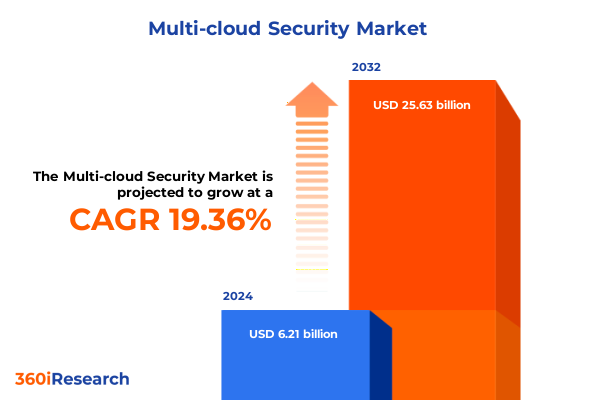
The Multi-cloud Security Market size was estimated at USD 7.43 billion in 2025 and expected to reach USD 8.75 billion in 2026, at a CAGR of 19.33% to reach USD 25.63 billion by 2032.
Exploring the Evolving Dynamics of Multi-Cloud Security to Illuminate Challenges and Opportunities for Modern Enterprise Infrastructure
Enterprises around the globe are rapidly embracing multi-cloud architectures to harness the flexibility, performance, and cost efficiencies that public, private, and hybrid cloud environments afford. However, this accelerated adoption brings with it unprecedented security complexities that extend far beyond traditional perimeter defenses. As organizations onboard a diverse array of cloud providers, they must navigate disparate security models, inconsistent policy frameworks, and fragmented visibility across workloads and data flows. Failure to establish a unified security posture in this context can result in misconfigurations, unprotected data, and gaps that sophisticated threat actors can exploit.
Moreover, the shifting threat landscape compounds these challenges, as adversaries innovate new techniques specifically targeting cloud-native environments. From automated misconfiguration scans to container escape exploits, attackers have developed a sophisticated toolkit designed to undermine perimeter assumptions. In response, security leaders must implement a defense-in-depth strategy that accounts for identity, data, network traffic, workloads, and user behavior holistically. This introduction sets the stage for understanding how multi-cloud security demands both broad strategic alignment and deep technical expertise in order to protect modern digital enterprises.
Uncovering the Paradigm-Shifting Forces Reshaping the Multi-Cloud Security Landscape in an Era of Rapid Digital Transformation
The multi-cloud security landscape is undergoing several paradigm-shifting transformations that require security practitioners to rethink existing architectures and processes. Firstly, zero trust principles are moving from theoretical frameworks into practical implementations, challenging traditional notions of trusted internal networks. This shift mandates continuous authentication, strict access controls, and microsegmentation to ensure that no user or workload operates with implicit trust. Secondly, the proliferation of containerized and serverless workloads has introduced ephemeral compute instances that demand automated security validation at every stage of the DevOps pipeline, blending security tooling directly into CI/CD workflows.
In addition, artificial intelligence and machine learning are becoming critical enablers for security operations centers (SOCs), enabling real-time anomaly detection across sprawling cloud footprints. These advanced analytics tools help identify patterns of malicious activity that manual monitoring would overlook. Meanwhile, compliance and privacy regulations are tightening across geographies, creating a need for cross-cloud policy orchestration that ensures consistent controls irrespective of deployment region. Taken together, these transformative forces are redefining how organizations secure their cloud-native assets, compelling them to adopt holistic, adaptive security strategies.
Assessing the Far-Reaching Consequences of New United States Tariff Measures on Multi-Cloud Security Operations and Supply Chain Dynamics in 2025
In 2025, the imposition of new tariffs on cloud infrastructure components, including specialized security appliances and networking hardware imported into the United States, has rippled through the multi-cloud ecosystem. These measures have led to increased procurement costs for on-premises security gateways and specialized servers used in private cloud deployments. Consequently, organizations seeking granular control over traffic inspection and data encryption at the network edge face budgetary pressures that can delay or limit planned security investments.
Conversely, tariff-driven shifts have accelerated interest in software-defined security solutions and managed detection and response services that rely less on physical appliances. By transitioning to cloud-native security platforms, organizations can mitigate cost fluctuations while benefiting from vendor-managed threat intelligence feeds and automatic policy updates. However, this reallocation also demands careful scrutiny of service-level agreements and data residency guarantees, as enterprises rebalance their security posture amid evolving regulatory and economic headwinds introduced by tariff adjustments.
