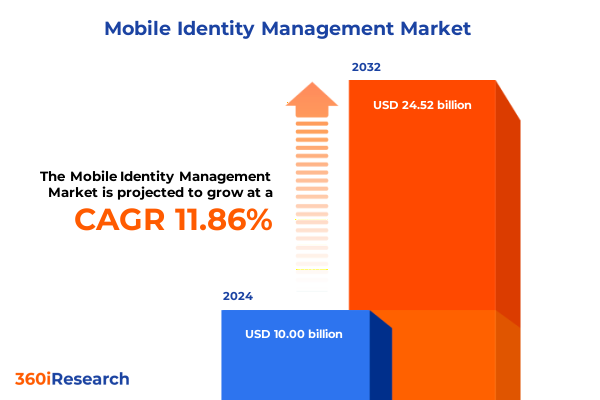
The Mobile Identity Management Market size was estimated at USD 11.16 billion in 2025 and expected to reach USD 12.46 billion in 2026, at a CAGR of 11.89% to reach USD 24.52 billion by 2032.
Setting the Stage for Secure Digital Interactions by Illuminating the Rising Importance and Strategic Drivers of Mobile Identity Management Solutions
Mobile identity management has emerged as a foundational element of modern digital ecosystems, driven by the exponential rise of mobile device usage and the critical need for secure access. As enterprises embrace digital transformation and remote work becomes the norm, the mobile channel has swiftly evolved from a convenience to a strategic touchpoint through which users interact with applications, services, and sensitive data. Consequently, organizations must adopt robust mobile identity solutions to ensure that each access request originates from a verified user and a trusted device.
In recent years, cyberthreats targeting mobile endpoints have escalated in both frequency and sophistication, compelling security leaders to reevaluate traditional perimeter-based approaches. The expanding threat surface-from phishing attempts using mobile channels to malware exploiting operating system vulnerabilities-has underscored the importance of an identity-centric security model. Against this backdrop, mobile identity management seeks to harmonize the twin imperatives of frictionless user experience and uncompromising security.
By integrating diverse authentication methods, leveraging adaptive risk assessment, and aligning with regulatory frameworks such as GDPR and CCPA, mobile identity management has become a cornerstone of digital trust. It enables seamless single-sign-on, contextual authentication, and lifecycle management of user credentials. The objective of this executive summary is to illuminate the key drivers reshaping the landscape, analyze the effects of external pressures such as tariffs, and present actionable insights to inform investment, deployment, and governance strategies.
Examining the Transformative Technological Shifts Redefining Mobile Identity Management in an Era Marked by AI Innovation and Zero Trust Security Adoption
The mobile identity management arena has undergone transformative shifts in recent years, driven by paradigm-changing technologies and evolving security philosophies. Among these, the adoption of zero trust security architectures has marked a departure from legacy perimeter defenses. In this model, no user or device is inherently trusted; continuous verification becomes the bedrock of access control. Organizations embracing zero trust are deploying micro-segmentation, least privilege principles, and real-time contextual risk assessments to thwart lateral movement and credential misuse.
Simultaneously, artificial intelligence and machine learning have become integral to dynamic authentication frameworks. By analyzing patterns in user behavior, device telemetry, and network signals, AI-driven systems can detect anomalies and elevate or reduce authentication requirements based on live risk scores. This approach enhances both security posture and user experience by minimizing friction for routine access over familiar environments while stepping up verification for higher-risk scenarios.
Advancements in biometric modalities have further redefined authentication, extending beyond fingerprint and facial scans to include iris recognition, voice analysis, and behavioral biometrics. These non-intrusive factors augment security without compromising convenience. In parallel, decentralized identity and blockchain technologies are gaining traction as means to empower users with self-sovereign control over personal data and reduce reliance on centralized identity repositories.
Together with the shift toward passwordless authentication and the rise of mobile digital IDs, these trends are converging to create an identity management environment that is adaptive, resilient, and user-centered. As organizations navigate this evolving landscape, strategic integration of these capabilities will be essential to maintaining robust security while delivering seamless digital experiences.
