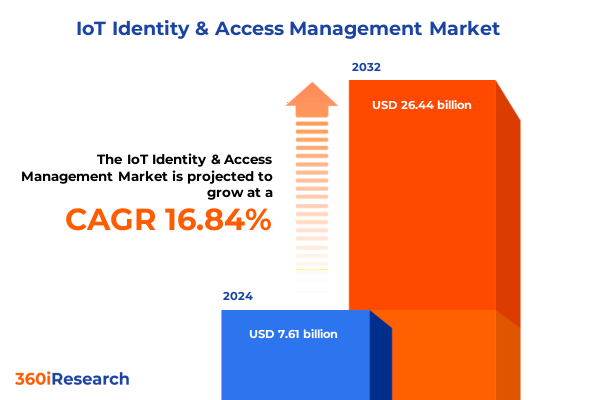
The IoT Identity & Access Management Market size was estimated at USD 8.85 billion in 2025 and expected to reach USD 10.30 billion in 2026, at a CAGR of 16.91% to reach USD 26.44 billion by 2032.
Exploring How Identity and Access Management Frameworks Are Ensuring Security, Compliance, and Operational Excellence in Emerging Internet of Things Ecosystems
As connected devices proliferate across enterprise operations and consumer environments alike, the imperative of establishing robust identity and access management (IAM) for the Internet of Things (IoT) has never been more critical. In this evolving landscape, organizations must not only authenticate and authorize a diverse array of sensors, gateways, and edge computing resources but also maintain compliance with stringent data protection regulations. Consequently, IAM frameworks have transformed from centralized, perimeter-based models into dynamic, scalable architectures capable of handling billions of device identities in real time.
Furthermore, the advent of zero trust principles and decentralized identity paradigms has catalyzed a shift towards more resilient IAM strategies. These frameworks treat every connection request as untrusted until verified, leveraging continuous authentication and adaptive access controls. As a result, security architects are designing end-to-end encryption, identity fabrics, and blockchain-based ledgers to provide immutable device credentials. Such innovations ensure that only authorized entities interact with critical systems, thereby mitigating the risk of lateral movement and supply chain attacks.
Moreover, the convergence of IAM with artificial intelligence and machine learning has enhanced threat detection capabilities by continuously analyzing behavioral patterns and anomaly signals. This integration empowers security teams to pivot from reactive incident response to proactive risk mitigation. Consequently, organizations that embrace these advanced IAM solutions position themselves to achieve operational excellence, regulatory compliance, and sustained resilience amid the accelerating complexity of IoT ecosystems.
Identifying the Transformative Technological Advances and Regulatory Overhauls Shaping Zero Trust Identity and Access Management in Evolving IoT Networks
Over the past two years, significant technological advances and evolving regulatory mandates have collectively reshaped the IoT identity and access management domain. The integration of zero trust architectures across edge computing infrastructures has redefined the role of IAM from a static gateway control to a continuous verification engine. As devices become more autonomous, IAM solutions have adopted certificate-based authentication, enabling machine-to-machine trust without human intervention.
In parallel, the rapid deployment of 5G networks has expanded the attack surface, necessitating IAM solutions that can operate under high throughput and low latency conditions. To address this, vendors are embedding lightweight identity agents at the network edge, enabling local authentication decisions that reduce central server dependencies. This approach not only optimizes performance but also enhances resilience against network disruptions.
Moreover, regulatory frameworks such as the Internet of Things Cybersecurity Improvement Act and regional data privacy laws have elevated compliance requirements for device manufacturers and service providers. The proliferation of mandatory guidelines around secure boot, firmware validation, and identity lifecycle management has spurred a wave of standards-based IAM deployments. Consequently, organizations are increasingly adopting decentralized identity models and verifiable credential schemes to achieve both regulatory adherence and interoperability across diverse IoT platforms.
Transitioning from legacy perimeter defenses to these modern paradigms has required close collaboration between security architects, network engineers, and compliance officers. As a result, transformational shifts in organizational structures and vendor ecosystems have emerged, paving the way for next-generation IAM capabilities tailored to vast, interconnected IoT landscapes.
