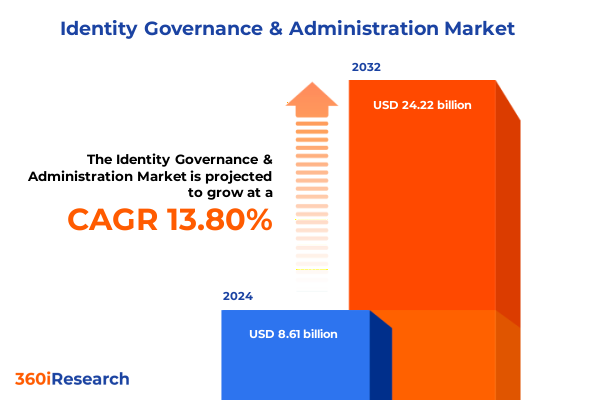
The Identity Governance & Administration Market size was estimated at USD 9.74 billion in 2025 and expected to reach USD 11.04 billion in 2026, at a CAGR of 13.89% to reach USD 24.22 billion by 2032.
Setting the Stage for Identity Governance & Administration: Navigating Complexities and Embracing Innovation in a Rapidly Evolving Security Landscape
In an era where digital identities constitute the bedrock of enterprise operations, understanding the evolving landscape of identity governance and administration is no longer optional-it is critical. Organizations are grappling with the dual challenge of granting seamless access to legitimate users while simultaneously thwarting sophisticated threats that exploit identity weaknesses. The proliferation of cloud services, remote work models, and hybrid infrastructures has magnified the complexity of managing user lifecycles, reinforcing the imperative for a unified approach that balances agility with rigorous controls.
As identity footprints expand across SaaS applications, on-premises systems, and emerging platforms, decision makers are recalibrating their strategies to embrace automation, real-time analytics, and risk-based policies. These developments are driven by regulatory pressures, including data privacy mandates and industry-specific compliance frameworks, which demand granular visibility into who has access to what resources and why. The introduction sets the stage for a deeper exploration into the transformative forces reshaping identity governance capabilities, the implications of recent policy shifts such as tariffs, and the segmentation and regional nuances that define modern deployment scenarios.
This introduction serves as the compass for security leaders, offering a concise orientation to the critical themes and insights that follow. By laying out the foundational challenges and opportunities, it primes stakeholders for a systematic examination of how technological innovation, market dynamics, and strategic imperatives converge to redefine identity governance in today’s threat landscape.
Unleashing the Next Wave of Security Evolution: How Artificial Intelligence, Zero Trust and Cloud Strategies Are Redefining Identity Governance Processes
The identity governance arena is experiencing a seismic shift as artificial intelligence and machine learning capabilities are infused into policy engines and access controls. These technologies automate repetitive tasks such as access certification, recertification, and anomaly detection, freeing security teams to focus on strategic initiatives. Concurrently, the principles of Zero Trust have moved from theoretical frameworks to operational mandates, driving organizations to assume breach and continuously validate every transaction-be it user access, privileged account activity, or third-party integrations.
Cloud-native architectures are reshaping the deployment paradigm, enabling quicker provisioning of services and more scalable lifecycle management for identities. This shift is complemented by the surge in passwordless authentication solutions, which leverage biometric modalities and cryptographic tokens to reduce reliance on static credentials. At the same time, policy management is becoming more contextual, incorporating behavioral analytics and risk scoring to dynamically adjust access based on real-time signals.
Together, these transformative shifts are forging a new blueprint for identity governance: one that is proactive, adaptable, and intelligence-driven. Organizations that embrace these changes will position themselves to not only respond to emerging threats more effectively but also to capitalize on the agility that modern digital business models demand. The ensuing sections will build upon this foundation, examining the broader market impacts and strategic considerations that stem from these evolutionary forces.
