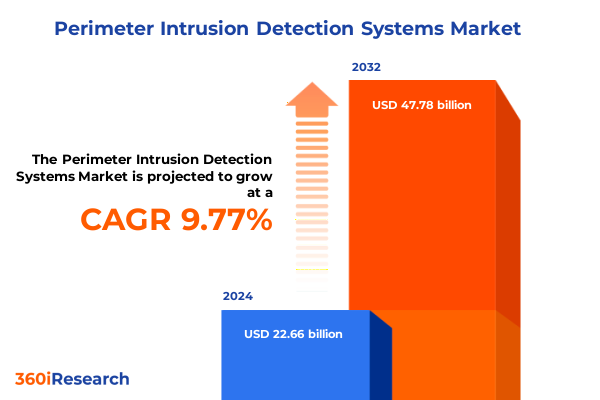
The Perimeter Intrusion Detection Systems Market size was estimated at USD 24.70 billion in 2025 and expected to reach USD 26.93 billion in 2026, at a CAGR of 9.88% to reach USD 47.78 billion by 2032.
Exploring the Strategic Evolution of Perimeter Intrusion Detection Systems in Shifting Threat Environments and Complex Security Ecosystems
Perimeter intrusion detection systems have become foundational to modern security infrastructures, evolving from simple barrier alarms to sophisticated multi-sensor platforms. Organizations across critical infrastructure, transportation hubs, industrial facilities, and commercial complexes recognize the imperative to detect and respond to unauthorized access attempts before breaches occur. This executive summary opens by contextualizing the shift in security paradigms, where deterrence alone no longer suffices and proactive detection with rapid verification is paramount. The accelerating frequency of sophisticated intrusion techniques has driven security architects to embrace technologies that deliver both high sensitivity and low false-alarm rates, ensuring that resources are focused on genuine threats rather than routine disturbances.
As digital transformation initiatives converge with heightened regulatory expectations, the role of perimeter intrusion detection has expanded well beyond physical boundaries. Seamless integration with video analytics, two-way communications, and centralized command platforms establishes a unified security posture. In this introduction, we frame the subsequent sections by highlighting the critical interplay between technological innovation, evolving threat landscapes, and strategic decision-making. Through a holistic overview, readers will understand how advanced sensors, analytics, and regulatory drivers collectively shape a dynamic market environment, setting the stage for deeper insights into emerging shifts, tariff impacts, segmentation nuances, and actionable recommendations.
Uncovering the Disruptive Technological and Regulatory Shifts Reshaping Perimeter Intrusion Detection Solutions for Modern Risk Mitigation Strategies
The landscape of perimeter intrusion detection is undergoing transformative change driven by breakthroughs in sensor fusion, artificial intelligence, and cloud-native architectures. Whereas legacy systems relied predominantly on single-technology barriers-such as buried cables or microwave beams-today’s offerings leverage multi-technology platforms that intelligently cross-validate intrusion events. This evolution enhances situational awareness, reduces false positives, and accelerates response workflows. Concurrently, the integration of deep learning algorithms and pattern-matching analytics enables systems to distinguish between innocuous environmental triggers and genuine security threats, leading to unprecedented levels of reliability and operational efficiency.
Alongside technological advances, regulatory dynamics and shifting organizational priorities are reshaping deployment strategies. Governments and critical infrastructure operators are updating security mandates to require real-time monitoring, data encryption, and interoperability with national security centers. Organizations are also extending perimeter detection boundaries to encompass virtual perimeters, leveraging remote sensors and edge-computing nodes. This convergence of physical and digital security demands agile platforms capable of evolving through software updates and cloud-driven features. As a result, perimeter intrusion detection solutions are no longer static installations but living ecosystems adapting to newly emerging threats and compliance requirements.
Assessing the Multifaceted Impact of 2025 United States Tariff Implementations on Supply Chains, Cost Structures, and Strategic Sourcing Decisions
The introduction of additional duties on imported security equipment from major overseas suppliers in early 2025 has introduced significant complexities for perimeter intrusion detection system providers and end users alike. Components such as high-precision fiber optic cables, specialized radar modules, and commercial off-the-shelf infrared sensors have experienced incremental cost increases, compelling system integrators to reexamine supply chain resilience. In many cases, manufacturers have absorbed portions of these levies to maintain competitive pricing, while end users have encountered subtle but distinct rises in installation budgets and maintenance contracts.
