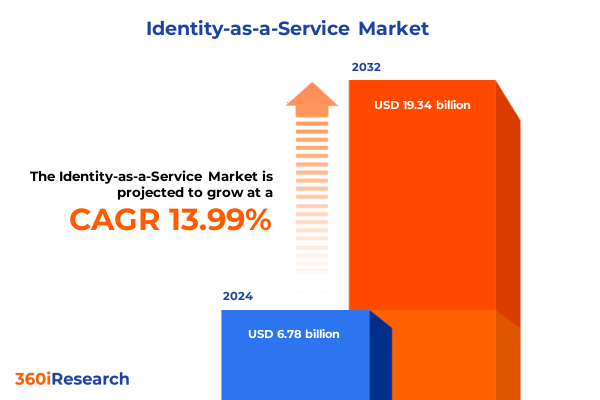
The Identity-as-a-Service Market size was estimated at USD 7.69 billion in 2025 and expected to reach USD 8.73 billion in 2026, at a CAGR of 14.08% to reach USD 19.34 billion by 2032.
Charting the Emerging Landscape of Identity-as-a-Service and Its Role in Shaping Secure, Scalable, and Agile Access Frameworks for Modern Enterprises
Identity-as-a-Service has rapidly emerged as a cornerstone of modern security and access management strategies, enabling organizations to unify authentication, authorization, and governance in a cloud-centric paradigm. As enterprises accelerate digital transformation initiatives, the need for a scalable, flexible, and secure identity framework becomes paramount. Today’s threat landscape, characterized by sophisticated attacks on user credentials and lateral movement within networks, demands a comprehensive solution that extends beyond traditional on-premises deployments.
In parallel, evolving workforce models-driven by remote and hybrid arrangements-have displaced the traditional network perimeter, rendering legacy identity systems insufficient. Organizations must now adopt an approach that centralizes identity control while delivering seamless user experiences across diverse applications and devices. Moreover, regulatory and compliance pressures continue to intensify, compelling security leaders to adopt integrated solutions that offer visibility, audit readiness, and granular policy enforcement.
Ultimately, the rise of Identity-as-a-Service signifies a shift toward proactive identity management, where organizations can leverage orchestration, analytics, and automation to mitigate risks and optimize operational efficiency. This executive summary outlines the critical drivers and market dynamics shaping the Identity-as-a-Service landscape, equipping decision-makers with the insights needed to navigate this transformative domain.
Recognizing the Pivotal Technological and Operational Inflection Points Redefining Identity-as-a-Service in a Rapidly Changing Security Environment
The Identity-as-a-Service market is undergoing transformative shifts driven by the convergence of zero trust security principles, cloud-native development models, and artificial intelligence–powered threat intelligence. Zero trust architectures compel organizations to adopt continuous authentication mechanisms and least-privileged access policies, thereby elevating the role of identity as the new security perimeter. Consequently, vendors are integrating risk-based adaptive authentication and behavioral analytics to detect anomalies in real time and to enforce dynamic access controls.
In parallel, the proliferation of cloud-native microservices and API-driven ecosystems has generated demand for extensible identity platforms that facilitate secure interoperability across heterogeneous environments. Identity providers are responding by offering robust APIs and developer toolkits that support rapid integration, customization, and orchestration, enabling organizations to embed identity workflows directly into their applications. Furthermore, the rise of passwordless authentication methods, including biometric verification and hardware-based cryptographic tokens, is redefining user experience expectations and reducing reliance on legacy credentials.
Moreover, regulatory requirements such as data residency, privacy, and auditability are shaping solution roadmaps. Organizations operating across global jurisdictions must ensure their identity deployments adhere to evolving frameworks for data protection and access governance. As a result, we observe a growing emphasis on identity governance and administration capabilities, encompassing policy creation, certification workflows, and entitlement management. These combined shifts underscore the need for holistic, forward-looking Identity-as-a-Service strategies that align security, compliance, and user productivity.