Assessing the Multifaceted Impact of Newly Imposed United States 2025 Tariffs on Component Supply Chains and Cost Structures in IoT Identity Solutions
The introduction of new United States tariffs in early 2025 has exerted upward pressure on the cost and availability of critical IoT components, directly influencing identity and access management strategies. These levies target a broad range of semiconductor devices, including microcontrollers, secure elements, and specialized sensors, all essential for embedding cryptographic functions and secure boot capabilities within IoT hardware. As costs for these components rise, device manufacturers and solution providers are reassessing hardware architectures to optimize resilience without sacrificing security integrity.
Consequently, many organizations have accelerated their adoption of software-centric identity approaches, relying on virtual secure environments and hardware security modules within data centers rather than embedding costly secure elements in each device. This transition has prompted IAM vendors to enhance their support for remote attestation, anchored in cloud-based root of trust frameworks that can validate device integrity at scale.
Furthermore, tariffs have amplified supply chain disruptions, leading companies to diversify their sourcing strategies and explore nearshoring partnerships. In doing so, security teams must rewrite identity provisioning workflows to accommodate multiple manufacturing sites and firmware variants. These adjustments require centralized identity orchestration platforms that can manage heterogeneous device profiles and certificate lifecycles across geographies.
Moreover, the increased focus on cost-efficient security has spurred innovation in open-source identity standards and lightweight cryptographic algorithms. By leveraging community-driven protocols, organizations can mitigate vendor lock-in while ensuring compliance with national export controls. As a result, the 2025 tariff environment has served as a catalyst for both cost optimization and architectural innovation within IoT IAM implementations.
Unveiling Granular Insights Across Components, Deployment Models, Organization Sizes, Industry Verticals, and Authentication Modalities in IoT Identity Management
Insights into the market’s composition reveal that the dichotomy between comprehensive solutions and auxiliary services plays a pivotal role in shaping adoption patterns. On one hand, enterprises prioritize turnkey platforms that integrate identity orchestration, certificate management, and analytics. On the other, they engage specialized managed offerings to outsource critical functions such as continuous monitoring and incident response, while professional services support strategy design and custom integrations.
Moreover, deployment preferences continue to split along cloud and on-premise modalities, each with its distinct benefits. Cloud-based models appeal to organizations seeking rapid scalability and minimal infrastructure overhead, especially within agile development environments. Within these, hybrid configurations balance the agility of public cloud resources with the control afforded by private or localized instances, enabling sensitive workloads to remain behind corporate firewalls. Conversely, on-premise deployments persist among regulated sectors that require complete data residency and direct hardware control.
In addition, organizational scale markedly influences IAM requirements. Large enterprises deploy centralized identity governance frameworks that cater to global operations and sophisticated role hierarchies. Conversely, small and medium enterprises prioritize streamlined solutions that can be rapidly provisioned with minimal administration, often leveraging functional presets and out-of-the-box connectors to core directories.
Finally, industry verticals and authentication modalities converge to define solution roadmaps. Financial institutions demand transaction-grade multi-factor authentication combined with hardware tokens and biometric verifications, while healthcare providers emphasize secure single sign-on and public key infrastructures for medical devices. Manufacturing and logistics sectors, by contrast, are experimenting with blockchain-based identity ledgers for traceability and firmware integrity. Across these dimensions, the ongoing refinement of biometric, token-based, and one-time password mechanisms underscores the trend toward adaptive, context-aware access controls.
This comprehensive research report categorizes the IoT Identity & Access Management market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Deployment Model
- Organization Size
- Authentication Type
- Industry Vertical
Analyzing Regional Variations in Adoption, Regulatory Environments, and Technology Preferences Across Americas, EMEA, and Asia Pacific IoT Identity Markets
Geographic dynamics fundamentally shape the trajectory of IoT identity and access management adoption. In the Americas, regulatory initiatives such as the IoT Cybersecurity Improvement Act have propelled demand for frameworks that can enforce secure boot procedures and certificate lifecycles across critical infrastructure deployments. This regulatory impetus, coupled with robust venture capital activity, has fostered a thriving ecosystem of IAM innovators focused on compliance automation and real-time risk analytics.
By contrast, Europe, Middle East, and Africa exhibit a patchwork of regulatory stringency driven by GDPR, the NIS2 Directive, and national data protection authorities. Consequently, organizations in these regions adopt modular IAM architectures that can adapt to country-specific data residency rules and cross-border data sharing requirements. This flexibility enables a blend of centralized policy management with localized control points, ensuring operational continuity amid evolving legal frameworks.
