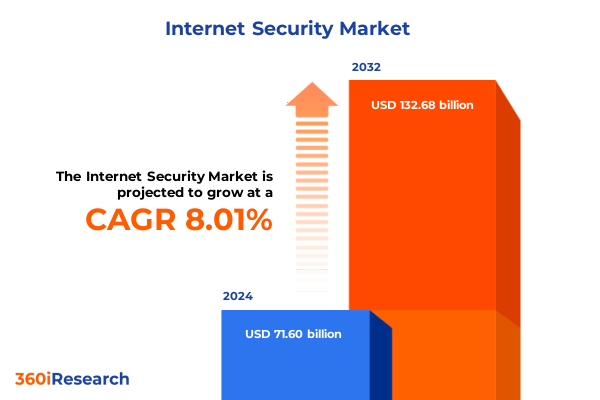
The Internet Security Market size was estimated at USD 77.05 billion in 2025 and expected to reach USD 82.93 billion in 2026, at a CAGR of 8.07% to reach USD 132.68 billion by 2032.
Unveiling the Digital Battlefield: Understanding How Remote Work, Cloud Proliferation, and AI-Powered Threats Are Reshaping Internet Security Strategies
The internet security landscape in 2025 has been radically transformed by the accelerated shift to remote work and hybrid cloud deployments. Organizations have had to balance agility and cost reduction with robust defense mechanisms, often making compromises in visibility, data quality, and seamless integration. Recent analysis reveals that 91% of security and IT leaders admit to sacrificing critical observability and robust telemetry capabilities in hybrid environments, underscoring systemic pressure on legacy tools and the need for more cohesive strategies.
Amid this transformation, cloud adoption remains at the forefront of enterprise risk management discussions. Over 70% of organizations now depend on cloud services to enable secure remote work infrastructures, driving unprecedented demand for cloud-native security solutions and multi-cloud governance frameworks. As AI-driven applications proliferate, sensitive data increasingly resides in dynamic environments, compelling security teams to reallocate budgets toward advanced threat detection and AI-specific defenses. More than half of enterprises report prioritizing AI security investments alongside foundational cloud protections to safeguard machine learning workloads and confidential assets.
This executive summary synthesizes the latest market dynamics by examining transformative shifts, the cumulative impact of U.S. trade policies, nuanced segmentation analyses, regional variations, and leading company initiatives. It offers actionable recommendations for industry leaders and outlines the rigorous research methodology employed. By weaving together stakeholder perspectives and empirical data, this report equips decision-makers with the insights needed to fortify cybersecurity postures and drive innovation in an ever-evolving threat environment.
From Perimeter Protection to AI-Driven Intelligence: Breakthrough Paradigms Transforming the Internet Security Landscape in Today’s Digital Era
As the threat landscape evolves, organizations are transitioning from perimeter-centric defenses to intelligence-driven security architectures. Zero-trust models have become imperative, abandoning the notion of implicit trust and enforcing strict identity verification, least‐privilege access, and microsegmentation across networks and cloud workloads. This paradigm shift demands not only new technologies but also cultural changes within enterprise operations to break down silos and foster continuous monitoring across hybrid environments.
At the same time, adversaries have accelerated their tactics, leveraging AI-driven reconnaissance and automation to compromise targets with alarming speed. Recent findings indicate that the average time for an attacker to move laterally within a network has dropped from over an hour to under 48 minutes, with the fastest recorded breach unfolding in just 51 seconds. Moreover, hands-on-keyboard activity eclipses malware payloads in most incidents, reflecting a shift toward targeted, stealthy intrusions that evade signature-based defenses.
Insider threats have also surged in frequency and sophistication, with 83% of organizations reporting at least one internal incident last year. These attacks exploit elevated privileges and weak monitoring controls, highlighting the ongoing need for behavioral analytics, rigorous access reviews, and comprehensive employee training programs to detect anomalous activities before they escalate into major breaches.
Concurrently, hybrid cloud environments are under mounting strain from AI-driven workloads, data sprawl, and divergent visibility gaps. A recent hybrid cloud security survey found that 91% of security leaders are actively recalibrating their risk strategies to address the complexity introduced by AI, underscoring the urgency of unified observability platforms that can correlate telemetry across on-premises, public cloud, and AI-based services.
