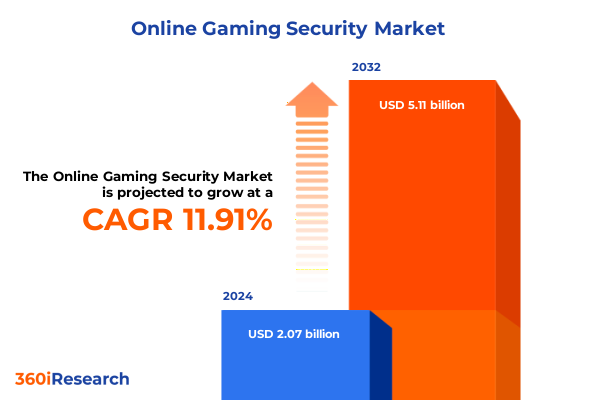
The Online Gaming Security Market size was estimated at USD 2.30 billion in 2025 and expected to reach USD 2.57 billion in 2026, at a CAGR of 12.03% to reach USD 5.11 billion by 2032.
Exploring the foundations of online gaming security to frame key challenges emerging from technological progress operational complexities and user safety needs
Online gaming has transformed into a vast ecosystem where millions of players engage simultaneously, exchanging digital assets, communicating in real time, and participating in increasingly sophisticated virtual environments. This expansion has created unprecedented economic opportunities, yet it has also escalated the complexity of safeguarding digital interactions. As technology advances, threat vectors multiply, requiring a comprehensive understanding of how emerging platforms and regulatory frameworks intersect with security imperatives to protect both game developers and end users.
Analyzing the tectonic shifts reshaping online gaming security through cloud adoption real-time analytics artificial intelligence and evolving threat actor tactics
The security paradigm within online gaming has been reshaped by the rapid adoption of cloud computing, which offers scalability and global access but also introduces new perimeter considerations. Parallel advances in real-time analytics and machine learning enable proactive threat detection and behavior analysis, yet they demand rigorous data governance and privacy safeguards. As development teams embrace continuous integration and continuous deployment methodologies, security must be embedded from the earliest stages to prevent vulnerabilities from propagating through agile release cycles.
Simultaneously, threat actors have evolved beyond traditional denial-of-service campaigns to orchestrate sophisticated identity theft, credential stuffing, and supply chain exploits. This shift compels organizations to strengthen identity management, enforce multi-factor authentication, and continuously monitor for anomalous behavior. Regulatory scrutiny has intensified across multiple jurisdictions, requiring cross-border compliance with data protection laws and digital transaction mandates. In this landscape, security strategies must be dynamic, holistic, and aligned with both technological innovations and the changing regulatory environment.
Assessing the comprehensive repercussions of 2025 United States tariffs on online gaming security supply chain economics and cross-border technology partnerships
In 2025, the United States implemented new tariff measures affecting hardware imports and software services integral to online gaming security. The levies on specialized networking equipment and encryption modules have increased direct procurement costs for security vendors, prompting a recalibration of supply chain strategies. Developers and service providers are exploring regional sourcing options and renegotiating long-term agreements to mitigate cost volatility, while also accelerating investment in domestic manufacturing capacities to ensure continuity of critical security infrastructure.
Beyond pricing pressures, these tariff adjustments have influenced collaborative arrangements between U.S. firms and international partners. Cross-border technology alliances have been restructured to account for shifting duty burdens, with some organizations opting to establish joint ventures or localized subsidiaries to maintain seamless access to essential solutions. As a result, the tariffs have not only imposed cost considerations but also catalyzed strategic realignment in global technology partnerships, underscoring the need for adaptive security procurement practices.
Deriving actionable insights from segmentation analysis across components risk types platforms deployment modes and end user categories in online gaming security
A nuanced examination of market segmentation reveals distinct patterns of demand and adoption across critical categories. When dissecting the component landscape, it becomes evident that service engagements, encompassing expert consulting and implementation, ongoing managed services, and dedicated support, are gaining traction as organizations seek guidance in integrating sophisticated security architectures. Meanwhile, solutions such as application layer protection, robust data encryption protocols, distributed denial-of-service mitigation, and comprehensive risk and fraud management platforms are prioritized for their ability to address specific threat vectors. Identity access controls, spanning multi-factor authentication, privileged access governance, and streamlined single sign-on experiences, form the cornerstone of user-centric protection frameworks.