Revealing Critical Insights Across Component Services, Deployment Models, End Use Industries, and Their Implications for Security Strategy
A nuanced understanding of market segmentation reveals where multi-cloud security requirements diverge and how specialized capabilities align with organizational priorities. Based on component analysis, the domain bifurcates into offerings centered on services and those defined by discrete solutions. Within the services category, managed services provide ongoing monitoring, incident response, and policy management, while professional services encompass custom security assessments, architecture design, and integration workshops. The solutions side features platforms such as cloud access security brokers that manage policy enforcement across applications, cloud security posture management tools that identify configuration drift and compliance deviations, data security offerings that encrypt and tokenize sensitive information, identity and access management suites that govern privileges, network security products that inspect traffic flows, and advanced threat intelligence and analytics modules that leverage behavioral data to anticipate attacks.
When considering service type, the market naturally separates into managed and professional offerings that address distinct maturity levels and resourcing models within IT teams. Deployment model segmentation further highlights variations in strategy, distinguishing between hybrid environments that intertwine on-premises and cloud resources, private clouds that serve dedicated enterprise workloads behind corporate firewalls, and public clouds offering scalable, multi-tenant infrastructure. Finally, industry verticals introduce specialized demands: the banking financial services and insurance sector requires granular audit trails and real-time fraud detection across banking, financial services, and insurance subdomains; government and defense entities emphasize rigorous compliance mandates and classified data handling; healthcare organizations focus on patient data privacy and interoperability; and IT and telecom companies prioritize network resilience and subscriber privacy across global infrastructures. Together, these segmentation lenses inform a granular approach to developing security solutions that meet the specific technical, regulatory, and operational needs of diverse enterprises.
This comprehensive research report categorizes the Multi-cloud Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Service Type
- Deployment Model
- End Use Industry
Analyzing Regional Variances and Strategic Priorities Across Americas, Europe Middle East & Africa, and Asia-Pacific in Multi-Cloud Security Context
Regional factors exert a profound influence on multi-cloud security strategies, driven by differing regulatory frameworks, maturity levels, and threat ecosystems. In the Americas, organizations benefit from a robust set of standards and guidelines that have matured alongside early cloud adoption. U.S. and Canadian enterprises often lead with integrated compliance toolkits that map to national regulations while leveraging extensive threat-sharing communities. Meanwhile, Latin American firms are advancing cloud security practices rapidly but continue to navigate infrastructure constraints and variable data localization requirements, resulting in a focus on lightweight, API-driven security controls.
Across Europe, the Middle East, and Africa, the security conversation centers on stringent privacy directives and cross-border data transfer rules. European entities place a premium on data sovereignty and consent management, frequently adopting cloud security posture management platforms with built-in GDPR compliance checks. Middle East governments are investing heavily in sovereign cloud frameworks to secure critical infrastructure, while African organizations are exploring cloud-first models that depend on managed service providers to deliver security expertise at scale. In the Asia-Pacific region, diverse economic and regulatory landscapes create a mosaic of security priorities. Mature markets like Japan and Australia emphasize zero trust adoption and advanced identity analytics, whereas Southeast Asian markets prioritize streamlined encryption capabilities and simplified onboarding processes to accelerate digital transformation initiatives. These regional distinctions underscore the importance of adaptable security architectures that can reconcile global policy mandates with local operational realities.
This comprehensive research report examines key regions that drive the evolution of the Multi-cloud Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Illuminating the Competitive Landscape Through Key Vendor Capabilities, Partnerships, and Innovations Driving Multi-Cloud Security Excellence
The competitive field for multi-cloud security solutions is defined by established incumbents and innovative challengers, each bringing unique strengths to bear. Leading vendors have fortified their portfolios through strategic partnerships and technology acquisitions, integrating endpoint security, network inspection, and identity management into cohesive platforms. Some providers differentiate themselves through advanced threat intelligence networks that aggregate global telemetry, offering subscribers real-time indicators of compromise tailored to their cloud footprints.
At the same time, cloud hyperscale operators are embedding security services directly into their platforms, enabling customers to leverage native access controls, automated posture assessments, and integrated logging without the need for external tooling. This vertical integration streamlines policy enforcement but also raises considerations around vendor lock-in and data portability. Challenger firms are carving out niches by focusing on next-generation use cases such as workload microsegmentation for container clusters, dynamic policy orchestration through infrastructure-as-code integrations, and AI-driven deception techniques that misdirect adversaries. The resulting vendor landscape compels security teams to evaluate not just feature sets, but partnership models, global support coverage, and roadmaps for emerging capabilities in areas like confidential computing and quantum-resistant encryption.
This comprehensive research report delivers an in-depth overview of the principal market players in the Multi-cloud Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Amazon Web Services, Inc.
- Aqua Security Software Ltd.
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- CrowdStrike Holdings, Inc.
- Darktrace Limited
- Forcepoint LLC
- Fortinet, Inc.
- Google LLC
- International Business Machines Corporation (IBM)
- Lacework, Inc.
- McAfee Corp.
- Microsoft Corporation
- Netskope, Inc.
- Orca Security Ltd.
- Palo Alto Networks, Inc.
- Rapid7, Inc.
- Tenable, Inc.
