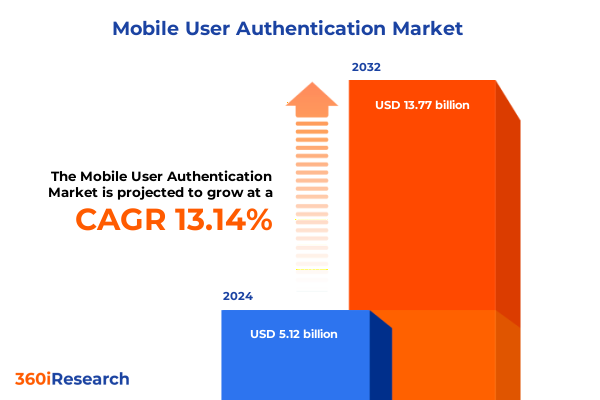
The Mobile User Authentication Market size was estimated at USD 5.79 billion in 2025 and expected to reach USD 6.54 billion in 2026, at a CAGR of 13.18% to reach USD 13.77 billion by 2032.
Mobilizing Trust at Your Fingertips—An Engaging Overview of Mobile User Authentication Drivers, Benefits, and Strategic Imperatives Shaping the Digital Future
In an era defined by digital transformation and remote engagement, mobile user authentication has emerged as a linchpin for securing interactions across applications, services, and devices. As smartphone penetration continues to soar, organizations face mounting pressure to protect sensitive data while ensuring seamless user experiences. Mobile authentication solutions bridge this imperative by integrating advanced technologies that verify identity with precision and speed. From the reliance on biometric identifiers such as facial recognition and fingerprint scanning to the resurgence of token-based mechanisms and knowledge-based credentials, businesses are reimagining their security posture to prioritize both trust and convenience.
Against this backdrop, decision-makers must navigate a complex landscape of evolving cybersecurity threats, stringent regulatory demands, and shifting user expectations. Legacy approaches are giving way to adaptive frameworks that can scale effortlessly and thwart sophisticated attacks. The rise of decentralized identity paradigms further underscores a transition toward user-owned credentials and privacy-preserving authentication flows. As stakeholders across financial services, healthcare, government, and retail sectors converge on mobile-first strategies, understanding the nuances of authentication modalities becomes paramount to crafting resilient digital ecosystems.
Navigating the Next Wave of Secure Access—Exploring Transformational Shifts in Mobile User Authentication Shaping Security Strategies Worldwide
Over the past few years, the mobile authentication domain has undergone seismic shifts driven by breakthroughs in artificial intelligence, cryptographic innovation, and platform integration. Biometric modalities, once confined to high-security installations, are now embedded in mainstream devices, delivering intuitive identity verification through facial mapping or voice recognition. Concurrently, knowledge-based safeguards such as patterns and PINs are being reinforced by adaptive risk engines that analyze behavioral cues and contextual data to detect anomalies in real time. These convergent developments have unlocked new possibilities for zero trust frameworks, where authentication and continuous verification coexist seamlessly.
Simultaneously, the maturation of software tokens and passkey standards is reshaping expectations for frictionless logins. Cloud-native deployment models have facilitated rapid rollouts of multi-factor authentication services, while hybrid and on-premise architectures cater to organizations with strict data sovereignty requirements. These hybrid frameworks empower institutions to calibrate security controls according to their operational imperatives, ensuring compliance with sector-specific mandates without compromising agility. The fusion of token-based protocols with advanced biometric assurance signals a future where identity is both portable and immutable, anchoring user confidence and operational resilience.
Assessing Tariff Turbulence on Secure Access Technologies—Unraveling the Cumulative Impact of United States 2025 Tariffs on Mobile Authentication Supply Chains and Costs
In 2025, the United States imposed a series of tariffs targeting hardware components integral to authentication devices, encompassing biometric sensors and secure elements used in smart tokens. These levies have reverberated across global supply chains, amplifying procurement costs for manufacturers and prompting reassessment of vendor contracts. As a direct consequence, market participants are accelerating the shift toward software-based tokens and subscription licensing models that circumvent hardware constraints while maintaining robust security postures. Enterprises are increasingly diversifying their sourcing strategies to mitigate exposure to tariff-induced price volatility, exploring partnerships with domestic chipset producers and regional electronics assemblers.
Moreover, the cumulative impact of these trade measures has catalyzed a strategic pivot toward end-to-end encryption frameworks that minimize reliance on specialized hardware. Organizations are piloting virtual secure modules and cloud-hosted authentication vaults that obviate the need for physical token shipments. This paradigm shift not only dampens the toll of import duties but also reduces logistical delays associated with cross-border shipments. In tandem, public sector initiatives are incentivizing local manufacturing through grants and tax credits, fostering a more resilient authentication ecosystem. These interventions, combined with an intensified focus on software innovation, are shaping a post-tariff era marked by leaner hardware footprints and amplified software-centric capabilities.