Diverse risk types further shape organizational priorities, with incidents ranging from large-scale data breaches and targeted doxing to complex identity takeover and stealthy malware infiltrations. Each category demands tailored countermeasures, driving investments in phishing resilience and proactive vulnerability assessments. Platform differentiation highlights that console environments and PC systems continue to require specialized defense tools, while the proliferation of mobile gaming on Android and iOS introduces unique mobile-specific security considerations. The choice between cloud-based deployments and on-premises installations offers varying trade-offs between scalability and control, influencing both architectural design and operational management. Finally, the divide between game developers seeking integrated security into development pipelines and gamers-whether casual players or competitive e-sports athletes-underscores the importance of user-tailored safeguards and performance-sensitive solutions.
This comprehensive research report categorizes the Online Gaming Security market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Component
- Risk Type
- Platform
- Deployment Mode
- End User
Unveiling critical regional nuances influencing online gaming security adoption regulatory frameworks and risk landscapes across Americas EMEA and Asia-Pacific markets
Regional dynamics exert a profound influence on the uptake and evolution of online gaming security measures. In the Americas, a robust regulatory framework and high-velocity internet infrastructure drive rapid adoption of advanced encryption and managed security services, with both domestic firms and global vendors collaborating to meet stringent data protection standards. The prevalence of cross-border digital transactions within this region has led to a prioritization of identity verification and fraud prevention solutions that can scale across national boundaries.
Contrastingly, Europe, the Middle East, and Africa present a multifaceted landscape where harmonized data privacy regulations coexist with emerging markets still building cybersecurity maturity. In Western Europe, compliance with comprehensive data protection mandates fuels investments in audit-ready security platforms, while in parts of the Middle East and Africa, public-private partnerships and international aid programs are fostering foundational capabilities. This diversity requires flexible approaches that can address both advanced threat intelligence needs and fundamental resilience building.
In the Asia-Pacific region, mobile gaming dominance and dynamic digital ecosystems have accelerated demand for real-time analytics, mobile-first security solutions, and regionally compliant encryption standards. Rapidly growing markets in Southeast Asia and East Asia are embracing cloud-native architectures, emphasizing low-latency protection for large player communities. At the same time, established markets such as Japan and Australia continue to innovate in user authentication and platform hardening, creating a rich environment for cross-regional knowledge exchange and collaborative defense initiatives.
This comprehensive research report examines key regions that drive the evolution of the Online Gaming Security market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Highlighting leading companies driving innovation investment and collaboration in securing online gaming environments against escalating cyber threats
A small cohort of technology leaders is shaping the trajectory of online gaming security through targeted innovation and strategic partnerships. Network security pioneers have expanded their portfolios to include gaming-specific threat mitigation modules, integrating artificial intelligence-driven detection engines with existing infrastructure. Security platforms specializing in identity and access management have launched developer-friendly SDKs that streamline authentication workflows without compromising performance, addressing the unique demands of real-time gaming environments.
At the same time, emerging vendors focused on fraud analytics and behavioral biometrics are collaborating with established players to embed advanced machine learning models into content delivery networks and game engines. These cross-industry alliances aim to unify user experience optimization and security orchestration, reducing friction for legitimate players while rapidly isolating malicious activities. Investment from venture capital and strategic corporate investors has accelerated the growth of these innovators, fueling continuous product enhancements and geographic expansion efforts.
This comprehensive research report delivers an in-depth overview of the principal market players in the Online Gaming Security market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Akamai Technologies, Inc.
- Amazon Web Services, Inc.
- AO Kaspersky Lab
- Arkose Labs, Inc.
- Bitdefender SRL
- Botbusters
- Cactus Gaming
- Cisco Systems Inc.
- Cloudflare, Inc.
- Digital.ai Software, Inc.
- F-Secure
- F5, Inc.
- FairPlay Labs
- Fortinet, Inc.
- Gen Digital Inc.
- Google LLC by Alphabet Inc.
- Human Security, Inc.
- Illusive Networks Ltd.
- Imperva, Inc. by Thales SA
- Inka Entworks Inc.
- Inka Entworks Inc.