Assessing the Ripple Effects of New United States Tariffs in 2025 on Global Supply Chains and Technology Procurement in Identity Governance Solutions
In 2025, the introduction of revised United States tariffs on imported technology components has exerted notable pressure on the procurement and deployment of identity governance platforms. Hardware security modules, cryptographic accelerators, and certain purpose-built appliances sourced from key manufacturing hubs have seen cost increases, compelling many organizations to reevaluate their investment timelines and total cost of ownership calculations. These adjustments have catalyzed a wider shift toward software-only and cloud subscription models, reducing dependency on tariff-impacted hardware deliveries.
Simultaneously, vendors have restructured supply chains and sought alternative partnerships to mitigate escalating duties. This realignment has accelerated negotiations with regional distributors and fueled interest in domestically produced appliances that fall outside the scope of newly imposed levies. For enterprises, the cumulative effect has been a renewed emphasis on cloud-first strategies-particularly for on-demand provisioning of identity governance capabilities-and a tighter integration of lifecycle management features within broader security service platforms.
As organizations adapt to these economic headwinds, they are also leveraging policy management and role management functions to optimize licensing footprints and align access request workflows with evolving budgetary constraints. While the initial tariff impacts introduced short-term procurement delays, they have ultimately underscored the resilience afforded by cloud environments and the necessity of flexible deployment models. The following insights will delve deeper into how these market adjustments interplay with segmentation dynamics and regional considerations.
Unveiling Critical Market Segments: How Services, Deployment Models and Industry Verticals Shape Identity Governance Strategies Across Enterprises
A nuanced understanding of how offerings, components, deployment approaches, enterprise scale, and industry verticals intersect is vital to deciphering the identity governance landscape. Across the spectrum of services and solutions, organizations demand a blend of managed and professional services to support both day-to-day operations and strategic initiatives. This dual emphasis has given rise to advisory engagements focused on policy frameworks as well as ongoing managed operations that ensure continuous certification and recertification of user entitlements.
On the component front, access certification and recertification remain cornerstone capabilities, working in concert with access request portals, lifecycle management engines, and password management tools. Policy management and role management modules provide the governance spine, while user provisioning automates the translation of approved requests into system-level rights. Each of these modules carries distinct maturity trajectories, with market participants prioritizing integrated suites that minimize silos and streamline administrative overhead.
Deployment preferences further stratify the market into cloud and on-premises models, reflecting divergent risk appetites and compliance postures. Large enterprises frequently maintain hybrid architectures to balance control with elasticity, whereas small and medium organizations gravitate toward cloud subscriptions to reduce infrastructure burdens. Vertical-specific requirements add another layer of complexity: BFSI institutions, including banks, fintech enterprises, and insurance firms, demand stringent audit trails; healthcare and life sciences entities such as hospitals, clinics, and pharmaceutical companies emphasize data privacy and consent management; and sectors from retail and e-commerce to energy utilities uphold their own regulatory frameworks.
Together, these segmentation dimensions illuminate the pathways by which organizations tailor identity governance strategies to their unique operational, regulatory, and technological contexts.
This comprehensive research report categorizes the Identity Governance & Administration market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Offering
- Component
- Deployment Model
- Enterprise Size
- Industry Vertical
Regional Dynamics Redefined: Examining How Americas, Europe Middle East Africa and Asia Pacific Drive Unique Identity Governance Demands
Regional dynamics are exerting a profound influence on identity governance priorities, driven by distinct regulatory landscapes, threat ecosystems, and digital maturity levels. In the Americas, privacy regulations such as the California Consumer Privacy Act and sector-specific rules for financial services heighten the demand for comprehensive audit capabilities and stringent access recertification protocols. This environment fuels rapid cloud adoption, as enterprises seek scalable solutions that can enforce policies consistently across disparate geographies.
In Europe, the Middle East, and Africa, the interplay of GDPR-inspired directives, emerging data localization requirements, and rising cyberthreats has galvanized investments in policy management and role-based access controls. Governments and public sector entities are accelerating modernization programs, integrating identity governance within broader Zero Trust architectures. Meanwhile, regional vendors are capitalizing on local compliance expertise, offering tailored services that address language diversity and complex jurisdictional nuances.