Assessing the Cumulative Impact of 2025 U.S. Tariffs on Security Technologies, Supply Chains, and Industry Resilience Amid Trade Uncertainty
The resurgence of U.S. trade tariffs under the America First policy has introduced significant cost pressures across security hardware and integrated solutions. Beginning March 12, 2025, the reinstatement of 25% Section 232 tariffs on steel and aluminum imports has reverberated throughout manufacturing supply chains, driving up raw material costs for firewalls, server racks, and physical security enclosures.
Beyond metals, a series of country-specific and product-specific levies have expanded the tariff net to include components like automotive-grade electronics and specialized semiconductors. For instance, the administration’s early-2025 measures imposed a 10% tariff on a broad range of Chinese imports on February 4, followed by 20% on select Chinese goods in March, and bespoke rates above 10% for 57 additional nations in April. Executives note that these layered duties complicate procurement strategies and inventory planning, as exemptions remain limited and application processes are opaque.
Industry stakeholders have voiced deep concerns over the indirect impact on finished security products. The Security Industry Association has formally requested relief and product-specific exemptions, warning that higher component tariffs could inflate costs for alarms, access control systems, camera modules, and identity management tools. With the U.S. security industry supporting over 2.1 million jobs and generating more than $430 billion in economic activity, continued tariff volatility risks disrupting project timelines and availability of critical life-safety solutions.
The cumulative effect of these trade actions is mounting uncertainty, compelling suppliers and integrators to reevaluate sourcing corridors, stockpile critical parts, and pass costs downstream. While the policy aims to strengthen domestic manufacturing, the unintended consequence may be constrained innovation cycles and higher total cost of ownership for end users prioritizing resilient security architectures.
Decoding Security Market Dynamics Through Comprehensive Segmentation Insights Spanning Applications, Deployment, Organization Size, End Users, Threats, and Attack Vectors
The security market’s granular segmentation reveals the multifaceted nature of product and service adoption across enterprises. Application security is dissected into dynamic and static testing, runtime protection, and web application firewalls, each addressing layers of the software development lifecycle. Cloud security encompasses access brokers, posture management, workload protection, and identity solutions, reflecting the diverse guardrails required to secure cloud-native architectures. Endpoint defenses range from antivirus to advanced detection and response platforms, while network security spans firewalls, intrusion prevention, unified threat management, and encrypted VPN channels.
Deployment modes also vary according to organizational priorities, with pure public cloud, dedicated private cloud, and hybrid on-premises deployments offering distinct trade-offs in control, scalability, and compliance. Organizational size further influences buying behavior, as large enterprises pursue integrated platforms, whereas small and medium enterprises navigate resource constraints by selecting modular, cost-effective options. End-user sectors from financial services to healthcare and retail experience unique threat profiles, driving differential investments in custom solutions and managed services. Threat types encompass volumetric and application-layer DDoS, insider exploits, malware variants, and sophisticated phishing campaigns. Attack vectors span email attachments and link-based campaigns, mobile-based social engineering, network-level brute force and man-in-the-middle exploits, and web application vulnerabilities like cross-site scripting and SQL injection. Together, these segmentation dimensions underscore the necessity for a holistic approach to portfolio design, ensuring that security solutions align with granular use cases and evolving adversary tactics.
This comprehensive research report categorizes the Internet Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Security Type
- Deployment Mode
- Organization Size
- Threat Type
- Attack Vector
- End User
Exploring Regional Variations in Internet Security Adoption, Threat Profiles, and Investment Priorities Across Americas, EMEA, and Asia-Pacific Markets
Regional markets exhibit divergent maturity curves shaped by regulatory frameworks, digital transformation initiatives, and geopolitical drivers. In the Americas, North America retains its leadership position, commanding an estimated 37% of global security revenues. This dominance is underpinned by stringent disclosure mandates, such as SEC incident reporting requirements, and high-profile compliance regimes that compel organizations to allocate significant budgets toward multi-layered security stacks and incident response capabilities. Latin America, while still emerging, demonstrates strong growth potential with mid-teen projected CAGRs, fueled by digitalization efforts in banking, e-commerce, and critical infrastructure modernization.