Over time, the accumulation of these tariffs has driven strategic localization efforts, with some leading vendors forging new partnerships with domestic manufacturers to secure critical components. This realignment mitigates reliance on susceptible supply routes, yet it also triggers longer lead times as production capacities are recalibrated. On the procurement side, project stakeholders are increasingly building tariff contingencies into capital planning, favoring modular and upgradable architectures to hedge against future cost shocks. As a result, a balance between cost containment and performance expectations defines current investment decisions, underscoring the need for proactive sourcing strategies and strategic inventory management.
Deriving Key Insights from Multifaceted Segmentation Across Technology, Application, Deployment and End User Industries to Drive Perimeter Security Strategy
A nuanced understanding of segmentation is essential for aligning perimeter intrusion detection investments with organizational priorities. Within the realm of technology, dual-technology systems that combine fiber optic radar with microwave infrared detection have emerged as versatile solutions for challenging environments, while standalone options such as fiber optic sensors, infrared beams, microwave barriers, radar units, and video surveillance platforms deliver targeted capabilities. Video solutions themselves bifurcate into cloud analytics deployments-ideal for centralized monitoring centers-and edge analytics implementations that support autonomous decision logic at remote sites.
End users span a broad spectrum, encompassing commercial centers, government installations, heavy industrial complexes, residential communities, and transportation facilities, each presenting unique operational requirements and threat vectors. Deployment modes further refine solution selection, distinguishing exterior field installations from interior safeguards around critical zones. Application focus areas range from asset protection and border security to safeguarding critical infrastructure, comprehensive facility surveillance, and continuous perimeter monitoring. Lastly, installation paradigms-new projects and retrofits-determine integration complexity and upgrade pathways, influencing budget allocation and lifecycle management. Together, these segmentation insights provide a structured lens through which security leaders can evaluate and tailor detection architectures to their specific risk profiles and infrastructural constraints.
This comprehensive research report categorizes the Perimeter Intrusion Detection Systems market into clearly defined segments, providing a detailed analysis of emerging trends and precise revenue forecasts to support strategic decision-making.
- Technology
- Installation Type
- End User Industry
- Deployment Mode
- Application
Identifying Regional Dynamics and Growth Drivers in the Americas, Europe Middle East Africa, and Asia-Pacific for Targeted Perimeter Intrusion Protection Deployment
Regional dynamics in perimeter intrusion detection reflect diverse security priorities, regulatory frameworks, and infrastructure investments across global markets. In the Americas, national focus areas include border control initiatives, critical energy installations, and expanding commercial developments that demand scalable intrusion solutions. Stakeholders prioritize modular platforms capable of integrating with existing physical barriers and command-and-control networks, while also accommodating rapid deployment in temporary or evolving sites.
In Europe, the Middle East, and Africa, heterogenous security landscapes drive demand for both high-end, multi-technology integrations and cost-effective legacy-upgrade projects. Stricter data privacy directives and cross-border security collaborations emphasize data sovereignty and secure communications protocols. Meanwhile, investment in infrastructure modernization programs spurs interest in perimeter solutions that support interoperability across diverse legacy systems and emergent smart city deployments.
The Asia-Pacific region continues to lead in large-scale infrastructure expansion, with extensive transit corridors, industrial parks, and smart manufacturing initiatives requiring advanced intrusion detection systems. The convergence of Internet of Things ecosystems with emerging 5G networks enables distributed sensor networks and real-time analytics, accelerating adoption of edge-driven detection platforms. Collectively, these regional insights underscore the need for adaptable solution sets tailored to local regulatory regimes, environmental conditions, and evolving threat scenarios.
This comprehensive research report examines key regions that drive the evolution of the Perimeter Intrusion Detection Systems market, offering deep insights into regional trends, growth factors, and industry developments that are influencing market performance.