- Trend Micro Incorporated
- Zscaler, Inc.
Strategic Actions and Practical Frameworks to Enhance Security Posture and Ensure Seamless Multi-Cloud Governance Across Complex IT Environments
Industry leaders can take definitive steps to bolster their security posture and streamline multi-cloud governance. It is essential to establish a unified policy framework that transcends individual cloud environments, ensuring consistent access controls and data classification standards. By embedding zero trust principles across applications, identities, and networks, organizations reduce the likelihood of lateral movement and privilege escalation. In parallel, integrating security checks early in the development lifecycle through infrastructure-as-code scanning and automated compliance gates helps to catch misconfigurations before workloads reach production.
Furthermore, consolidating security tooling around platforms that support both managed services and professional engagements optimizes operational efficiency while providing access to expert guidance. Automation and orchestration should be leveraged to manage incident response workflows and policy updates at scale. Investment in upskilling internal teams through cross-functional training programs equips staff to navigate the evolving threat landscape and cloud-native paradigms. Lastly, regularly revisiting vendor contracts to align with emerging requirements in data residency, performance SLAs, and threat intelligence sharing ensures that cloud security investments remain adaptive and cost-effective.
Detailing the Comprehensive Research Design, Data Collection Methods, and Analytical Approaches Underpinning Insights into Multi-Cloud Security Trends
The research approach underpinning these insights blends primary and secondary data collection to ensure a holistic view of the multi-cloud security market. Primary research comprised in-depth interviews with CISOs, security architects, and cloud operations leads across diverse industries, complemented by surveys that gathered quantitative data on deployment challenges, technology preferences, and budget priorities. Vendor briefings and product demonstrations provided firsthand exposure to emerging features and roadmap commitments.
Secondary research incorporated an extensive review of regulatory publications, technical whitepapers, and peer-reviewed articles to contextualize trends within compliance frameworks and threat intelligence landscapes. Data triangulation techniques were applied to reconcile variations between self-reported organizational practices and observed market developments. Throughout the analysis, rigorous validation procedures-such as cross-referencing public disclosures with private interview data-ensured accuracy. This methodology delivers a reliable foundation for the strategic recommendations and detailed segmentation insights contained in this report.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Multi-cloud Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Multi-cloud Security Market, by Component
- Multi-cloud Security Market, by Service Type
- Multi-cloud Security Market, by Deployment Model
- Multi-cloud Security Market, by End Use Industry
- Multi-cloud Security Market, by Region
- Multi-cloud Security Market, by Group
- Multi-cloud Security Market, by Country
- United States Multi-cloud Security Market
- China Multi-cloud Security Market
- Competitive Landscape
- List of Figures [Total: 16]
- List of Tables [Total: 1272 ]
Synthesizing Key Findings to Outline the Critical Imperatives and Future Directions for Organizations Adopting Multi-Cloud Security Architectures
As multi-cloud adoption accelerates, the imperative for robust, cohesive security strategies becomes more urgent. Key findings reveal that organizations must balance the agility gains of hybrid and public cloud deployments with the discipline of centralized governance and policy enforcement. Zero trust and automation emerge as critical enablers, while tariff-induced economic pressures are driving a strategic pivot toward software-centric security services. Additionally, distinguishing security requirements by workload type and industry vertical allows for targeted investments that maximize risk reduction without overburdening operational teams.
Looking ahead, the convergence of AI-driven analytics, advanced encryption methods, and container-aware defense mechanisms will define the next chapter of multi-cloud security innovation. By internalizing these insights and maintaining a proactive posture, organizations can safeguard data integrity, ensure regulatory compliance, and sustain business continuity in an ever-evolving threat environment.
Empowering Decisions Today by Engaging with Associate Director Ketan Rohom to Secure Comprehensive Multi-Cloud Security Intelligence and Report Access
If you are seeking to gain a competitive edge through comprehensive multi-cloud security intelligence, Ketan Rohom stands ready to guide you through the intricacies of this rapidly evolving domain. As the Associate Director overseeing Sales & Marketing for multi-cloud security research, he can provide bespoke insights tailored to your organization’s specific needs and technical environment. Engaging with Ketan will grant you exclusive access to in-depth analysis, battle-tested best practices, and forward-looking intelligence that will underpin your strategic planning and risk mitigation efforts.
By contacting Ketan, you will be connected to a seamless purchasing process that ensures rapid delivery of the full research report along with supplementary materials and advisory support. His expertise in aligning complex security requirements with real-world business objectives will facilitate informed decision-making and accelerate your journey toward resilient multi-cloud architectures. Reach out today to secure your organization’s place at the forefront of secure, cloud-native innovation and ensure you have the insights needed to stay ahead of emerging threats and regulatory shifts.

- How big is the Multi-cloud Security Market?
- What is the Multi-cloud Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