Across Europe, the Middle East, and Africa, evolving regulatory landscapes and geopolitical tensions inform security investments. In the European Union, compliance with GDPR and NIS2 directives continues to drive demand for data protection and network segmentation technologies, while Middle Eastern economies ramp up national cybersecurity strategies to safeguard oil, gas, and financial sectors. Geopolitical frictions and rising state-sponsored threats have prompted 73% of regional CISOs to elevate cybersecurity as a board-level priority, investing in AI-enabled detection and threat intelligence platforms to anticipate increasingly sophisticated attacks.
In Asia-Pacific, rapid digitization and hyperscale cloud adoption have catalyzed a blistering 15.8% CAGR over recent years. Governments and enterprises across China, India, Japan, and ASEAN nations are embedding security by design into national initiatives and smart city projects, driving strong demand for cloud workload protection and identity-centric controls. The vibrancy of APAC markets is further buoyed by local innovation in secure access service edge architectures and virtualized firewalls targeting carrier networks and 5G infrastructures.
This comprehensive research report examines key regions that drive the evolution of the Internet Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Identifying Leading Internet Security Innovators: Key Company Profiles, Strategic Initiatives, and Competitive Positioning Shaping the Market
Leading vendors are converging around integrated, AI-infused platforms designed to unify threat detection, analysis, and response. CrowdStrike’s Falcon platform, built on adversary-focused telemetry, reported a 26% surge in cloud intrusions year-over-year, reinforcing the need for behavioral analytics and threat hunting across endpoints and workloads. Meanwhile, Palo Alto Networks has advanced its platformization strategy with the Prisma SASE suite, enabling secure access converged with zero-trust network access and cloud firewall capabilities, which has driven notable increases in enterprise multi-module contracts.
Fortinet continues to differentiate through its Security Fabric architecture, integrating AI-driven threat intelligence, secure SD-WAN, and embedded network operations center capabilities. The company’s recent partnerships with hyperscale cloud providers have extended its fabric reach into public cloud environments, enhancing visibility and enforcement for distributed sites. Check Point Software has responded to evolving threats with Infinity AI Copilot, embedding generative AI to accelerate threat detection, automate policy updates, and reduce mean time to remediation across hybrid architectures.
Cloud-native and identity-focused providers are also gaining momentum. Thales’s 2025 Cloud Security Study found that more than half of enterprises now rank AI security second only to cloud security in budget priority, underscoring the urgency of protecting machine-learning models and sensitive data flowing across cloud applications. This shift has opened opportunities for specialist platforms in identity and access management, where vendors leverage risk-based authentication and continuous adaptive controls to mitigate both external and insider threats.
This comprehensive research report delivers an in-depth overview of the principal market players in the Internet Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- Cloudflare, Inc.
- CrowdStrike Holdings, Inc.
- CyberArk Software Ltd.
- Darktrace plc
- FireEye, Inc.
- Fortinet, Inc.
- International Business Machines Corporation
- McAfee, LLC
- Microsoft Corporation
- Okta, Inc.
- Palo Alto Networks, Inc.
- Rapid7, Inc.
- SentinelOne, Inc.
- Symantec Corporation
- Tenable Holdings, Inc.
- Trend Micro Incorporated
- Zscaler, Inc.
Actionable Strategies for Industry Leaders to Strengthen Cyber Defenses, Drive Innovation, and Navigate Evolving Threats in an AI-Driven Security Ecosystem
Industry leaders should prioritize the adoption of zero-trust architectures to eliminate implicit trust and reduce lateral movement risks. Implementing continuous identity verification, microsegmentation, and least-privilege access controls can significantly lower the attack surface and improve incident containment efficiency. Strengthening identity intelligence should be complemented by behavior-based analytics and adaptive IAM policies to counter increasingly sophisticated credential-based threats.
Organizations must also align security and development teams to integrate robust DevSecOps practices. Embedding static and dynamic application security testing into continuous integration pipelines ensures early detection of vulnerabilities, while runtime protection and web application firewalls safeguard production environments. By fostering cross-functional accountability, enterprises can accelerate innovation without compromising risk management.
Given the persistent skills gap, companies should invest in workforce development programs, prioritizing upskilling in cloud and AI security domains. Two-thirds of organizations report moderate to critical talent shortages, with only 14% confident in their existing skill sets. Establishing continuous training, leveraging automation to augment scarce human resources, and partnering with academic institutions can help bridge the talent divide and future-proof cyber resilience.