Analyzing the Far-Reaching Cumulative Effects of 2025 United States Tariffs on Mobile Identity Management Supply Chains and Technology Costs
Since the beginning of 2025, United States tariff policies have exerted significant pressure on technology supply chains, with average import duties climbing from just above 2 percent to approximately 15 percent as manufacturers and importers grapple with higher costs and regulatory uncertainty. These measures, aimed at incentivizing domestic production and addressing trade imbalances, have reverberated across the mobile identity management sector, where critical components such as secure element chips, biometric sensors, and networking hardware are often sourced internationally.
Major technology providers have reported mixed outcomes in this environment. While companies like SK Hynix and Alphabet have leveraged robust demand for AI chips and cloud services to offset tariffs, others have faced margin compression and supply shortages. Hardware manufacturers are responding by diversifying their supplier base, accelerating shifts toward alternate geographies such as India and Vietnam, and in some cases stockpiling inventory ahead of further tariff escalations. However, these strategies introduce complexity in logistics and inventory management, risking delays and cost overruns.
Consumer electronics exemplify the acute impact of these policies. For instance, the combined tariffs imposed on Chinese-assembled smartphones have the potential to increase the retail price of flagship devices substantially, with analysts projecting that certain models could approach or exceed a $2,000 threshold if costs are passed directly to end users. Such price pressures threaten adoption rates and compel vendors to absorb costs or seek targeted tariff exemptions through lobbying and trade negotiations.
Legal challenges have also shaped the tariff landscape. In May 2025, the United States Court of International Trade invalidated portions of the executive branch’s broad tariff authority, only to have that ruling temporarily stayed as appeals proceed. This judicial back-and-forth has heightened uncertainty for procurement and finance leaders, underscoring the need for agile sourcing strategies and real-time visibility into landed costs to navigate the evolving regulatory framework.
Uncovering Deep Insights Across Organizational Component Deployment Authentication And Industry Vertical Segments Shaping The Mobile Identity Management Market
A nuanced understanding of the mobile identity management market emerges when viewed through the lens of organizational size, component offerings, deployment models, authentication methods, and industry use cases. In terms of scale, the requirements and buying behaviors of large enterprises differ markedly from those of small enterprises and medium-sized businesses. Large organizations often invest in end-to-end platforms and professional services to ensure integration with their sprawling IT estates, whereas smaller firms seek modular solutions that can be rapidly deployed and scaled in line with growth.
Breaking the market down by component reveals a dichotomy between services and solutions. While integration and consulting engagements help organizations tailor identity frameworks to their unique IT landscapes, hardware and software offerings underpin the technical capabilities required for multi-factor authentication, device management, and access governance. Providers that can seamlessly bundle professional services with robust platforms enjoy a competitive advantage.
Deployment mode continues to influence purchasing decisions. Pure cloud environments attract businesses prioritizing swift implementation and minimal infrastructure footprints, whereas hybrid and on-premises installations remain prevalent among regulated and risk-averse sectors. Among cloud variants, public cloud delivers broad accessibility, private cloud enhances data isolation, and community cloud offers a middle ground for industries with shared compliance requirements.
Authentication methodology and industry vertical converge to shape solution roadmaps. Biometric options, including facial, fingerprint, iris, and voice recognition, cater to organizations demanding heightened assurance, while one-time passcodes delivered via email, SMS, hardware or software tokens address more traditional access workflows. Industry-specific regulations and threat vectors drive adoption patterns among banking, government, healthcare, telecom, and retail sectors, each balancing security, user experience, and compliance imperatives.
This comprehensive research report categorizes the Mobile Identity Management market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Organization Size
- Component
- Deployment Mode
- Authentication Method
- Industry Vertical
Highlighting Critical Regional Dynamics Influencing Mobile Identity Management Solutions Adoption In The Americas Europe Middle East & Africa And Asia-Pacific
Regional factors play a pivotal role in shaping the adoption of mobile identity management solutions, driven by distinct regulatory landscapes, technological maturity, and geopolitical dynamics. In the Americas, the United States leads with a strong emphasis on zero trust architectures, AI-enabled authentication, and comprehensive privacy regulations. Canadian organizations increasingly seek interoperable systems that align with both national standards and cross-border requirements, while Latin American markets are investing in mobile-first identity solutions to support burgeoning digital government initiatives.
Across Europe, the Middle East & Africa, diverse regulatory frameworks influence market drivers. European Union member states adhere to the eIDAS regulation and the upcoming European Digital Identity framework, promoting unified credentials across borders and fueling investments in mobile driver’s licenses and wallet integrations. In the Middle East, sovereign identity programs and smart city deployments prioritize scalable mobile identity infrastructures, whereas African nations leverage mobile credentials to extend financial inclusion and streamline government services amidst fragmented legacy systems.