Meanwhile, the Asia-Pacific region experiences rapid uptake in manufacturing, smart city, and telecommunications applications, underpinned by substantial government-led digital transformation initiatives. Here, the convergence of 5G rollouts and edge computing has spurred demand for distributed identity fabrics capable of local authentication decisions. As a result, regional vendors and integrators are advancing lightweight identity agents and decentralized credential stores to optimize performance under low-latency, high-throughput conditions.
Across all geographies, cross-border collaboration and interoperability standards have gained prominence, reflecting a broader imperative to harmonize security practices while accommodating regional nuances. This balance of global consistency and local adaptability has become a hallmark of successful IoT IAM deployments worldwide.
This comprehensive research report examines key regions that drive the evolution of the IoT Identity & Access Management market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Revealing Competitive Dynamics and Strategic Initiatives from Leading Industry Players Steering Innovation in IoT Identity and Access Management Spaces
Multiple leading technology vendors have intensified their focus on delivering specialized IAM capabilities tailored for the unique demands of IoT environments. One established provider has augmented its IAM suite with integrated edge identity agents that enforce zero trust policies directly on gateway devices, thereby reducing latency and dependency on centralized servers. Another prominent software firm has launched a blockchain-based credential issuance platform designed to enable decentralized verification of device certificates without sacrificing auditability.
Meanwhile, cloud hyperscalers continue to enrich their IoT security portfolios by integrating identity services that unify device, user, and application authentication under a single pane of glass. These expansions include AI-driven anomaly detection modules that flag suspicious behavior patterns, as well as streamlined onboarding pipelines that leverage domain-specific templates to expedite deployment.
In parallel, specialized security integrators have established managed security service offerings focused exclusively on IoT IAM. These services encompass continuous policy tuning, certificate lifecycle automation, and incident response tailored to embedded device fleets. By blending cybersecurity expertise with domain-specific knowledge in manufacturing, energy, and healthcare, these firms are enabling organizations to offload operational complexity while ensuring robust security postures.
Finally, emerging challengers in the IAM space are exploring open-source protocols and federated identity models, aiming to reduce vendor lock-in and foster ecosystem interoperability. Their contributions to community-driven standards accelerate the development of lightweight cryptographic libraries and verifiable credential frameworks that address the scalability and performance requirements of next-generation IoT deployments.
This comprehensive research report delivers an in-depth overview of the principal market players in the IoT Identity & Access Management market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Amazon.com Inc.
- Arm Limited
- Broadcom Inc.
- Cisco Systems Inc.
- Cloudflare Inc.
- Device Authority Ltd.
- DigiCert Inc.
- Entrust Corporation
- ForgeRock Inc.
- GlobalSign Inc.
- Google LLC
- HID Global Corporation
- IBM Corporation
- Intel Corporation
- Keyfactor Inc.
- Microsoft Corporation
- Nexus Group AB
- NVIDIA Corporation
- Okta Inc.
- Oracle Corporation
- Ping Identity Holding Corp.
- Qualcomm Incorporated
- Thales Group
- Zscaler Inc.
Empowering Industry Leaders with Strategic Recommendations to Drive Secure, Scalable, and Cost-Effective IoT Identity and Access Management Deployments
Industry leaders should adopt a holistic zero trust mindset that permeates every layer of IoT architecture. By treating device identity as the new perimeter, security teams can enforce continuous authentication and dynamic access policies that adapt to contextual risk signals. This approach requires integrating identity fabrics with real-time analytics engines to proactively identify anomalous device behavior before it escalates into critical incidents.
Moreover, organizations must strategically invest in hybrid deployment models that leverage public cloud scalability for noncritical workloads while retaining on-premise control over sensitive systems. By implementing unified identity orchestration platforms, enterprises can manage device certificates and access tokens consistently across environments, ensuring seamless policy enforcement and compliance tracking.
In addition, forging partnerships with specialized service providers can accelerate time to value and reduce operational burdens. Outsourcing certificate management and incident response to expert managed service teams allows internal IT staff to focus on core business initiatives. Concurrently, engaging professional services for customized integration ensures that IAM frameworks align precisely with unique infrastructure and regulatory requirements.
Finally, a proactive ongoing training program is essential for cultivating the technical expertise needed to maintain and evolve IAM frameworks. By blending hands-on workshops, scenario-based simulations, and industry certification pathways, organizations can build a resilient talent pipeline capable of addressing emerging threats and technological shifts. Through these combined measures, industry leaders will be well-positioned to deliver secure, scalable, and cost-effective IoT deployments.