- INUI Gaming FZ-LLC
- Irdeto B.V.
- Kamu Group Oy
- Kidentify Corp
- McAfee, LLC
- Microsoft Corporation
- Modulate, Inc.
- NAGRAVISION S.à.r.l
- NETSCOUT Systems, Inc.
- Noventiq Holdings plc
- OneSpan Inc.
- Palo Alto Networks, Inc.
- PlayerVerify
- Radware Ltd.
- SecurePlay
- Shield Security
- Synack, Inc.
- Synack, Inc.
- Tencent Holdings Limited
- Trend Micro Incorporated
- Ubisoft Entertainment SA
- Unbotify
Presenting strategic and actionable recommendations for industry leaders to strengthen defenses governance and resilience in the evolving online gaming security landscape
Industry leaders should prioritize a zero-trust framework that rigorously verifies every user, device, and transaction before granting access, thereby reducing the attack surface in distributed gaming architectures. Embedding security into every phase of the development lifecycle will ensure vulnerabilities are identified early, enabling faster remediation and minimizing risk exposure during rapid release cycles.
Organizations must also cultivate strategic alliances with specialized security providers to augment in-house capabilities, leveraging managed detection and response services to continuously monitor global threat landscapes. Investing in adaptive authentication techniques that combine multi-factor mechanisms with contextual behavioral analysis will fortify identity defenses without degrading user experience. Finally, fostering a culture of continuous learning through collaborative threat intelligence sharing and targeted training programs will empower both technical teams and executive stakeholders to make informed decisions and maintain resilience against evolving adversaries.
Detailing rigorous research methodology encompassing data collection triangulation validation and qualitative expert inputs to ensure robust findings in gaming security
This analysis leverages a rigorous multi-method research approach, initiating with an extensive review of public sources, patent filings, regulatory disclosures, and security standards documentation. Secondary data was complemented by a series of structured interviews with senior security architects, chief information security officers, and platform operators, providing qualitative depth and contextual nuance.
Quantitative insights were validated through triangulation across vendor product roadmaps and publicly reported incident case studies, ensuring consistency and accuracy. A panel of subject-matter experts reviewed preliminary findings and contributed scenario-based stress testing to challenge assumptions and refine strategic implications. This combination of primary and secondary research, underpinned by methodical validation steps, underscores the credibility and reliability of the conclusions presented.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Online Gaming Security market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Online Gaming Security Market, by Component
- Online Gaming Security Market, by Risk Type
- Online Gaming Security Market, by Platform
- Online Gaming Security Market, by Deployment Mode
- Online Gaming Security Market, by End User
- Online Gaming Security Market, by Region
- Online Gaming Security Market, by Group
- Online Gaming Security Market, by Country
- United States Online Gaming Security Market
- China Online Gaming Security Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1431 ]
Summarizing key findings and strategic takeaways that encapsulate the critical importance of proactive security measures in the fast-paced online gaming domain
The convergence of advanced technologies, shifting regulatory regimes, and geopolitical influences has created a complex yet opportunity-rich environment for securing online gaming platforms. By understanding the nuances of component and platform segmentation, regionally distinct risk profiles, and evolving threat actor behaviors, organizations can craft comprehensive defenses that align with strategic objectives.
Proactive adoption of integrated security frameworks, continuous collaboration with leading solution providers, and investment in agile, data-driven monitoring capabilities will position stakeholders to navigate future challenges. These insights serve as a foundation for informed decision-making, enabling both developers and operators to maintain trust, ensure compliance, and deliver seamless gaming experiences in an increasingly digital world.
Immediate next steps for C-suite engagement and partnerships with Ketan Rohom to secure in-depth intelligence on the online gaming security market report today
To gain comprehensive and actionable intelligence on the evolving online gaming security landscape and to align organizational strategies with the latest insights, reach out to Ketan Rohom, Associate Director of Sales & Marketing. Partnering with him will provide tailored access to the full market research report, including in-depth analyses, executive interactions, and exclusive data extracts. Engage with Ketan to secure your organization’s competitive advantage and unlock detailed guidance on navigating security challenges, leveraging emerging technologies, and capitalizing on regional market dynamics for sustainable growth in the online gaming sector

- How big is the Online Gaming Security Market?
- What is the Online Gaming Security Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