In the Asia-Pacific region, rapid digitalization and smartphone penetration underpin strong demand for mobile identity management. China’s government-led digital ID pilots and regional bank mandates accelerate the use of biometric authentication, while Japan and South Korea focus on privacy-preserving protocols and blockchain-based credentialing. Southeast Asian economies, propelled by e-commerce growth and digital banking expansion, center on cost-effective SaaS deployments, hybrid models for data sovereignty, and mobile-native user experiences to reach diverse and distributed populations.
This comprehensive research report examines key regions that drive the evolution of the Mobile Identity Management market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Key Industry Players Driving Innovation In Mobile Identity Management Through Strategic Partnerships Technological Leadership And Market Expansion
The competitive landscape of mobile identity management features a blend of established technology giants and specialized security vendors, each leveraging unique strengths to capture market opportunity. Leading software providers integrate identity-as-a-service offerings with broad cloud ecosystems, enabling seamless single-sign-on, API-driven extensibility, and centralized policy administration. At the same time, niche players deliver purpose-built authentication modules, hardware-backed secure elements, and professional services tailored to highly regulated industries.
Strategic partnerships and alliances have become a critical way to accelerate innovation. Technology incumbents collaborate with telecom operators and device manufacturers to embed identity frameworks at the operating system and chipset level. Meanwhile, consulting firms forge joint go-to-market engagements with platform specialists to deliver comprehensive digital identity roadmaps, combining threat modeling, risk assessments, and implementation services.
Venture-backed challengers are also making inroads through rapid product iterations and open-source contributions. By focusing on interoperability, developer-friendly SDKs, and community standards, these disruptors lower barriers to entry and cultivate ecosystems of third-party integrators. As digital transformation intensifies, companies that balance scale-driven investments with agile product cycles will define the next generation of mobile identity management leadership.
This comprehensive research report delivers an in-depth overview of the principal market players in the Mobile Identity Management market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- AO Kaspersky Lab
- AppTec GmbH
- Baramundi Software AG
- Broadcom, Inc.
- Cisco Systems, Inc.
- Cloud Software Group, Inc.
- Fortinet, Inc.
- F‑Secure Corporation
- GB Group PLC
- IBM Corporation
- Ivanti, Inc.
- Juniper Networks, Inc.
- Mitsogo Inc.
- One Identity LLC by Quest Software Inc.
- Oracle Corporation
- S.C. BITDEFENDER S.R.L.
- SAP SE
- SecureAuth Corporation
- Signicat AS
- Sophos Limited
- SOTI Inc
- Telesign Corporation
- Telstra Corporation Limited
- Thales SA
- Trend Micro Inc.
- Zoho Corporation Pvt. Ltd.
Delivering Actionable Strategic Recommendations For Industry Leaders To Enhance Security Posture And Drive Growth In The Mobile Identity Management Ecosystem
Industry leaders seeking to enhance their mobile identity management capabilities should prioritize a series of strategic initiatives. First, investing in an adaptive authentication framework that leverages continuous risk assessment will enable real-time responses to evolving threat patterns. By integrating machine learning-driven analytics with contextual intelligence, organizations can minimize false positives while maintaining rigorous security enforcement.
Second, enterprises must adopt a modular approach to technology acquisition, selecting vendors whose solutions can interoperate across on-premises, private cloud, and public cloud environments. This flexibility not only mitigates vendor lock-in but also allows organizations to tailor their deployments in line with jurisdictional data residency requirements and changing business priorities.
Third, building a comprehensive identity governance program that encompasses lifecycle management, least privilege access, and regular access reviews will strengthen compliance posture and reduce insider risk. Organizations should align these governance processes with cross-functional teams-spanning security operations, IT, and business units-to ensure consistent policy application and accountability.
Finally, cultivating strategic alliances with device manufacturers, carrier networks, and regulatory bodies will facilitate early access to emerging capabilities and influence standardization efforts. By engaging in industry consortiums and pilot programs for mobile driver’s licenses and decentralized identity frameworks, enterprises can position themselves at the forefront of innovation while shaping the future of digital identity.