Finally, security investments must adapt to shifting geopolitical and trade landscapes. Businesses with global supply chains should incorporate tariff risk analyses into procurement decisions and explore localized sourcing or dual-sourcing strategies to mitigate potential price shocks. Engaging with trade associations and advocating for pragmatic exemption processes can also preserve access to essential components and stabilize project costs.
Defining Rigorous Research Methodology: Integrating Primary Interviews, Secondary Data Analysis, and Expert Validation to Ensure Data Integrity and Insights Quality
This analysis draws on a blended methodology that integrates primary and secondary research to ensure depth and reliability. Primary insights stem from in-depth interviews with over 30 senior cybersecurity professionals, including CISOs, CIOs, and heads of risk management, representing diverse industries and organization sizes. These conversations provided first-hand perspectives on evolving threat vectors, procurement challenges, and security investment rationales.
Secondary research leveraged a wide spectrum of authoritative sources, including industry surveys, vendor white papers, regulatory filings, and peer-reviewed studies. Data points were cross-validated across multiple publications and anonymized industry databases to maintain accuracy and objectivity. Publicly available tariff schedules, government trade announcements, and association letters were systematically analyzed to capture the cumulative impact of U.S. trade policies on security markets.
Quantitative data from global and regional market studies were juxtaposed with qualitative intelligence from threat reports and expert commentaries to identify emerging patterns and reconcile discrepancies. All findings were subjected to multi-layer editorial review and fact-checking protocols, ensuring that the insights presented herein adhere to rigorous standards of integrity and relevance.
This robust approach provides a holistic view of the internet security ecosystem, balancing empirical data with practitioner experiences to support informed decision-making and strategic planning.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Internet Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Internet Security Market, by Security Type
- Internet Security Market, by Deployment Mode
- Internet Security Market, by Organization Size
- Internet Security Market, by Threat Type
- Internet Security Market, by Attack Vector
- Internet Security Market, by End User
- Internet Security Market, by Region
- Internet Security Market, by Group
- Internet Security Market, by Country
- United States Internet Security Market
- China Internet Security Market
- Competitive Landscape
- List of Figures [Total: 18]
- List of Tables [Total: 3498 ]
Concluding Reflections on Internet Security Challenges and Opportunities: Synthesizing Insights to Guide Strategic Decision-Making in an Uncertain Environment
The rapidly evolving internet security landscape demands continuous adaptation and strategic foresight. Organizations that embrace zero-trust principles, shore up hybrid cloud visibility, and invest in AI-focused defenses will be better equipped to counter agile adversaries. Simultaneously, aligning security measures with application development lifecycles and workforce development programs can mitigate both external and internal threats.
While U.S. trade policies introduce complexities, proactive engagement with regulatory bodies and diversified sourcing strategies can alleviate tariff-induced cost pressures. Regional dynamics underscore the importance of tailored approaches, as maturity levels, regulatory mandates, and threat vectors vary significantly across continents. Leading vendors continue to innovate through AI-infused platforms and integrated architectures, but partnerships and ecosystem collaboration remain critical to closing coverage gaps.
Ultimately, sustainable cyber resilience hinges on the convergence of technology, process, and people. By synthesizing the insights in this report, decision-makers can prioritize initiatives that drive measurable risk reductions, optimize security investments, and foster a culture of continuous improvement. The evolving threat environment presents both challenges and opportunities, and organizations that harness data-driven strategies will secure a competitive edge in the digital era.
Take the Next Step: Secure Your Competitive Edge by Partnering with Ketan Rohom to Access the Full Internet Security Market Research Report
Unlock unparalleled insights and drive strategic advantage by securing the comprehensive Internet security market research report. Connect directly with Ketan Rohom, the Associate Director overseeing Sales & Marketing, to explore tailored data, in-depth analyses, and custom consulting options. Engage in a personalized consultation to align the report’s findings with your organization’s unique priorities, whether mapping competitive landscapes, optimizing security investments, or benchmarking threat preparedness.
Elevate your decision-making with exclusive access to the full suite of deliverables, including detailed regional deep dives, company profiles, and actionable recommendations. Reach out to Ketan Rohom to schedule a briefing and discover how these insights can fortify your cybersecurity strategy and accelerate growth.

- How big is the Internet Security Market?
- What is the Internet Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




