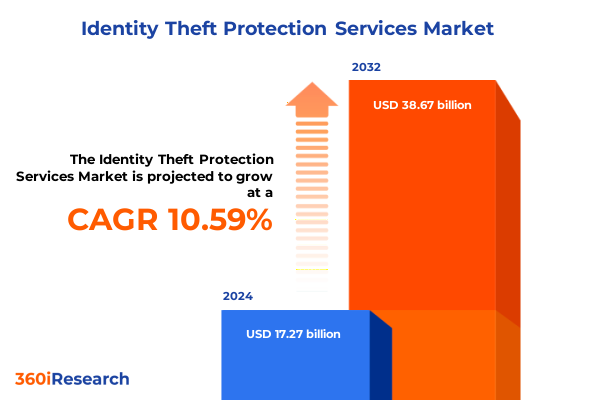
The Identity Theft Protection Services Market size was estimated at USD 19.12 billion in 2025 and expected to reach USD 20.82 billion in 2026, at a CAGR of 10.57% to reach USD 38.67 billion by 2032.
Unveiling the Critical Role of Identity Theft Protection Services in Safeguarding Personal and Corporate Digital Assets Worldwide
In an era where digital footprints have become as valuable as tangible assets, the imperative for robust identity theft protection services has never been more pronounced. Rapid digitization across consumer and enterprise spheres has accelerated the volume and velocity of personal data traversing online channels. Simultaneously, threat actors have evolved their techniques, transforming traditional fraud schemes into complex, multi-stage operations targeting every link in the identity lifecycle. As these dynamics intensify, organizations and individuals alike find themselves navigating an increasingly perilous landscape, where a single lapse can trigger cascading financial, legal, and reputational consequences.
Against this backdrop, identity theft protection services emerge as pivotal safeguards designed to detect, prevent, and remediate unauthorized use of personally identifiable information. From continuous credit monitoring and real-time alerts on public record changes to advanced dark web surveillance and social media scanning, providers are deploying a spectrum of solutions tailored to preempt evolving attack vectors. Beyond detection, comprehensive platforms integrate fraud resolution teams, identity restoration specialists, risk analytics engines, and stolen funds reimbursement policies, forming a cohesive defense mechanism. This foundational layer of protection not only mitigates direct monetary losses but also strengthens consumer confidence, regulatory compliance, and brand integrity in an age where trust is the ultimate currency.
Tracing the Emergence of New Threat Vectors and Technological Paradigm Shifts Reshaping Identity Theft Protection in 2025
The identity theft protection landscape is undergoing seismic transformation driven by emergent threat vectors and technological leaps. On one front, the proliferation of AI-driven phishing campaigns, deepfake-enabled impersonations, and synthetic identity fraud has outpaced traditional rule-based defenses. These sophisticated attacks leverage vast data repositories to craft highly personalized lures and synthetic personas that bypass conventional verification protocols. As a result, service providers are shifting toward advanced machine learning models capable of behavioral anomaly detection and predictive risk scoring, enabling earlier intervention and more nuanced threat classification.
Concurrently, privacy regulations and data protection mandates are reshaping solution architectures. Stricter requirements under domestic and international frameworks compel providers to embed robust encryption, consent management, and data minimization techniques into their platforms. This not only fortifies customer data against exfiltration but also enforces transparency and user control, reinforcing brand trust. Moreover, integrations with identity proofing technologies-such as biometric verification and multi-factor authentication-are becoming ubiquitous, offering frictionless user experiences without compromising security. These paradigm shifts collectively signal an industry in transition, where agility, intelligence, and privacy by design define the next generation of identity theft protection services.
Analyzing the Compound Effects of United States Tariff Adjustments Enacted in 2025 on the Identity Theft Protection Services Landscape
In 2025, newly imposed United States tariffs on select technology imports have reverberated across the identity theft protection services sector, catalyzing both cost pressures and strategic recalibrations. Service providers reliant on hardware components for on-premise appliances have encountered increased procurement costs, prompting a reassessment of infrastructure investments and service delivery models. Similarly, tariff-driven price escalations for network equipment and security appliances have nudged many enterprises toward cloud-based deployments, where economies of scale and flexible consumption models can absorb incremental duties more effectively.
These tariff adjustments have also influenced vendor sourcing strategies. Providers are seeking to diversify their supply chains, forging partnerships with regional hardware manufacturers and cloud infrastructure providers outside tariff constraints. This realignment enhances service resilience, reduces lead times, and mitigates geopolitical dependency. Clients, in turn, are reexamining their deployment roadmaps, weighing the total cost of ownership between direct on-premise investments and subscription-based cloud alternatives. As a result, the industry is witnessing a noteworthy acceleration in the adoption of cloud-first identity protection offerings, where scalability and cost predictability outweigh the upfront capital expenditures burdened by import tariffs.
Amid these shifts, forward-looking organizations are exploring hybrid architectures that combine localized appliance-based monitoring for sensitive data with cloud-hosted orchestration engines. This balanced approach enables critical assets to remain under direct control while leveraging the agility of cloud services to adapt to tariff-induced market fluctuations and evolving threat scenarios.