Deep Diving into Authentication Personas and Technologies—Key Segmentation Insights Revealing Varied Preferences and Adoption Patterns Across Industries and Models
Delving into authentication technology classifications reveals nuanced adoption trajectories across biometric, knowledge-based, multi-factor, and token-based solutions. Biometric verification extends beyond fingerprint scanning to embrace facial, iris, and voice recognition, each modality gaining traction in segments demanding high-speed user onboarding or stringent compliance. Knowledge-driven mechanisms, including password, pattern, and PIN constructs, remain ubiquitous for their simplicity and legacy integration, yet they are rapidly enhanced by behavioral analytics to detect unusual access patterns. Token-based authentication bifurcates into hardware and software tokens, with hardware devices experiencing headwinds from recent import duties while software tokens flourish under cloud subscription models.
Deployment paradigms further stratify the landscape into cloud-based, hybrid, and on-premise models that cater to varying regulatory and operational imperatives. Cloud-first architectures enable swift scaling and feature updates, particularly appealing to digital-native enterprises, whereas hybrid environments bridge legacy infrastructure with modernized authentication services. Pure on-premise configurations persist in sectors where data localization and sovereignty are paramount. Across end users, financial institutions rely heavily on multi-factor approaches to meet regulatory benchmarks, government agencies prioritize iris and facial biometrics for official services, healthcare entities emphasize convenience and hygiene through contactless methods, while IT telecom operators value scalable, high-availability frameworks and retail chains seek frictionless guest checkouts. Finally, authentication factor strategies range from single-factor simplicity to robust two-factor deployments, with multi-factor systems becoming the gold standard for high-risk transactions.
This comprehensive research report categorizes the Mobile User Authentication market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Authentication Technology
- Authentication Factor
- End User
- Deployment Model
Unveiling Regional Dynamics in Mobile Authentication Adoption—Comparative Insights Highlighting Distinct Drivers and Challenges across Americas, EMEA, and Asia-Pacific
Across the Americas, the emphasis on mobile user authentication is driven by extensive smartphone penetration and a proactive regulatory environment that mandates secure digital identities for financial transactions. Enterprises in North and South America are accelerating implementations of biometric onboarding alongside risk-based multi-factor approaches, reflecting a consumer appetite for both security and convenience. In contrast, Europe, the Middle East, and Africa exhibit a heterogeneous tapestry of regulatory frameworks and technology maturities. The European Union’s digital identity scheme harmonizes standards across member states, fostering interoperability, while emerging markets within the region adopt cloud-based services to circumvent legacy infrastructure constraints.
In the Asia-Pacific theater, rapid digitization initiatives and government-led identity platforms are fueling widespread adoption of mobile authentication. Nations with advanced banking ecosystems are pioneering decentralized identity architectures that grant citizens direct control over their credentials. Meanwhile, providers are tailoring their offerings to diverse linguistic, cultural, and infrastructural contexts, integrating local language support and offline authentication fallbacks in areas with intermittent connectivity. These regional dynamics underscore the need for solution providers to customize deployment models and feature sets according to localized requirements, ensuring end-to-end accessibility and compliance across diverse markets.
This comprehensive research report examines key regions that drive the evolution of the Mobile User Authentication market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Profiling Industry Innovators Revolutionizing Mobile Access Security—Core Corporate Strategies, Partnerships, and Technology Milestones Defining Competitive Leadership
Leading entities in the mobile authentication domain are crystallizing their positions through strategic alliances, product innovations, and targeted acquisitions. Biometric pioneers are enhancing sensor fidelity and anti-spoofing capabilities, while tokenization specialists are forging partnerships with fintech platforms to embed secure elements into digital wallets. Multi-factor solutions providers are diversifying their portfolios with adaptive risk analytics and contextual authentication services that learn from environmental and behavioral data. Additionally, several agile startups have emerged, harnessing decentralized identity standards to challenge incumbents and drive interoperability across ecosystems.
Collaborations between cloud infrastructure giants and cybersecurity firms are creating integrated platforms that consolidate authentication, authorization, and threat intelligence into unified offerings. These partnerships are instrumental in delivering end-to-end managed services that relieve enterprises of the complexities associated with maintaining discrete authentication stacks. Meanwhile, established technology vendors are expanding their footprints in vertical markets through acquisitions of niche providers specializing in healthcare-grade authentication and government-grade identity management. This wave of consolidation is shaping a competitive landscape where scale, interoperability, and innovation converge to define market leadership.
This comprehensive research report delivers an in-depth overview of the principal market players in the Mobile User Authentication market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Broadcom Inc.
- Cifrasoft Ltd.
- Cisco Systems, Inc.
- CyberArk Software Ltd.
- Dell Inc.
- Entrust Corporation
- Entrust Corporation.
- Nexus Group
- Okta, Inc.
- OneLogin LLC
- OneSpan Inc.
- Ping Identity Inc.
- Plurilock Security Inc.
- Protectimus Ltd.
- Secret Double Octopus Inc.
- SecureAuth Corporation
- SecurEnvoy PLC
- Sophos Ltd.