Across Asia-Pacific, digital transformation agendas in manufacturing, telecom, and retail amplify the need for agile lifecycle management and robust user provisioning frameworks. Cloud-native deployments dominate in growth markets, enabling rapid onboarding of partners and contractors. At the same time, energy and utilities firms in mature economies, along with large academic institutions, maintain hybrid deployments to serve both legacy systems and progressive digital initiatives.
These regional insights highlight the imperative for vendors to deliver adaptable solutions that address heterogeneous regulatory requirements, cultural expectations, and technology landscapes, ensuring identity governance frameworks remain both compliant and resilient.
This comprehensive research report examines key regions that drive the evolution of the Identity Governance & Administration market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Spotlight on Leading Identity Governance Innovators: How Pioneering Vendors Are Shaping Solutions with Strategic Partnerships and Advanced Capabilities
Leading vendors in the identity governance arena are distinguishing themselves through strategic alliances, modular architectures, and investment in cutting-edge analytics. Market innovators are forging partnerships with cloud hyperscalers to embed native APIs and accelerate integration across diverse SaaS and IaaS platforms. Concurrently, acquisitions of specialized cybersecurity startups are infusing policy engines with advanced behavioral analytics, enabling real-time risk scoring that adapts to evolving threat vectors.
A select group of providers has focused on expanding professional service portfolios, offering advisory engagements that align identity governance roadmaps with broader digital transformation objectives. These service-oriented strategies underscore the shift toward outcome-based engagements, where vendors assume partial accountability for ongoing compliance outcomes and user experience enhancements. In parallel, solution providers are enhancing interoperability with complementary tools such as privileged access management and security information and event management, constructing cohesive security stacks that reduce vendor sprawl.
Investment in user experience has emerged as a key differentiator, with vendors streamlining access request workflows through intuitive interfaces and mobile-first designs. This focus not only accelerates end-user adoption but also reduces operational friction for IT administrators. Collectively, these strategic moves illustrate how leading companies are cementing their positions by delivering flexible, data-driven, and user-centric identity governance solutions that align with enterprise risk and compliance imperatives.
This comprehensive research report delivers an in-depth overview of the principal market players in the Identity Governance & Administration market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Broadcom Inc.
- Clear Skye Inc.
- Eviden SAS
- ForgeRock, Inc.
- Fortra, LLC
- GuidePoint Security, LLC
- Identity Automation, Inc.
- IDM Technologies
- International Business Machines Corporation
- Microsoft Corporation
- Okta, Inc.
- Omada A/S
- One Identity LLC
- OneLogin, Inc.
- OpenText Corporation
- Optiv Security Inc.
- Oracle Corporation
- Ping Identity Holding Corp.
- RSA Security LLC
- SailPoint Technologies Holdings, Inc.
- Saviynt, Inc.
- Simeio Solutions, LLC
- SITS Group
- Tools4ever
- Zluri Technologies Pvt. Ltd
- Zoho Corporation
Strategic Imperatives for Security Leaders: Practical Steps to Harness Emerging Technologies and Strengthen Identity Governance Posture Across Organizations
To stay ahead in the dynamic identity governance market, security leaders must prioritize a series of strategic actions that bridge technology, process, and people dimensions. First, they should advance their Zero Trust initiatives by embedding continuous authentication and dynamic policy enforcement into every access decision, thereby reducing attack surfaces and limiting lateral movement. Embracing AI-powered analytics will further enhance the ability to detect anomalous behavior early, minimizing the window of opportunity for malicious actors.
Next, organizations should evaluate their portfolio of services versus solutions, ensuring that managed operations can complement in-house expertise and professional services engagements can expedite strategic transformations. A hybrid deployment approach may offer the optimal balance between centralized control and on-demand scalability, particularly for enterprises facing complex compliance mandates and global footprints. It is equally important to harmonize policy management, role management, and lifecycle orchestration to streamline governance processes and reduce administrative overhead.
Finally, leaders should invest in user experience enhancements that simplify access requests and leverage risk-based authentication methods, such as passwordless and adaptive MFA, to improve security without impeding productivity. Regularly reviewing and refining segmentation strategies-by enterprise size, vertical industry requirements, and component maturity-will ensure that identity governance programs remain aligned with evolving business objectives. By following these recommendations, organizations can fortify their security posture while enabling the agility required in today’s digital-first environment.