Assessing How the United States Tariff Escalations Announced for 2025 Are Exerting Broad Economic Pressure on Identity-as-a-Service Ecosystem Dynamics
The cumulative impact of the tariff adjustments implemented by the United States in 2025 has exerted significant economic pressure across the supply chains fundamental to Identity-as-a-Service solutions. A substantial portion of the hardware-such as servers, network switches, and storage arrays-relies on semiconductor and components sourced from international manufacturers. Tariffs on these imports have driven higher procurement costs for original equipment manufacturers, catalyzing trickle-down effects that elevate capital expenditures for cloud service providers and data center operators.
As vendors grapple with these increased input costs, many have shifted toward strategic inventory management and diversified sourcing strategies. Supply chain lead times have lengthened, compelling organizations to reassess deployment timelines for new service rollouts and to buffer for contingency planning. In turn, Identity-as-a-Service providers must balance cost absorption with competitive pricing models, often leading to tiered service offerings or bundled subscription packages that realign feature sets against customer budgets.
Furthermore, the uncertainty surrounding prospective tariff escalations has prompted some vendors to explore onshoring or nearshoring of component manufacturing to mitigate trade exposure. This strategic pivot not only affects the total cost of ownership but also introduces new variables in vendor reliability and delivery schedules. Ultimately, the 2025 tariffs have reshaped procurement dynamics and underscored the need for resilient supplier ecosystems, compelling Identity-as-a-Service providers to innovate in both product architecture and operational agility.
Revealing the Crucial Segmentation Perspectives That Define Component, Authentication, Deployment, Organizational, and Industry Dimensions of Identity-as-a-Service
The Identity-as-a-Service market can be understood through a detailed segmentation framework that begins with core components categorized into services and solutions. Services encompass offerings such as compliance and audit readiness, which ensure regulatory adherence, and customization and API development, designed to tailor identity workflows to unique use cases. Deployment and integration services facilitate seamless onboarding across hybrid environments, while identity strategy and advisory engagements provide high-level roadmaps for secure digital transformation. Managed Identity-as-a-Service services deliver ongoing operational support and optimization for customers seeking to outsource day-to-day identity administration.
Solutions span multiple technology domains, including cloud infrastructure entitlement management (CIEM), which oversees permissions across dynamic cloud environments, and identity and access management (IAM) platforms that unify authentication and authorization. Identity governance and administration (IGA) solutions provide visibility into user entitlements and support policy enforcement through lifecycle management processes. Identity threat detection and response (ITDR) tools integrate analytics to uncover suspicious activity, while multi-factor authentication (MFA) and privileged access management (PAM) enhance the security of high-risk credentials. Single sign-on (SSO) solutions, meanwhile, streamline user access journeys across diverse applications.
Authentication mechanisms further differentiate offerings between multi-factor and single-factor approaches. Multi-factor authentication solutions emphasize layered security by combining knowledge, possession, or inherence factors, whereas single-factor solutions often leverage existing credentials for rapid user onboarding. Deployment mode represents a critical axis of choice, with cloud-based identity services offering elasticity and managed upgrades, contrasted against on-premises deployments that may better satisfy stringent data residency or latency requirements.
Organizational size also influences solution requirements, as large enterprises typically demand extensive customization, broad integrations, and high-volume support, while small and medium enterprises often seek packaged offerings with rapid time to value and simplified management. Across industry verticals, specific use cases emerge: banking, financial services, and insurance organizations rely on robust governance to meet regulatory mandates; government and defense entities prioritize stringent access controls; healthcare providers focus on securing patient data while enabling clinician productivity; IT and telecommunication firms drive developer-centric integrations; and retail and e-commerce businesses emphasize frictionless customer journeys.
This comprehensive research report categorizes the Identity-as-a-Service market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Authentication Type
- Deployment Mode
- Organization
- Industry Vertical
Understanding Regional Adoption Patterns and Regulatory Imperatives Shaping Identity-as-a-Service Deployment Across the Americas, EMEA, and Asia-Pacific
In the Americas, the Identity-as-a-Service market benefits from mature cloud infrastructures, robust funding environments, and well-established regulatory frameworks. North American enterprises lead adoption, propelled by high-profile security breaches that underscore the need for advanced identity controls. Meanwhile, Latin American organizations demonstrate growing interest in cloud-driven models to modernize legacy systems, with accelerated digital initiatives in banking and retail sectors. This region’s emphasis on data privacy regulations, such as state-level consumer protection laws, further amplifies demand for integrated identity governance and audit capabilities.