- Stytch Inc.
- Telesing Corporation
- Thales Group
- Vonage LLC
- Yubico AB
Empowering Strategic Excellence in Access Security—Actionable Recommendations Guiding Industry Leaders to Futureproof Mobile User Authentication Investments and Roadmaps
To navigate the complex mobile authentication terrain, leaders should enact a multipronged strategy that balances innovation with operational resilience. Prioritizing investment in cloud-native biometric services can accelerate time-to-market while reducing dependency on hardware constrained by tariff exposures. Complementing this with adaptive risk-based frameworks will enable dynamic authentication flows that calibrate security levels based on transaction risk profiles. Additionally, diversifying downstream ecosystems through partnerships with local technology integrators can expedite deployments in regionally fragmented markets, ensuring cultural and regulatory alignment.
Industry decision-makers must also cultivate an agile supply chain by identifying alternative hardware token manufacturers and exploring virtual secure module offerings to mitigate cost inflation. Engaging in standards bodies and consortia will secure early insights into emerging authentication protocols, empowering organizations to influence interoperability roadmaps. Finally, embedding analytics-driven intelligence within identity infrastructures will deliver continuous visibility into access patterns, streamline compliance reporting, and fortify real-time threat detection capabilities, thereby underpinning a resilient and future-ready authentication ecosystem.
Ensuring Research Rigor through Comprehensive Methodologies—An In-depth Overview of Data Collection, Validation Techniques, and Analytical Frameworks Underpinning Findings
Our research methodology integrates a multi-layered approach encompassing primary and secondary data sources to ensure comprehensive coverage of the mobile authentication landscape. Initial phases involved in-depth interviews with key industry stakeholders across financial services, healthcare, government, and retail verticals to capture qualitative nuances. These insights were complemented by a detailed review of regulatory filings, public disclosures, and technical whitepapers focused on biometric algorithms, tokenization frameworks, and risk analytics architectures.
Quantitative data was triangulated through surveys administered to technology decision-makers and end users, capturing sentiment around adoption drivers and pain points. Secondary research spanned a diverse array of credible publications, academic journals, and industry symposium proceedings, facilitating cross-validation of emerging trends. Data synthesis was conducted via robust analytical frameworks that mapped segmentation matrices against adoption curves. Quality assurance protocols, including peer reviews and expert validations, were employed to refine findings and corroborate hypothesis-driven insights, ensuring that the report’s conclusions maintain the highest standards of accuracy and reliability.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Mobile User Authentication market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Mobile User Authentication Market, by Authentication Technology
- Mobile User Authentication Market, by Authentication Factor
- Mobile User Authentication Market, by End User
- Mobile User Authentication Market, by Deployment Model
- Mobile User Authentication Market, by Region
- Mobile User Authentication Market, by Group
- Mobile User Authentication Market, by Country
- United States Mobile User Authentication Market
- China Mobile User Authentication Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 1272 ]
Mastering Mobile Access Security Through Conclusive Insights—Synthesized Reflections on Emerging Trends, Persistent Challenges, and Strategic Pathways for Future Growth
Bringing together the myriad insights on mobile user authentication paints a coherent narrative of an industry at the cusp of dramatic evolution. Technological convergence among biometric, token-based, and knowledge-driven modalities is unlocking novel authentication paradigms that harmonize security with user convenience. Regional heterogeneity in regulatory landscapes and market maturity demands tailored approaches, while recent tariff interventions have underscored the imperative to pivot toward software-defined solutions. Competitive dynamics are being redefined through collaborative ecosystems and disruptive entrants championing decentralized identity.
Ultimately, organizations that strategically invest in adaptable, data-driven authentication frameworks will be best positioned to navigate emerging threats and regulatory shifts. By aligning technological selection with deployment imperatives and end-user expectations, enterprises can fortify trust, streamline customer journeys, and sustain digital growth. The evolving authentication frontier offers a rich tapestry of opportunities; seizing them requires an integrative approach that leverages innovation, compliance, and strategic foresight.
Accelerate Your Security Strategy with Expert-Led Insights—Contact Ketan Rohom, Associate Director of Sales & Marketing, to Unlock the Full Mobile Authentication Market Report
Elevate your organizational security posture by leveraging our comprehensive market research report tailored to mobile user authentication. Engage directly with Ketan Rohom, our Associate Director of Sales & Marketing, to explore how this in-depth analysis can catalyze your strategic decision-making. By connecting with Ketan, you will gain personalized guidance on harnessing the report’s rich insights into technology adoption, regulatory impacts, and competitive benchmarks. Secure a competitive edge through actionable intelligence on emerging authentication protocols, deployment strategies, and regional growth vectors. Reach out now to discover detailed intelligence on biometric implementations, next-generation tokenization, multi-factor frameworks, and more-all designed to empower your roadmap for robust, user-centric access control solutions.

- How big is the Mobile User Authentication Market?
- What is the Mobile User Authentication Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




