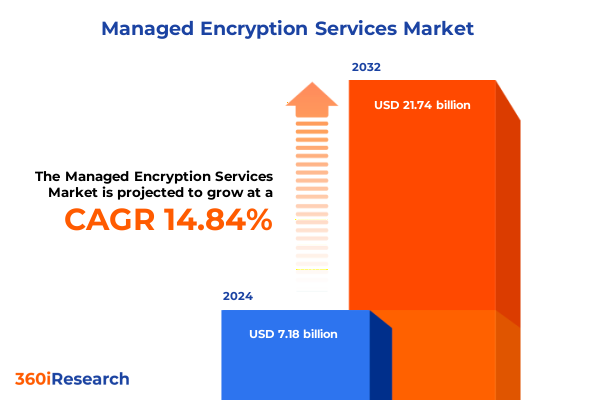
The Managed Encryption Services Market size was estimated at USD 8.27 billion in 2025 and expected to reach USD 9.32 billion in 2026, at a CAGR of 14.79% to reach USD 21.74 billion by 2032.
Understanding the Critical Role of Managed Encryption Services in Safeguarding Data and Enabling Secure Digital Transformation Across Enterprises Worldwide
As organizations contend with escalating cyber threats and increasing volumes of sensitive data, managed encryption services have emerged as an indispensable cornerstone of modern security architectures. Encryption alone no longer presents an adequate defense; the complexities of key generation, distribution, rotation, and secure storage demand specialized expertise and robust processes. Consequently, enterprises across sectors are embracing managed encryption services to offload operational burdens, accelerate deployment timelines, and ensure adherence to stringent compliance frameworks.
The transition toward cloud-native environments, microservices, and remote workforce models has further amplified the need for a cohesive encryption strategy that spans on-premises infrastructure, public and private cloud platforms, and edge deployments. By centralizing key management and leveraging dedicated hardware security modules operated by experienced providers, organizations are able to maintain consistent encryption policies and granular access controls across distributed environments. This approach not only improves security outcomes but also fosters agility by enabling rapid provisioning of encryption services in support of digital transformation initiatives.
Moreover, with regulatory regimes such as the General Data Protection Regulation in Europe, the California Consumer Privacy Act, and emerging sector-specific mandates imposing tougher requirements on data protection, adopting a managed encryption model offers a proven path to compliance. By coupling advanced cryptographic techniques with ongoing policy updates and expert guidance, managed encryption services empower organizations to navigate evolving compliance landscapes with confidence and maintain customer trust.
Exploring the Evolving Encryption Landscape as Cloud Adoption Accelerates, Zero Trust Becomes Ubiquitous, and Data Privacy Regulations Intensify Across Industries
Over the past several years, the managed encryption market has undergone a series of transformative shifts driven by changes in architecture, user expectations, and regulatory environments. Cloud-first strategies have taken center stage, prompting service providers to deliver encryption solutions that natively integrate with public cloud platforms and support multi-cloud deployments with minimal administrative overhead. Furthermore, as zero trust security models gain broader adoption, the role of encryption has evolved from a compliance checkbox to a dynamic, context-aware control that verifies trust at every layer of the network.
In parallel, organizations are demanding end-to-end automation of cryptographic processes to keep pace with DevOps and continuous delivery cycles. Encryption-as-code frameworks are emerging, enabling developers and security teams to provision keys programmatically via APIs, enforce policy-driven key rotation schedules, and generate auditable logs without manual intervention. Transitioning from siloed encryption implementations to unified, policy-centric platforms accelerates innovation while reducing the risk of human error associated with manual key handling.
Additionally, the heightened focus on data privacy has spawned a wave of new regional and vertical regulations that mandate specific encryption standards, reporting obligations, and breach notification protocols. As a result, managed encryption providers are embedding compliance advisory services into their offerings, delivering tailored policy updates, risk assessments, and training modules that align with each customer’s regulatory footprint. These combined shifts underscore a broader trend toward convergence: encryption services are now integral to comprehensive data security strategies rather than standalone solutions.