Europe, the Middle East, and Africa present a complex tapestry of adoption drivers, shaped by stringent data protection legislation such as the General Data Protection Regulation and diverse sovereignty requirements across nations. European enterprises are increasingly investing in vendor-neutral, interoperable identity frameworks that support cross-border operations and compliance with local mandates. In the Middle East, government-led digital transformation programs emphasize secure citizen and workforce identity platforms, while African markets are experiencing nascent adoption, with telecom operators integrating identity services to expand digital financial inclusion and address-first identity use cases.
The Asia-Pacific region exhibits some of the fastest growth trajectories, driven by rapid cloud penetration, widespread mobile usage, and progressive e-governance initiatives. Large technology conglomerates are partnering with global identity vendors to deliver localized solutions that comply with varied regulatory landscapes. Moreover, the proliferation of fintech and telemedicine platforms accelerates demand for scalable authentication services that can accommodate high transaction volumes. Consequently, APAC organizations place significant emphasis on platform resilience and on-the-ground integration services to support hybrid deployments across urban and emerging markets.
This comprehensive research report examines key regions that drive the evolution of the Identity-as-a-Service market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Analyzing Strategic Positioning and Innovation Trajectories of Leading Technology Providers Driving Competitive Differentiation in the Identity-as-a-Service Market
Leading providers in the Identity-as-a-Service space have each carved out distinct competitive advantages through innovation, strategic partnerships, and specialized service offerings. Some vendors differentiate themselves by offering comprehensive identity governance suites that integrate certification, policy management, and entitlement analytics into a cohesive platform. Others place a premium on advanced threat detection and response capabilities, leveraging machine learning algorithms to identify anomalous access patterns and to trigger automated remediation workflows.
In parallel, several technology leaders have expanded their footprints through targeted acquisitions, incorporating niche capabilities-such as privileged access management or cloud entitlement oversight-into broader identity ecosystems. This consolidation trend underscores the market’s drive toward all-in-one platforms that simplify vendor management and streamline integration. Partnerships with major cloud hyperscalers have also emerged as a key strategy, enabling identity vendors to deliver native integrations and joint go-to-market initiatives that enhance product visibility and accelerate customer adoption.
Emerging players are challenging incumbents by focusing on innovative authentication modalities, such as decentralized identity models that empower users with self-sovereign credentials. These entrants often adopt agile delivery methodologies and open-source foundations, compelling established providers to evolve their roadmaps and to support extensible architectures. Collectively, this dynamic competitive landscape spurs continuous advancement, driving the development of interoperable, intelligence-driven Identity-as-a-Service solutions that can meet the evolving needs of diverse enterprise environments.
This comprehensive research report delivers an in-depth overview of the principal market players in the Identity-as-a-Service market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Alloy, Inc.
- CyberArk Software Ltd.
- Delinea Inc.
- Entrust Corporation
- Google LLC by Alphabet Inc.
- Hive Identity, Inc.
- Incode Technologies, Inc.
- International Business Machines Corporation
- JenID Solutions GmbH
- Jumio Corporation
- JumpCloud, Inc.
- Microsoft Corporation
- Okta, Inc.
- One Identity LLC
- OneLogin, Inc.
- Oracle Corporation
- Ping Identity Holding Corp.
- SailPoint Technologies Holdings, Inc.
- Salesforce, Inc.
- Semperis, Inc.
- SEON Technologies, Inc.
- Simeio Solutions, LLC
- TeleSign Corporation
- Trulioo Information Services, Inc.
- Veriff, Inc.
Providing Actionable Strategic Imperatives to Guide Industry Leaders in Accelerating Adoption, Enhancing Security Posture, and Maximizing Value from Identity-as-a-Service Investments
Industry leaders should prioritize the adoption of a zero trust framework that places identity at the center of security strategy. By implementing continuous risk-based authentication and least-privilege access controls, organizations can reduce attack surfaces and limit lateral movement. Additionally, integrating identity governance into the core security fabric ensures that access policies remain aligned with evolving compliance requirements and organizational roles.