- Americas
- Europe, Middle East & Africa
- Asia-Pacific
Examining the Competitive Landscape and Innovation Strategies of Leading Manufacturers Shaping the Future of Perimeter Intrusion Detection Solutions
Leading manufacturers in the perimeter intrusion detection domain distinguish themselves through differentiated technology portfolios, strategic partnerships, and ongoing innovation roadmaps. Honeywell leverages its global engineering capabilities to integrate multi-sensor modalities with unified command systems, while Bosch invests in intelligent sensor development and secure communication protocols that simplify field deployments. Senstar stands out for its expertise in fiber optic and microwave barrier technologies, offering highly sensitive detection tailored for high-security perimeters and border installations.
Emerging players such as Future Fibre Technologies introduce novel signal processing algorithms that enhance zone resolution, and established cybersecurity vendors collaborate to embed secure remote access layers into detection architectures. Axis Communications and FLIR/Teledyne have focused on expanding video analytics suites to complement traditional detection barriers, enabling rich metadata tagging and automated threat classification. Meanwhile, system integrators and regional specialists bring critical applications expertise, guiding customers through complex compliance environments and facilitating seamless upgrades of legacy systems.
Across the competitive landscape, strategic alliances with telecommunications providers, cloud service operators, and defense contractors are shaping new opportunities for joint offerings. The pursuit of open-architecture frameworks, adherence to emerging security standards, and commitment to comprehensive service models position these key players to lead the next wave of perimeter intrusion detection advancements.
This comprehensive research report delivers an in-depth overview of the principal market players in the Perimeter Intrusion Detection Systems market, evaluating their market share, strategic initiatives, and competitive positioning to illuminate the factors shaping the competitive landscape.
- Advanced Perimeter Systems Ltd.
- Axis Communications AB
- Carrier Global Corporation
- CIAS Elettronica S.r.l.
- Detection Technologies Ltd.
- Fiber SenSys Inc.
- Future Fibre Technologies Ltd.
- GJD Manufacturing Ltd.
- Hangzhou Hikvision Digital Technology Co., Ltd.
- Harper Chalice Group Ltd.
- Honeywell International Inc.
- Jacksons Fencing Ltd.
- Johnson Controls International plc
- Magal Security Systems Ltd.
- Magos Systems Ltd.
- Optex Co., Ltd.
- PureTech Systems Inc.
- Schneider Electric SE
- Senstar Corporation
- Sorhea SAS
- Southwest Microwave Inc.
- ST Engineering Electronics Ltd.
- Teledyne FLIR LLC
- Tyco International Ltd.
- Zhejiang Dahua Technology Co., Ltd.
Articulating Pragmatic and Strategic Recommendations for Industry Leaders to Enhance Operational Resilience and Technological Agility in Perimeter Security
To navigate the evolving perimeter intrusion detection landscape with confidence, industry leaders should adopt a multifaceted approach that emphasizes both technological and operational resilience. Investing in multi-technology detection platforms mitigates single-point failures and enhances threat discrimination, while ensuring ongoing support for both cloud-based and edge-driven analytics preserves agility in deployment models. Security teams must also prioritize integration capabilities, seeking systems that seamlessly interface with video management software, access control networks, and incident response platforms to create cohesive protection ecosystems.
Supply chain diversification is equally critical; developing relationships with multiple component suppliers and exploring domestic manufacturing options can buffer against tariff volatility and logistical disruptions. Leaders should formalize tariff-adjustment contingencies in procurement strategies, ensuring project timelines and budgets remain intact even as duty structures evolve. Additionally, establishing service-level agreements with clear performance metrics fosters accountability and drives continuous performance improvements.
Finally, cultivating partnerships with academic institutions, cybersecurity firms, and government agencies can accelerate innovation in advanced threat analytics and detection algorithms. By engaging in collaborative research programs and pilot deployments, security leaders position themselves at the forefront of technology validation, enabling early adoption of next-generation intrusion detection capabilities and sustaining a competitive edge.
Detailing a Rigorous and Transparent Research Methodology Underpinning Insights into Perimeter Intrusion Detection Systems Market Dynamics and Trends
This analysis is underpinned by a systematic, multi-stage research methodology designed to ensure robustness and reliability of insights. Initially, a comprehensive review of technical literature and industry standards provided foundational context on sensor technologies and integration frameworks. Subsequently, structured interviews were conducted with security directors, system integrators, and technology architects, enabling firsthand perspectives on deployment challenges and emerging requirements.