Underpinning Rigor and Transparency: A Comprehensive Overview of the Qualitative and Quantitative Approaches Guiding Identity Governance Research
The insights presented in this report are grounded in a rigorous research methodology that integrates both qualitative and quantitative evidence. Primary data was gathered through in-depth interviews with senior security and IT executives across industries, as well as structured surveys capturing the perspectives of over one hundred enterprise practitioners. These engagements provided firsthand accounts of challenges in access certification, lifecycle management, and policy enforcement, enabling precise calibration of technology adoption trends and operational pain points.
Complementing this, a comprehensive review of vendor documentation, regulatory publications, and industry thought leadership articles formed the basis of secondary research. Publicly available whitepapers, analyst briefings, and academic studies were systematically analyzed to contextualize market dynamics, identify regulatory shifts, and map emerging technological innovations. Data validation techniques, including triangulation across multiple sources and cross-functional peer reviews, ensured the integrity and reliability of all findings.
Finally, the research process incorporated iterative feedback loops with security practitioners and domain experts, refining the report’s structure and enhancing the relevance of actionable recommendations. This multi-stage approach guarantees that the conclusions and insights reflect both empirical rigor and practical applicability, equipping decision makers with a robust foundation for identity governance strategy development.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Identity Governance & Administration market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Identity Governance & Administration Market, by Offering
- Identity Governance & Administration Market, by Component
- Identity Governance & Administration Market, by Deployment Model
- Identity Governance & Administration Market, by Enterprise Size
- Identity Governance & Administration Market, by Industry Vertical
- Identity Governance & Administration Market, by Region
- Identity Governance & Administration Market, by Group
- Identity Governance & Administration Market, by Country
- United States Identity Governance & Administration Market
- China Identity Governance & Administration Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1431 ]
Synthesis of Evolving Priorities and Future Readiness: Consolidating Insights to Empower Decision Makers in Crafting Robust Identity Governance Frameworks
The journey through the evolving identity governance landscape underscores the imperative of balancing innovation with disciplined controls. From the integration of AI-enhanced policy engines to the adoption of Zero Trust principles, organizations are rewriting the rules of access and entitlement management. The influence of United States tariffs in 2025 has further highlighted the resilience that cloud-centric strategies and flexible deployment models can deliver in mitigating external cost pressures.
Segment-specific considerations-spanning services, components, deployment preferences, enterprise scale, and industry verticals-reveal the nuanced ways in which organizations tailor their identity governance roadmaps. Regional insights emphasize the divergent regulatory imperatives and threat vectors that shape investment priorities across the Americas, EMEA, and Asia-Pacific. Leading vendors continue to innovate through partnerships, advanced analytics, and user-centric design, helping enterprises navigate complexity and accelerate digital transformation.
Collectively, the insights and recommendations articulated in this report provide a cohesive framework for security leaders to assess current capabilities, identify strategic gaps, and chart a path toward more resilient and agile identity governance programs. As digital ecosystems grow in scale and sophistication, the ability to govern identities with precision and foresight will remain a defining factor in organizational success.
Empower Your Organization with Actionable Insights: Connect with Ketan Rohom to Access the Complete Identity Governance Market Research Report Today
Engaging with Ketan Rohom, Associate Director of Sales & Marketing, offers you a direct pathway to unlock the strategic insights and actionable intelligence embedded within the full report on identity governance and administration. His expertise in aligning market intelligence with organizational objectives ensures that your investment drives measurable outcomes. By partnering with him, you will gain tailored guidance on integrating the report’s findings into your security roadmap, fortifying compliance postures, and accelerating digital transformation initiatives. Reach out to initiate a consultation, secure priority access to exclusive data visualizations, and customize the research results to your unique industry and operational needs. Let this dialogue be the catalyst for transformational change in how your enterprise governs, authenticates, and secures identities across complex environments.

- How big is the Identity Governance & Administration Market?
- What is the Identity Governance & Administration Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