Analyzing How the 2025 United States Tariff Policies Are Reshaping Supply Chains, Driving Costs in Hardware Security Modules, and Influencing Encryption Service Strategies
In 2025, the United States introduced a series of targeted tariffs on imported cryptographic hardware, notably those sourced from certain international suppliers, in response to growing concerns around national security and supply chain sovereignty. These measures have had a cumulative impact on the managed encryption services market, especially in segments reliant on hardware security modules and specialized key storage appliances. Providers have encountered increased procurement costs and extended lead times, compelling many to explore alternative manufacturing partnerships and local assembly options.
As a result of these tariffs, service providers have begun revisiting pricing structures for hardware-based encryption offerings, often passing incremental costs to end customers or absorbing a portion of the fees to maintain competitive positioning. Moreover, some providers have accelerated investments in cloud-based HSM alternatives, which leverage shared infrastructure and software-defined cryptographic engines, alleviating hardware dependencies while providing near-equivalent security assurances. This strategic pivot has implications for organizations weighing the trade-offs between dedicated on-premises modules and elastic cloud services.
Furthermore, the tariffs have prompted many enterprises to scrutinize their long-term sourcing strategies for encryption hardware, evaluating domestic suppliers and exploring hybrid procurement models that blend imported components with locally produced modules. These adjustments underscore the importance of supply chain resilience within encryption service frameworks and highlight the necessity for organizations to maintain visibility into the provenance and integrity of cryptographic assets across global and domestic networks.
Unveiling Critical Market Segments by Service Type, Deployment Model, Organization Size, Industry Vertical, Encryption Type, and Key Management Model to Guide Strategy
The managed encryption services market can be dissected along multiple dimensions to reveal distinct patterns of adoption and innovation. When viewed through the prism of service type, compliance and consulting engagements are frequently contracted by organizations navigating intricate regulatory landscapes, while data encryption services-covering application, database, and file encryption-are sought to protect sensitive workloads spanning development pipelines and production environments. In parallel, hardware security module management offerings, differentiated by cloud-hosted or on-premises deployments, are favored by entities requiring physical separation of key storage, and key management services-centralized or distributed-address diverse control requirements.
Considering deployment model, pure cloud solutions dominate growth charts, driven by their ease of integration and rapid scalability, though hybrid architectures are increasingly embraced to balance performance, cost, and compliance. On-premises installations remain a fixture in sectors with stringent data residency rules or latency-sensitive applications, ensuring that organizations retain direct control over cryptographic assets. When assessing organization size, large enterprises typically invest in end-to-end managed encryption suites that incorporate advisory services and bespoke integrations, whereas small and medium-sized enterprises often prioritize modular, consumption-based key management models to minimize upfront commitments.
Industry verticals further influence service preferences. Banking, financial services, and insurance entities frequently opt for sophisticated key management models underpinned by policy-driven workflows, while government and defense customers emphasize sovereign key control and hold-your-own-key frameworks. Healthcare providers and payers balance encryption imperatives with interoperability demands, and IT and telecommunications firms integrate encryption services into their broader service portfolios to support enterprise digital transformation initiatives. Across all verticals, the selection of encryption type-be it symmetric, asymmetric, hashing, or tokenization-must align with application requirements and regulatory mandates, and key management models such as bring-your-own-key and key-as-a-service continue to proliferate as enterprises seek a balance between control and convenience.
This comprehensive research report categorizes the Managed Encryption Services market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Service Type
- Deployment Model
- Encryption Type
- Key Management Model
- Organization Size
- Industry Vertical
Highlighting Regional Dynamics in the Managed Encryption Service Market Across the Americas, Europe Middle East Africa, and Asia Pacific to Inform Growth Opportunities
Regional dynamics play a pivotal role in shaping the managed encryption services landscape. In the Americas, the United States leads adoption, propelled by federal and state privacy regulations and a vibrant ecosystem of cloud providers and security startups. Canada’s regulatory alignment with its southern neighbor and Latin America’s burgeoning fintech sector also drive demand for managed encryption solutions that can be rapidly deployed across borders with minimal configuration.
Moving to Europe, Middle East, and Africa, GDPR in Europe serves as the catalyst for widespread adoption of encryption as a core compliance control, while many Middle East governments are investing heavily in digital infrastructure and defense initiatives that prioritize sovereign data protection. Africa’s market remains nascent but shows promise as telecommunications operators and financial institutions seek to fortify their networks against escalating cyber threats.