Unraveling Market Dynamics Through Multifaceted Segmentation to Illuminate Key Drivers and Service Preferences Across Diverse Customer Needs
A multifaceted view of the identity theft protection services domain reveals distinct service categories and deployment configurations tailored to diverse customer imperatives. Within the broader service taxonomy, offerings span credit monitoring, fraud resolution, identity monitoring, identity restoration, public records monitoring, risk analysis, and stolen funds reimbursement, with further granularity in credit monitoring separating report monitoring from score tracking and identity monitoring distinguishing dark web intelligence, public record alerts, and social media surveillance. Complementing these functional dimensions, end user profiles encompass government and defense entities requiring stringent compliance controls, individuals seeking personal data security, large enterprises balancing internal resource allocation with external expertise, and small to medium businesses aiming to safeguard their reputations with cost-effective solutions.
Deployment architectures bifurcate into cloud-based and on-premise models, reflecting varying preferences for operational control, scalability, and security posture. Organizations prioritizing minimal infrastructure overhead and rapid feature updates are gravitating toward cloud-native platforms, whereas those bound by regulatory or privacy mandates often opt for localized appliance-based installations. Distribution channels further differentiate service accessibility, with direct sales engagements providing bespoke customization and consultative support, while online portals deliver standardized packages optimized for ease of purchase and self-service onboarding. Understanding the interplay among these segmentation axes is instrumental in decoding buyer priorities, designing solution bundles, and calibrating go-to-market strategies that resonate across distinct customer cohorts.
This comprehensive research report categorizes the Identity Theft Protection Services market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Service Type
- End User
- Deployment Model
- Distribution Channel
Examining Regional Variances and Demand Patterns Across the Americas Europe Middle East and Africa and Asia Pacific to Guide Strategic Expansion
Regional dynamics in identity theft protection services reflect the nuanced interplay of regulatory environments, consumer awareness, and technological adoption across the Americas, Europe Middle East and Africa, and Asia Pacific. In the Americas, heightened consumer litigation and evolving federal and state privacy statutes drive robust demand for credit monitoring and identity restoration suites. U.S. enterprises, in particular, are integrating native data protection solutions with broader cybersecurity ecosystems, emphasizing seamless interoperability and centralized visibility.
Across Europe, the Middle East and Africa, stringent data privacy regimes underpinned by GDPR and regional directives have created a fertile ground for advanced identity monitoring services. Providers operating in this jurisdiction tailor their platforms to incorporate granular consent frameworks and purpose-limitation principles, while also accommodating multilingual support and local compliance workflows. In addition, burgeoning digital transformation initiatives in the Middle East are catalyzing investments in risk analysis and fraud resolution capabilities to safeguard rapid fintech expansion.
The Asia Pacific region is characterized by its digital-first consumer base and aggressive mobile adoption, which translates into high demand for dark web monitoring and real-time social media scanning. Enterprises across key markets such as Australia, Japan, and Singapore are forging strategic partnerships with global providers to localize threat intelligence feeds and expedite response times. Meanwhile, emerging economies within the region are leveraging public records monitoring solutions to underpin nascent identity verification frameworks and bolster financial inclusion efforts.
This comprehensive research report examines key regions that drive the evolution of the Identity Theft Protection Services market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting Competitive Strategies and Innovation Trajectories of Leading Identity Theft Protection Providers Shaping Industry Evolution
Leading players in the identity theft protection services sector are differentiating through a blend of technological innovation, strategic alliances, and service diversification. Established credit bureaus and data analytics firms have consolidated their positions by integrating proprietary data repositories with machine learning-driven risk scoring engines, enabling more precise threat identification. Concurrently, cybersecurity vendors are expanding their portfolios to include identity-centric modules, capitalizing on cross-selling opportunities within existing client bases.
Notable industry frontrunners are investing in proprietary dark web intelligence networks and forging partnerships with law enforcement agencies to accelerate fraud mitigation and identity restoration processes. Some have introduced white-label programs for financial institutions and insurance carriers, embedding turnkey identity protection modules into broader customer loyalty and insurance bundles. Others are pioneering behavioral biometrics and continuous authentication solutions to preempt emerging fraud tactics. On the distribution front, direct-to-consumer startups are gaining traction with subscription-based models complemented by mobile app interfaces, while enterprise-focused providers emphasize API-driven integrations and custom service-level agreements.
The competitive landscape is further evolving as specialized startups attract venture funding to develop niche capabilities-ranging from synthetic identity detection algorithms to real-time breach mapping dashboards-forcing incumbents to accelerate innovation cycles and consider mergers or acquisitions to maintain market relevance.
This comprehensive research report delivers an in-depth overview of the principal market players in the Identity Theft Protection Services market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Acronis International GmbH
- Allstate Corporation
- Aura Company LLC
- Bitdefender S.R.L.
- Equifax Inc.
- Eset spol. s r.o.
- Experian plc
- Fair Isaac Corporation
- Gen Digital Inc.