Delineating Rigorous Research Methodologies and Data Triangulation Techniques Underpinning Comprehensive IoT Identity and Access Management Market Analysis
The research underpinning this analysis combines rigorous primary and secondary methodologies to ensure depth, accuracy, and impartiality. Primary data collection involved in-depth interviews with security architects, CIOs, and compliance officers across diverse industry verticals, allowing for the capture of firsthand insights into deployment challenges and strategic priorities. These conversations were supplemented by direct engagement with IAM solution providers to validate emerging feature sets and roadmaps.
Secondary research encompassed an extensive review of regulatory texts, industry white papers, and academic publications. Key sources included federal guidelines on IoT cybersecurity, international standards bodies’ protocols for identity management, and publicly available vendor documentation. This review provided a comprehensive understanding of both the technical and legal landscapes shaping IoT IAM evolution.
To enhance reliability, data triangulation techniques were employed, comparing qualitative insights from interviews with documented case studies and vendor press releases. In addition, an expert advisory panel of industry veterans reviewed preliminary findings to identify potential biases and refine thematic areas of focus. This iterative validation process ensured that the analysis reflects real-world deployment experiences and forward-looking innovations.
Finally, the research adopted a modular framework that aligns insights by component, deployment model, organizational scale, industry vertical, and authentication type, enabling stakeholders to isolate relevant segments and drive tactical decision making. Through this structured methodology, the report provides a balanced and actionable view of the IoT identity and access management landscape.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our IoT Identity & Access Management market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- IoT Identity & Access Management Market, by Component
- IoT Identity & Access Management Market, by Deployment Model
- IoT Identity & Access Management Market, by Organization Size
- IoT Identity & Access Management Market, by Authentication Type
- IoT Identity & Access Management Market, by Industry Vertical
- IoT Identity & Access Management Market, by Region
- IoT Identity & Access Management Market, by Group
- IoT Identity & Access Management Market, by Country
- United States IoT Identity & Access Management Market
- China IoT Identity & Access Management Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1431 ]
Synthesizing Critical Findings to Illuminate the Future Trajectory and Strategic Imperatives for Sustainable IoT Identity and Access Management Ecosystems
Throughout this executive summary, we have examined the critical role of identity and access management in safeguarding interconnected devices and maintaining regulatory compliance. By exploring transformative shifts-driven by zero trust architectures, edge-based identity agents, and AI-enhanced threat analytics-we have highlighted the strategic evolution of IAM solutions tailored for IoT environments.
Furthermore, analysis of the United States’ 2025 tariff landscape demonstrated its influence on hardware-centric security strategies and the accelerating shift toward software-oriented identity frameworks. We then delved into segmentation insights, revealing how component choices, deployment preferences, organizational scale, industry demands, and authentication modalities collectively inform solution roadmaps.
Regional variations underscored the importance of harmonizing global best practices with local regulatory imperatives, while competitive dynamics showcased how leading vendors and challenger firms are innovating to address scalability and interoperability challenges. Our actionable recommendations have provided a clear blueprint for industry leaders to adopt zero trust mindsets, hybrid deployment models, and expert partnerships, all supported by robust training programs.
Looking ahead, the trajectory of IoT identity and access management will be shaped by emerging paradigms such as decentralized identities, AI-driven continuous verification, and cross-industry standards collaboration. By synthesizing these insights, stakeholders are equipped to navigate complexity and drive secure, resilient connected ecosystems.
Engage With Ketan Rohom to Unlock Customized, Actionable Insights for Securing and Managing IoT Identities in Your Enterprise Environment
By partnering with Ketan Rohom, Associate Director of Sales and Marketing, organizations can gain exclusive access to an in-depth examination of IoT Identity and Access Management that aligns with their strategic goals. Through tailored briefings and specialized workshops, clients will receive actionable insights on safeguarding devices, optimizing access protocols, and navigating regulatory complexities across global markets. Ketan’s deep understanding of both technical security requirements and evolving business priorities ensures that stakeholders will leave equipped with a clear roadmap for secure IoT deployments. Engage now to secure premium consulting sessions and receive a customized market research package designed to address your organization’s unique challenges in IoT identity management.

- How big is the IoT Identity & Access Management Market?
- What is the IoT Identity & Access Management Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