In Asia-Pacific, a confluence of regulatory initiatives-ranging from data localization mandates in India to stringent privacy laws in Japan and South Korea-has accelerated the uptake of managed encryption services. China’s focus on domestic cryptographic standards and certification programs underscores the importance of regional partnerships for service providers. Meanwhile, Southeast Asian economies leverage cloud-based key management to support rapid digitalization in e-commerce and government modernization projects. These regional differences highlight the need for providers to tailor service portfolios to local compliance regimes and infrastructure realities.
This comprehensive research report examines key regions that drive the evolution of the Managed Encryption Services market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Examining the Strategic Moves of Leading Encryption Service Providers, Their Partnerships, Innovation Roadmaps, and Competitive Differentiators in a Crowded Marketplace
The competitive landscape of managed encryption services features a blend of traditional security vendors, cloud infrastructure giants, and specialized cryptographic service providers. Industry incumbents have leveraged long-standing relationships with enterprise clients to expand offerings from hardware security modules and on-premises key management appliances into comprehensive, cloud-native platforms. Cloud providers have capitalized on their infrastructure scale by embedding advanced key management capabilities into existing service catalogs, simplifying consumption for existing customers while driving deeper integration with native cloud services.
Meanwhile, pure-play encryption specialists differentiate through industry-specific compliance templates, professional services, and flexible deployment options that cater to complex hybrid environments. Partnerships and acquisitions remain key strategies for both vendors and service providers seeking to augment cryptographic portfolios with adjacent capabilities, such as tokenization, digital identity solutions, and secure enclave services. Additionally, certain players are innovating with open-source projects to foster community-driven improvements in key lifecycle management, further illustrating the competitive imperative to balance proprietary features with broader interoperability.
Emerging contenders are also entering the arena, leveraging automation and artificial intelligence to optimize key rotation schedules, detect anomalous access patterns, and provide predictive analytics on cryptographic usage. These advancements underscore the evolving nature of competition, where platform extensibility, ease of integration with DevSecOps workflows, and the ability to deliver consistent global compliance are increasingly decisive factors.
This comprehensive research report delivers an in-depth overview of the principal market players in the Managed Encryption Services market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Amazon Web Services, Inc.
- Atos SE
- Broadcom Inc.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- CrowdStrike Holdings, Inc.
- Entrust Corporation
- Fortinet, Inc.
- Google LLC
- Hewlett Packard Enterprise Development LP
- IBM Corporation
- McAfee Corp.
- Microsoft Corporation
- Palo Alto Networks, Inc.
- Proofpoint, Inc.
- Sophos Ltd.
- Thales Group
- Trend Micro Incorporated
- Unbound Security Ltd.
- Zscaler, Inc.
Providing Clear, Actionable Recommendations for Industry Leaders to Optimize Encryption Strategies, Enhance Security Posture, and Achieve Compliance in Complex Environments
To fully harness the benefits of managed encryption services, industry leaders should adopt a series of targeted actions. First, enterprises must evaluate their existing key management processes and identify opportunities to consolidate disparate systems under a unified platform that supports both cloud-native and on-premises workloads. This consolidation not only streamlines operational overhead but also establishes consistent policy enforcement and auditability across the environment.
Next, organizations should carefully assess the trade-offs between bring-your-own-key and key-as-a-service models, considering factors such as control, cost, and compliance obligations. In scenarios requiring strict data sovereignty or defense-grade controls, holding one’s own key may be non-negotiable, whereas more elastic applications can benefit from the flexibility of managed key services. Additionally, security teams must integrate encryption workflows into DevSecOps pipelines, leveraging infrastructure-as-code templates and automated policy checks to prevent configuration drift and ensure continuous compliance.
Finally, enterprises should invest in ongoing training and awareness programs to equip both technical and business stakeholders with the knowledge required to navigate evolving regulatory landscapes and cryptographic best practices. By establishing clear governance frameworks, negotiating robust service-level agreements with providers, and proactively monitoring key usage metrics, organizations can transform encryption from a static control into a strategic enabler of secure innovation.
