of the Identity & Access Management market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Market Leading Identity and Access Management Providers and Their Strategic Initiatives Driving Innovation and Competitive Differentiation
Several leading companies are shaping the future of identity and access management through differentiated technology portfolios and strategic partnerships. One prominent provider specializes in consumer identity solutions that streamline registration, login, and user lifecycle management for digital-first enterprises. Another vendor has established its leadership by integrating adaptive multifactor authentication and contextual access intelligence within a comprehensive identity governance suite. A major cloud platform player offers a unified directory service that seamlessly integrates with collaboration, productivity, and infrastructure services, reinforcing its footprint across hybrid and multi cloud environments.
Privileged access management is dominated by a specialist whose endpoint privilege controls and session monitoring capabilities are widely deployed in highly regulated industries. An identity governance innovator leverages machine learning to automate certification and role mining, enabling security teams to reduce risk and accelerate compliance. Other key participants include firms that focus on open source identity frameworks, single sign on gateways, risk based authentication engines, and biometric verification services. Across the board, these companies are investing in AI driven threat analytics, cloud interoperability, and developer friendly APIs to foster extensibility, accelerate integrations, and deliver continuous innovation.
This comprehensive research report delivers an in-depth overview of the principal market players in the Identity & Access Management market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Affinidi Pte. Ltd.
- Amazon Web Services Inc.
- Avatier Corporation
- Broadcom Inc.
- Cisco Systems, Inc.
- Cloudflare, Inc.
- CyberArk Software, Inc.
- Entrust Corporation
- Fujitsu Limited
- Google LLC by Alphabet Inc.
- HCL Technologies Limited
- Hewlett Packard Enterprise Development LP
- Hid Global Corporation
- Huawei Technologies Co., Ltd.
- HYPR Corp.
- Imperva, Inc.
- Intel Corporation
- International Business Machines Corporation
- Ivanti, Inc.
- Microsoft Corporation
- miniOrange Security Software Pvt Ltd.
- NEC Corporation
- Okta, Inc.
- OneLogin, Inc.
- Open Text Corporation
- Optimal IdM
- Oracle Corporation
- Ping Identity Corporation
- Salesforce, Inc.
- SAP SE
- Thales Group
- Thoma Bravo, L.P.
- Zoho Corporation Pvt. Ltd.
Delivering Actionable Strategies and Best Practices for Industry Leaders to Elevate Identity and Access Management Posture and Secure Competitive Advantage
To capitalize on emerging opportunities and fortify identity defenses, industry leaders should first embrace a zero trust philosophy that mandates continuous verification of user identities and device posture. Transitioning to a cloud first approach will enable organizations to reduce dependency on tariff exposed hardware while unlocking agile, scalable identity services. Implementing passwordless authentication methods, such as biometrics and software tokens, will enhance user experience and decrease credential compromise, thereby driving higher adoption rates. Additionally, embedding AI and machine learning within identity workflows can deliver adaptive authentication and anomaly detection, strengthening threat response capabilities in real time.
It is equally critical to streamline governance processes by automating provisioning, certification, and role management to minimize manual errors and accelerate compliance cycles. Security and IT teams should engage closely with business stakeholders to ensure identity policies align with user productivity objectives and regulatory obligations. Moreover, fostering a culture of continuous monitoring, regular risk assessments, and privacy by design will uphold data protection standards and support evolving compliance mandates. Finally, partnering with specialized identity vendors and system integrators can expedite deployment timelines, reduce integration complexity, and enable rapid innovation through access to best of breed solutions.
Detailing the Rigorous Research Methodology Employed to Ensure Robust Data Integrity and Insight Validity in Identity and Access Management Analysis
The research methodology underpinning this report is grounded in a rigorous, multi stage process designed to ensure data integrity, analytical validity, and actionable relevance. Primary research comprised in depth interviews with senior security professionals, CIOs, and identity architects across diverse industry verticals, complemented by an extensive survey of end users and channel partners to capture deployment experiences and future priorities. Secondary research involved a thorough review of regulatory publications, vendor documentation, technology whitepapers, and relevant academic and trade literature to contextualize market trends and validate emerging use cases.
Data triangulation was applied to reconcile inputs from various sources, ensuring consistency and reducing bias through cross validation. Quantitative and qualitative insights were synthesized to develop detailed segmentation frameworks, regional profiles, and vendor maps. Expert panels were convened to peer review findings, challenge assumptions, and refine strategic recommendations. A final quality assurance stage verified the accuracy and currency of all content, supported by continuous editorial oversight to maintain clarity, coherence, and alignment with stakeholder requirements.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Identity & Access Management market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Identity & Access Management Market, by Offering
- Identity & Access Management Market, by Access Type
- Identity & Access Management Market, by Technology
- Identity & Access Management Market, by Deployment Mode
- Identity & Access Management Market, by Authentication Type
- Identity & Access Management Market, by End User
- Identity & Access Management Market, by Organization Size
- Identity & Access Management Market, by Region
- Identity & Access Management Market, by Group
- Identity & Access Management Market, by Country
- United States Identity & Access Management Market
- China Identity & Access Management Market
- Competitive Landscape
- List of Figures [Total: 19]
- List of Tables [Total: 1749 ]
Synthesizing Key Takeaways and Forward Looking Conclusions that Reinforce the Strategic Value of Identity and Access Management Initiatives
This executive summary has synthesized the critical developments, segmentation insights, regional nuances, and vendor strategies defining the contemporary identity and access management ecosystem. It has underscored the importance of adopting adaptive, context driven security controls, embracing cloud delivered architectures, and integrating advanced analytics to counter escalating cyber threats. The analysis of tariff impacts has highlighted the growing impetus toward software centric approaches and supply chain diversification, while the segmentation review has illuminated priority areas for investment across components, deployment modes, organization sizes, and industry verticals.
Ultimately, a holistic identity strategy that balances security, compliance, and user experience will be instrumental in safeguarding digital assets and sustaining competitive advantage. The actionable recommendations and methodological rigor presented herein provide a roadmap for decision makers to elevate their IAM initiatives. As enterprises navigate an increasingly complex threat landscape and evolving regulatory environment, this report offers the strategic perspective and practical guidance needed to drive measurable improvements in enterprise security posture.
Empowering Decision Makers to Unlock Advanced Identity and Access Management Perspectives Through a Personalized Discussion with Associate Director Ketan Rohom
If you are ready to deepen your understanding of the identity and access management market and gain actionable guidance tailored to your strategic priorities, reach out to Ketan Rohom, Associate Director of Sales & Marketing. Engaging in a personalized discussion will afford you exclusive access to the comprehensive research findings, rich segmentation insights, and forward-looking recommendations distilled from this analysis. By partnering directly with an expert, you can align these insights with your organizational objectives and accelerate your security roadmap with clarity and confidence.
Schedule a conversation with Ketan Rohom today to secure your competitive edge and ensure your identity and access management strategy is poised for sustained success.

- How big is the Identity & Access Management Market?
- What is the Identity & Access Management Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