Quantitative data collection involved assembling a curated database of recent project implementations, tariff schedules, and publicly disclosed procurement orders to identify cost trends and sourcing patterns. Data triangulation techniques cross-verified these observations against vendor press releases, policy announcements, and independent technical evaluations. To validate findings, an expert advisory panel comprising security consultants, supply chain analysts, and regulatory specialists reviewed the preliminary outcomes, offering iterative feedback to refine thematic emphases and ensure practical relevance.
Finally, insights were synthesized into the segmentation framework and regional analyses presented in this summary, ensuring each recommendation and observation aligns with both current market realities and anticipated technological trajectories. This structured approach ensures that executives and decision-makers receive actionable, credible guidance tailored to the complexities of modern perimeter intrusion detection ecosystems.
This section provides a structured overview of the report, outlining key chapters and topics covered for easy reference in our Perimeter Intrusion Detection Systems market comprehensive research report.
- Preface
- Research Methodology
- Executive Summary
- Market Overview
- Market Insights
- Cumulative Impact of United States Tariffs 2025
- Cumulative Impact of Artificial Intelligence 2025
- Perimeter Intrusion Detection Systems Market, by Technology
- Perimeter Intrusion Detection Systems Market, by Installation Type
- Perimeter Intrusion Detection Systems Market, by End User Industry
- Perimeter Intrusion Detection Systems Market, by Deployment Mode
- Perimeter Intrusion Detection Systems Market, by Application
- Perimeter Intrusion Detection Systems Market, by Region
- Perimeter Intrusion Detection Systems Market, by Group
- Perimeter Intrusion Detection Systems Market, by Country
- United States Perimeter Intrusion Detection Systems Market
- China Perimeter Intrusion Detection Systems Market
- Competitive Landscape
- List of Figures [Total: 17]
- List of Tables [Total: 1272 ]
Concluding Critical Reflections on the Evolution Trajectory and Strategic Imperatives of Perimeter Intrusion Detection Technology in Modern Security Frameworks
The journey of perimeter intrusion detection technology illustrates a continuous quest for heightened reliability, adaptability, and integration. From early stand-alone sensors to today’s interconnected, AI-enhanced platforms, each evolutionary step reflects the persistent drive to pre-empt and mitigate emerging security threats. Critical imperatives for the future include embracing modular architectures that facilitate seamless technology upgrades, fostering cross-sector collaborations to address complex threat vectors, and maintaining agility in the face of shifting regulatory and tariff environments.
As organizations confront increasingly sophisticated intrusion tactics, the capacity to harness real-time analytics, deploy edge-computing nodes, and integrate with broader security ecosystems will define leadership in perimeter protection. Strategic planners must balance the allure of cutting-edge innovations with pragmatic considerations around total cost of ownership, supply chain resilience, and long-term serviceability. By internalizing the insights presented-from segmentation deep-dives to regional dynamics and company strategies-security executives can chart a course that both addresses immediate vulnerabilities and positions their infrastructures for future success.
Ultimately, the resilience of modern security operations hinges on proactive adaptation and informed decision-making. The convergence of advanced detection technologies, regulatory momentum, and evolving threat profiles creates a landscape rich with opportunity for those prepared to act decisively.
Driving Strategic Engagement and Next-Step Consultations with Ketan Rohom to Secure Your Competitive Edge in Perimeter Intrusion Detection Investment Decisions
I invite you to connect directly with Ketan Rohom, Associate Director of Sales & Marketing, to explore how this comprehensive analysis can empower your organization with actionable intelligence. By engaging in a strategic dialogue, you will gain exclusive insights into emerging security paradigms and leverage tailored recommendations to reinforce your perimeter defenses. Reach out to schedule a personalized briefing and discover a clear roadmap for aligning your security investments with next-generation technologies. Secure your competitive advantage in perimeter intrusion detection by initiating a conversation with Ketan-your next step toward informed decision-making and resilient protection.

- How big is the Perimeter Intrusion Detection Systems Market?
- What is the Perimeter Intrusion Detection Systems Market growth?
- When do I get the report?
- In what format does this report get delivered to me?
- How long has 360iResearch been around?
- What if I have a question about your reports?
- Can I share this report with my team?
- Can I use your research in my presentation?