To capitalize on emerging opportunities, organizations must enhance their identity analytics capabilities. Leveraging AI-driven behavioral insights enables proactive detection of anomalous activities and automated response mechanisms. Simultaneously, investing in developer-friendly APIs and SDKs fosters seamless integration of identity workflows into bespoke applications, driving productivity and lowering operational bottlenecks. Furthermore, exploring passwordless and biometric-driven authentication modalities can elevate user experience while strengthening security.
Finally, establishing robust partnerships with identity and cloud service vendors can accelerate time to value and reduce integration complexity. Engaging in collaborative advisory engagements ensures that roadmaps reflect industry best practices and emerging threat trends. By balancing technological innovation with a user-centric approach, organizations can maximize ROI on Identity-as-a-Service investments and position themselves for sustained resilience in an increasingly digital economy.
Detailing a Rigorous and Transparent Research Methodology Underpinning Market Analysis Through Systematic Data Collection, Validation, and Expert Collaboration Processes
This analysis is grounded in a hybrid research methodology that combines primary and secondary data collection with rigorous validation protocols. Our team conducted in-depth interviews with senior security executives, IT architects, and industry analysts to capture firsthand perspectives on adoption drivers, pain points, and solution requirements. These qualitative insights were complemented by a comprehensive review of vendor documentation, regulatory publications, and thought leadership reports to ensure contextual accuracy.
Quantitative data was triangulated through targeted surveys distributed to a broad spectrum of enterprises, spanning multiple industries and geographic regions. Responses were systematically analyzed to identify trends in deployment preferences, budget allocations, and anticipated technology roadmaps. Throughout the process, we applied strict quality controls, including cross-validation of data points, peer review, and alignment with publicly available benchmarks to ensure the robustness and reliability of our findings.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Identity-as-a-Service market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Identity-as-a-Service Market, by Component
- Identity-as-a-Service Market, by Authentication Type
- Identity-as-a-Service Market, by Deployment Mode
- Identity-as-a-Service Market, by Organization
- Identity-as-a-Service Market, by Industry Vertical
- Identity-as-a-Service Market, by Region
- Identity-as-a-Service Market, by Group
- Identity-as-a-Service Market, by Country
- United States Identity-as-a-Service Market
- China Identity-as-a-Service Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1272 ]
Summarizing Key Insights and Strategic Takeaways Highlighting How Identity-as-a-Service Drives Secure and Agile Business Transformations
In conclusion, Identity-as-a-Service has reached a critical juncture as organizations navigate an increasingly complex security and regulatory landscape. The convergence of zero trust principles, cloud-native architectures, and AI-driven threat intelligence is accelerating the evolution of identity platforms. As businesses grapple with supply chain disruptions and tariff pressures, the agility and resilience offered by cloud-based identity services have never been more valuable.
By understanding the nuanced segmentation across components, authentication methods, deployment modes, organizational sizes, and industry verticals, enterprises can craft a tailored identity strategy that balances security, compliance, and user experience. Regional considerations and competitive dynamics further inform decision-making, guiding investments in the most impactful areas. Ultimately, organizations that adopt a strategic, data-driven approach to Identity-as-a-Service will unlock new levels of operational efficiency and risk mitigation.
Inviting Stakeholders to Connect with Associate Director Ketan Rohom for Personalized Insights and Access to a Detailed Identity-as-a-Service Market Research Report
I appreciate your interest in exploring the comprehensive insights our Identity-as-a-Service market research report offers. To discuss how these findings can address your organization’s unique challenges and to gain early access to in-depth analysis, I invite you to connect directly with Associate Director, Sales & Marketing, Ketan Rohom. By engaging in a personalized consultation, you will receive tailored recommendations that align with your strategic objectives and technology priorities.
Let’s arrange a meeting to explore how our detailed study can inform your decision-making, refine your security roadmap, and position your enterprise ahead of emerging identity and access management trends. Reach out to Ketan Rohom today to secure your copy of the report and benefit from our expert guidance in unlocking the full potential of Identity-as-a-Service.

- How big is the Identity-as-a-Service Market?
- What is the Identity-as-a-Service Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