Detailing the Robust Research Methodology Incorporating Primary Interviews, Secondary Data Analysis, and Expert Validation to Ensure Insightful, Accurate Findings
The insights presented in this report are underpinned by a rigorous research methodology combining primary and secondary sources. Primary research involved in-depth interviews with chief information security officers, cybersecurity architects, and compliance leaders from a cross-section of industries, enabling a nuanced understanding of encryption challenges and priorities. These qualitative insights were complemented by a quantitative survey distributed to IT decision makers across enterprises of varying sizes, capturing adoption trends, spending priorities, and technology preferences.
Secondary research drew upon a wide array of publicly available resources, including government regulations and guidance documents, technical white papers from standards bodies, trade publications, and leading technology vendor collateral. This phase also encompassed an analysis of patent filings and product documentation to trace the evolution of key management innovations. All data points and thematic findings underwent validation through an expert advisory panel comprising seasoned practitioners and academic researchers, ensuring both accuracy and relevance.
Throughout the research process, adherence to strict data quality protocols was maintained. Structured coding frameworks were applied to qualitative feedback, while statistical rigor was enforced in survey sample design and analysis. This integrated approach ensures that the report’s conclusions and recommendations rest upon a foundation of methodical evidence gathering and critical peer review.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Managed Encryption Services market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Managed Encryption Services Market, by Service Type
- Managed Encryption Services Market, by Deployment Model
- Managed Encryption Services Market, by Encryption Type
- Managed Encryption Services Market, by Key Management Model
- Managed Encryption Services Market, by Organization Size
- Managed Encryption Services Market, by Industry Vertical
- Managed Encryption Services Market, by Region
- Managed Encryption Services Market, by Group
- Managed Encryption Services Market, by Country
- United States Managed Encryption Services Market
- China Managed Encryption Services Market
- Competitive Landscape
- List of Figures [Total: 18]
- List of Tables [Total: 2703 ]
Summarizing Key Findings and Strategic Implications of Managed Encryption Services to Empower Decision Makers with Clarity on Securing Data and Driving Innovation
Managed encryption services occupy a pivotal position in modern cybersecurity strategies, bringing together advanced cryptographic technologies, streamlined key management processes, and compliance expertise. The market is actively shaped by cloud proliferation, zero trust models, and heightened regulatory scrutiny, while the recent tariff-driven shifts in hardware sourcing underscore the importance of supply chain resilience. Segmentation insights reveal distinct adoption patterns driven by service type, deployment model, enterprise scale, industry vertical, encryption technology, and key management models.
Regional dynamics further highlight the differentiation between mature markets in the Americas and EMEA, where regulatory mandates are driving robust adoption, and the dynamic growth opportunities emerging across Asia-Pacific’s data sovereignty and digital modernization initiatives. Competitive analysis shows that both established incumbents and innovative newcomers are vying to deliver seamless, policy-driven encryption solutions that integrate with DevSecOps workflows and hybrid infrastructures. For industry leaders, the path forward involves unifying key management, aligning service models with control and compliance needs, automating cryptographic operations, and fostering continuous learning across stakeholder groups.
By embracing these imperatives, organizations can transform encryption from a compliance necessity into a strategic driver of secure innovation, ensuring that sensitive data remains protected without hampering operational agility or growth ambitions.
Encouraging Decision Makers to Engage with Associate Director Sales & Marketing for Customized Insights and Access to the Comprehensive Managed Encryption Services Research Report
For readers ready to transform their data protection posture, a direct conversation with Ketan Rohom, whose deep expertise in managed encryption underscores his role as the Associate Director of Sales & Marketing, represents the ideal next step. Engaging with Ketan provides the opportunity to explore tailored solutions that align precisely with an organization’s unique security requirements, ensuring that encryption strategies not only address current regulatory demands but also anticipate future shifts in technology and threat landscapes.
By initiating this dialogue, decision makers gain firsthand access to exclusive intelligence on innovations in key management, hardware security, and compliance frameworks. Ketan’s insights will illuminate how to leverage managed encryption services as a competitive advantage, balancing operational efficiency with rigorous security controls. Interested stakeholders can reach out to Ketan to schedule a personalized briefing, during which they will receive a detailed overview of the comprehensive managed encryption services research report and custom recommendations designed to accelerate secure digital transformation.

- How big is the Managed Encryption Services Market?
- What is the Managed Encryption Services Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