Detailing A Robust Research Methodology Incorporating Primary Interviews Secondary Research And Rigorous Validation To Ensure Credibility And Accuracy
This market research study employs a multi-tiered methodology to ensure the accuracy, reliability, and relevance of its findings. Primary research comprises in-depth interviews with senior executives and technology leaders across enterprise, vendor, and channel partner segments. These discussions provide firsthand perspectives on adoption drivers, investment priorities, and pain points in deploying mobile identity management solutions.
Secondary research encompasses a comprehensive review of industry publications, regulatory filings, and technology whitepapers. Publicly available information from standard bodies, government regulations, and vendor press releases has been rigorously analyzed to map the evolving competitive landscape and identify emerging trends. This desk research establishes the quantitative and qualitative baseline for the study.
The study’s analytical framework incorporates top-down and bottom-up approaches to market segmentation, categorizing data by organization size, component type, deployment mode, authentication method, and industry vertical. Data triangulation techniques-cross-referencing interview insights with secondary sources-ensure consistency and mitigate bias. Furthermore, the research includes a validation phase where preliminary findings are reviewed by an expert advisory panel to refine assumptions and interpretations.
Throughout the process, strict data governance practices govern source verification, version control, and audit trails. This robust methodology underpins the credibility of the conclusions and recommendations presented in this report.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Mobile Identity Management market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Mobile Identity Management Market, by Organization Size
- Mobile Identity Management Market, by Component
- Mobile Identity Management Market, by Deployment Mode
- Mobile Identity Management Market, by Authentication Method
- Mobile Identity Management Market, by Industry Vertical
- Mobile Identity Management Market, by Region
- Mobile Identity Management Market, by Group
- Mobile Identity Management Market, by Country
- United States Mobile Identity Management Market
- China Mobile Identity Management Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1908 ]
Drawing Conclusive Insights To Summarize Core Findings And Emphasize The Strategic Imperatives For Mobile Identity Management Stakeholders
This executive summary has outlined the pivotal trends, market forces, and strategic imperatives shaping the mobile identity management landscape. The confluence of zero trust architectures, AI-enabled authentication, and diverse biometric modalities underscores a shift toward adaptive, user-centric security models. At the same time, geopolitical pressures such as United States tariffs in 2025 have introduced supply chain challenges and cost considerations that demand agile sourcing and financial resilience.
Key segmentation insights reveal that organizations must tailor their identity strategies to fit their size, industry, and technical requirements-whether that involves modular SaaS deployments for small businesses or integrated platforms for global enterprises. Regional dynamics further influence solution roadmaps, from regulatory compliance in Europe, Middle East & Africa to technology adoption patterns across the Americas and Asia-Pacific.
Leading companies continue to innovate through strategic alliances, developer-focused ecosystems, and comprehensive professional services offerings. Actionable recommendations emphasize the importance of adaptive frameworks, governance programs, and cooperative engagements with device and standards bodies. By following these strategic pathways, organizations can optimize both security and user experience while capitalizing on emerging opportunities.
Ultimately, the imperative for industry stakeholders is to maintain a forward-looking posture-anticipating regulatory evolutions, technology breakthroughs, and shifting threat landscapes. The collective insights presented here provide a roadmap for navigating this dynamic environment and achieving sustained success in securing digital identities on mobile platforms.
Drive Your Strategic Advantage by Contacting Ketan Rohom Associate Director Sales & Marketing to Acquire the Comprehensive Mobile Identity Management Report
To gain a competitive edge and access the comprehensive insights outlined in this report, reach out to Ketan Rohom Associate Director Sales & Marketing at 360iResearch. Ketan Rohom can guide you through the detailed findings, clarify how these insights align with your strategic objectives, and facilitate a seamless acquisition of the full market research report. Engaging with Ketan will ensure your organization receives tailored recommendations, detailed segmentation analyses, and in-depth regional perspectives essential for informed decision-making in the mobile identity management landscape. Contacting Ketan Rohom today will empower your team with the knowledge to navigate evolving security challenges, leverage emerging technologies, and capitalize on market opportunities. Take the next step toward strengthening your mobile identity strategy by connecting with Ketan Rohom Associate Director Sales & Marketing to secure this indispensable resource and elevate your organizational readiness for the future of digital identity.

- How big is the Mobile Identity Management Market?
- What is the Mobile Identity Management Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