- Identity Guard
- IdentityForce Inc.
- IDnotify
- IDWatchdog Inc.
- Intuit Inc.
- Kaspersky Lab
- LegalShield
- LifeLock Inc.
- Malwarebytes Corporation
- McAfee Corp.
- OpenText Corporation
- PrivacyGuard
- TransUnion LLC
- Trend Micro Incorporated
- Zander Insurance Group Inc.
Strategic Recommendations Empowering Industry Leaders to Strengthen Resilience and Capitalize on Emerging Opportunities in Identity Theft Protection
Industry leaders must harness a proactive posture by embedding advanced analytics and automation into their identity protection frameworks to stay ahead of increasingly sophisticated threat actors. Investing in artificial intelligence and machine learning-driven anomaly detection can reduce incident response times and refine risk prioritization. Equally critical is the cultivation of strategic alliances with specialized data brokers and technology partners to expand monitoring coverage, enhance threat intelligence feeds, and support localized compliance requirements. By orchestrating a partner ecosystem, providers can deliver end-to-end solutions that address both global threat landscapes and regional regulatory nuances.
Furthermore, organizations should elevate user experience by streamlining onboarding processes and integrating frictionless identity proofing mechanisms-such as biometric verification and adaptive authentication-to minimize abandonment rates and foster enduring customer loyalty. Concurrently, a balanced deployment strategy that offers cloud-based agility alongside optional on-premise modules will cater to a broader spectrum of end users, from data-sensitive government agencies to dynamically scaling digital-native enterprises.
Finally, cultivating thought leadership through transparent reporting of threat trends, regulatory updates, and best practices will position solution providers as trusted advisors rather than mere vendors. By delivering educational content, interactive workshops, and certification programs, industry leaders can deepen customer engagement, drive upsell opportunities, and reinforce their brands as pillars of trust in the identity protection ecosystem.
Detailing Rigorous Research Methodologies Employed to Ensure Comprehensive Insights and Data Integrity in Identity Theft Protection Analysis
This research analysis synthesizes primary and secondary methodologies to present a holistic perspective on the identity theft protection services ecosystem. Secondary data collection encompassed a comprehensive review of public disclosures, regulatory filings, technology white papers, and cybersecurity incident repositories, ensuring that trend identification and contextualization were grounded in verifiable industry sources. Secondary findings were augmented by primary interviews with C-level executives, product managers, and cybersecurity specialists to capture nuanced insights into solution roadmaps, client pain points, and adoption barriers.
Quantitative surveys targeting end users across government, enterprise, and consumer segments provided statistical grounding for service preference patterns, deployment model viability, and channel effectiveness. Qualitative feedback from in-depth interviews and focus group discussions served to validate these quantitative trends, uncovering motivations, expectations, and experience-driven recommendations. Throughout the analysis, data triangulation techniques were employed to cross-verify findings and mitigate potential biases, while expert panels offered peer review to reinforce methodological rigor and analytical objectivity.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Identity Theft Protection Services market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Identity Theft Protection Services Market, by Service Type
- Identity Theft Protection Services Market, by End User
- Identity Theft Protection Services Market, by Deployment Model
- Identity Theft Protection Services Market, by Distribution Channel
- Identity Theft Protection Services Market, by Region
- Identity Theft Protection Services Market, by Group
- Identity Theft Protection Services Market, by Country
- United States Identity Theft Protection Services Market
- China Identity Theft Protection Services Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 1113 ]
Concluding Perspectives on the Imperative of Robust Identity Theft Protection Frameworks to Navigate Complexity and Foster Trust
As digital ecosystems continue to expand and threat actors leverage ever more sophisticated methods, the centrality of identity theft protection services to organizational resilience and consumer confidence cannot be overstated. The convergence of advanced analytics, regulatory imperatives, and user empowerment strategies underscores a pivotal moment in the industry’s evolution. Providers that successfully integrate proactive monitoring, rapid incident response, and seamless user experiences will differentiate themselves in a competitive landscape defined by trust and reliability.
Looking ahead, the interplay between artificial intelligence, biometric authentication and adaptive security frameworks promises to further elevate the efficacy of identity protection solutions. Concurrently, the global push for data privacy and consumer rights will catalyze innovation in consent-driven architectures and transparent service models. In this dynamic context, agile providers who align technological innovation with user-centric design and robust compliance protocols will be best positioned to navigate complexity, foster long-term relationships, and sustain growth.
Drive Informed Action Today by Engaging Ketan Rohom for Access to the Definitive Identity Theft Protection Services Market Research Report
To explore the full depth of this comprehensive analysis and secure a strategic advantage in the evolving identity theft protection services arena, reach out to Ketan Rohom, Associate Director, Sales & Marketing at 360iResearch. His expertise will guide you through tailored insights and enable you to access the definitive report, arming your organization with actionable intelligence and bespoke recommendations to safeguard digital assets and customer trust.

- How big is the Identity Theft Protection Services Market?
- What is the Identity Theft Protection Services Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




